- 说明
- 参数
- 示例一
- ip rule add from 192.168.1.112/32 [tos 0x10] table test2 pref 999 prohibit
#ip rule add to 192.168.1.2 pref 1000 table test1
#ip rule add from 192.168.1.0/24 pref 1001 table test1
#ip rule add [from 0/0] table test1 pref 1003
#ip rule add fwmark 1 pref 1002 table test2 此句型配合iptables -t mangle应用.如先对数据包作标记:
#iptables -t mangle -A PREROUTING -p tcp -m multiport —dports 80,8080,20,21 -s 192.168.1.0/24 -j MARK —set-mark 1 - 示例二
- 示例三
说明
iproute2里面的一个命令,ip rule 路由策略数据库管理命令
进行路由时,根据路由规则来进行匹配,按优先级(pref)从低到高匹配,直到找到合适的规则,所以在应用中配置默认路由是必要的
Internet上采用的路由算法一般是基于数据包目的地址的。
而在某些情况下,我们不只是需要通过数据包的目的地址决定路由,可能还需要通过其他一些域:源地址、IP协议、传输层端口甚至数据包的负载。这就叫做:策略路由(policy routing)。
注意:策略路由(policy routing)不等于路由策略(rouing policy)。路由_路由策略和策略路由有什么区别
在这种情况下,传统的基于目的地址的路由表就无法满足要求了,需要使用路由策略数据库(routing policy database,RPDB)代替,通过它选择执行某些路由。这些规则可以由很多不同的状态,而且它们没有天生的次序,要由系统管理员决定。
RPDB可以 匹配以下的域:
- 数据包的源地址;
- 数据包的目的地址;
- 服务类型(Type of Service);
- 进入的网络接口;
匹配IP协议和传输层端口也是可能的,不过这要依靠iptables或者ipchains通过fwmark为某些数据包做标记,并重定向。
每个路由策略由一个选择符(selector)和一个操作(action)组成。系统按照顺序搜索路由策略数据库,把选择符和{源地址、目的地址、进入接口、tos、fwmark}等关键词进行匹配,如果匹配成功,就执行action定义的操作。操作或者成功返回,或者失败并且中止路由策略。否则,系统继续查询路由策略数据库。
操作如何定义?最原始的操作是选择下一跳(nexthop)和输出设备(output device)。Cisco IOS使用这种方式,我们姑且把这叫做匹配并设置(match & set)。而Linux的方式则更为灵活,Linux允许的操作包括:基于目的地址的路由表查询以及按照最长匹配的原则从路由表中选择路由。因此,匹配并 设置(match & set)的方式只是一个最简单的特例而已。
再系统启动时,内核会为路由策略数据库配置三条缺省的规则: 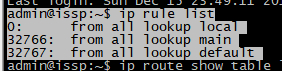
| 优先级 | 选择符 | 动作 | 解释 |
|---|---|---|---|
| 0 | 匹配任何条件 | 查询路由表local(ID 255) | 路由表local是一个特殊的路由表,包含对于本地和广播地址的高优先级控制路由。rule 0非常特殊,不能被删除或者覆盖。 一张表用于本地地址,存储了全部的本地地址,假设在该表中能查到匹配表项,则表明数据报是发给本机的 |
| 32766 | 匹配任何条件 | 查询路由表main(ID 254) | 是一个通常的表,包含所有的无策略路由。系统管理员可以删除或者使用另外的规则覆盖这条规则。 一张表用于全部其它的路由,路由表项由用户手工静态配置(默认就是main表)或由路由协议动态配置 |
| 32767 | 匹配任何条件 | 查询路由表default(ID 253) | 是一个空表,它是为一些后续处理保留的。对于前面的缺省策略没有匹配到的数据包,系统使用这个策略进行处理。这个规则也可以删除。 |
注:这里匹配任何条件就说明是按路由策略的优先级匹配各个路由表,如果没有匹配高优先级路由策略指定的路由表,就接着往下匹配,而不是说就直接进行丢弃了
不要混淆路由表和策略:规则指向路由表,多个规则可以引用一个路由表,而且某些路由表可以没有策略指向它。如果系统管理员删除了指向某个路由表的所有规则,这个表就没有用了,但是仍然存在,直到里面的所有路由都被删除,它才会消失。
参数
注:具体参数还是看系统命令,新版的iproute2里面又加了很多
**Usage: ip rule [ list | add | del ] SELECTOR ACTION (add 添加;del 删除; llist 列表)**
- SELECTOR := [ from PREFIX 数据包源地址] [ to PREFIX 数据包目的地址] [ tos TOS 服务类型][ dev STRING 物理接口] [ pref NUMBER ] [fwmark MARK iptables 标签]
- ACTION := [ table TABLE_ID 指定所使用的路由表] [ nat ADDRESS 网络地址转换][ prohibit 丢弃该表| reject 拒绝该包| unreachable 丢弃该包]
- [ flowid CLASSID ]
- TABLE_ID := [ local | main | default | new | NUMBER ]
可参数解析如下:
From — 源地址
To — 目的地址(这里是选择规则时使用,查找路由表时也使用)
Tos — IP包头的TOS(type of sevice)域
Dev — 物理接口
Fwmark — 防火墙参数
采取的动作除了指定路由表外,还可以指定下面的动作:
Table 指明所使用的表
Nat 透明网关
Prohibit 丢弃该包,并发送 COMM.ADM.PROHIITED的ICMP信息
Reject 单纯丢弃该包
Unreachable丢弃该包, 并发送 NET UNREACHABLE的ICMP信息
示例一
ip rule add from 192.168.1.112/32 [tos 0x10] table test2 pref 999 prohibit
#ip rule add to 192.168.1.2 pref 1000 table test1
#ip rule add from 192.168.1.0/24 pref 1001 table test1
#ip rule add [from 0/0] table test1 pref 1003
#ip rule add fwmark 1 pref 1002 table test2 此句型配合iptables -t mangle应用.如先对数据包作标记:
#iptables -t mangle -A PREROUTING -p tcp -m multiport —dports 80,8080,20,21 -s 192.168.1.0/24 -j MARK —set-mark 1
示例二
Source IP
根据来源端IP来决定数据包参考哪个路由表发送出去。以下两个示例分别指出,如果数据包的来源端IP是192.168.1.10,就参考路由表10;如果来源端IP为192.168.2.0/24网段的IP,就参考路由表20
ip rule add from 192.168.1.10 table 10 2 ip rule add from 192.168.2.0/24 table 20
Destination IP
根据目的端IP来决定数据包参考哪个路由表发送出去。以下两个示例分别指出,如果数据包的目的端IP是168.95.1.1,就参考路由表10;如果目的端IP是168.95.0.0/24网段的IP,就参考路由表20
ip rule add to 168.95.1.1 table 10 2 ip rule add to 168.96.0.0/24 table 20
ip rule show命令所显示内容的第一个字段就是优先级别,数字越小,代表优先级别越高,也代表这条规则可以排得越靠前
[root@localhost ~]# ip rule show0: from all lookup local32766: from all lookup main32767: from all lookup default[root@localhost ~]# ip rule add from 192.168.1.0/24 table 1 prio 10[root@localhost ~]# ip rule add from 192.168.2.0/24 table 2 prio 20[root@localhost ~]# ip rule show0: from all lookup local10: from 192.168.1.0/24 lookup 120: from 192.168.2.0/24 lookup 232766: from all lookup main32767: from all lookup default
删除规则
ip rule del prio 10ip rule del from 192.168.1.0/24ip rule del table 1ip rule del from 192.168.1.0/24 table 1 prio 10
示例三
官方参考:http://www.man7.org/linux/man-pages/man8/ip-rule.8.html
IP-RULE(8) Linux IP-RULE(8)NAME topip-rule - routing policy database managementSYNOPSIS topip [ OPTIONS ] rule { COMMAND | help }ip rule [ list [ SELECTOR ]]ip rule { add | del } SELECTOR ACTIONip rule { flush | save | restore }SELECTOR := [ not ] [ from PREFIX ] [ to PREFIX ] [ tos TOS ] [fwmark FWMARK[/MASK] ] [ iif STRING ] [ oif STRING ] [ prefNUMBER ] [ l3mdev ] [ uidrange NUMBER-NUMBER ] [ ipprotoPROTOCOL ] [ sport [ NUMBER | NUMBER-NUMBER ] ] [ dport [NUMBER | NUMBER-NUMBER ] ] [ tun_id TUN_ID ]ACTION := [ table TABLE_ID ] [ protocol PROTO ] [ nat ADDRESS ] [realms [SRCREALM/]DSTREALM ] [ goto NUMBER ] SUPPRESSORSUPPRESSOR := [ suppress_prefixlength NUMBER ] [ suppress_ifgroupGROUP ]TABLE_ID := [ local | main | default | NUMBER ]DESCRIPTION topip rule manipulates rules in the routing policy database control theroute selection algorithm.Classic routing algorithms used in the Internet make routingdecisions based only on the destination address of packets (and intheory, but not in practice, on the TOS field).In some circumstances we want to route packets differently dependingnot only on destination addresses, but also on other packet fields:source address, IP protocol, transport protocol ports or even packetpayload. This task is called 'policy routing'.To solve this task, the conventional destination based routing table,ordered according to the longest match rule, is replaced with a'routing policy database' (or RPDB), which selects routes byexecuting some set of rules.Each policy routing rule consists of a selector and an actionpredicate. The RPDB is scanned in order of decreasing priority (notethat lower number means higher priority, see the description ofPREFERENCE below). The selector of each rule is applied to {sourceaddress, destination address, incoming interface, tos, fwmark} and,if the selector matches the packet, the action is performed. Theaction predicate may return with success. In this case, it willeither give a route or failure indication and the RPDB lookup isterminated. Otherwise, the RPDB program continues with the next rule.Semantically, the natural action is to select the nexthop and theoutput device.At startup time the kernel configures the default RPDB consisting ofthree rules:1. Priority: 0, Selector: match anything, Action: lookup routingtable local (ID 255). The local table is a special routingtable containing high priority control routes for local andbroadcast addresses.2. Priority: 32766, Selector: match anything, Action: lookuprouting table main (ID 254). The main table is the normalrouting table containing all non-policy routes. This rule maybe deleted and/or overridden with other ones by theadministrator.3. Priority: 32767, Selector: match anything, Action: lookuprouting table default (ID 253). The default table is empty.It is reserved for some post-processing if no previous defaultrules selected the packet. This rule may also be deleted.Each RPDB entry has additional attributes. F.e. each rule has apointer to some routing table. NAT and masquerading rules have anattribute to select new IP address to translate/masquerade. Besidesthat, rules have some optional attributes, which routes have, namelyrealms. These values do not override those contained in the routingtables. They are only used if the route did not select anyattributes.The RPDB may contain rules of the following types:unicast - the rule prescribes to return the route found in therouting table referenced by the rule.blackhole - the rule prescribes to silently drop the packet.unreachable - the rule prescribes to generate a 'Network isunreachable' error.prohibit - the rule prescribes to generate 'Communication isadministratively prohibited' error.nat - the rule prescribes to translate the source address ofthe IP packet into some other value.ip rule add - insert a new ruleip rule delete - delete a ruletype TYPE (default)the type of this rule. The list of valid types wasgiven in the previous subsection.from PREFIXselect the source prefix to match.to PREFIXselect the destination prefix to match.iif NAMEselect the incoming device to match. If the interfaceis loopback, the rule only matches packets originatingfrom this host. This means that you may create separaterouting tables for forwarded and local packets and,hence, completely segregate them.oif NAMEselect the outgoing device to match. The outgoinginterface is only available for packets originatingfrom local sockets that are bound to a device.tos TOSdsfield TOSselect the TOS value to match.fwmark MARKselect the fwmark value to match.uidrange NUMBER-NUMBERselect the uid value to match.ipproto PROTOCOLselect the ip protocol value to match.sport NUMBER | NUMBER-NUMBERselect the source port value to match. supports portrange.dport NUMBER | NUMBER-NUMBERselect the destination port value to match. supportsport range.priority PREFERENCEthe priority of this rule. PREFERENCE is an unsignedinteger value, higher number means lower priority, andrules get processed in order of increasing number. Eachrule should have an explicitly set unique priorityvalue. The options preference and order are synonymswith priority.table TABLEIDthe routing table identifier to lookup if the ruleselector matches. It is also possible to use lookupinstead of table.protocol PROTOthe routing protocol who installed the rule inquestion. As an example when zebra installs a rule itwould get RTPROT_ZEBRA as the installing protocol.suppress_prefixlength NUMBERreject routing decisions that have a prefix length ofNUMBER or less.suppress_ifgroup GROUPreject routing decisions that use a device belonging tothe interface group GROUP.realms FROM/TORealms to select if the rule matched and the routingtable lookup succeeded. Realm TO is only used if theroute did not select any realm.nat ADDRESSThe base of the IP address block to translate (forsource addresses). The ADDRESS may be either the startof the block of NAT addresses (selected by NAT routes)or a local host address (or even zero). In the lastcase the router does not translate the packets, butmasquerades them to this address. Using map-to insteadof nat means the same thing.Warning: Changes to the RPDB made with these commandsdo not become active immediately. It is assumed thatafter a script finishes a batch of updates, it flushesthe routing cache with ip route flush cache.ip rule flush - also dumps all the deleted rules.protocol PROTOSelect the originating protocol.ip rule show - list rulesThis command has no arguments. The options list or lst aresynonyms with show.ip rule saveprotocol PROTOSelect the originating protocol.save rules table information to stdoutThis command behaves like ip rule show except that the outputis raw data suitable for passing to ip rule restore.ip rule restorerestore rules table information from stdinThis command expects to read a data stream as returned from iprule save. It will attempt to restore the rules tableinformation exactly as it was at the time of the save. Anyrules already in the table are left unchanged, and duplicatesare not ignored.SEE ALSO topip(8)AUTHOR topOriginal Manpage by Michail Litvak <mci@owl.openwall.com>COLOPHON topThis page is part of the iproute2 (utilities for controlling TCP/IPnetworking and traffic) project. Information about the project canbe found at⟨http://www.linuxfoundation.org/collaborate/workgroups/networking/iproute2⟩.If you have a bug report for this manual page, send it tonetdev@vger.kernel.org, shemminger@osdl.org. This page was obtainedfrom the project's upstream Git repository⟨https://git.kernel.org/pub/scm/network/iproute2/iproute2.git⟩ on2019-11-19. (At that time, the date of the most recent commit thatwas found in the repository was 2019-11-17.) If you discover anyrendering problems in this HTML version of the page, or you believethere is a better or more up-to-date source for the page, or you havecorrections or improvements to the information in this COLOPHON(which is not part of the original manual page), send a mail toman-pages@man7.org
/

