TryHackMe | Cyber Security Training
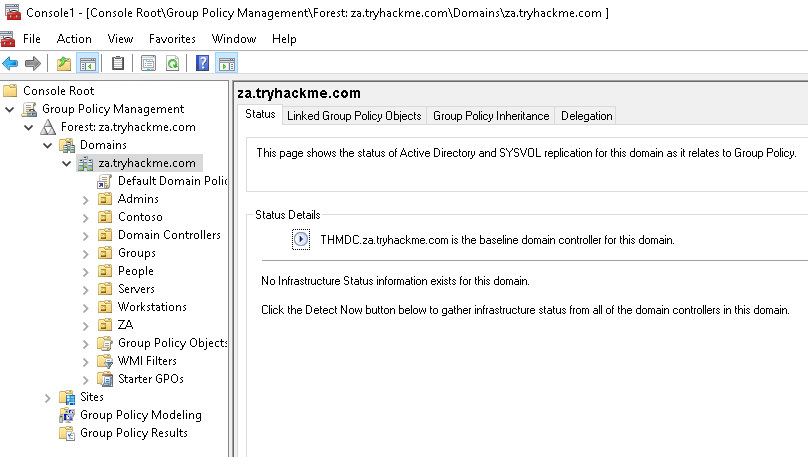
在该示例中我们有与一个账户具有对 GPO 所有权,此外,该 CPO 可用于我们的 THMSERVER2 机器:

加入域的计算机会定期从 STYSVOL 来提权所有策略并进行应用。
我们使用 RDP 连接到 THMWARK1:
C:\> xfreerdp /v:thmwrk1.za.tryhackme.loc /u:username /p:'password'
当连接到目标后,我们直接下方命令:
C:\> runas /netonly /user:za.tryhackme.loc\svcServMan cmd.exeC:\> mmc.exe
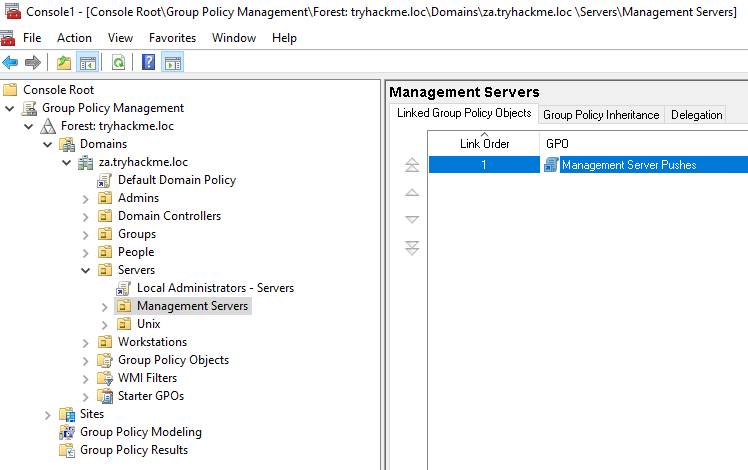
打开 MMC 后,我们先添加管理单元:
- Click File -> Add/Remove Snap-in
- Select the Group Policy Management snap-in and click Add
- Click Ok
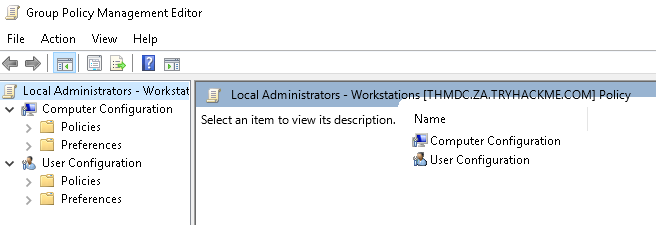
- 打开 Computer Configuration
- Expand Policies
- Expand Windows Settings
- Expand Security Settings
- Right Click on Restricted Groups and select Add Group (If the IT Support group already exists, it means someone has already performed the exploit. You can either delete it to create it yourself, or just inspect it to see what was configured.)
- Click Browse,** enter IT Support and click Check Names**
- Click Okay twice
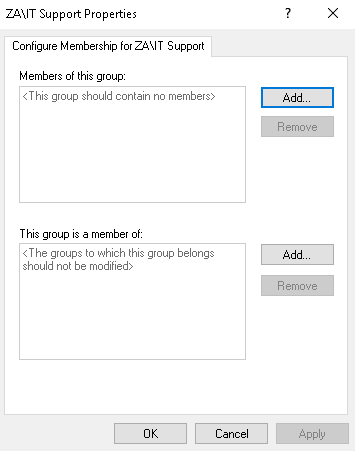
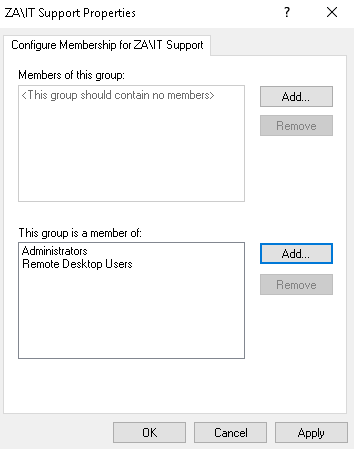
配置完成后,我们可以点击Apply和OK 。现在,我们需要做的就是等待足够的时间来应用GPO 。在此之后,我们成为IT 支持组成员的初始帐户现在将拥有THMSERVER2 的管理和RDP权限!

