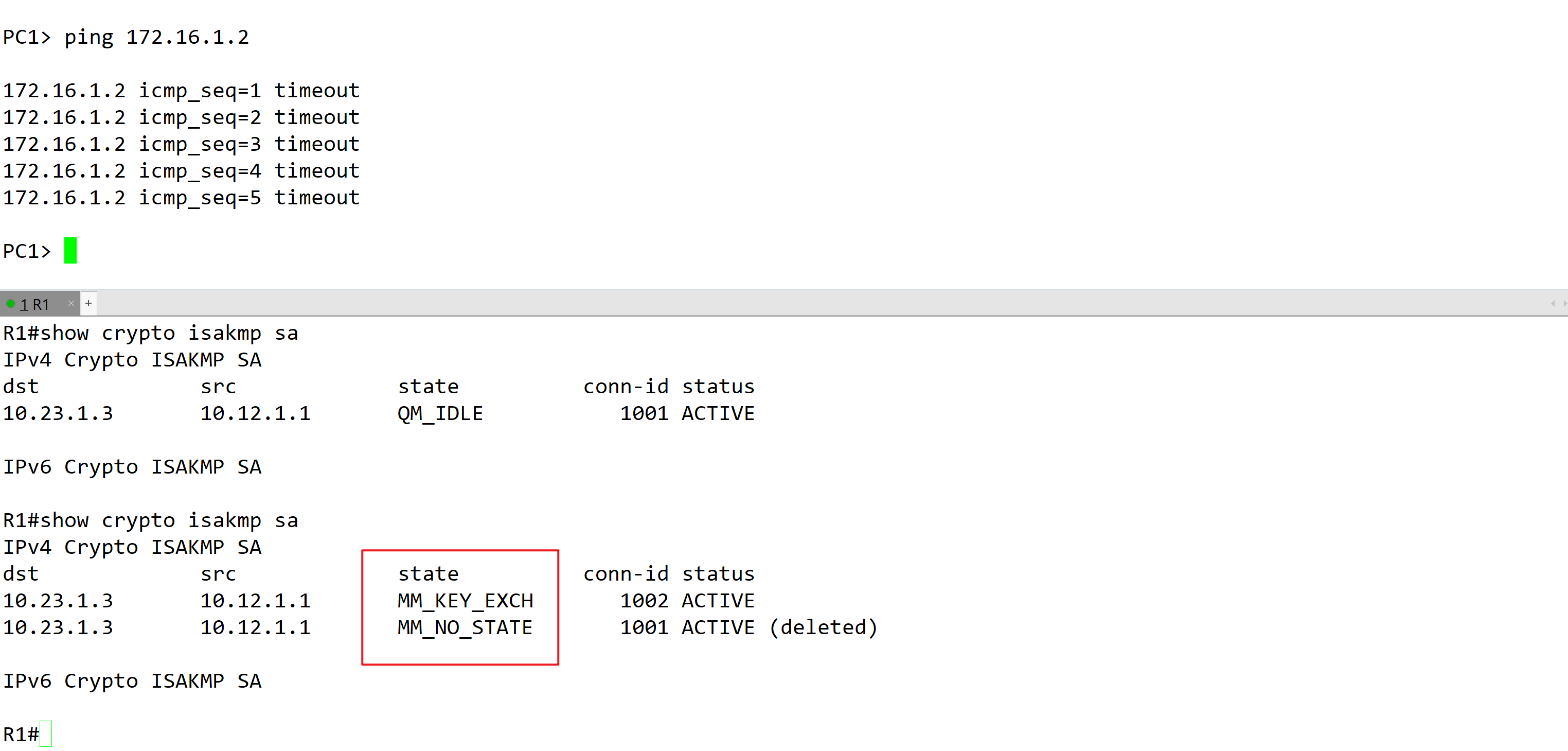
拓扑

步骤
IPsec
- crypto ipsec transform-set MT_TS esp-sha256-hmac esp-aes 256 前半部分是 auth,后半部分是 cipher
- ip access-list extended VPN_TRAFFIC permit ip 172.16.1.0 0.0.0.255 192.168.1.0 0.0.0.255 —— 其实设置的就是Proxy-ID
!!!!!!!!R1crypto isakmp policy 1 encr aes 256 hash sha256 authentication pre-share group 5crypto isakmp key CISCO address 10.23.1.3 crypto ipsec transform-set MT_TS esp-sha256-hmac esp-aes 256 mode tunnelcrypto map MY_CRYPTO 10 ipsec-isakmp set peer 10.23.1.3 set transform-set VPN_TS match address VPN_TRAFFIC!!!!!!!!!R3crypto isakmp policy 1 encr aes 256 hash sha256 authentication pre-share group 5crypto isakmp key CISCO address 10.12.1.1 crypto ipsec transform-set MT_TS esp-sha256-hmac esp-aes 256 crypto map MY_CRYPTO_MAP 10 ipsec-isakmp set peer 10.12.1.1 set transform-set VPN_TS match address VPN_TRAFFIC!!!!!ip access-list extended VPN_TRAFFIC permit ip 172.16.1.0 0.0.0.255 192.168.1.0 0.0.0.255 !!!!!interface GigabitEthernet0/0 crypto map MY_CRYPTO_MAP
- ip access-list extended VPN_TRAFFIC permit ip 172.16.1.0 0.0.0.255 192.168.1.0 0.0.0.255 —— 这种配置方式,端口状态需要在有流量时才会被激活,当前是DOWN
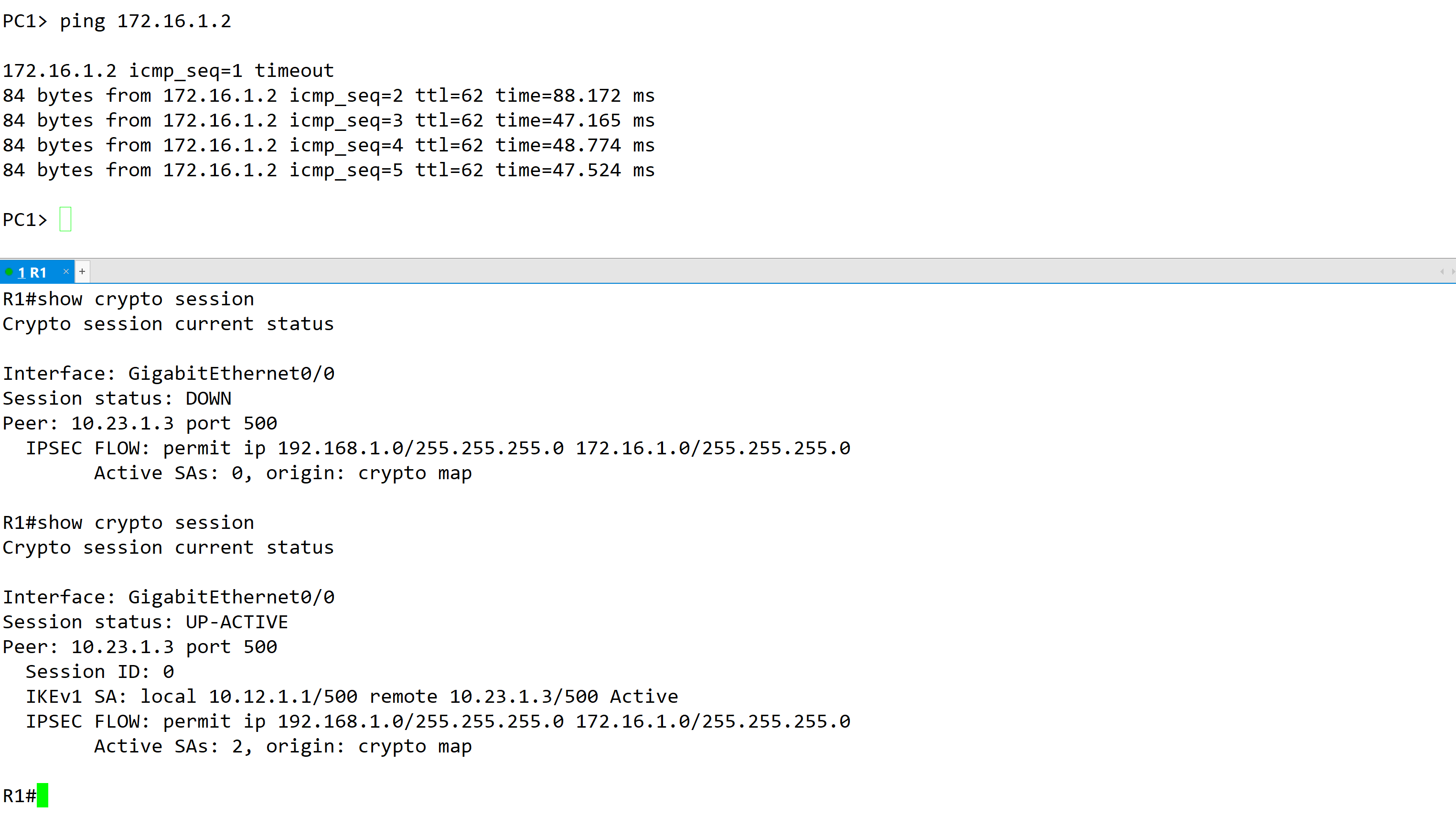
- show crypto ipsec sa —— 查看Phase2 的结果
- Proxy-ID
- 数据包数量
- 建立IPsec 的地址/端口
- inbound 和 outbound SA
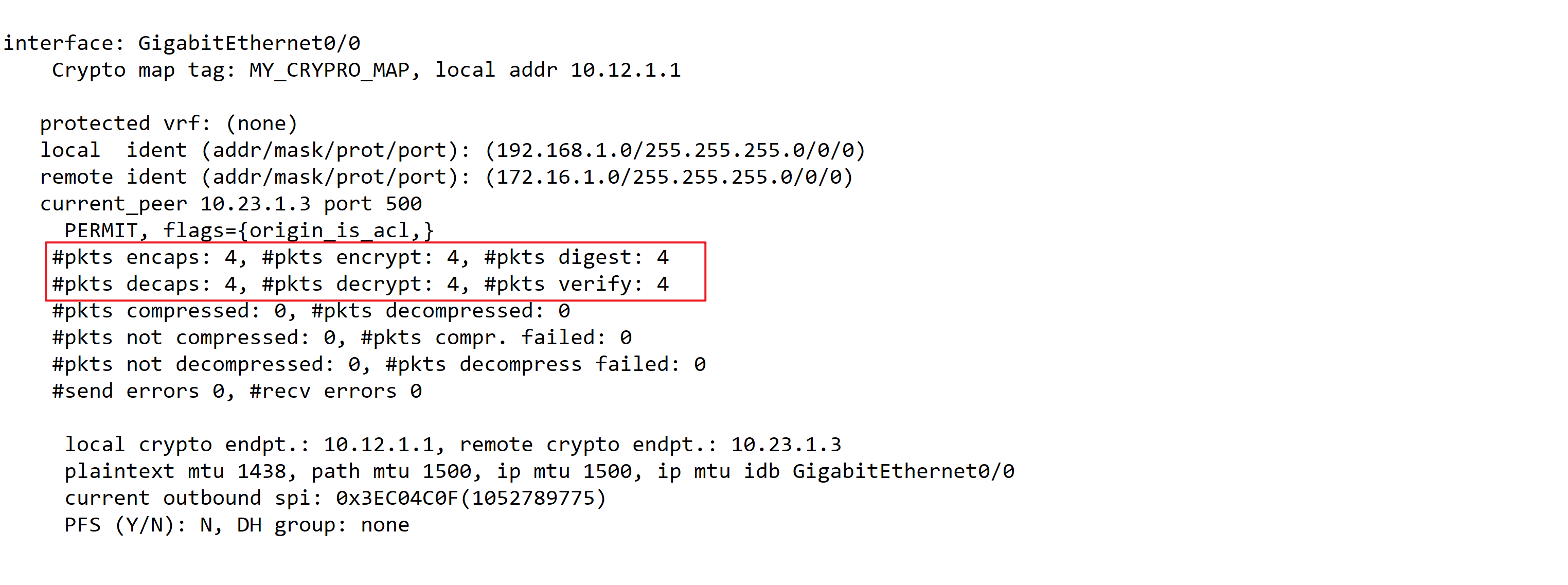
- show crypto isakmp sa —— 查看Phase1 的结果。此时状态为QM_IDLE (Phase 2的状态)
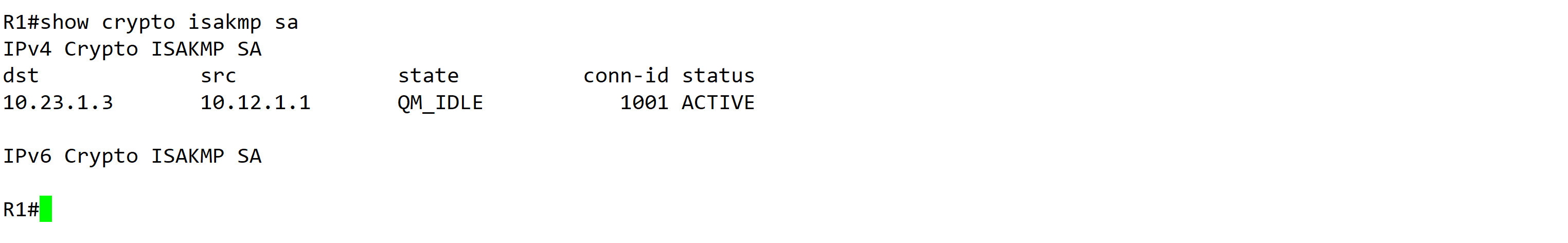
- 我们在R3 上修改key 为 CISOC123,然后清理下缓存 (clear crypto session),就可以看到网络断开。