- Enterprise Evaluation 2020">Enterprise Evaluation 2020
- 威胁棱镜 - MITRE ATT&CK 第三轮评估结果发布》">中文解说:《威胁棱镜 - MITRE ATT&CK 第三轮评估结果发布》
Enterprise Evaluation 2020
结果
ATT&CK 技术范围导航器
{"name": "Carbanak+FIN7","version": "2.2","domain": "mitre-enterprise","description": "","filters": {"stages": ["act"],"platforms": ["Windows","Linux","macOS"]},"sorting": 0,"viewMode": 0,"hideDisabled": false,"techniques": [{"techniqueID": "T1138","tactic": "persistence","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1110","tactic": "credential-access","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1088","tactic": "privilege-escalation","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1116","tactic": "defense-evasion","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1043","tactic": "command-and-control","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1175","tactic": "execution","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1090","tactic": "command-and-control","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1003","tactic": "credential-access","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1002","tactic": "exfiltration","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1022","tactic": "exfiltration","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1074","tactic": "collection","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1005","tactic": "collection","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1140","tactic": "defense-evasion","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1480","tactic": "defense-evasion","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1106","tactic": "execution","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1041","tactic": "exfiltration","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1179","tactic": "persistence","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1179","tactic": "credential-access","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1056","tactic": "collection","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1036","tactic": "defense-evasion","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1170","tactic": "execution","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1135","tactic": "discovery","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1010","tactic": "discovery","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1050","tactic": "privilege-escalation","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1050","tactic": "persistence","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1027","tactic": "defense-evasion","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1086","tactic": "execution","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1047","tactic": "execution","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1057","tactic": "discovery","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1093","tactic": "defense-evasion","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1055","tactic": "defense-evasion","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1055","tactic": "privilege-escalation","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1038","tactic": "privilege-escalation","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1060","tactic": "persistence","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1076","tactic": "lateral-movement","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1105","tactic": "command-and-control","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1018","tactic": "discovery","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1053","tactic": "execution","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1113","tactic": "collection","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1064","tactic": "execution","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1035","tactic": "execution","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1045","tactic": "defense-evasion","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1193","tactic": "initial-access","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1071","tactic": "command-and-control","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1032","tactic": "command-and-control","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1082","tactic": "discovery","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1016","tactic": "discovery","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1033","tactic": "discovery","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1204","tactic": "execution","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1078","tactic": "privilege-escalation","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1497","tactic": "defense-evasion","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1077","tactic": "lateral-movement","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1087","tactic": "discovery","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1059","tactic": "execution","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1503","tactic": "credential-access","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1089","tactic": "defense-evasion","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1173","tactic": "execution","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1107","tactic": "defense-evasion","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1083","tactic": "discovery","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1056","tactic": "credential-access","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1112","tactic": "defense-evasion","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1202","tactic": "defense-evasion","score": 2,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1075","tactic": "lateral-movement","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1069","tactic": "discovery","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1012","tactic": "discovery","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1219","tactic": "command-and-control","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1105","tactic": "lateral-movement","score": 3,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1021","tactic": "lateral-movement","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1095","tactic": "command-and-control","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1169","tactic": "privilege-escalation","score": 1,"color": "","comment": "","enabled": true,"metadata": []},{"techniqueID": "T1078","tactic": "persistence","score": 3,"color": "","comment": "","enabled": true,"metadata": []}],"gradient": {"colors": ["#0033a0","#da291c","#ffe86c"],"minValue": 1,"maxValue": 3},"legendItems": [{"label": "Carbanak","color": "#0033a0"},{"label": "FIN7","color": "#da291c"},{"label": "Carbanak+FIN7","color": "#ffe86c"}],"metadata": [],"showTacticRowBackground": false,"tacticRowBackground": "#dddddd","selectTechniquesAcrossTactics": true}
中文解说:《威胁棱镜 - MITRE ATT&CK 第三轮评估结果发布》
MITER 每年会针对不同的攻击组织进行模拟,对参加的各个安全厂商进行评估。2021 年 4 月 20 日,MITER 发布了最新一轮的 ATT&CK 安全解决方案评估结果。这是继 2018 年测试评估检测 APT3、2019 年测试评估检测 APT29 后的第三轮评估测试,2020 年测试评估的目标是检测 Carbanak/FIN7。
本轮评估有 29 个安全厂商参加,包括 Microsoft、Cisco 等大厂;CrowdStrike、Carbon Black 等终端安全强势厂商;Bitdefender、McAfee、Symantec 等传统安全厂商等,具体如下所示:
Carbanak/FIN7 从 2013 年开始活跃,于 2018 年被跨国联合行动沉重打击后仍在活动。数年间在全球三十多个国家/地区造成了超过 10 亿欧元的损失,累计窃取了超过 1500 万张信用卡信息。
MITRE 模拟了 Carbanak/FIN7 的复杂攻击手法,评估不同安全解决方案的检测与分析能力。每个参与测评的厂商都单独提供结果,评估指标如下所示:
- 检测数量:检测总数,包括原始遥测和分析检测
- 分析覆盖:能提供额外上下文检测的子步骤数量
- 遥测覆盖:最少处理就能检测的子步骤数量
- 可见数量:可分析或遥测的子步骤数量
将各个厂商的数据整理在一起,如下所示:
| 厂商 | 检测数量 | 分析覆盖 | 遥测覆盖 | 可见数量 |
|---|---|---|---|---|
| AhnLab | 123 | 37 | 80 | 90 |
| Bitdefender | 366 | 151 | 150 | 158 |
| Check Point | 330 | 157 | 161 | 162 |
| Cisco | 160 | 42 | 112 | 122 |
| CrowdStrike | 231 | 64 | 141 | 152 |
| Cybereason | 302 | 148 | 153 | 160 |
| CyCraft | 264 | 125 | 128 | 130 |
| BlackBerry Cylance | 253 | 99 | 134 | 141 |
| Cynet | 261 | 107 | 140 | 153 |
| Elastic | 214 | 63 | 138 | 140 |
| ESET | 271 | 93 | 143 | 147 |
| Fidelis | 282 | 119 | 147 | 147 |
| FireEye | 259 | 124 | 117 | 136 |
| Fortinet | 196 | 68 | 113 | 117 |
| F-Secure | 253 | 80 | 137 | 152 |
| GoSecure | 153 | 59 | 84 | 100 |
| Malwarebytes | 187 | 85 | 99 | 116 |
| McAfee | 274 | 93 | 148 | 151 |
| Micro Focus | 146 | 82 | 56 | 122 |
| Microsoft | 356 | 134 | 148 | 151 |
| Open Text | 238 | 67 | 122 | 125 |
| Palo Alto Networks | 335 | 149 | 154 | 169 |
| ReaQta | 220 | 101 | 119 | 135 |
| SentinelOne | 333 | 159 | 164 | 174 |
| Sophos | 157 | 39 | 114 | 118 |
| Symantec | 282 | 122 | 143 | 159 |
| Trend Micro | 338 | 139 | 162 | 167 |
| Uptycs | 204 | 62 | 124 | 127 |
| VMware Carbon Black | 278 | 90 | 152 | 154 |
值得注意的是,有些 Linux 环境的子步骤因为有些厂商没有对应的 Agent 无法检测,包括 AhnLab、ESET、Fortinet、GoSecure、Malwarebytes、Open Text、Sophos。
按检测数量进行排序,如下所示: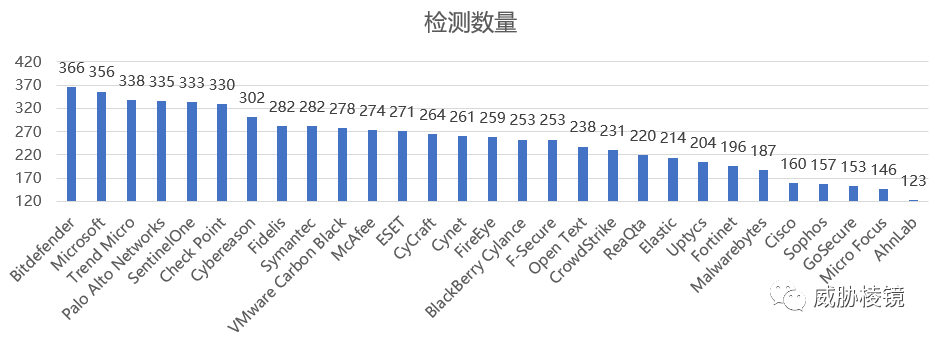
按分析覆盖进行排序,如下所示: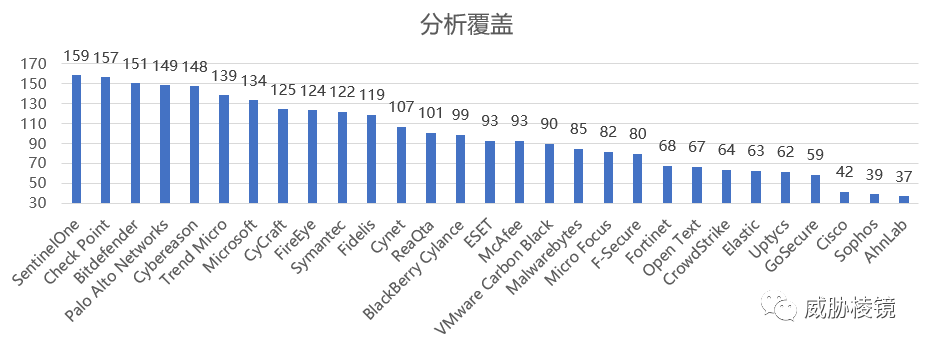
按遥测覆盖进行排序,如下所示: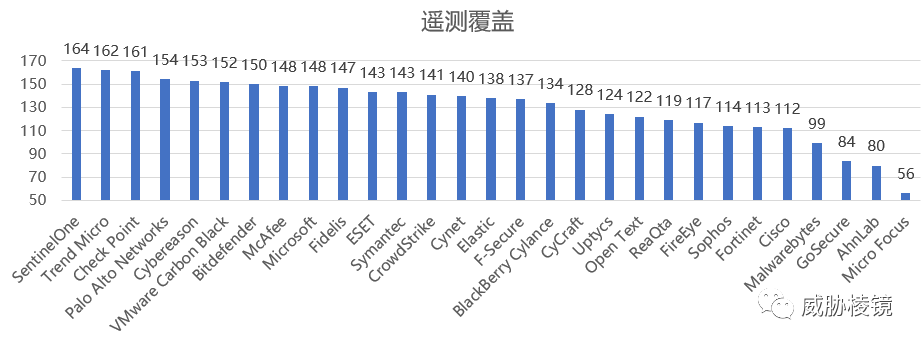
按可见数量进行排序,如下所示: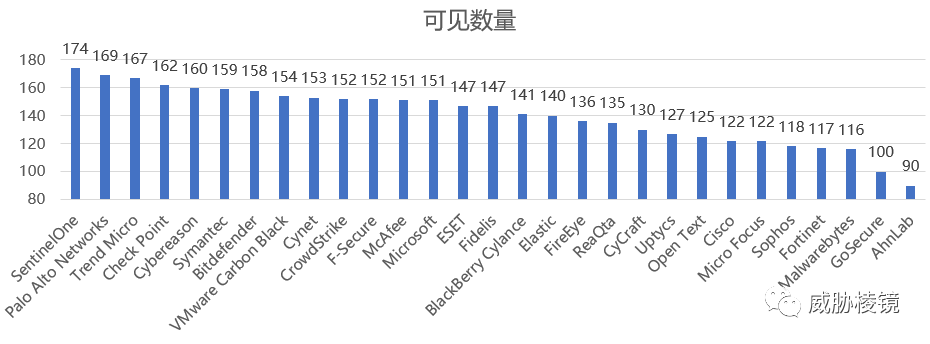
取各项的 TOP3 如下所示:
参与测评的 29 个安全厂商还是以美国的厂商为主,单是美国自己就占到了 18 家,在网络安全领域较为强势的英国和以色列紧随其后。而有些厂商缺席了本次评估测试,例如参与过此前评估的卡巴斯基未参与本次评估。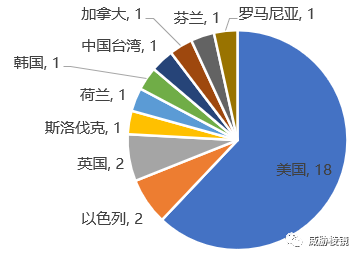
ATT&CK 的三轮评估使用了知名 APT 和黑产组织进行模拟,无论是专攻 EDR 领域的厂商还是号称能够进行高级威胁检测的厂商都可以参与评估模拟,从参加的厂商来看也是不同细分领域都有厂商参加,希望将来能有更多的国内安全厂商参与评估。
附录一
两个场景下不同阶段的检测数量如下所示,想要看具体的数字可在附录二的每个厂商的具体页面中进行查看。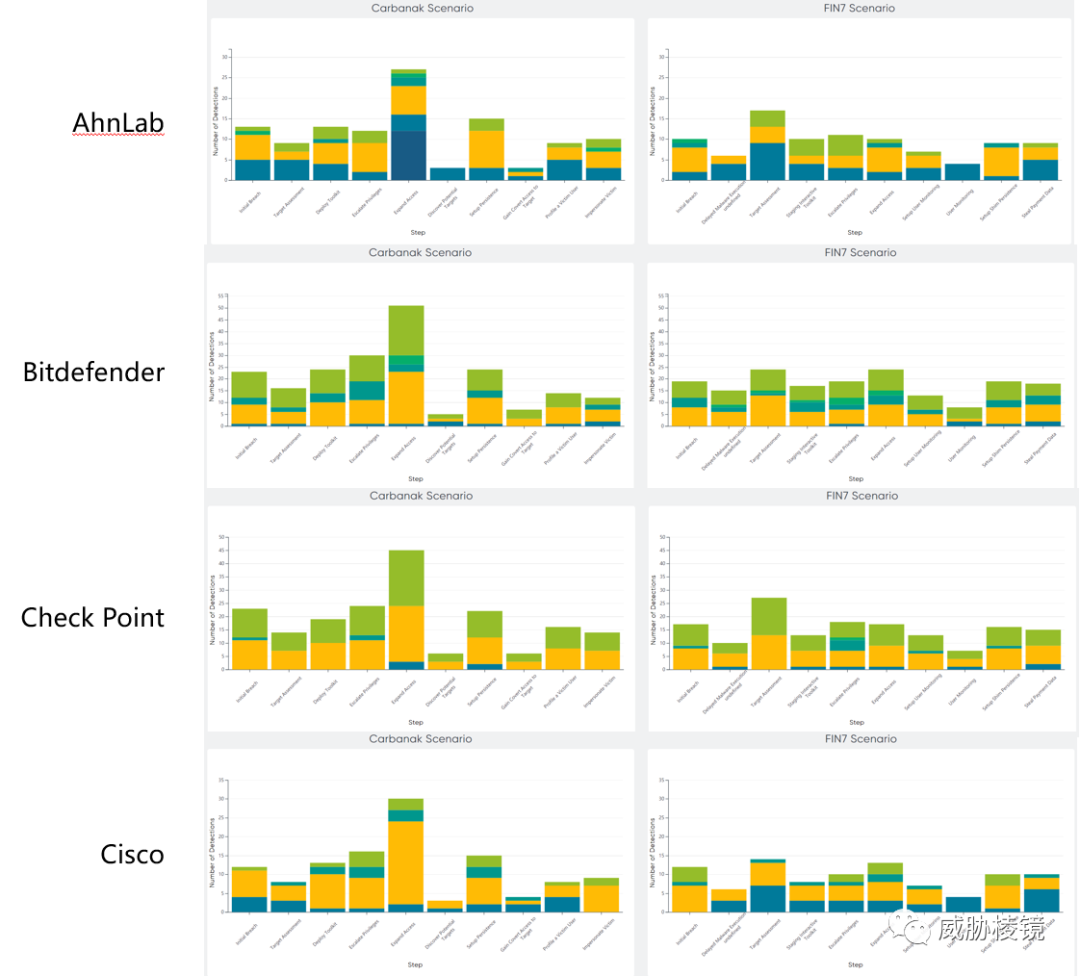
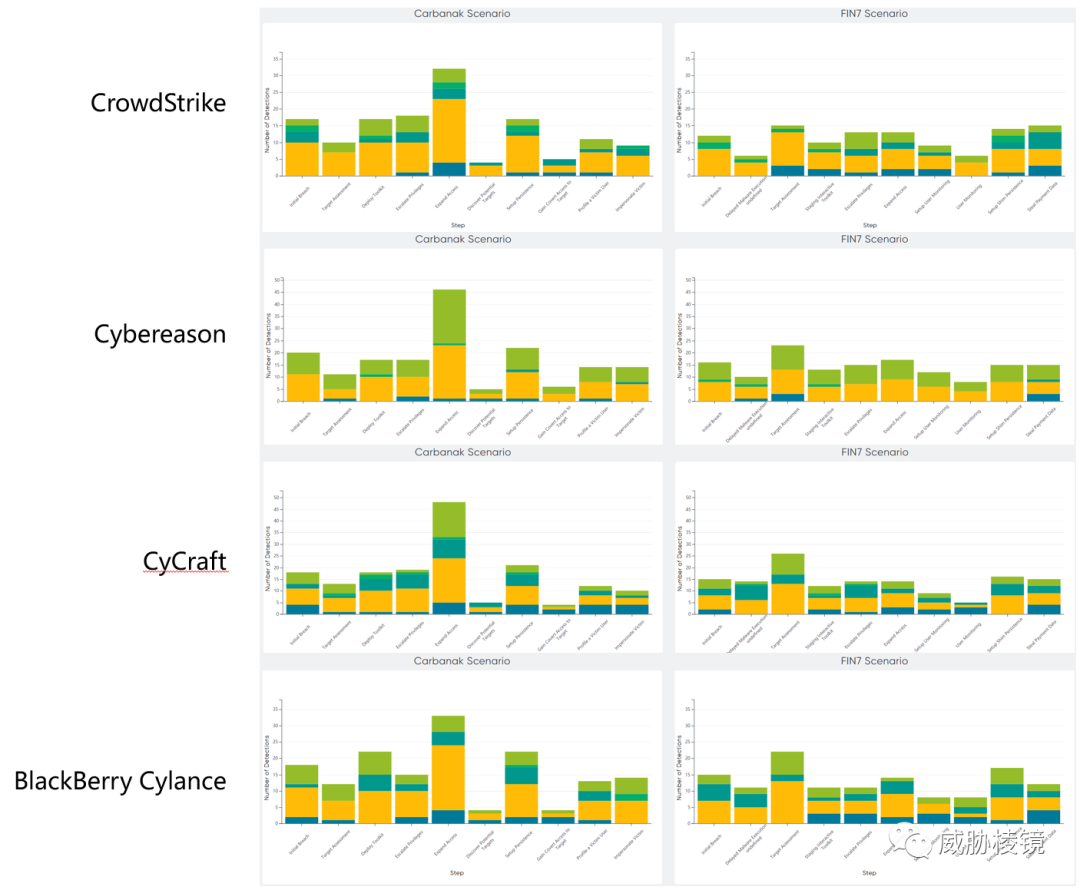
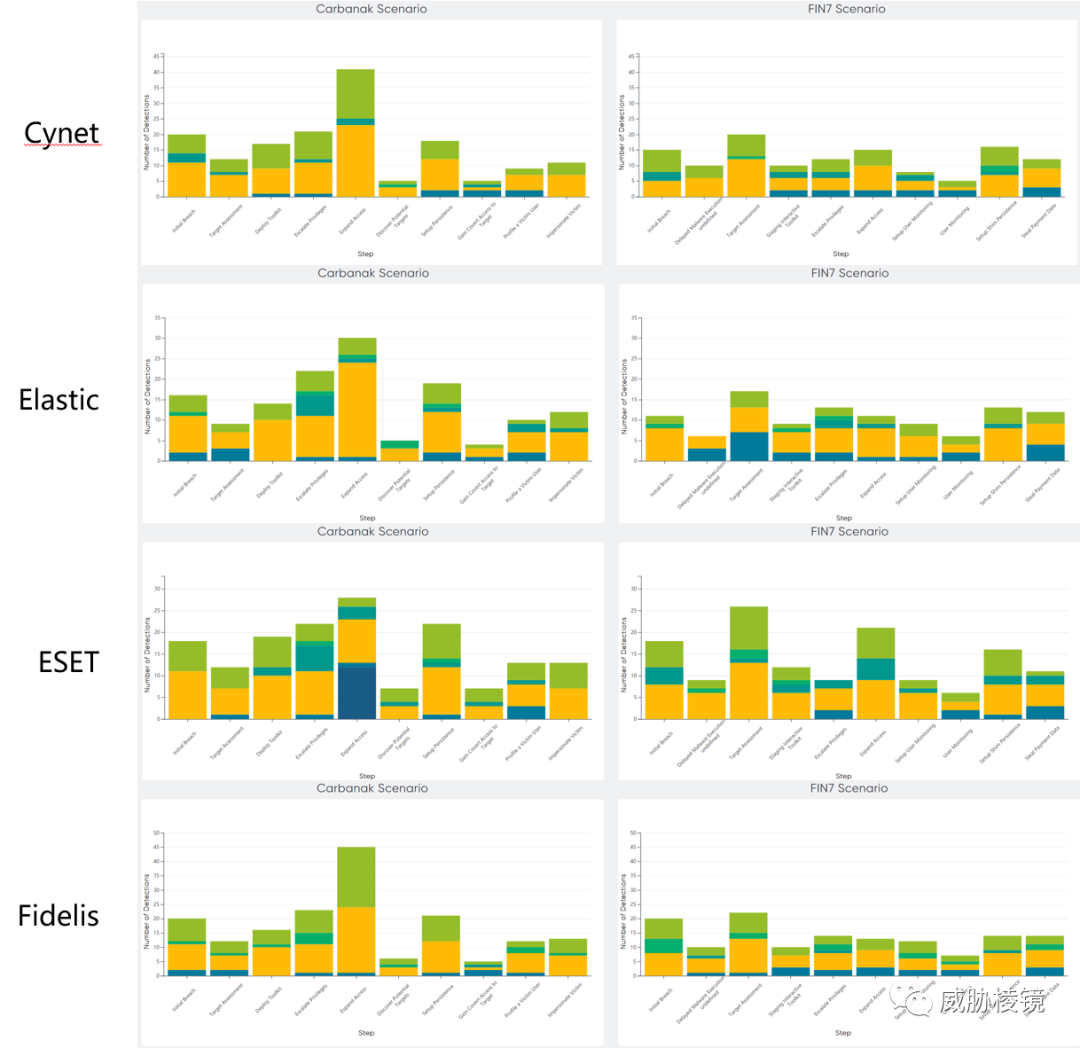
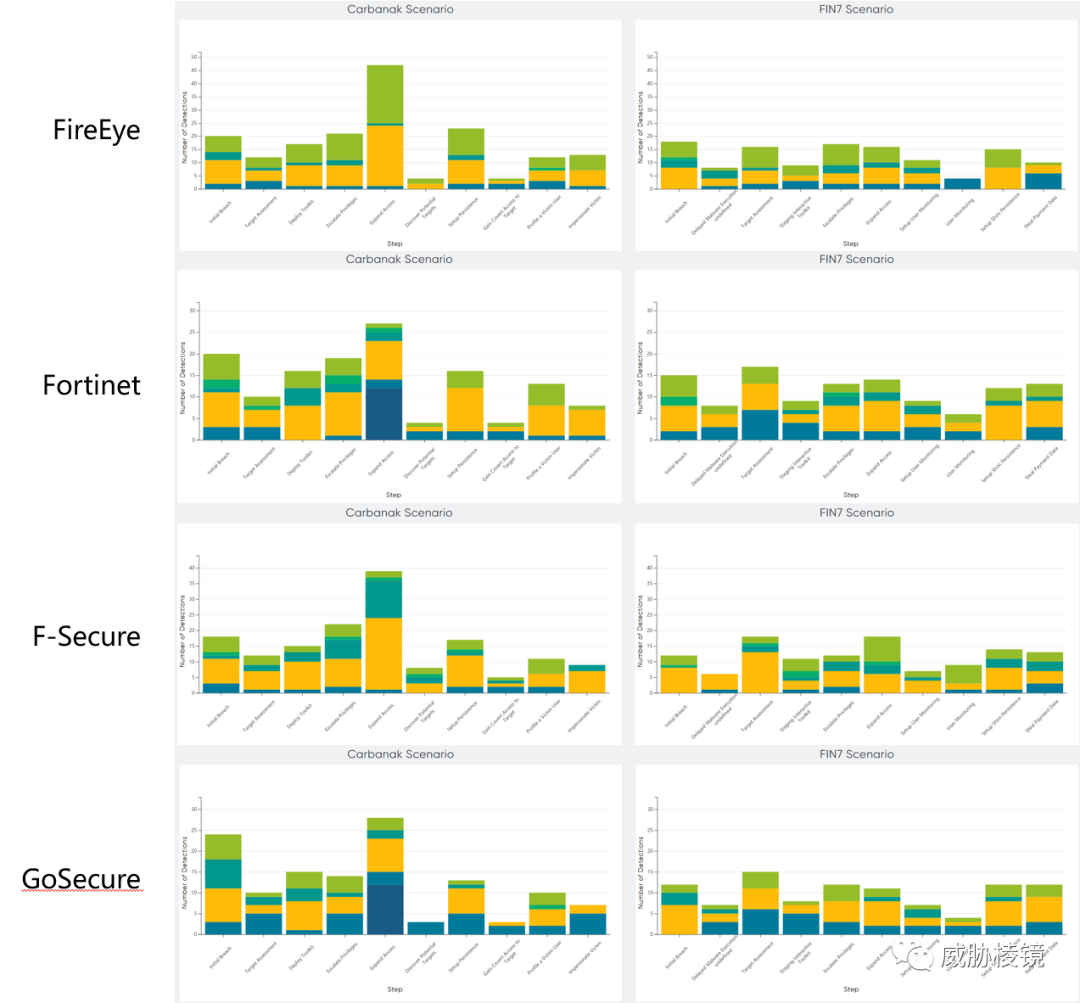
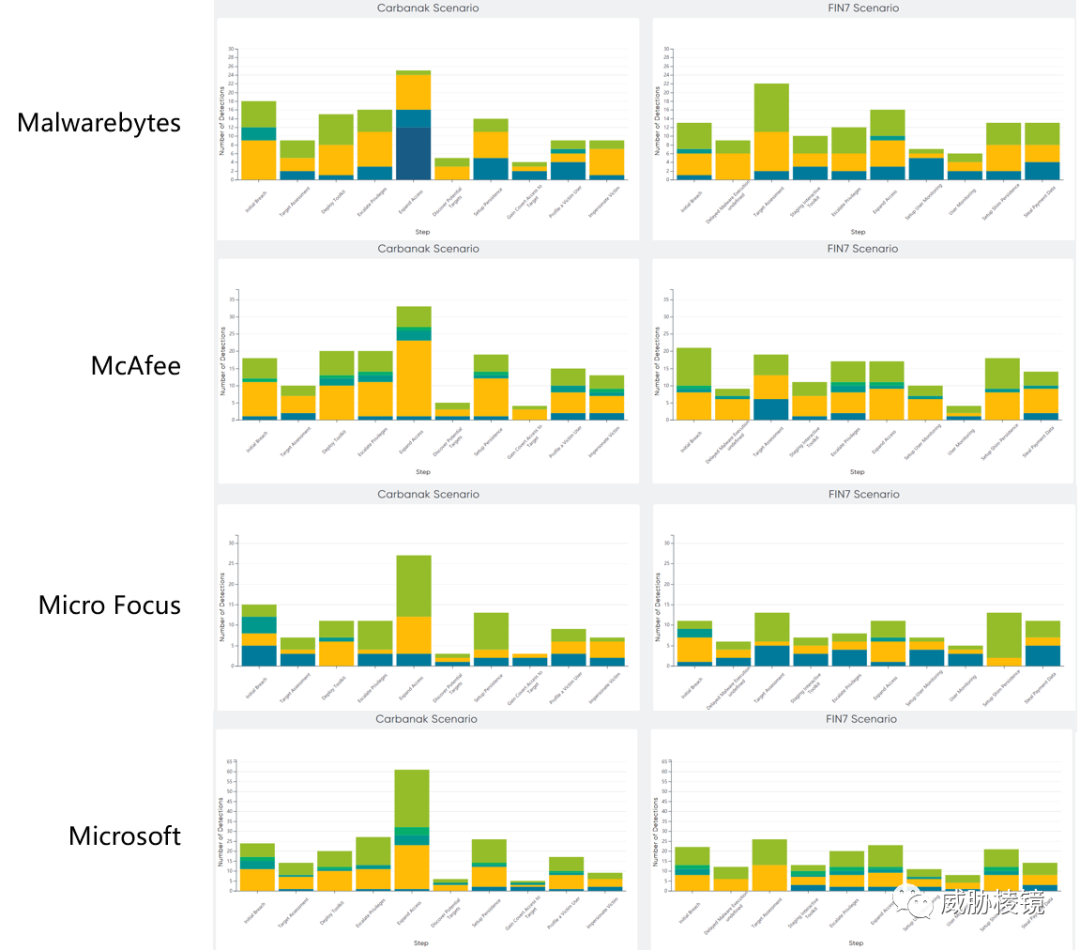
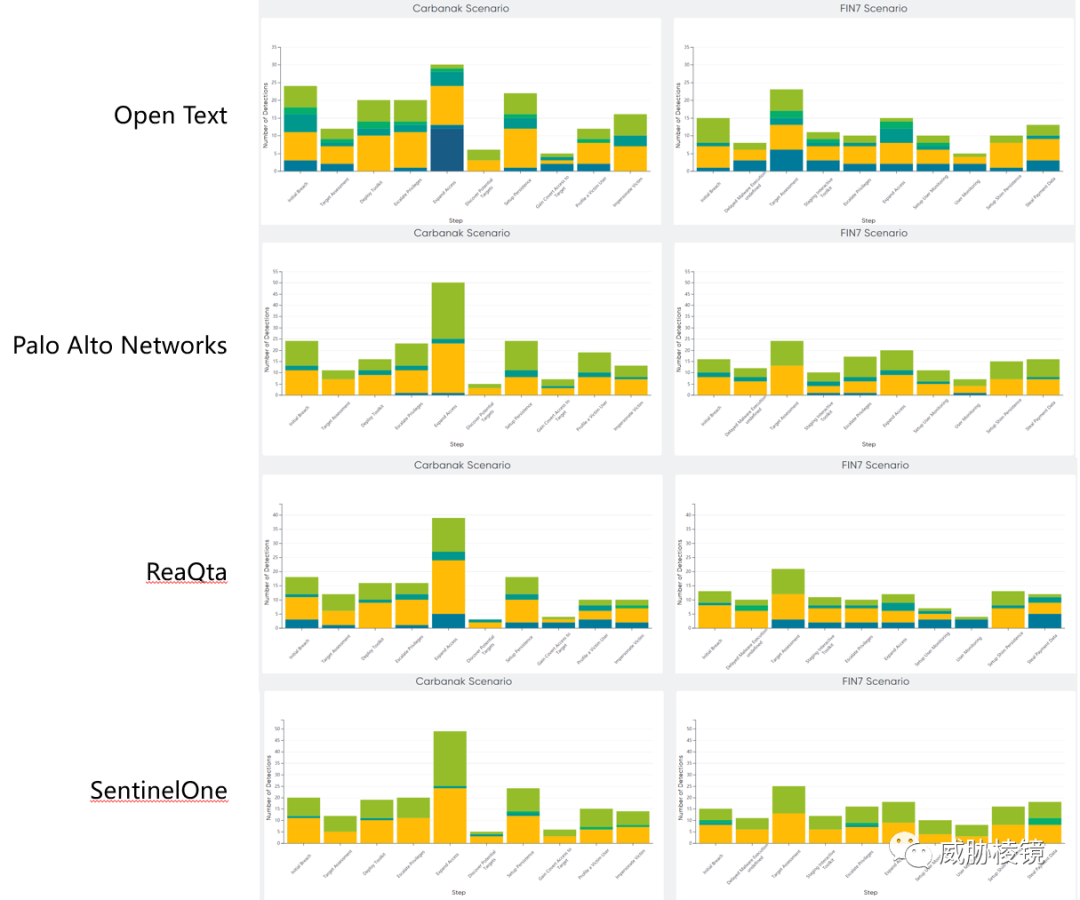
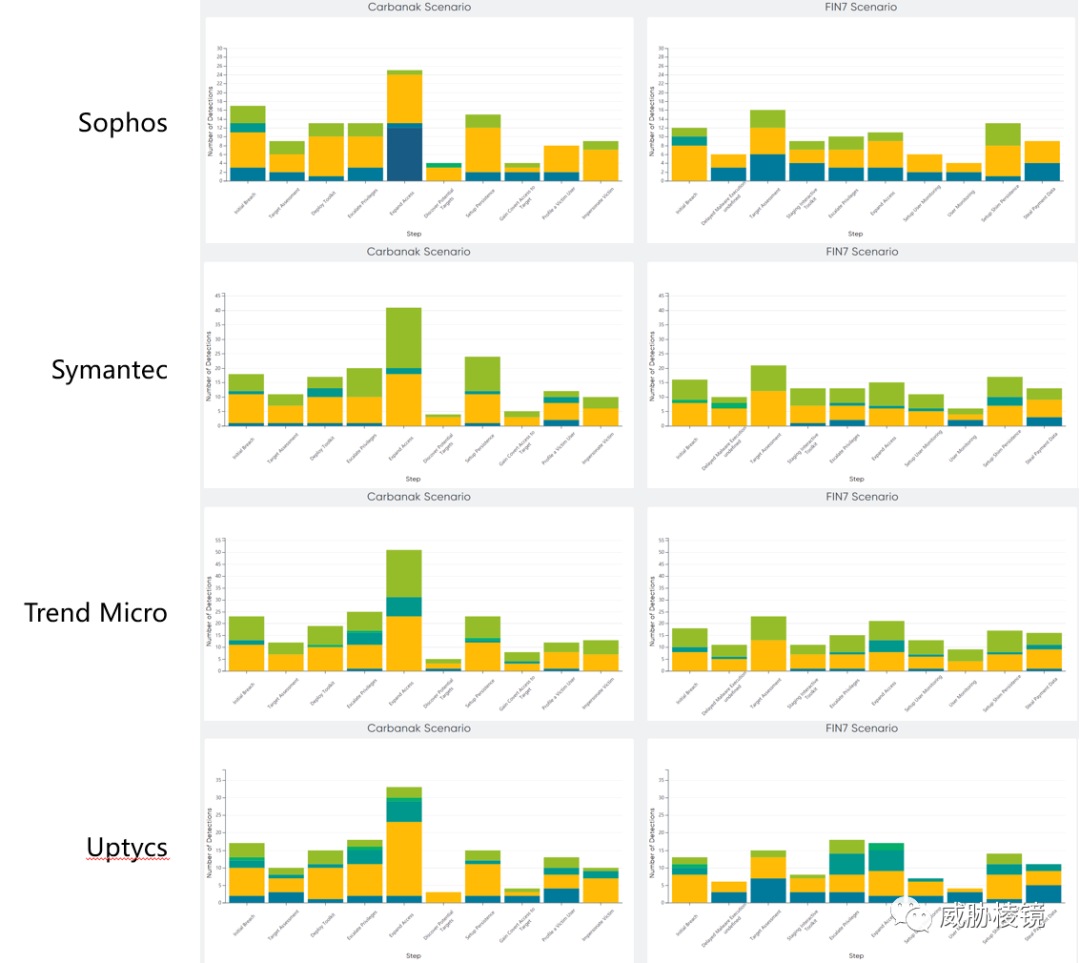
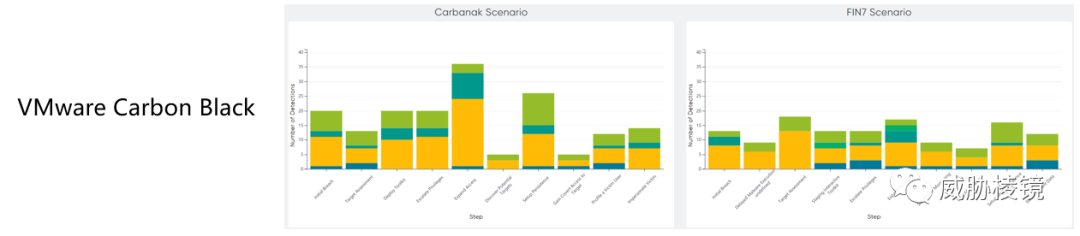
附录二
AhnLab
Bitdefender
Check Point
Cisco
CrowdStrike
Cybereason
CyCraft
BlackBerry Cylance
Cynet
Elastic
ESET
Fidelis
FireEye
Fortinet
F-Secure
GoSecure
Malwarebytes
McAfee
Micro Focus
Microsoft
Open Text
Palo Alto Networks
ReaQta
SentinelOne
Sophos
Symantec
Trend Micro
Uptycs
VMware Carbon Black

