拓扑
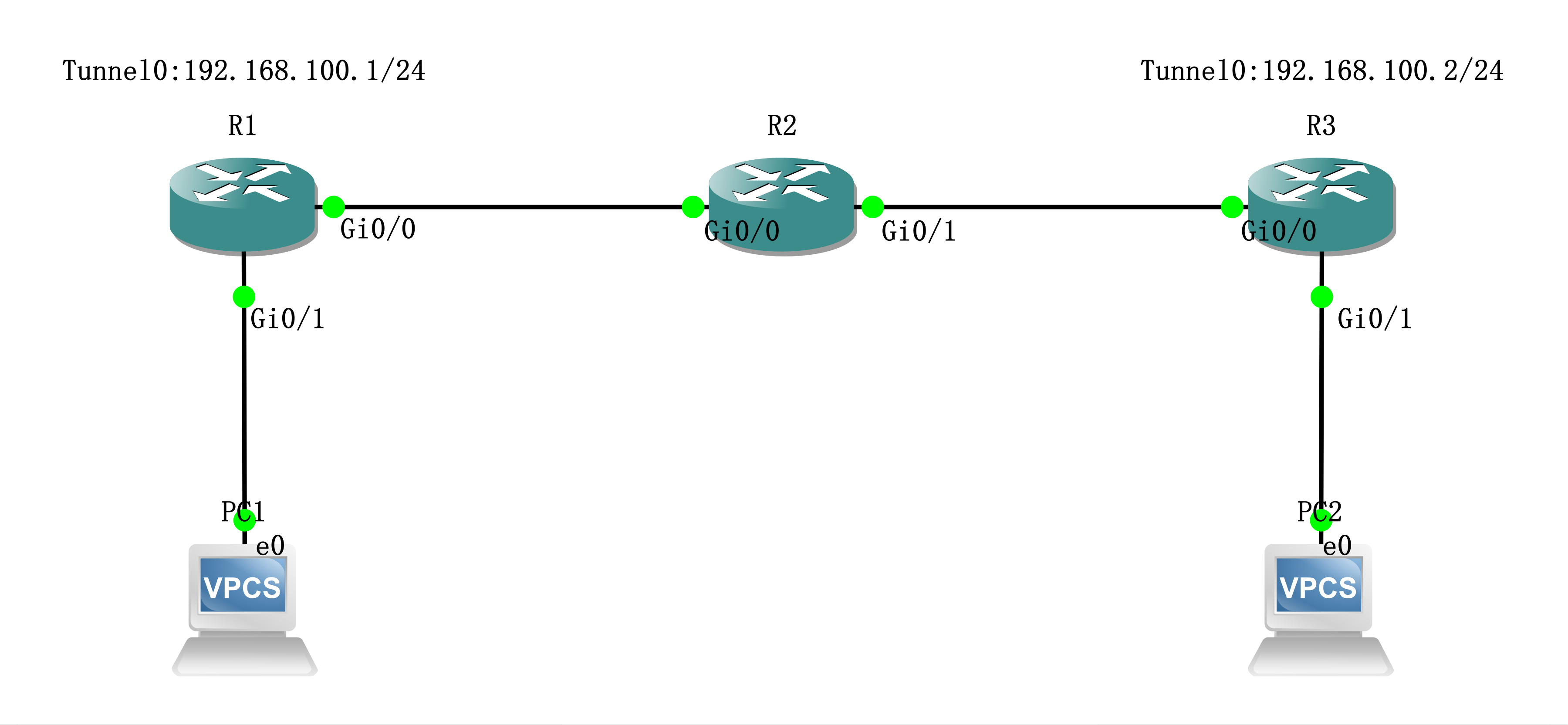
步骤
IPsec
!!!!!!!!R1crypto isakmp policy 1 encr aes 256 hash sha256 authentication pre-share group 5crypto isakmp key CISCO address 10.23.1.3 crypto ipsec transform-set VPN_TS esp-aes 256 esp-sha256-hmac mode tunnelcrypto map MY_CRYPTO 10 ipsec-isakmp set peer 10.23.1.3 set transform-set VPN_TS match address VPN_TRAFFIC crypto map MY_CRYPTO!!!!!!!!!R3crypto isakmp policy 1 encr aes 256 hash sha256 authentication pre-share group 5crypto isakmp key CISCO address 10.12.1.1 crypto ipsec transform-set VPN_TS esp-aes 256 esp-sha256-hmac crypto map MY_CRYPTO 10 ipsec-isakmp set peer 10.12.1.1 set transform-set VPN_TS match address VPN_TRAFFIC!!!!!ip access-list extended VPN_TRAFFIC permit ip host 10.23.1.3 host 10.12.1.1!!!!!interface GigabitEthernet0/0 crypto map MY_CRYPTO
GRE Tunnel
interface Tunnel0 ip address 192.168.100.2 255.255.255.0 tunnel source GigabitEthernet0/0 tunnel destination 10.12.1.1end
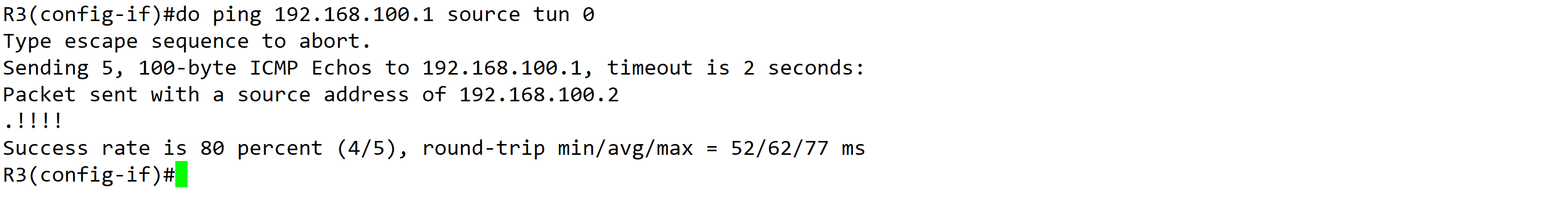
整体验证
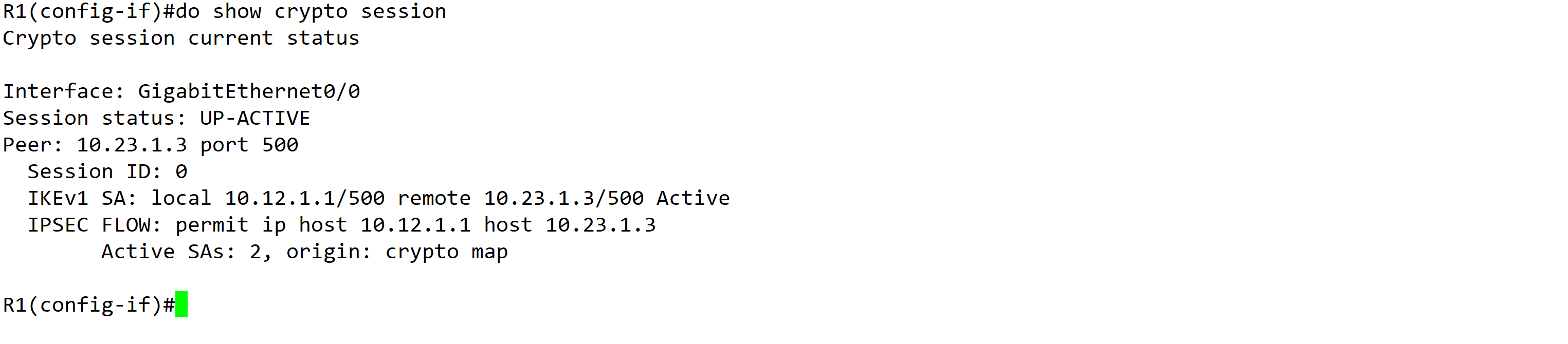
- 查看Ipsec Session:show crypto session
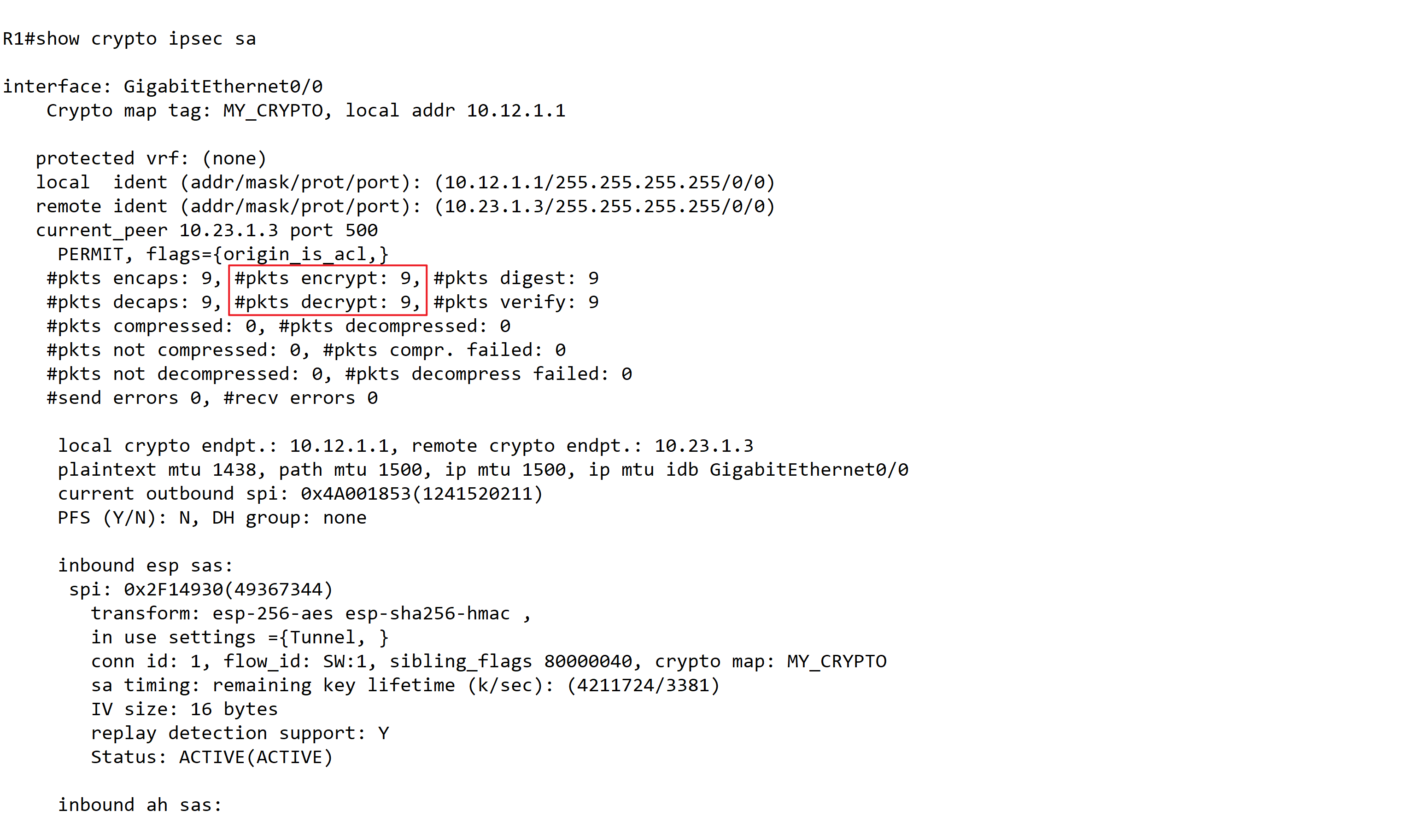
- 查看ipsec sa :show crypto ipsec sa
- 可以看到9个数据包被加密—— 执行了2次ping,第1次5个包,第2次4个包。这样就证明GRE 经过了IPsec
- 将R1、R3 的 Tunnel 端口 ,以及和终端相连的接口开启OSPF。可以看到R1 和R3之间通过Tunnel 建立了OSPF,并且通过Tunnel 学到了和终端连接的网络路由

- 此时可以在PC1 上 Ping PC2,并在R1上查看 ipsec sa






