Victim 为含有漏洞的智能合约,在 Rinkeby 测试网络的合约地址为:0x68D28fE315E6A344029D42915Fbc7af4261AB833接口为:contract Victim {function withdraw() public returns (string memory ){return "ISCC{xxxxx}";}}请编写攻击合约,实现对 Victim 的攻击,获取 flag。
也是给了个合约地址,继续访问https://rinkeby.etherscan.io/,搜索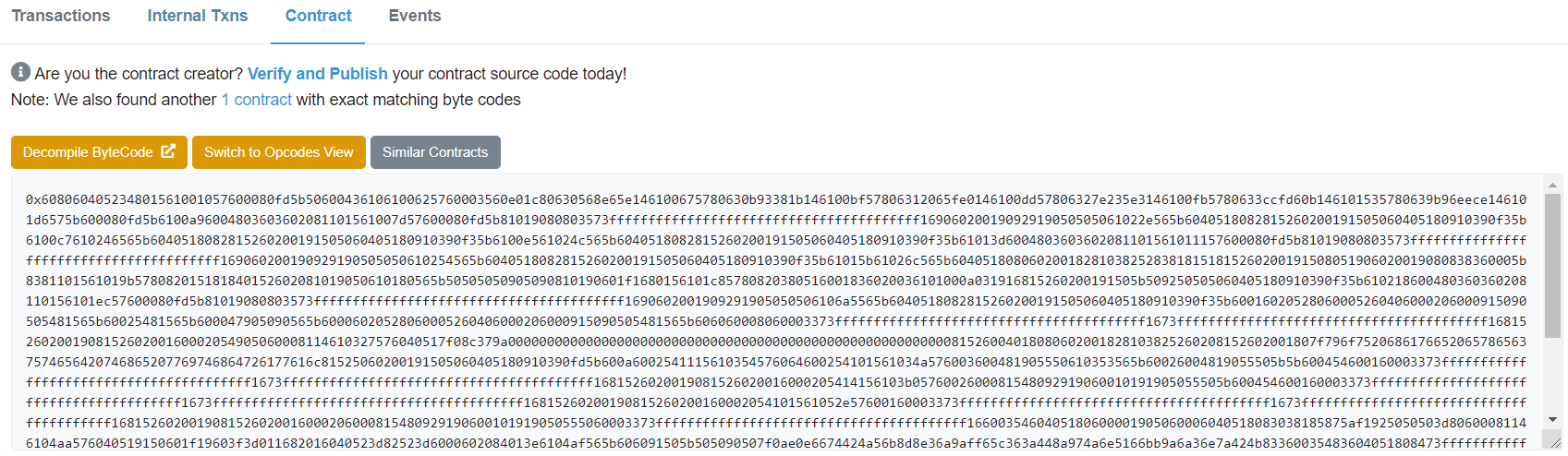
在contract中点击decompile bytecode,反编译出来代码,拿到flag
## Panoramix v4 Oct 2019# Decompiled source of rinkeby:0x68D28fE315E6A344029D42915Fbc7af4261AB833## Let's make the world open source### I failed with these:# - getBalance()# All the rest is below.#def storage:balances is mapping of uint256 at storage 0unknown0568e65e is mapping of uint256 at storage 1success is uint256 at storage 2stor3 is uint256 at storage 3stor4 is uint256 at storage 4def unknown0568e65e(addr _param1) payable:require calldata.size - 4 >= 32return unknown0568e65e[_param1]def success() payable:return successdef balances(address _param1) payable:require calldata.size - 4 >= 32return balances[_param1]def getBalanceOf(address _address) payable:require calldata.size - 4 >= 32return balances[addr(_address)]## Regular functions#def _fallback() payable: # default functionrevertdef withdraw() payable:if balances[caller]:revert with 0, 'you have executed the withdrawal'if success > 10:if success >= 100:stor4 = 2else:stor4 = 3if unknown0568e65e[caller] == stor4:success++if unknown0568e65e[caller] < stor4:unknown0568e65e[caller]++call caller with:value stor3 weigas gas_remaining weilog 0xae0e6674: caller, stor3, bool(ext_call.success)balances[caller] = stor3 * unknown0568e65e[caller]if balances[caller] <= stor3:revert with 0, 'failed to withdraw'return 'ISCC{h@ve_fun~Re-EntRan(y}'
yysy,这两道区块链题目真的是这么做的吗

