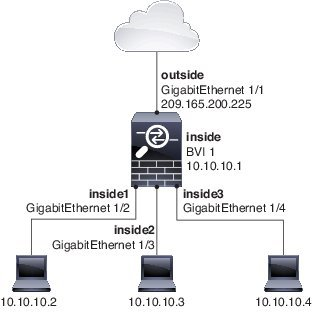
Bridge Virtual Interface (BVI)
Each bridge group includes a Bridge Virtual Interface (BVI). The ASA uses the BVI IP address as the source address for packets originating from the bridge group. The BVI IP address must be on the same subnet as the bridge group member interfaces. The BVI does not support traffic on secondary networks; only traffic on the same network as the BVI IP address is supported.
In transparent mode: Only bridge group member interfaces are named and can be used with interface-based features.
In routed mode: The BVI acts as the gateway between the bridge group and other routed interfaces. To route between bridge groups/routed interfaces, you must name the BVI. For some interface-based features, you can use the BVI itself:
Access rules—You can configure access rules for both bridge group member interfaces and for the BVI; for inbound rules, the member interface is checked first. For outbound rules, the BVI is checked first.
DHCPv4 server—Only the BVI supports the DHCPv4 server configuration.
Static routes—You can configure static routes for the BVI; you cannot configure static routes for the member interfaces.
Syslog server and other traffic sourced from the ASA—When specifying a syslog server (or SNMP server, or other service where the traffic is sourced from the ASA), you can specify either the BVI or a member interface.
ASA 路由模式
路由模式下所有接口都位于不同的子网上,可以在不同墙之间共享接口,如果不需要多模、Cluster、EtherChannel、redundant、VNI member,可以考虑使用透明模式,而不是路由模式。
Bridge Groups in Routed Firewall Mode
在路由模式下,所有的BG组都可以自由通信,但是如果向隔离一个BG组,可以不给它命名,它就会与其它接口和BG组隔离,无法通信。
路由模式特性
在路由模式下,即使在ACL 中明确放行了某些类型的流量,但其仍然无法穿越ASA
IP 流量 - 在路由模式下,即使在ACL中放行了广播和多播流量,但也无法穿越ASA,包括动态路由协议和DHCP。
非 IP 流量 - AppleTalk , IPX , BPDU , PPPOE 和 MPLS 等流量。
部署方式
Unsupported Features for Bridge Groups in Routed Mode
| Feature | Description |
|---|---|
| EtherChannel or VNImember interfaces | Only physical interfaces, redundant interfaces, and subinterfaces are supported as bridge group member interfaces. Management interfaces are also not supported. |
| Clustering | Bridge groups are not supported in clustering. |
| Dynamic DNS | — |
| DHCPv6 stateless server | Only the DHCPv4 server is supported on BVIs. |
| DHCP relay | The routed firewall can act as a DHCPv4 server, but it does not support DHCP relay on BVIs or bridge group member interfaces. |
| Dynamic routing protocols | You can, however, add static routes for BVIs. You can also allow dynamic routing protocols through the ASA using an access rule. Non-bridge group interfaces support dynamic routing. |
| Multicast IP routing | You can allow multicast traffic through the ASA by allowing it in an access rule. Non-bridge group interfaces support multicast routing. |
| Multiple Context Mode | Bridge groups are not supported in multiple context mode. |
| QoS | Non-bridge group interfaces support QoS. |
| VPN termination for through traffic | You cannot terminate a VPN connection on the BVI. Non-bridge group interfaces support VPN. Bridge group member interfaces support site-to-site VPN tunnels for management connections only. It does not terminate VPN connections for traffic through the ASA. You can pass VPN traffic through the bridge group using an access rule, but it does not terminate non-management connections. Clientless SSL VPN is also not supported. |
| Unified Communications | Non-bridge group interfaces support Unified Communications. |
ASA 透明模式
Layer 2 connectivity is achieved by using a “bridge group” where you group together the inside and outside interfaces for a network, and the ASA uses bridging techniques to pass traffic between the interfaces. Each bridge group includes a Bridge Virtual Interface (BVI) to which you assign an IP address on the network. You can have multiple bridge groups for multiple networks. In transparent mode, these bridge groups cannot communicate with each other.
路由模式会对原有网络拓扑产生较大改变,但透明模式不会,适合网络拓扑已经确定的拓扑并且不想做较大改动。路由模式下ASA所有接口都属于三层接口,透明模式下ASA所有接口都是二层接口。
Bridge Groups in Transparent Firewall Mode
透明模式下BG都互相独立,并且彼此不能通信,但是不同的BG组会共享很多配置,syslog server or aaa server 配置等信息,如果需要对每个BG做独立配置,需要在每个墙下的组 进行配置
透明模式特性
允许 3 层流量
允许单播 IPv4 和 IPv6 流量通过网桥组从较高安全性到较低安全性的接口,不需要明确放行
从较低安全性接口到较高安全性接口流量需要访问控制规则放行
ARP 默认可以穿越 ASA
可以使用访问规则传送广播和多播流量
允许 MAC 地址
网桥可以通过一下MAC地址进行MAC地址过滤
TRUE broadcast destination MAC address equal to FFFF.FFFF.FFFF
IPv4 multicast MAC addresses from 0100.5E00.0000 to 0100.5EFE.FFFF
IPv6 multicast MAC addresses from 3333.0000.0000 to 3333.FFFF.FFFF
BPDU multicast address equal to 0100.0CCC.CCCD
AppleTalk multicast MAC addresses from 0900.0700.0000 to 0900.07FF.FFFF
BPDU
数据包处理(MAC查找与路由查找)
对于网桥组内的流量需要执行目的MAC地址查找而不是进行路由查找,根据MAC地址查找来确定出接口。
疑问:是否不同网桥之间永远不能互通???
以下情况进行路由查找
ASA 始发的流量
Voice over IP (VoIP) and TFTP traffic with inspection enabled
CTIQBE
GTP
H.323
MGCP
RTSP
SIP
Skinny (SCCP)
SQL*Net
SunRPC
TFTP
ASA 执行NAT 流量
部署方式
需要将接口划入Bridge Group 中,每一个Bridge Group 都需要有一个和连接网段相同的地址配置到BVI上,在ASA发起流量时该地址用于源地址。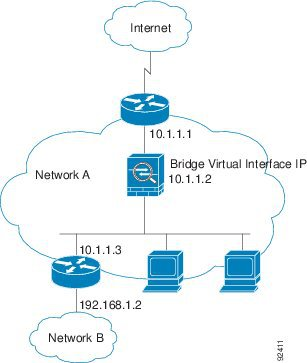
Management Interface
In addition to each Bridge Virtual Interface (BVI) IP address, you can add a separate Management slot/port interface that is not part of any bridge group, and that allows only management traffic to the ASA.
Passing Traffic For Routed-Mode Features
For features that are not directly supported on the transparent firewall, you can allow traffic to pass through so that upstream and downstream routers can support the functionality. For example, by using an access rule, you can allow DHCP traffic (instead of the unsupported DHCP relay feature) or multicast traffic such as that created by IP/TV. You can also establish routing protocol adjacencies through a transparent firewall; you can allow OSPF, RIP, EIGRP, or BGP traffic through based on an access rule. Likewise, protocols like HSRP or VRRP can pass through the ASA.
Unsupported Features for Bridge Groups in Transparent Mode
| Feature | Description |
|---|---|
| Dynamic DNS | — |
| DHCPv6 stateless server | Only the DHCPv4 server is supported on bridge group member interfaces. |
| DHCP relay | The transparent firewall can act as a DHCPv4 server, but it does not support DHCP relay. DHCP relay is not required because you can allow DHCP traffic to pass through using two access rules: one that allows DCHP requests from the inside interface to the outside, and one that allows the replies from the server in the other direction. |
| Dynamic routing protocols | You can, however, add static routes for traffic originating on the ASA for bridge group member interfaces. You can also allow dynamic routing protocols through the ASAusing an access rule. |
| Multicast IP routing | You can allow multicast traffic through the ASA by allowing it in an access rule. |
| QoS | — |
| VPN termination for through traffic | The transparent firewall supports site-to-site VPN tunnels for management connections only on bridge group member interfaces. It does not terminate VPN connections for traffic through the ASA. You can pass VPN traffic through the ASA using an access rule, but it does not terminate non-management connections. Clientless SSL VPN is also not supported. |
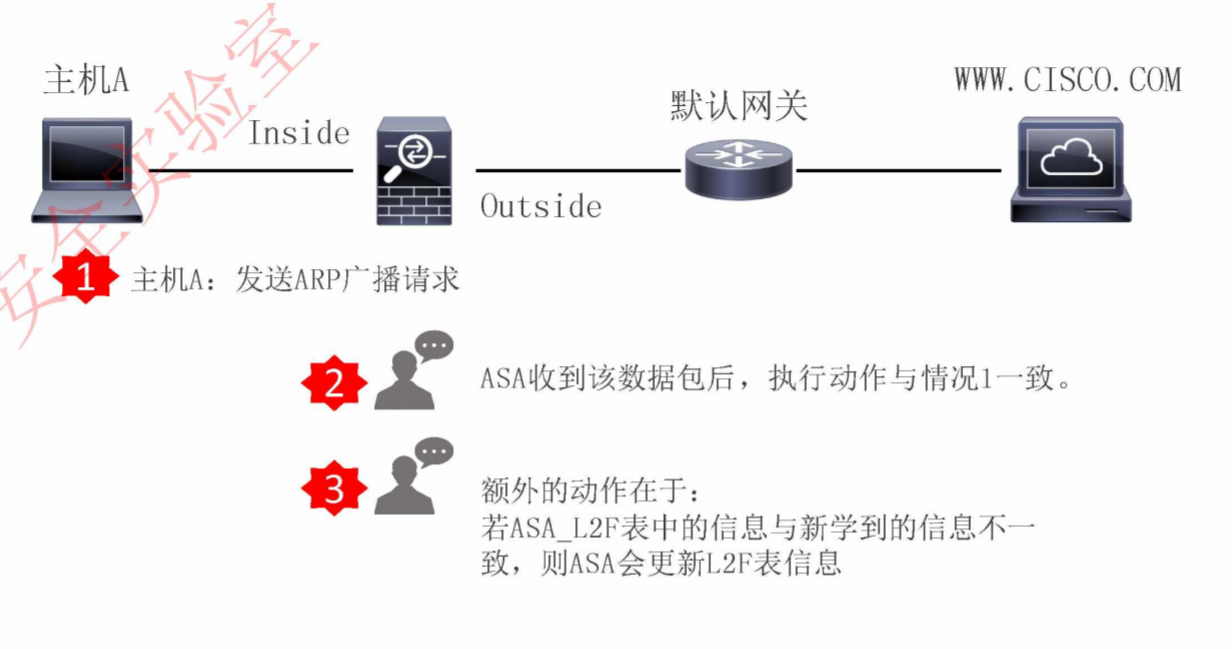
ARP 解析与MAC 地址处理
- 主机A以及ASA没有网关的MAC地址
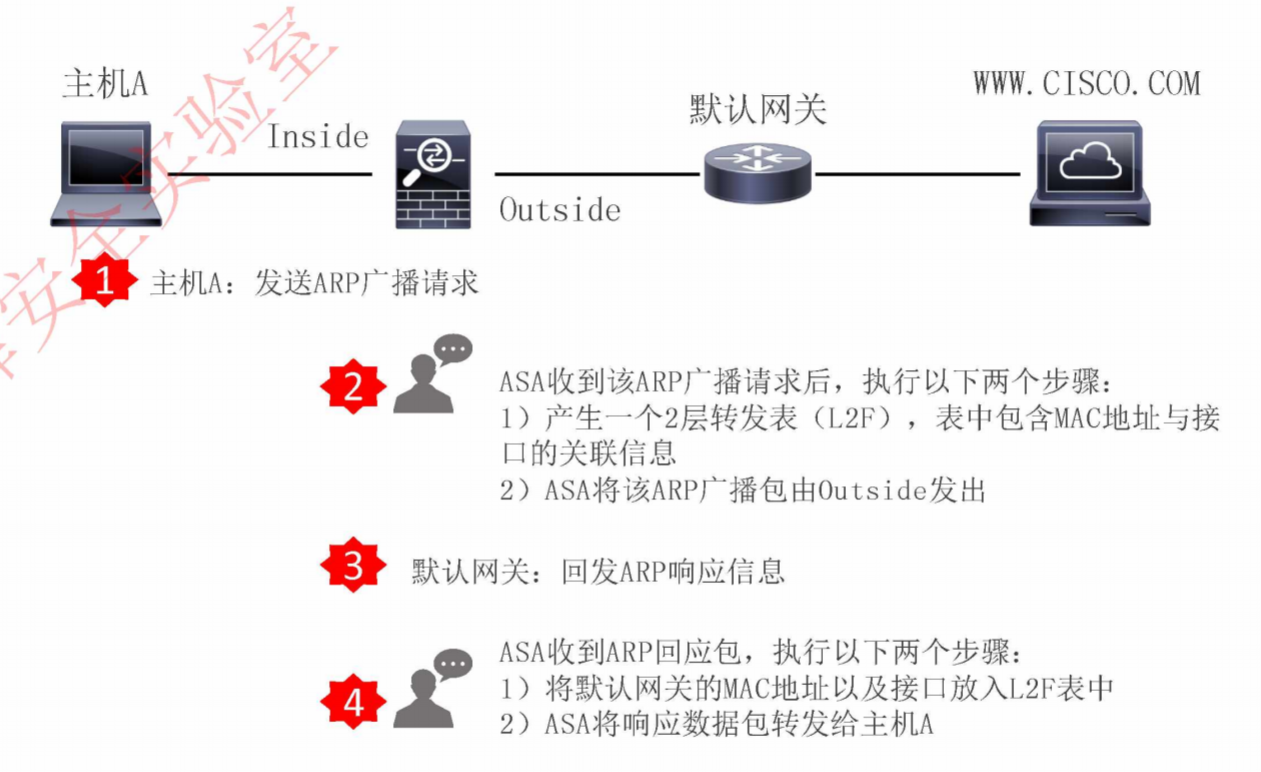
主机A有网关的MAC地址,但是ASA没有
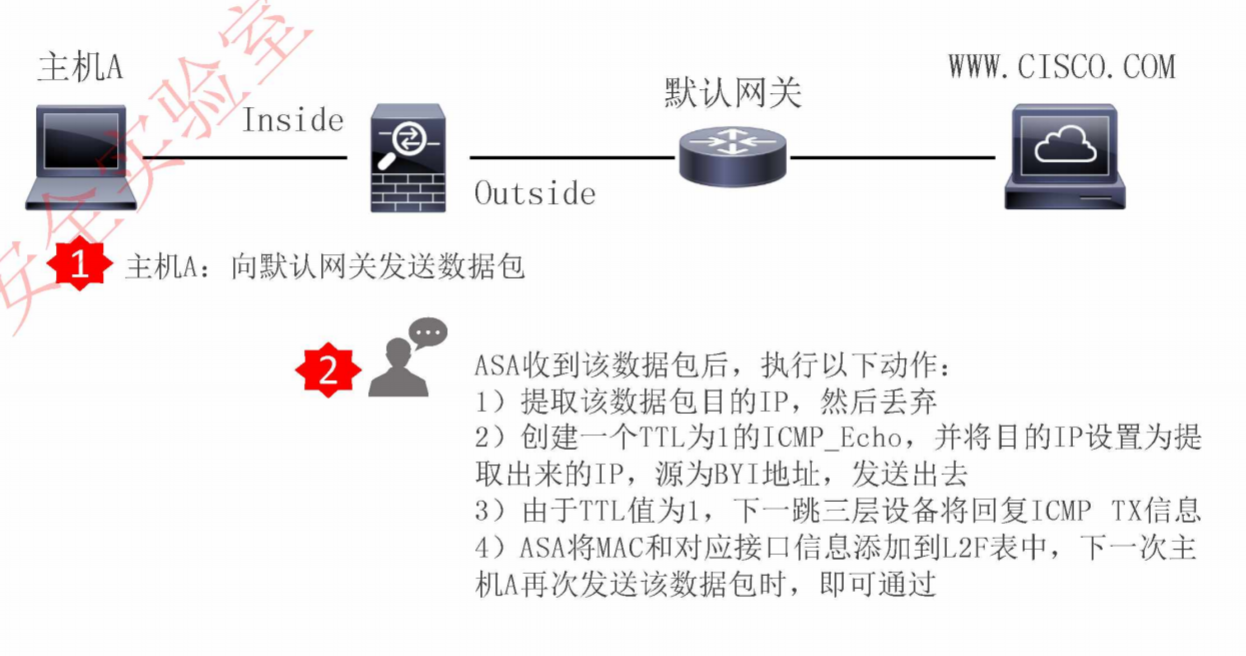
主机A没有网关的MAC地址,但是ASA有
透明防火墙配置指南
内外接口直连网络必须在相同的子网内部
必须要配置一个网管IP
网管IP必须要和内外网段相同
网管IP不能作为网关使用
组播和广播流量需要明确放行(需要双向放行)
可以指定一个特定接口抵达的IP为默认网关,这条路由只起到网管的作用
每个接口必须在不同的VLAN(同网段不同VLAN)
所有流量都可以通过ACL、EtherTypeACL
ARP 默认能够穿越防火墙,可以通过 ARP inspection 来控制
CDP 无法穿越
透明模式下仅管理口可以配置IP地址,也可以使用BVI口做为管理口
透明防火墙支持3层以上访问控制
能够使用所有的访问控制技术
访问控制列表
应用层监控和控制
基于用户策略
IPS和防病毒模块
配置相同
透明模式能转发一些在路由模式转发的流量
透明防火墙默认的安全策略
单播IP流量和路由模式一样,循序相同的安全级别和ACL规则
ARP流量是默认双向允许通过的
CDP流量默认被禁止,即使有明确放行
广播和组播的IP流量需要使用ACL在全部接口明确放行才能通过
在接口使用以太网ACL放行非IP协议流量
如果需要MPLS穿越安全设备,必须确保TDP和LDP会话配置了路由器ID,且该ID必须是与防火墙直连的接口IP
透明防火墙ARP监控
默认情况下ARP监控被关闭
透明防火墙可以开启ARP监控来防止ARP攻击
若数据包完全匹配静态ARP表项,将数据包通过安全设备转发出去
若数据包的IP地址或入接口与静态ARP表项不匹配,则丢弃数据包
若没有在静态ARP表项中找到对应的MAC地址,同时ARP监控启用了FLOOD参数,安全设备会将该数据包从另外接口转发出去
若没有在静态ARP表项中找到对应的MAC地址,同时ARP监控没有启用了FLOOD参数,安全设备会丢弃该数据包并创建一个log
透明防火墙MAC地址表
MAC地址表,经常被用于基于目的MAC地址来查找出接口
CAM表根据收到的帧的二层MAC地址动态构建
如果目的MAC地址在CAM表中没有被找到,则丢弃数据帧
动态MAC地址学习功能是可以关闭的(交换机不行)
能够阻止使用MAC地址欺骗而造成的DOS攻击
能够阻止通过MAC地址泛洪而造成的CAM表溢出攻击
所有连接到ASA的设备MAC地址需要收到被配置

模拟实验
放行非IP流量