证书认证前提:
- 网络连通性。
- 时间同步性(由于证书具有有效期,顾CA服务器与申请证书客户端必须时间同步)。
IKEv1 证书认证VPN
- 时间同步
CA 服务器配置 clock timezone GMT +8 ntp authentication-key 1 md5 110A1016141D 7 ntp authenticate ntp trusted-key 1 ntp master
客户端配置
clock timezone GMT +8
ntp authentication-key 1 md5 110A1016141D 7
ntp authenticate
ntp trusted-key 1
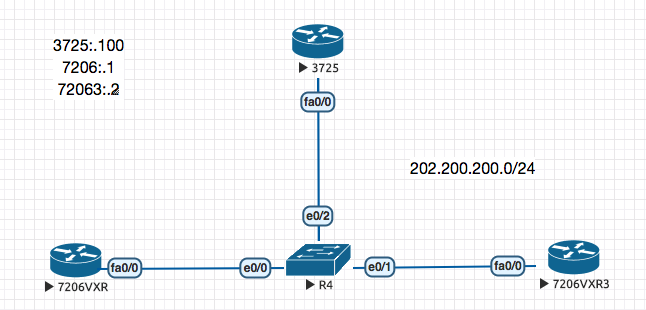
ntp server 202.200.200.100 key 1
- 配置证书服务器 && 申请证书
CA 证书服务器配置 ip http server
ip domain name cisco.com
crypto pki server CA
issuer-name cn=[CA.cisco.com](http://ca.cisco.com/),c=CN,l=NMG #证书服务器信息lifetime certificate 180 #有效期 180天no shutdownPassword: #密码用于加密私匙Re-enter password:在线颁发证书
crypto pki server CA info requests # 查看证书申请请求
crypto pki server CA grant 1 #颁发证书
离线颁发证书
crypto pki export CA pem terminal # 通过终端导出CA 根证书
crypto pki server CA request pkcs10 terminal # 通过终端倒入证书申请信息
crypto pki server CA grant 2 #颁发证书,并从命令行导出颁发的证书信息
Site_1 在线申请证书配置方式
ip domain name cisco.com
crypto key generate rsa modulus 1024 label S1key
crypto pki trustpoint CA
enrollment url [http://202.200.200.100:80](http://202.200.200.100/)subject-name cn=Site_1.[cisco.com](http://cisco.com/)revocation-check crlrsakeypair S1keycrypto pki authenticate CA #通过在线方式认证证书服务器,即可得到CA 服务器的根证书
crypto pki enroll CA #向 CA 服务器申请个人证书
Site_2 离线申请证书配置方式
ip domain name cisco.com
crypto key generate rsa modulus 1024 label S2key
crypto pki trustpoint CA
enrollment terminalsubject-name cn=Site_2.[cisco.com](http://cisco.com/)revocation-check nonecrypto pki authenticate CA # 将导出的 CA 服务器根证书复制黏贴到命令行认证 CA 证书
crypto pki trustpoint CA
rsakeypair S2key # 调用密钥crypto pki enroll CA # 申请证书,会从命令行导出证书申请信息
crypto pki import CA certificate # 导入 CA 颁发的证书
IKEv2 证书认证VPN
Site—1
crypto ikev2 proposal s1
encryption 3des
integrity sha1
group 2
crypto ikev2 policy s1-policy
proposal s1
crypto ikev2 keyring Site-key
peer Site2
address 202.200.200.2
crypto ikev2 profile pro
match identity remote address 202.200.200.2 255.255.255.255
identity local address 202.200.200.1
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint CA
crypto ipsec transform-set Trans esp-3des esp-md5-hmac
mode tunnel
crypto map cisco 10 ipsec-isakmp
set peer 202.200.200.2
set transform-set Trans
set ikev2-profile pro
match address vpn
crypto map cisco
Site—2
crypto ikev2 proposal s2
encryption 3des
integrity sha1
group 2
crypto ikev2 policy s2-poilcy
proposal s2
crypto ikev2 keyring Site2-key
peer Site1
address 202.200.200.1
!
crypto ikev2 profile pro
match identity remote address 202.200.200.1 255.255.255.255
identity local address 202.200.200.2
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint CA
crypto ipsec transform-set Trans esp-3des esp-md5-hmac
mode tunnel
crypto map cisco 10 ipsec-isakmp
set peer 202.200.200.1
set transform-set Trans
set ikev2-profile pro
match address vpn
crypto map cisco

