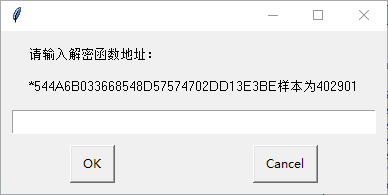
IDA
代码
将函数传入的参数指针,取值后Xor3计算的结果,作为返回值的重命名参数: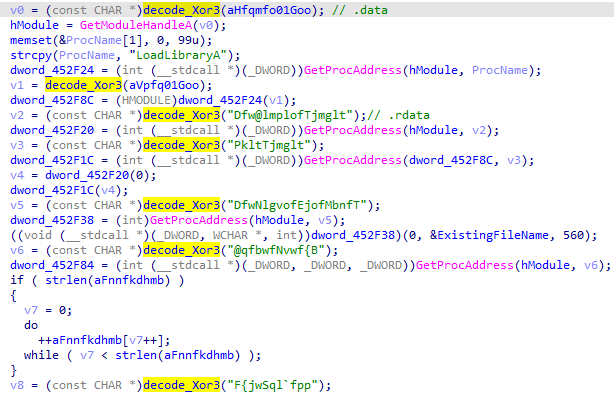
汇编
取“push offset [地址]”中地址保存的值,Xor 3: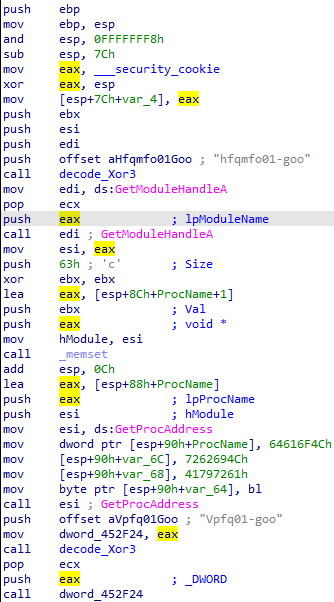
IDA Python
文件:544A6B033668548D57574702DD13E3BE
import idcimport idaapiimport easyguidef GetAdd_StrXored3(addr):# prev_head:获取上一行汇编addr = prev_head(addr)# print_insn_mnem:获取操作符# print_operand:获取操作数if print_insn_mnem(addr) == "push" and "offset" in print_operand(addr,0):#get_operand_value:获取操作值return get_operand_value(addr,0)else:return 0def GetStr_Xored3(addr):outChar = ""while(True):byte = idaapi.get_byte(addr)if byte != 0:outChar += chr(byte)else:breakaddr += 1return outChardef GetStr_Decoded(str):#加密Key值key = 3i = 0outChar = ""length = len(str)while i < length:outChar += chr(ord(str[i]) ^ key)i += 1return outCharif __name__ == '__main__':strFunction = easygui.enterbox("请输入解密函数地址:\r\n*544A6B033668548D57574702DD13E3BE样本为402901")addFunction = int(strFunction, 16)print("解密函数地址:", hex(addFunction).upper()[2:])for x in XrefsTo(addFunction, flags = 0):addStrXored3 = GetAdd_StrXored3(x.frm)if addStrXored3 != 0:strXored3 = GetStr_Xored3(addStrXored3)strDecoded = GetStr_Decoded(strXored3)print("加密 | 解密:", strXored3, " | ", strDecoded)set_cmt(prev_head(x.frm), strDecoded, 0)else:continueprint("结束")
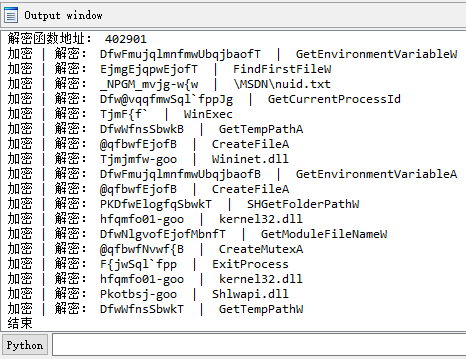
运行
打印
找BUG
个数不对,总共35处调用,打印结果是18个。
打印出交叉引用的函数地址和参数地址,发现有多个参数地址为0值: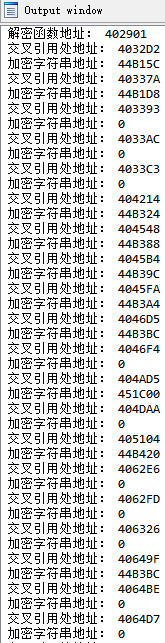
汇编代码不同
即使是同一个函数,但是传输传递的方式有可能不同,该样本传递的参数有两种传参方式。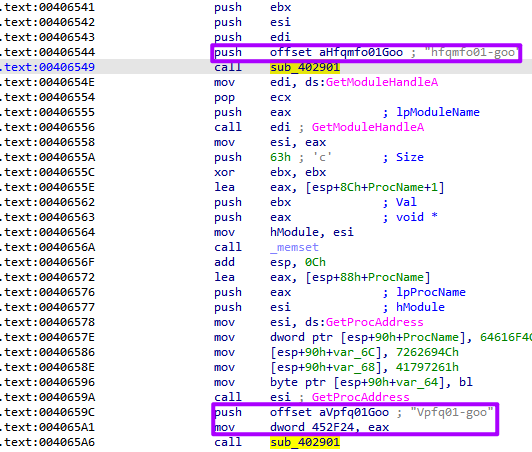
解决方案
对操作符为mov的上一行汇编,再取上一行地址。