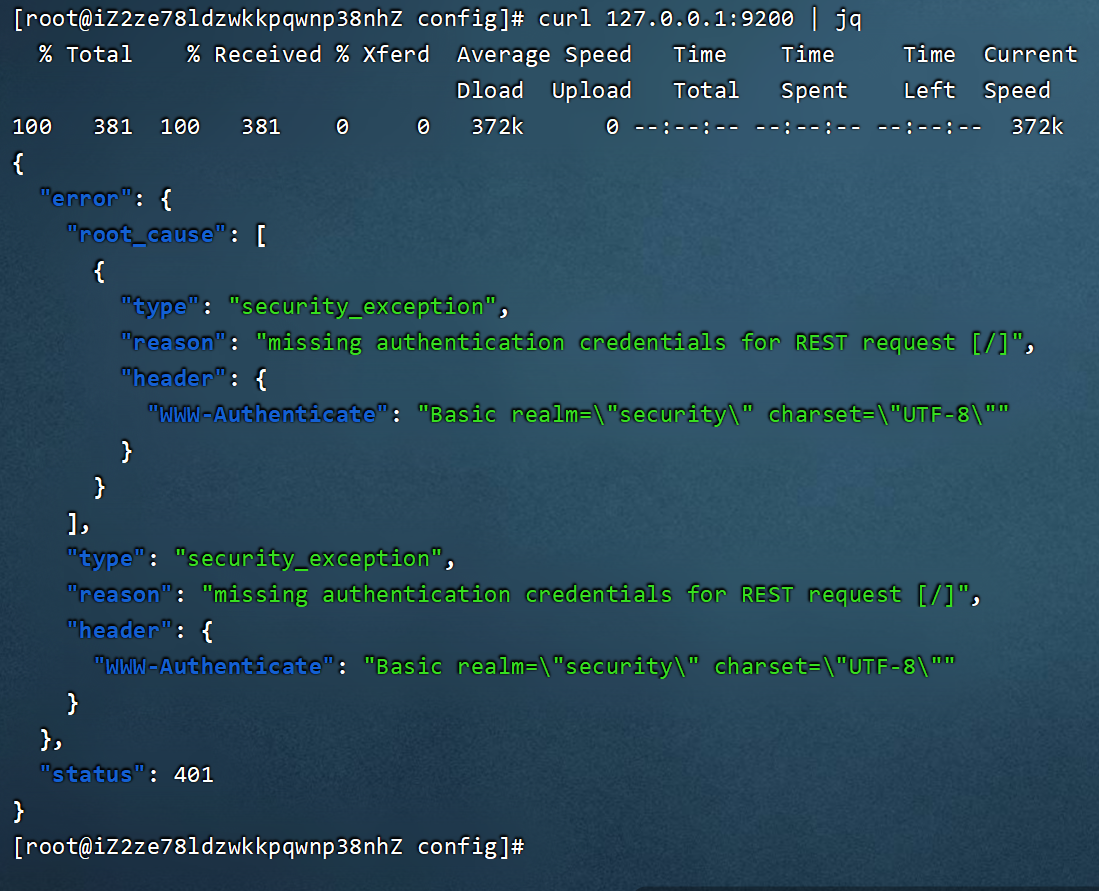
https://blog.csdn.net/star1210644725/article/details/107121850
一、节点间通讯加密
生成证书不需关注集群是否启动。也就是不管集群有没有启动,都可以生成证书。
随便进入一个节点的bin目录下,执行
**./elasticsearch-certutil ca**$ cd $ES_MASTER_NODE01_HOME/bin/$ ./elasticsearch-certutil ca
执行完会让你输入密码, 请记住这个密码。
执行完毕后会生成一个证书: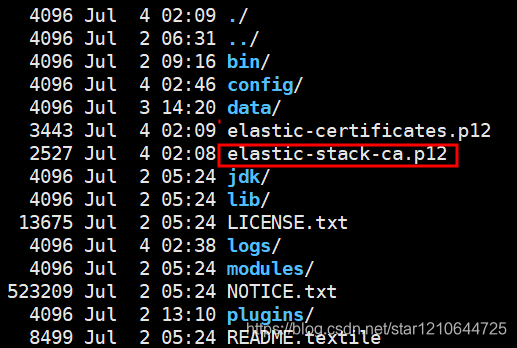
接着还在 bin 目录下执行
**./elasticsearch-certutil cert --ca elastic-stack-ca.p12**$ cd $ES_MASTER_NODE01_HOME/bin/$ ./elasticsearch-certutil cert --ca elastic-stack-ca.p12
依然会让你确认证书的名字和密码,名字的话直接回车用默认的就好,密码的话自定义。请记住这个密码。
执行完毕后会生成第二个证书文件: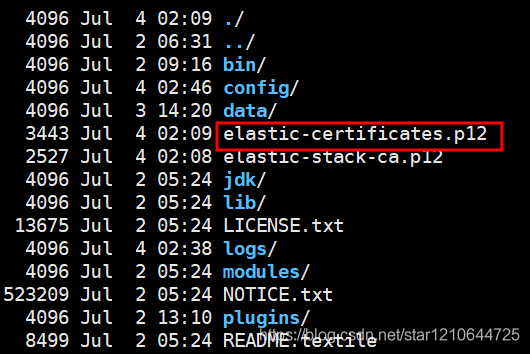
把
elastic-certificates.p12文件复制到config目录下$ cd $ES_MASTER_NODE01_HOME$ cp elastic-certificates.p12 ./config/$ cd ./config/$ ll
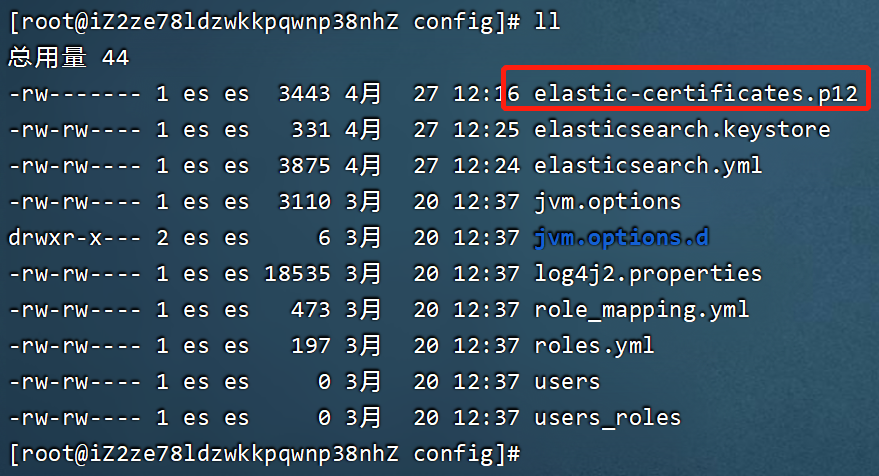
配置
keystore的密码和truststore的密码$ cd $ES_MASTER_NODE01_HOME/bin/$ ./elasticsearch-keystore add xpack.security.transport.ssl.keystore.secure_password#输入之前的密码...$ ./elasticsearch-keystore add xpack.security.transport.ssl.truststore.secure_password#输入之前的密码...
执行完毕之后 会发现
elasticsearch.keystore文件变大了。在
elasticsearch.yml文件内加入如下配置, 并将此配置复制到集群内所有节点。# 开启安全认证xpack.security.enabled: true# 开启节点间通讯加密xpack.security.transport.ssl.enabled: true#认证模式为证书认证模式xpack.security.transport.ssl.verification_mode: certificate# 指定keystore证书的存放目录,默认config目录下xpack.security.transport.ssl.keystore.path: elastic-certificates.p12# 指定truststore证书的存放目录,默认config目录下xpack.security.transport.ssl.truststore.path: elastic-certificates.p12
将
config目录下的elastic-certificates.p12和elasticsearch.keystore复制到集群内其他所有节点的config目录下- 重启整个集群,并去 logs 日志文件里边查看一下集群是否正常启动。
二、配置kibana
进入任意一个bin下边执行,需要分别设置几个密码,可以设置成相同的。
$ ./elasticsearch-setup-passwords interactiveInitiating the setup of passwords for reserved users elastic,apm_system,kibana,logstash_system,beats_system,remote_monitoring_user.You will be prompted to enter passwords as the process progresses.Please confirm that you would like to continue [y/N]yReenter password for [elastic]:Passwords do not match.Try again.Enter password for [elastic]: {输入elastic的密码}Reenter password for [elastic]: {再次输入elastic的密码}Enter password for [apm_system]: {输入apm_system的密码}Reenter password for [apm_system]: {再次输入apm_system的密码}Enter password for [kibana]: {输入kibana的密码}Reenter password for [kibana]: {再次输入kibana的密码}Enter password for [logstash_system]: {输入logstash_system的密码}Reenter password for [logstash_system]: {再次输入logstash_system的密码}Enter password for [beats_system]: {输入beats_system的密码}Reenter password for [beats_system]: {再次输入beats_system的密码}Enter password for [remote_monitoring_user]: {输入remote_monitoring_user的密码}Reenter password for [remote_monitoring_user]: {再次输入remote_monitoring_user的密码}Changed password for user [apm_system]Changed password for user [kibana]Changed password for user [logstash_system]Changed password for user [beats_system]Changed password for user [remote_monitoring_user]Changed password for user [elastic]$
修改kibana配置文件加入如下配置:
elasticsearch.username: "kibana"elasticsearch.password: "{上面设置的kibana密码}"
然后重启kibana,在kibana登录时需要输入另一个账号,这里用elastic账号和和密码登录:
三、修改账号密码
curl -H "Content-Type:application/json" -XPOST -u {{要登录的账号。一般为elastic} } 'http://127.0.0.1:9200/_xpack/security/user/elastic/_password' -d '{ "password" : "{新密码}" }'
然后会让你输入旧密码:
Enter host password for user 'elastic': {elastic账号的密码}
输入后如果返回一个空的“{}”表示修改成功。
登录elastic账号,并修改kibana的密码为“123456”
curl -H "Content-Type:application/json" -XPOST -u elastic 'http://127.0.0.1:9200/_xpack/security/user/kibana/_password' -d '{ "password" : "123456" }'