wireshark打开,很容易就找到了要解密的字符串: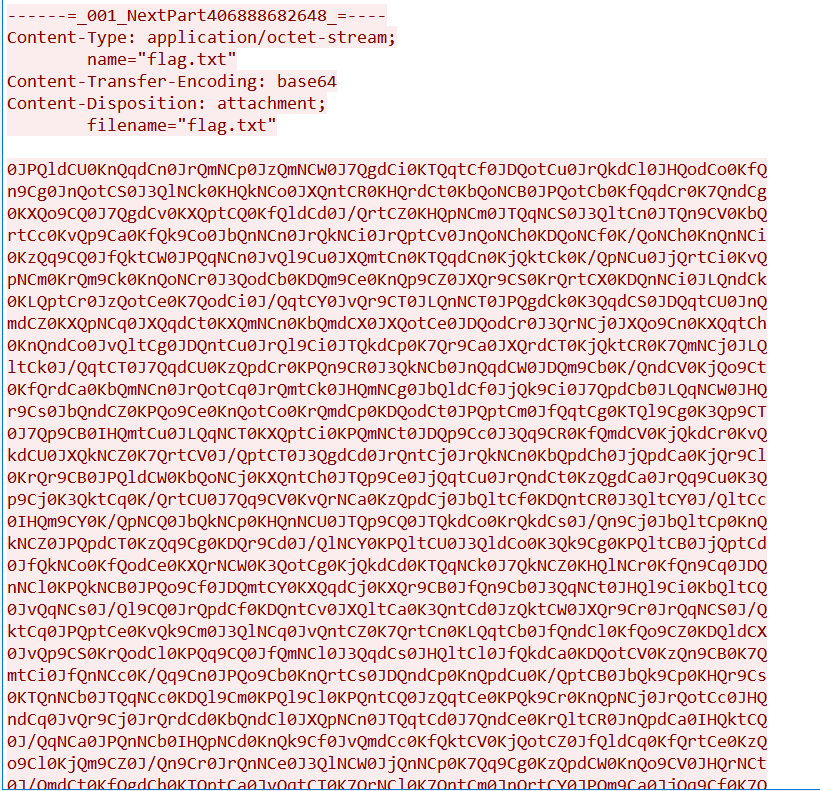
由于传送时时base64编码,所以要先base64解码: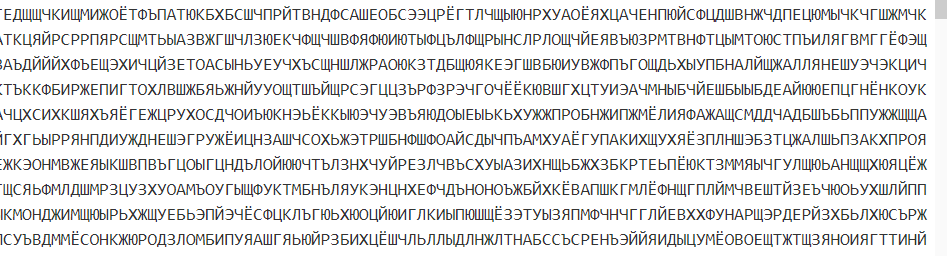
解码出来一堆俄语字母。而且正好33个
从大佬那里抄来一个脚本:
import base64from collections import Counterimport stringfrom Crypto.Util.number import *with open('flag2.txt') as f:s = f.read()s = ''.join(s.splitlines())s = base64.b64decode(s).decode()ru = 'АБВГДЕЁЖЗИЙКЛМНОПРСТУФХЦЧШЩЪЫЬЭЮЯ'ru = ''.join(ru.splitlines())base = string.digits + string.ascii_uppercase[:23]print(ru)s = s.translate(str.maketrans(ru, base))s = long_to_bytes(int(s, 33))with open('gao.png', 'wb') as f:f.write(s)
0~W分别对应俄语的33个字母。
运行脚本得到一张图片
暂时看不出来是什么东西。
010 editor打开后末尾写了5px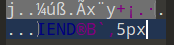
脚本:
from PIL import Imageimg = Image.open("gao.png")width,height = img.size[0],img.size[1]img2 = Image.new('RGB',(1000,1000))w1 = 0for w in range(1,width,10):b = (w,0,w+5,height)re = img.crop(b)img2.paste(re,(w1,0))img2.save('tmp.png')w1 = w1 +5img2.save("flag.png")

