了解NetworkPolicy
一个 NetworkPolicy 会应用在匹配它的标签选择器的 pod 上,指明这些允许访问这些 pod 的源地址,或这些 pod 可以访问的目标地址。这些分别由入向(ingress) 和出向(egress)规则指定。这两种规则都可以匹配由标签选择器选出的 pod,或者一个 namespace 中的所有 pod,或者通过无类别域间路由(Classless Inter-Domain Routing, CIDR)指定的 IP 地址段。 默认是允许入站和出站。
- ingress:入站流量,限制的是源地址,pod端口
- engress:出站流量,限制的是目的地址。目的端口

举例说明
创建2个名称空间
kubectl create namespace devkubectl create namespace test
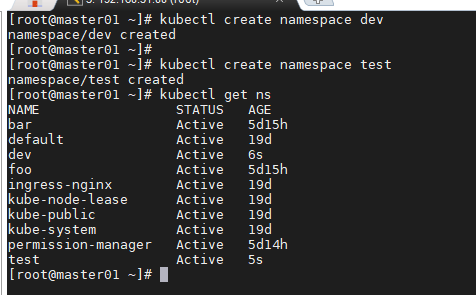
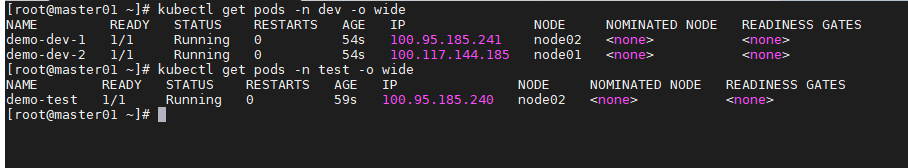
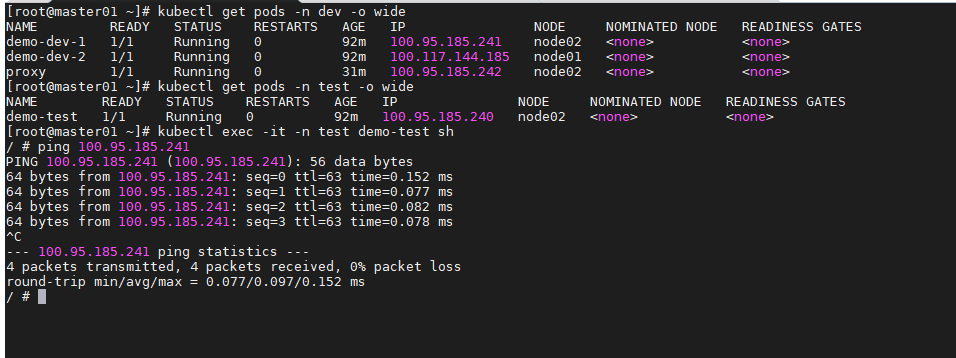
每个名称空间创建一个pod
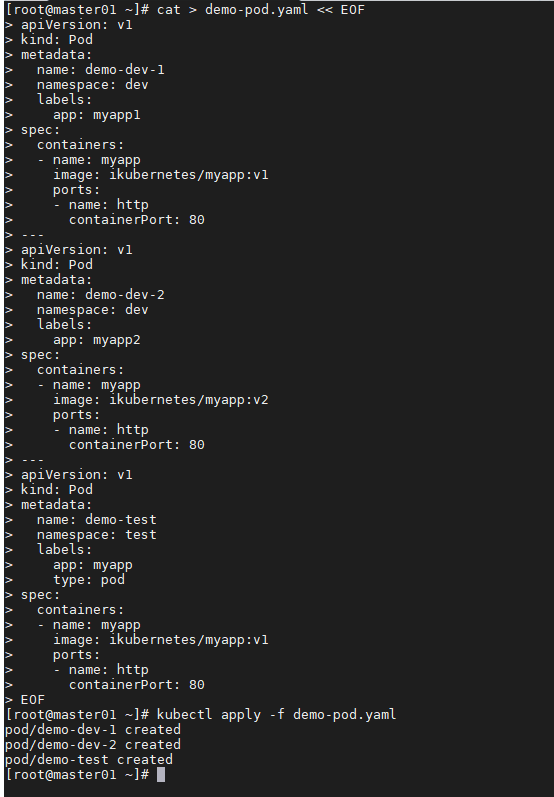
cat > demo-pod.yaml << EOF
apiVersion: v1
kind: Pod
metadata:
name: demo-dev-1
namespace: dev
labels:
app: myapp1
spec:
containers:
- name: myapp
image: ikubernetes/myapp:v1
ports:
- name: http
containerPort: 80
---
apiVersion: v1
kind: Pod
metadata:
name: demo-dev-2
namespace: dev
labels:
app: myapp2
spec:
containers:
- name: myapp
image: ikubernetes/myapp:v2
ports:
- name: http
containerPort: 80
---
apiVersion: v1
kind: Pod
metadata:
name: demo-test
namespace: test
labels:
app: myapp
type: pod
spec:
containers:
- name: myapp
image: ikubernetes/myapp:v1
ports:
- name: http
containerPort: 80
EOF
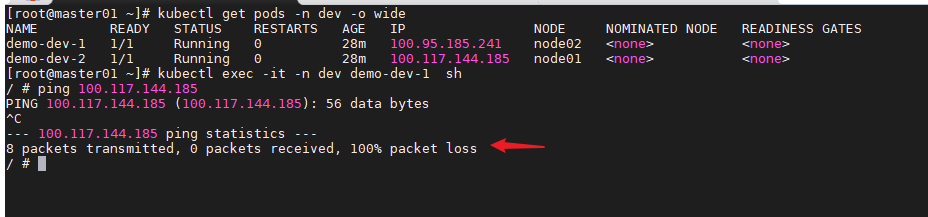
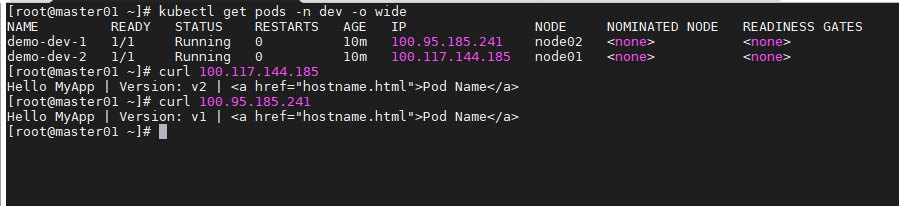
禁止访问该namespace的pod
cat > dev-deny.yaml << EOF
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: dev-deny
namespace: dev
spec:
podSelector: {}
EOF
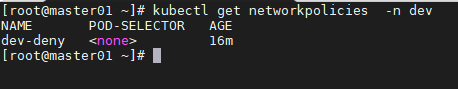
添加网络策略后访问失败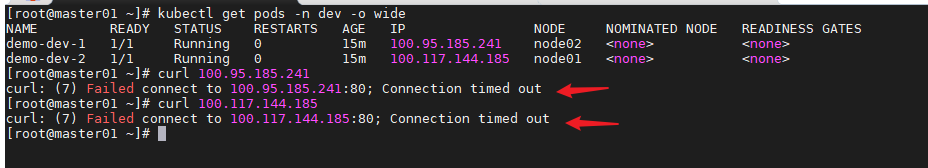
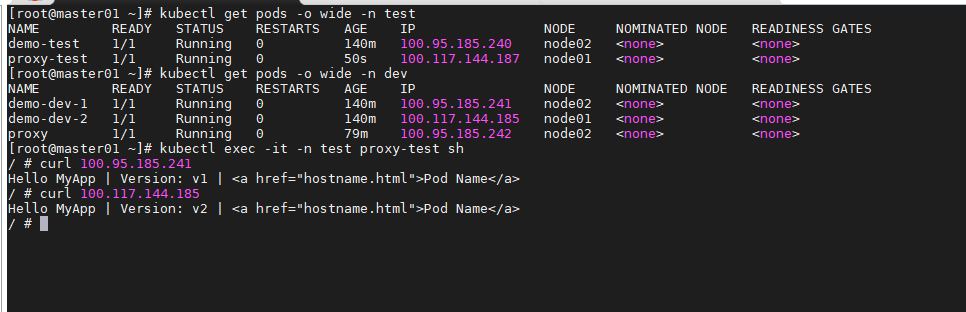
允许同一namespace中的pod访问一个pod
cat > allow-pod.yaml << EOF
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-pod
namespace: dev
spec:
podSelector:
matchExpressions:
- {key: app, operator: In, values: [myapp1, myapp2]}
ingress:
- from:
- podSelector:
matchLabels:
app: proxy
ports:
- protocol: TCP
port: 80
---
apiVersion: v1
kind: Pod
metadata:
name: proxy
namespace: dev
labels:
app: proxy
spec:
containers:
- name: proxy
image: luksa/kubectl-proxy
imagePullPolicy: IfNotPresent
restartPolicy: Always
EOF
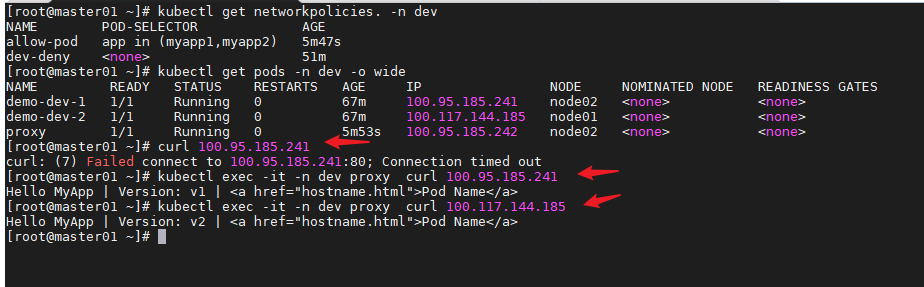
只允许进站,不允许该namespace下的pod出站
cat > allow-all-ingress.yaml << EOF
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-all-ingress
namespace: dev
spec:
podSelector: {}
ingress:
- {}
policyTypes:
- Ingress
- Egress
EOF
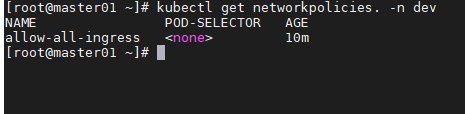
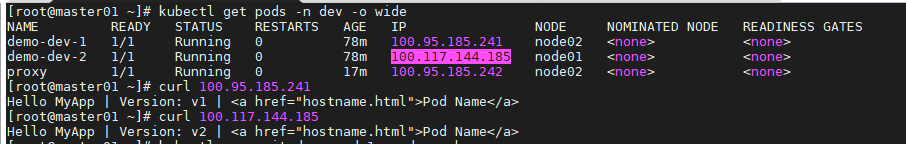
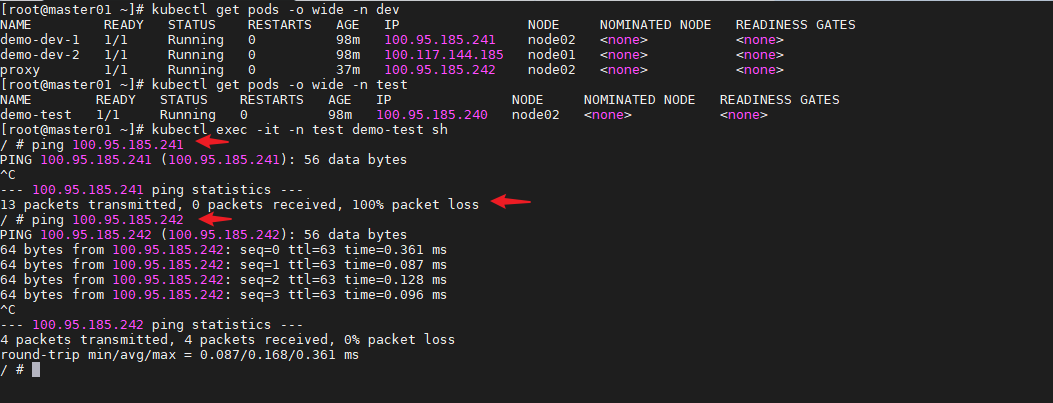
禁止单ip入站
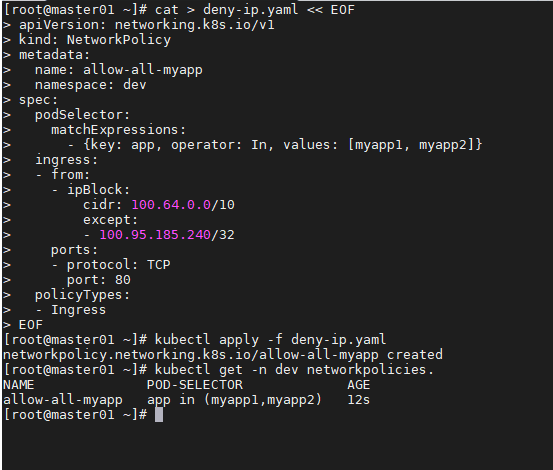
cat > deny-ip.yaml << EOF
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-all-myapp
namespace: dev
spec:
podSelector:
matchExpressions:
- {key: app, operator: In, values: [myapp1, myapp2]}
ingress:
- from:
- ipBlock:
cidr: 100.64.0.0/10
except:
- 100.95.185.240/32
ports:
- protocol: TCP
port: 80
policyTypes:
- Ingress
EOF
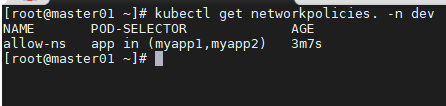
只允许namespace下的特定pod入站
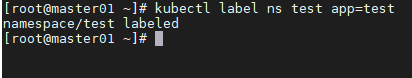
cat > allow-ns.yaml << EOF
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-ns
namespace: dev
spec:
podSelector:
matchExpressions:
- {key: app, operator: In, values: [myapp1, myapp2]}
ingress:
- from:
- namespaceSelector:
matchLabels:
app: test
ports:
- protocol: TCP
port: 80
policyTypes:
- Ingress
---
apiVersion: v1
kind: Pod
metadata:
name: proxy-test
namespace: test
labels:
app: proxy-test
spec:
containers:
- name: proxy
image: luksa/kubectl-proxy
imagePullPolicy: IfNotPresent
restartPolicy: Always
EOF