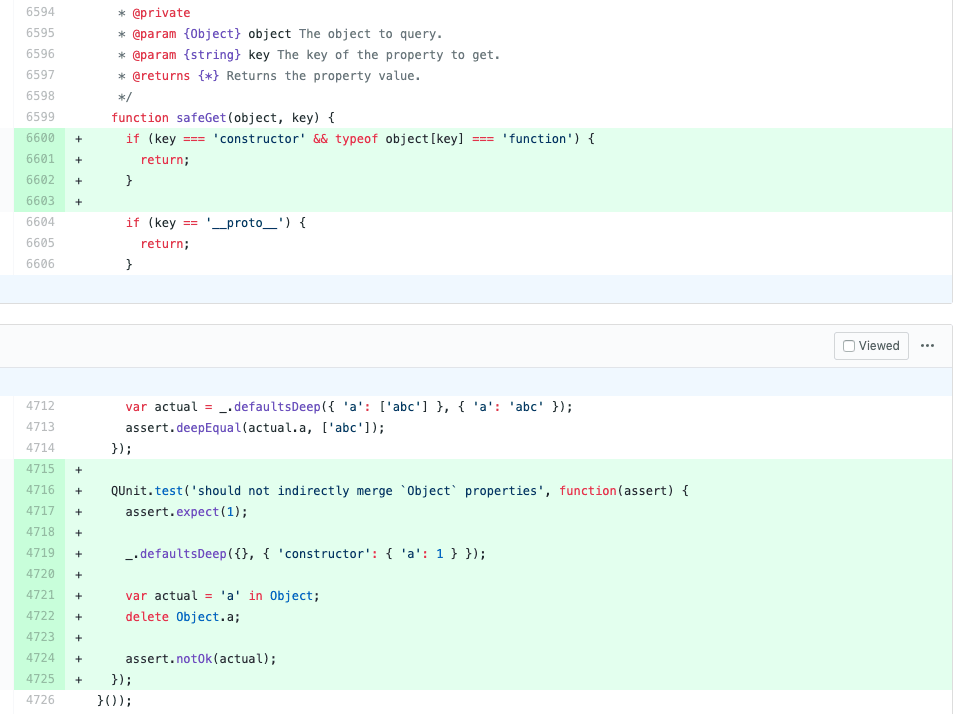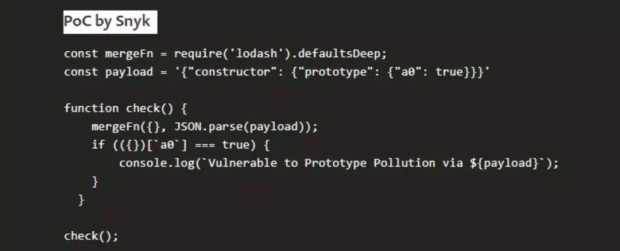
原型污染就是指攻击者通过某种手段修改 JavaScript 对象的 prototype。
只有在下面3个条件同时满足时,漏洞利用才会发生:
- 对象递归合并
- 属性通过路径定义
- 对象克隆
'use strict';const express = require('express');const bodyParser = require('body-parser')const cookieParser = require('cookie-parser');const path = require('path');const isObject = obj => obj && obj.constructor && obj.constructor === Object;function merge(a, b) {for (var attr in b) {if (isObject(a[attr]) && isObject(b[attr])) {merge(a[attr], b[attr]);} else {a[attr] = b[attr];}}return a}function clone(a) {return merge({}, a);}// Constantsconst PORT = 8080;const HOST = '0.0.0.0';const admin = {};// Appconst app = express();app.use(bodyParser.json())app.use(cookieParser());app.use('/', express.static(path.join(__dirname, 'views')));app.post('/signup', (req, res) => {var body = JSON.parse(JSON.stringify(req.body));var copybody = clone(body)if (copybody.name) {res.cookie('name', copybody.name).json({"done": "cookie set"});} else {res.json({"error": "cookie not set"})}});app.get('/getFlag', (req, res) => {var аdmin = JSON.parse(JSON.stringify(req.cookies))if (admin.аdmin == 1) {res.send("hackim19{}");} else {res.send("You are not authorized");}});app.listen(PORT, HOST);console.log(`Running on http://${HOST}:${PORT}`);