排查思路
报文是否上到防火墙?
报文是否被防火墙阻断?
报文被防火墙阻断不会有会话表
步骤一: 是否有会话表
- 查看会话时要写明源目的地址,另外要加verbose才能显示更多信息
- 有会话说明报文上到了防火墙
display session table ipv4 source-ip 172.31.0.1 destination-ip 172.31.0.4 ver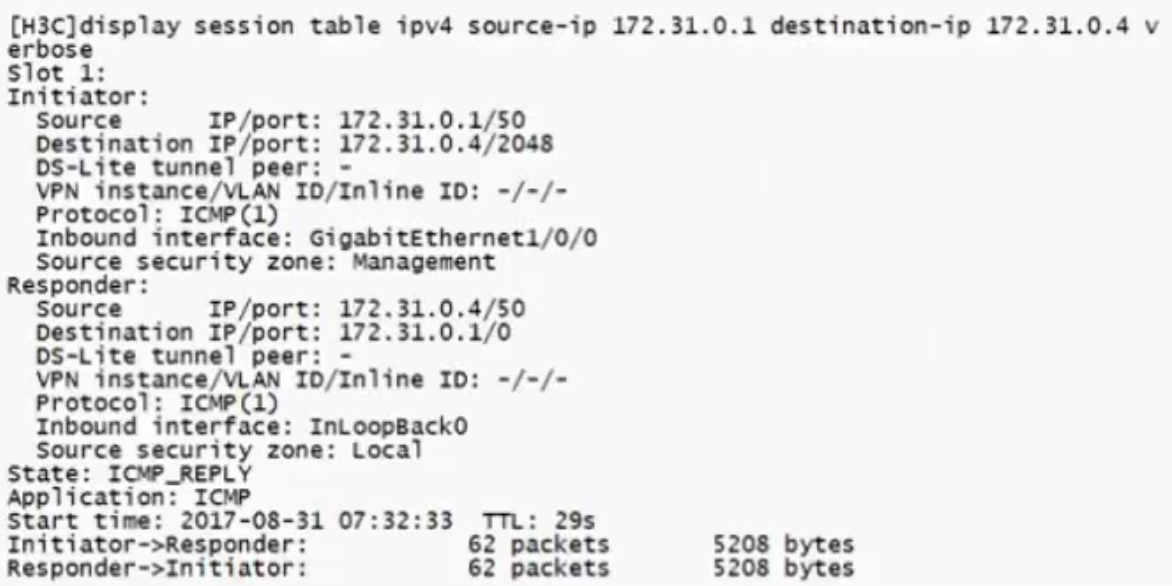
步骤二:查看报文是否到防火墙
debug ip packet acl
➢debug报文很多 ,一般要求后面写明细ACL匹配报文(写明源目的地址和协议)
acl advanced 3000rule 0 permit icmp source 172.31.0.1 0 destination 172.31.0.4 0<H3C> debugging ip packet acl 3000This command is CPU intensive and might affect ongoing services. Are you sure you want to continue? [Y/N]:Y<H3C> terminal monitorThe current terminal is enabled to display logs.<H3C> terminal debugging
有匹配ACL的debug信息说明报文到达了防火墙。否则报文没到防火墙,需排查路由等其它网络因素。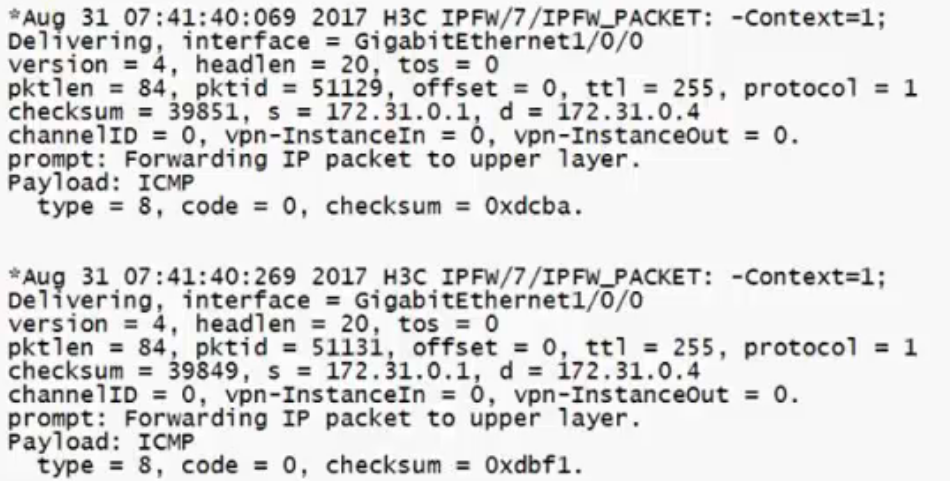
步骤三:抓包
在Web管理平台中 ,在[系统] - [维护] - [报文捕获]下点击(开始报文捕获]配置报文捕获过滤条件,选择接口,流量较大的时候建议匹配ACL。
报文是否被防火墙阻断
步骤一 : 检查安全策略是否放通报文
debugging security-policy packet ip acl
Debug报文很多 ,一般要求后面写明细ACL匹配报文(写明源目的地址和协议)
acl advanced 3000rule 5 permit icmp source 192. 168.10.2 0 destination 192.168.10.1 0<H3C> debugging security-policy packet ip acl 3000This command is CPU intensive and might affect ongoing services. Are you sure you want to continue? [Y/N]:Y<H3C> terminal monitorThe current terminal is enabled to display logs.<H3C> terminal debugging
正常debug(The packet is permitted)
<H3C> *Aug 31 08:24:11:380 2017 F1020 FILTER/7/PACKET: -Context=1; The packet is permitted. Src-Zone=Trust, Dst-Zone=Local;lf-In=GigabitEthernet1/0/5(6), |f-Out=InLoopBack0(132); Packet Info:Src-IP=192.168.10.2, Dst-lP=192. 168.10.1, VPN-Instance=, Src-Port=8, Dst-Port=0, Protocol=ICMP(1), Application=ICMP(22742),SecurityPolicy=1, Rule-lD=0.
阻断debug(The packet is denied SecurityPolicy=4, Rule-lD=3)
<H3C> *Aug 31 08:26:31:988 2017 H3C FILTER/7/PACKET: -Context=1; The packet is denied. Src-Zone=Trust, Dst-Zone=Local;lf-In=GigabitEthernet1/0/5(6), |f-Out=InL oopBack0(132); Packet Info:Src-IP=192. 168.10.2, Dst-lP=192. 168.10.1, VPN-Instance=, Src-Port=8, Dst-Port=0, Protocol=ICMP(1), Application=|CMP(22742),SecurityPolicy=4, Rule-lD=3
防火墙配置deny的安全策略会打印上面的信息,显示被哪条规则deny
步骤二: debugging aspf packet {acl}检查ASPF策略是否阻断报文
第一种情况
The packet was dropped by ASPF for nonexistent zone pair.(说明接口没有加入安全域,检查安全域配置)<H3C>debugging aspf packetThis command is CPU intensive and might affect ongoing services. Are you sure youwant to continue? [Y/N]:y<H3C> *Aug 31 08:21:38:114 2017 F1020 ASPF/7/PACKET: -Context=1; The packet wasdropped by ASPF for nonexistent zone pair. Src-Zone=-, Dst-Zone=L ocal;lf-In=GigabitEthernet1/0/5(6), lf-Out=InL oopBack0(132); Packet Info:Src-lP=192.168.10.2,Dst-IP=192.168.10.1, VPN-Instance=none Src-Port=1533, Dst-Port= 2048.Protocol=lCMP(1).
步骤二: 检查ASPF策略是否阻断报文
debugging aspf packet {ac|}
第二种情况
The first packet was dropped by packet filter or object-policy.(说明报文被安全策略阻断,检查是否有相应permit的安全策略)<H3C>debugging aspf packetThis command is CPU intensive and might affect ongoing services. Are you sure youwant to continue? [Y/N]:y<H3C> *Aug 31 08:26:31:988 2017 H3C ASPF/7/PACKET: -Context=1; The first packet was dropped by packet filter or object-policy. Src-Zone=Trust, Dst Zone=Local;lf-In=GigabitEthernet1/0/5(6), lIf-Out=InLoopBack0(132); Packet Info:Src-lP=192.168.10.2,Dst-IP=192.168.10.1, VPN-Instance=none,Src-Port=1535, Dst-Port 2048.Protocol=lCMP(1).
总结
判断报文是否.上防火墙
➢display session table ipv4
➢debug ip packet acl
判断报文是否被防火墙阻断
➢debugging security-policy packet ip acl
➢debugging aspf packet acl
注意事项
debug的注意事项
➢首先通过命令查看设备是否开启 了debug开关
<H3C>display debuggingSecurity-policy packet ip acl 3000 debugging switch is on
➢debug完成后关闭debug开启 ,可以通过命令行或者快捷键
<H3C>undo terminal debuggingThe current terminal is disabled to display debugging logs.<H3C>u t dThe current terminal is disabled to display debugging logs.
快捷键:CTR+C回到<用户模式>,CTR+O关闭debug信息
debug的FAQ
没有debug信息怎么办

