漏洞: 
测试:
[root@ocdp-42-55 ~]# openssl s_client -connect 10.1.236.55:5151
CONNECTED(00000003)
depth=0 C = US, O = mycompany, OU = authenticator, CN = unixauthservice
verify error:num=18:self signed certificate
verify return:1
depth=0 C = US, O = mycompany, OU = authenticator, CN = unixauthservice
verify return:1
—-
Certificate chain
0 s:/C=US/O=mycompany/OU=authenticator/CN=unixauthservice
i:/C=US/O=mycompany/OU=authenticator/CN=unixauthservice
—-
Server certificate
——-BEGIN CERTIFICATE——-
MIIDRTCCAi2gAwIBAgIEbF8nMTANBgkqhkiG9w0BAQsFADBTMQswCQYDVQQGEwJV
UzESMBAGA1UEChMJbXljb21wYW55MRYwFAYDVQQLEw1hdXRoZW50aWNhdG9yMRgw
FgYDVQQDEw91bml4YXV0aHNlcnZpY2UwHhcNMTgxMDE5MDI1OTE0WhcNMjgwODI3
MDI1OTE0WjBTMQswCQYDVQQGEwJVUzESMBAGA1UEChMJbXljb21wYW55MRYwFAYD
VQQLEw1hdXRoZW50aWNhdG9yMRgwFgYDVQQDEw91bml4YXV0aHNlcnZpY2UwggEi
MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCpU0tYR/oeR/ZAouifZxx7+0m9
cqVQc1SlDF2iXvaBrah1VDo21M7XdkMWSQ/Qo0bAB2Ct7f3JA27rlfKz8EG/+Tsb
DY5a1XzNf4dMuvtxw+CwKkUDqYcI/rIkfvNJ+FGU5RY1ub0648zZc1kXw8WqnvE+
1iEi/yJkYeE/zNPZrLn/Q63/pKaNoPsJfgWTGZo/37rvg9TLA0qE3h3ZjixDSy+o
EIZfFMgaLYj032yuIBq+llZP1uecU6Ciqb62GvzTxTdu4rGXK9w6bXcf6ZoKcoZ2
szft+UOeQhJPFwg4uQk9IuXB2+b3PRq9rPJKGOAcCk9EQcvuXYgEorMk/3d1AgMB
AAGjITAfMB0GA1UdDgQWBBRCUxtegvoSQzLzfU5ZyzPhB/QV6zANBgkqhkiG9w0B
AQsFAAOCAQEAM0eB5if+xb0AUeK3eKciNFk5gLum1GoEAcNrWW0BqbDlu41EIoSH
X36vJvuPH3MLhfNcfZCHIsI0ui18bAtRefrrF+nA/5mpeYkKK4OjDXQwW40lbX0X
lzr3IYc/J9u/isTyC7fim7CWwy4EnHAMAFo38AgTE7IfY97/A0iLl4DJDIaRvpso
uLHvxRrnMSKV7bHJq1II0bFYuNIR4EnISwlWQQVoT+ZokBBcZxUx73zTfTq25tj2
l2QD3UwCgY8sG4evZTNNsEyVNSekXR1m/YL6f/6lhqVVAcBlb4hVH1Vb9b0ornyP
XwvQ61tSL1Lm6rL9KT1ueCWj35Jc1p24kw==
——-END CERTIFICATE——-
subject=/C=US/O=mycompany/OU=authenticator/CN=unixauthservice
issuer=/C=US/O=mycompany/OU=authenticator/CN=unixauthservice
—-
No client certificate CA names sent
Server Temp Key: ECDH, secp521r1, 521 bits
—-
SSL handshake has read 1393 bytes and written 441 bytes
—-
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bitSecure Renegotiation IS supported
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 5C0A0D09DED1F933D7A2E9975A72CDB3B13923E10F650013B741A5404D8F7930
Session-ID-ctx:
Master-Key:
2754CD294164F105C37CC7570234071E9A97AC316C9302601C898A63A167793BE32D1A227CFA2ABFA2AF3612D9C5FC45
Key-Arg : None
Krb5 Principal: None
PSK identity: None
PSK identity hint: None
Start Time: 1544162569
Timeout : 300 (sec)
Verify return code: 18 (self signed certificate)
—-
可以看到ranger的5151端口确实有漏洞。 
漏洞修复: 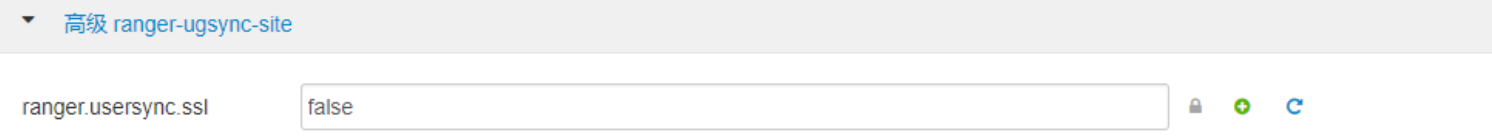
重启ranger服务。
测试:
[root@ocdp-42-55 ~]# openssl s_client -connect 10.1.236.55:5151
CONNECTED(00000003)
140269047473992:error:140770FC:SSL routines:SSL23_GET_SERVER_HELLO:unknown protocol:s23_clnt.c:769:
—-
no peer certificate available
—-
No client certificate CA names sent
—-
SSL handshake has read 7 bytes and written 247 bytes
—-
New, (NONE), Cipher is (NONE)
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
—-

