下载下来俩文件,1和FFFL@G.cry,后者打开是乱码,前者内容如下:
[35, 8, 6, 23, 2, 34, 9, 8, 15, 17, 24, 20, 17, 0, 24, 32,5,2,0,0,2,1,0,0,0,0,8,3,0,0,5,2]
仔细观察可以发现数组的前面一部分带空格,而后面则不带,将两部分分开,正好一组16个元素,可以组成两个4x4的矩阵。
接着去搜索相关的密码,查到有可能是希尔密码,找到一个解密脚本:https://blog.csdn.net/qq_43968080/article/details/103643920
#!/usr/bin/python3.7# -*- coding: utf-8 -*-# @Time : 2019/12/11 14:53# @Author : SystemDefenser# @Email : mrwx1116@163.com# @Software: PyCharmfrom numpy import linalg# 输入矩阵并判断是否存在逆矩阵def inputMatrix():while True:# 输入一行、作为行列式的阶数和行列式的第一行rank = list(input("").split())matrix = [[0] * len(rank) for i in range(len(rank))]matrix[0] = rank# 输入行列式剩余数据for i in range(1, len(matrix)):matrix[i] = list(input("").split())# 判断每一行输入是否合法if len(matrix[i]) != len(matrix):print("输入有误,重新输入。")continue# 转换字符型为整型for i in range(len(matrix)):matrix[i] = list(map(lambda x: int(x), matrix[i]))# 判断是否存在逆矩阵if not judgeInverse(matrix):print("矩阵不存在逆矩阵,重新输入。")continuereturn matrix# 判断是否存在逆元def judgeInverse(matrix):try:linalg.inv(matrix)except:return Falsereturn True# 生成密钥(矩阵的逆矩阵)def createMatrixInverse(matrix):try:matrix_inverse = linalg.inv(matrix)except:return -1return matrix_inverse# 生成消息分组def createMassageList(massage, matrix):matrixRank = len(matrix)massageList = []# 扩充消息序列并创建分组while len(massage) % matrixRank != 0:massage += " "for i in range(1, len(massage) + 1, matrixRank):massageList.append(massage[i-1:i + matrixRank - 1])return massageList# 字母序列转化为数字def letterToDigit(massageList):massageDigitList = [] # 替换后的数字列表letterList = [] # 字母列表for i in range(ord("a"), ord("z") + 1):letterList.append(chr(i))for i in range(10):letterList.append(str(i))# 添加空格,解决分组填充问题letterList.append(" ")# 替换字母为数字for massage in massageList:listTmp = []for i in range(len(massage)):listTmp.append(letterList.index(massage[i]))massageDigitList.append(listTmp)return massageDigitList# 数字序列转化为字母def digitToLetter(massageList):massageLetterList = [] # 还原后的字母列表letterList = []for i in range(ord("a"), ord("z") + 1):letterList.append(chr(i))for i in range(10):letterList.append(str(i))letterList.append(" ")# 替换数字为字母for massage in massageList:massageLetterList.append(letterList[massage % 37])return massageLetterList# 加密def encrypt(massage, matrix):ciphertextList = [] # 加密结果列表massageList = createMassageList(massage, matrix)massageDigitList = letterToDigit(massageList)# 矩阵相乘for massageDigit in massageDigitList:for i in range(len(massageDigit)):sum = 0for j in range(len(massageDigit)):sum += massageDigit[j] * matrix[j][i % len(matrix)]ciphertextList.append(sum % 37)return ciphertextList# 解密def decrypt(massage, matrix):plaintextList = [] # 解密结果列表matrix_inverse = createMatrixInverse(matrix)massageList = createMassageList(massage, matrix)# 矩阵相乘for msg in massageList:for i in range(len(msg)):sum = 0for j in range(len(msg)):sum += msg[j] * matrix_inverse[j][i % len(matrix)]plaintextList.append(sum % 37)# 浮点型转换为整型(采用四舍五入——round())plaintextList = list(map(lambda x: int(round(x)), plaintextList))plaintextList = digitToLetter(plaintextList) # 数字转换为字母plaintext = ""for item in plaintextList:plaintext += itemreturn plaintextif __name__ == "__main__":while True:print("—————希尔密码—————")choice = input("1、加密 2、解密\n请选择:")if choice == "1":print("输入矩阵:")matrix = inputMatrix()massage = input("输入msg:")massageList = createMassageList(massage, matrix)ciphertextList = encrypt(massage, matrix)print("加密结果:", ciphertextList)elif choice == "2":massageList = list(map(int, list(input("输入密文序列:").split(","))))print("输入矩阵:")matrix = inputMatrix()matrix_inverse = createMatrixInverse(matrix)print("逆矩阵:")for item in matrix_inverse:print(item)plaintext = decrypt(massageList, matrix)print("解密结果:", plaintext)
结果:
—————希尔密码—————1、加密 2、解密请选择:2输入密文序列:35,8,6,23,2,34,9,8,15,17,24,20,17,0,24,32输入矩阵:5 2 0 02 1 0 00 0 8 30 0 5 2逆矩阵:[ 1. -2. 0. 0.][-2. 5. 0. 0.][ 0. 0. 2. -3.][ 0. 0. -5. 8.]解密结果: thisispassword
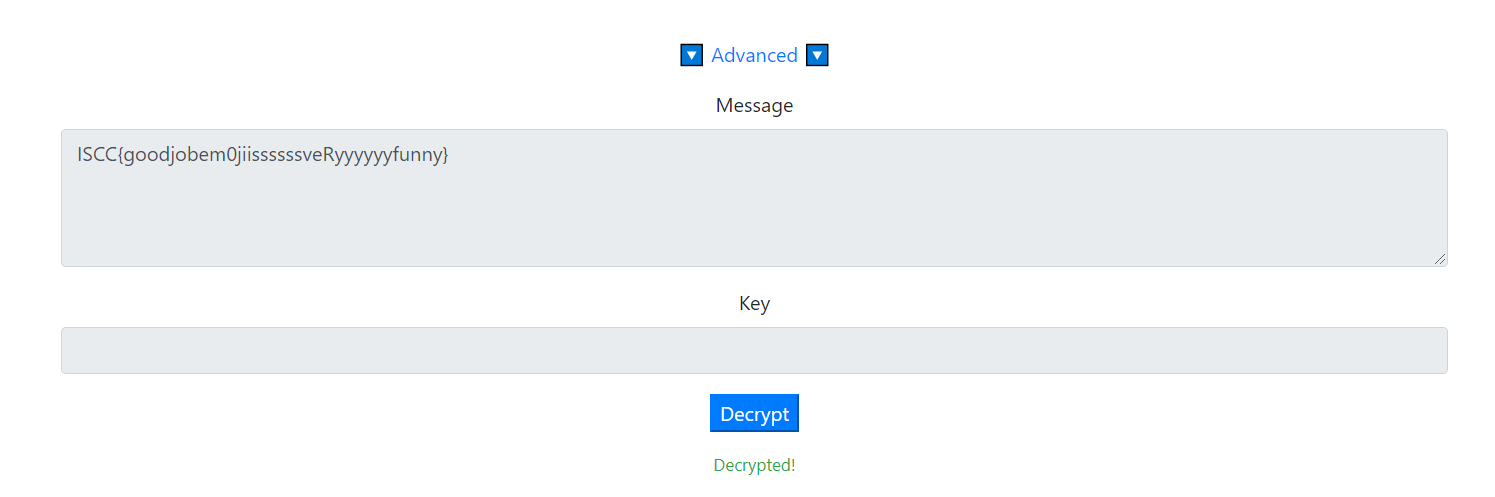
得到密码后,看另一个文件,根据文件后缀cry,猜测完整后缀名是crypto,经过查阅资料,得知需要使用软件:Encrypto打开。
打开后得到一堆emoji,使用https://aghorler.github.io/emoji-aes/解密,密钥是弱口令ISCC2021。